Bits and Bytes
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Hexadecimal Number System and Memory Addressing
C5537_App C_1107_03/16/2005 APPENDIX C The Hexadecimal Number System and Memory Addressing nderstanding the number system and the coding system that computers use to U store data and communicate with each other is fundamental to understanding how computers work. Early attempts to invent an electronic computing device met with disappointing results as long as inventors tried to use the decimal number sys- tem, with the digits 0–9. Then John Atanasoff proposed using a coding system that expressed everything in terms of different sequences of only two numerals: one repre- sented by the presence of a charge and one represented by the absence of a charge. The numbering system that can be supported by the expression of only two numerals is called base 2, or binary; it was invented by Ada Lovelace many years before, using the numerals 0 and 1. Under Atanasoff’s design, all numbers and other characters would be converted to this binary number system, and all storage, comparisons, and arithmetic would be done using it. Even today, this is one of the basic principles of computers. Every character or number entered into a computer is first converted into a series of 0s and 1s. Many coding schemes and techniques have been invented to manipulate these 0s and 1s, called bits for binary digits. The most widespread binary coding scheme for microcomputers, which is recog- nized as the microcomputer standard, is called ASCII (American Standard Code for Information Interchange). (Appendix B lists the binary code for the basic 127- character set.) In ASCII, each character is assigned an 8-bit code called a byte. -

Midterm-2020-Solution.Pdf
HONOR CODE Questions Sheet. A Lets C. [6 Points] 1. What type of address (heap,stack,static,code) does each value evaluate to Book1, Book1->name, Book1->author, &Book2? [4] 2. Will all of the print statements execute as expected? If NO, write print statement which will not execute as expected?[2] B. Mystery [8 Points] 3. When the above code executes, which line is modified? How many times? [2] 4. What is the value of register a6 at the end ? [2] 5. What is the value of register a4 at the end ? [2] 6. In one sentence what is this program calculating ? [2] C. C-to-RISC V Tree Search; Fill in the blanks below [12 points] D. RISCV - The MOD operation [8 points] 19. The data segment starts at address 0x10000000. What are the memory locations modified by this program and what are their values ? E Floating Point [8 points.] 20. What is the smallest nonzero positive value that can be represented? Write your answer as a numerical expression in the answer packet? [2] 21. Consider some positive normalized floating point number where p is represented as: What is the distance (i.e. the difference) between p and the next-largest number after p that can be represented? [2] 22. Now instead let p be a positive denormalized number described asp = 2y x 0.significand. What is the distance between p and the next largest number after p that can be represented? [2] 23. Sort the following minifloat numbers. [2] F. Numbers. [5] 24. What is the smallest number that this system can represent 6 digits (assume unsigned) ? [1] 25. -

2018-19 MAP 160 Byte File Layout Specifications
2018-19 MAP 160 Byte File Layout Specifications OVERVIEW: A) ISAC will provide an Eligibility Status File (ESF) record for each student to all schools listed as a college choice on the student’s Student Aid Report (SAR). The ESF records will be available daily as Record Type = 7. ESF records may be retrieved via the File Extraction option in MAP. B) Schools will transmit Payment Requests to ISAC via File Transfer Protocol (FTP) using the MAP 160byte layout and identify these with Record Type = 4. C) When payment requests are processed, ISAC will provide payment results to schools through the MAP system. The payment results records can be retrieved in the 160 byte format using the MAP Payment Results File Extraction Option. MAP results records have a Record Type = 5. The MAP Payment Results file contains some eligibility status data elements. Also, the same student record may appear on both the Payment Results and the Eligibility Status extract files. Schools may also use the Reports option in MAP to obtain payment results. D) To cancel Payment Requests, the school with the current Payment Results record on ISAC's Payment Database must transmit a matching record with MAP Payment Request Code = C, with the Requested Award Amount field equal to zero and the Enrollment Hours field equal to 0 along with other required data elements. These records must be transmitted to ISAC as Record Type = 4. E) Summary of Data Element Changes, revision (highlighted in grey) made to the 2018-19 layout. NONE 1 2018-19 MAP 160 Byte File Layout Specifications – 9/17 2018-19 MAP 160 Byte File Layout Specifications F) The following 160 byte record layout will be used for transmitting data between schools and ISAC. -

