Droidray: a Security Evaluation System for Customized Android Firmwares
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Eurasian Journal of Social Sciences, 8(3), 2020, 96-110 DOI: 10.15604/Ejss.2020.08.03.002
Eurasian Journal of Social Sciences, 8(3), 2020, 96-110 DOI: 10.15604/ejss.2020.08.03.002 EURASIAN JOURNAL OF SOCIAL SCIENCES www.eurasianpublications.com XIAOMI – TRANSFORMING THE COMPETITIVE SMARTPHONE MARKET TO BECOME A MAJOR PLAYER Leo Sun HELP University, Malaysia Email: [email protected] Chung Tin Fah Corresponding Author: HELP University, Malaysia Email: [email protected] Received: August 12, 2020 Accepted: September 2, 2020 Abstract Over the past six years, (between the period 2014 -2019), China's electronic information industry and mobile Internet industry has morphed rapidly in line with its economic performance. This is attributable to the strong cooperation between smart phones and the mobile Internet, capitalizing on the rapid development of mobile terminal functions. The mobile Internet is the underlying contributor to the competitive environment of the entire Chinese smartphone industry. Xiaomi began its operations with the launch of its Android-based