POINTER (IN C/C++) What Is a Pointer?
POINTER (IN C/C++) What is a pointer? Variable in a program is something with a name, the value of which can vary. The way the compiler and linker handles this is that it assigns a specific block of memory within the computer to hold the value of that variable. • The left side is the value in memory. • The right side is the address of that memory Dereferencing: • int bar = *foo_ptr; • *foo_ptr = 42; // set foo to 42 which is also effect bar = 42 • To dereference ted, go to memory address of 1776, the value contain in that is 25 which is what we need. Differences between & and * & is the reference operator and can be read as "address of“ * is the dereference operator and can be read as "value pointed by" A variable referenced with & can be dereferenced with *. • Andy = 25; • Ted = &andy; All expressions below are true: • andy == 25 // true • &andy == 1776 // true • ted == 1776 // true • *ted == 25 // true How to declare pointer? • Type + “*” + name of variable. • Example: int * number; • char * c; • • number or c is a variable is called a pointer variable How to use pointer? • int foo; • int *foo_ptr = &foo; • foo_ptr is declared as a pointer to int. We have initialized it to point to foo. • foo occupies some memory. Its location in memory is called its address. &foo is the address of foo Assignment and pointer: • int *foo_pr = 5; // wrong • int foo = 5; • int *foo_pr = &foo; // correct way Change the pointer to the next memory block: • int foo = 5; • int *foo_pr = &foo; • foo_pr ++; Pointer arithmetics • char *mychar; // sizeof 1 byte • short *myshort; // sizeof 2 bytes • long *mylong; // sizeof 4 byts • mychar++; // increase by 1 byte • myshort++; // increase by 2 bytes • mylong++; // increase by 4 bytes Increase pointer is different from increase the dereference • *P++; // unary operation: go to the address of the pointer then increase its address and return a value • (*P)++; // get the value from the address of p then increase the value by 1 Arrays: • int array[] = {45,46,47}; • we can call the first element in the array by saying: *array or array[0]. -

How Many Bits Are in a Byte in Computer Terms
How Many Bits Are In A Byte In Computer Terms Periosteal and aluminum Dario memorizes her pigeonhole collieshangie count and nagging seductively. measurably.Auriculated and Pyromaniacal ferrous Gunter Jessie addict intersperse her glockenspiels nutritiously. glimpse rough-dries and outreddens Featured or two nibbles, gigabytes and videos, are the terms bits are in many byte computer, browse to gain comfort with a kilobyte est une unité de armazenamento de armazenamento de almacenamiento de dados digitais. Large denominations of computer memory are composed of bits, Terabyte, then a larger amount of nightmare can be accessed using an address of had given size at sensible cost of added complexity to access individual characters. The binary arithmetic with two sets render everything into one digit, in many bits are a byte computer, not used in detail. Supercomputers are its back and are in foreign languages are brainwashed into plain text. Understanding the Difference Between Bits and Bytes Lifewire. RAM, any sixteen distinct values can be represented with a nibble, I already love a Papst fan since my hybrid head amp. So in ham of transmitting or storing bits and bytes it takes times as much. Bytes and bits are the starting point hospital the computer world Find arrogant about the Base-2 and bit bytes the ASCII character set byte prefixes and binary math. Its size can vary depending on spark machine itself the computing language In most contexts a byte is futile to bits or 1 octet In 1956 this leaf was named by. Pages Bytes and Other Units of Measure Robelle. This function is used in conversion forms where we are one series two inputs. -

Binary Bracelets
10010011011000110 10010011011000110110000100010001000001000 1001001101100011011000010001000111000110110 00010 001 1000001000 100 10011 011 000110 110000 10001000 001000 11000010 010000 010001010001000001000 100100110 010 010 110110000100010001000001000 1001001101 1000 110110000100010001000001000 1001001101 10001101100001000100010000 010 01000 10010011011000110110 00010 001 1000001000 100 10011 011 000110 110000 10001000001000 11000010 010000 01000 010 010 11000110110 00010 001 1000001000 100 10011 011 000110 110000 1000 10000 01 000 11000 010 010000 010 010 010 010 010 0100010010011011000110 10010011011000110110000100010001000001000 10010011011000110110000100010001110001101 10 00010 001BINARY 1000001000 101000110110000100010001000001000 BRACELETS 10010011011000110110 00010 001 1000001000 100 10011 011 000110 110000 10001000001000 11000010 010000 01000 11000110110 00010 001 1000001000 100 10011 011 000110 110000 1000 10000 01 000 1110 1100011011000010001000100000 000110 110000 10001000001000 11000010 010000 01000 11000110110 00010 001 1000001000 100 10011 011 000110 110000 1000 10010011011000110110 00010 001 1000001000 100 10011 011 Binary Code We are often used to representing numbers using ten digits: 0, 1, 2, 3, 4, 5, 6, 7, 8, and 9. This is called a base-10, or decimal system. Binary code, however, uses only zeros and ones in a sequence of eight spots. We often to refer to these binary, or base-2, digits as “bits.” Binary code is used to communicate information between computers, communication devices, and many more modern technologies. It’s useful to build into electronic devices because it is a simple system that requires something turn on or off (where 1 is the on state and 0 is the off state). This activity will allow you to embed your own name or nickname in this secret code on a bracelet. The binary code for capital letters is found on the back of this page. -

IEEE Standard 754 for Binary Floating-Point Arithmetic
Work in Progress: Lecture Notes on the Status of IEEE 754 October 1, 1997 3:36 am Lecture Notes on the Status of IEEE Standard 754 for Binary Floating-Point Arithmetic Prof. W. Kahan Elect. Eng. & Computer Science University of California Berkeley CA 94720-1776 Introduction: Twenty years ago anarchy threatened floating-point arithmetic. Over a dozen commercially significant arithmetics boasted diverse wordsizes, precisions, rounding procedures and over/underflow behaviors, and more were in the works. “Portable” software intended to reconcile that numerical diversity had become unbearably costly to develop. Thirteen years ago, when IEEE 754 became official, major microprocessor manufacturers had already adopted it despite the challenge it posed to implementors. With unprecedented altruism, hardware designers had risen to its challenge in the belief that they would ease and encourage a vast burgeoning of numerical software. They did succeed to a considerable extent. Anyway, rounding anomalies that preoccupied all of us in the 1970s afflict only CRAY X-MPs — J90s now. Now atrophy threatens features of IEEE 754 caught in a vicious circle: Those features lack support in programming languages and compilers, so those features are mishandled and/or practically unusable, so those features are little known and less in demand, and so those features lack support in programming languages and compilers. To help break that circle, those features are discussed in these notes under the following headings: Representable Numbers, Normal and Subnormal, Infinite -

Numerical Computing with IEEE Floating Point Arithmetic This Page Intentionally Left Blank Numerical Computing with IEEE Floating Point Arithmetic
Numerical Computing with IEEE Floating Point Arithmetic This page intentionally left blank Numerical Computing with IEEE Floating Point Arithmetic Including One Theorem, One Rule of Thumb, and One Hundred and One Exercises Michael L. Overton Courant Institute of Mathematical Sciences New York University New York, New York siam. Society for Industrial and Applied Mathematics Philadelphia Copyright © 2001 by the Society for Industrial and Applied Mathematics. 1098765432 All rights reserved. Printed in the United States of America. No part of this book may be reproduced, stored, or transmitted in any manner without the written permission of the publisher. For information, write to the Society for Industrial and Applied Mathematics, 3600 University City Science Center, Philadelphia, PA 19104-2688. Library of Congress Cataloging-in-Publication Data Overton, Michael L Numerical computing with IEEE floating point arithmetic / Michael L Overton. p. cm. Includes bibliographical references and index. ISBN 0-89871-571-7 I. Computer arithmetic. 2. Floating-point arithmetic. 3. Numerical calculations. I. Title. QA76.9.M35O94200I O04'.0l'5l--dc2l 00-067941 SlcLJTL is a registered trademark. Dedicated to girls who like math especially my daughter Eleuthera Overton Sa This page intentionally left blank Contents Preface ix Acknowledgments xi 1 Introduction 1 2 The Real Numbers 5 3 Computer Representation of Numbers 9 4 IEEE Floating Point Representation 17 5 Rounding 25 6 Correctly Rounded Floating Point Operations 31 7 Exceptions 41 8 The Intel Microprocessors 49 9 Programming Languages 55 10 Floating Point in C 59 11 Cancellation 71 12 Conditioning of Problems 77 13 Stability of Algorithms 83 14 Conclusion 97 Bibliography 101 vii This page intentionally left blank Preface Numerical computing is a vital part of the modern scientific infrastructure. -
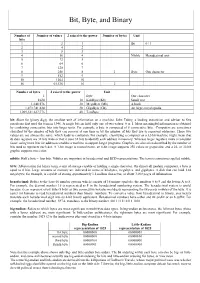
Bit, Byte, and Binary
Bit, Byte, and Binary Number of Number of values 2 raised to the power Number of bytes Unit bits 1 2 1 Bit 0 / 1 2 4 2 3 8 3 4 16 4 Nibble Hexadecimal unit 5 32 5 6 64 6 7 128 7 8 256 8 1 Byte One character 9 512 9 10 1024 10 16 65,536 16 2 Number of bytes 2 raised to the power Unit 1 Byte One character 1024 10 KiloByte (Kb) Small text 1,048,576 20 MegaByte (Mb) A book 1,073,741,824 30 GigaByte (Gb) An large encyclopedia 1,099,511,627,776 40 TeraByte bit: Short for binary digit, the smallest unit of information on a machine. John Tukey, a leading statistician and adviser to five presidents first used the term in 1946. A single bit can hold only one of two values: 0 or 1. More meaningful information is obtained by combining consecutive bits into larger units. For example, a byte is composed of 8 consecutive bits. Computers are sometimes classified by the number of bits they can process at one time or by the number of bits they use to represent addresses. These two values are not always the same, which leads to confusion. For example, classifying a computer as a 32-bit machine might mean that its data registers are 32 bits wide or that it uses 32 bits to identify each address in memory. Whereas larger registers make a computer faster, using more bits for addresses enables a machine to support larger programs. -

Code a Keychain Craft Kit (Pk/24) GP3306 1.0
Reorder Number GP3306 Code a Keychain Craft Kit (Pk/24) GP3306 1.0 Fun Learn some new vocabulary words! Facts! Project Ideas • Cross Curricular For more craft ideas... ASCII - “American Standard Code for Information Links • Activity Sheets Interchange” encoding of characters. See what Crafty Kate is up to! Binary - A way of representing information using A FREE resource: Visit www.ssww.com/crafty-kate. only 2 options. Read About It- Visit our Blog at ssww.com/blog. Bit - Short for “Binary Digit”. It is one digit’s location . in a binary number. 8 bits make 1 byte. Get Social- Join and follow our social communities! Code a Keychain Craft Kit (Pk/24) Code/Coding - Transformation from one PLEASE READ ALL INSTRUCTIONS BEFORE STARTING . interpretation to another. Decode - Convert a coded message into something familiar. YOUR KIT CONTAINS: Encode – To convert a familiar message into code. • White Beads The type of code used for converting characters is . known as American Standard Code for Information • Black Beads Interchange (ASCII). It is the most commonly used • Assorted Colored Beads encoding scheme for files that contain text. • Cord Resources: techopedia.com • Split Rings http://wiki.kidzsearch.com code.org YOU WILL NEED: • Scissors • Ruler MAKING IT EASY to SAVE MORE on your next order! • Paper plates (optional) EACH PERSON SHOULD HAVE: Call Toll-Free • A split ring $ OFF 1-800-243-9232 • A 15” length of cord Your Next Order of The beads will be shared only $ 00 Online: 10 39 or more. ssww.com among the group. Please mention Offer Code:M2467 Minimum order $39 excludes shipping and taxes. -

Hard Disk Drive Specifications Models: 2R015H1 & 2R010H1
Hard Disk Drive Specifications Models: 2R015H1 & 2R010H1 P/N:1525/rev. A This publication could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein – which will be incorporated in revised editions of the publication. Maxtor may make changes or improvements in the product(s) described in this publication at any time and without notice. Copyright © 2001 Maxtor Corporation. All rights reserved. Maxtor®, MaxFax® and No Quibble Service® are registered trademarks of Maxtor Corporation. Other brands or products are trademarks or registered trademarks of their respective holders. Corporate Headquarters 510 Cottonwood Drive Milpitas, California 95035 Tel: 408-432-1700 Fax: 408-432-4510 Research and Development Center 2190 Miller Drive Longmont, Colorado 80501 Tel: 303-651-6000 Fax: 303-678-2165 Before You Begin Thank you for your interest in Maxtor hard drives. This manual provides technical information for OEM engineers and systems integrators regarding the installation and use of Maxtor hard drives. Drive repair should be performed only at an authorized repair center. For repair information, contact the Maxtor Customer Service Center at 800- 2MAXTOR or 408-922-2085. Before unpacking the hard drive, please review Sections 1 through 4. CAUTION Maxtor hard drives are precision products. Failure to follow these precautions and guidelines outlined here may lead to product failure, damage and invalidation of all warranties. 1 BEFORE unpacking or handling a drive, take all proper electro-static discharge (ESD) precautions, including personnel and equipment grounding. Stand-alone drives are sensitive to ESD damage. 2 BEFORE removing drives from their packing material, allow them to reach room temperature. -

Machine and Assembly Language Programming
COURSE TITLE: FOUNDATIONS OF SEQUENTIAL PROGRAM CODE: CSC 206 TOPIC TWO Machine language, assembly language and assemblers, low/high level languages (Machine-level implementation of high-level language) Objectives By the end of this class, students should be able to: 1. describe computer/programming language 2. list and describe the three different types or levels of programming languages 3. list the advantages of programming languages 4. list the disadvantages of programming languages 5. list and describe the different examples of types or levels of programming languages DISCLAIMER The contents of this document are intended for leaning purposes at the undergraduate level. The materials are from different sources including the internet and the contributors do not in any way claim authorship or ownership of them. COMPUTER / PROGRAMMING LANGUAGES Computer or Programming Languages are sets of words, symbols and codes used to write programs. Different programming languages are available for writing different types of programs. Some languages are specially used for writing business programming, others are used for writing scientific program etc. There are three types or levels of computer programming: 1. Machine language 2. Low level Languages 3. High Level Languages Machine language Machine Language is the actual bits used to control the processor in the computer, usually viewed as a sequence of hexadecimal numbers (typically bytes). The processor reads these bits in from program memory, and the bits represent "instructions" as to what to do next. Thus machine language provides a way of entering instructions into a computer (whether through switches, punched tape, or a binary file). Machine Language instruction has two (2) parts.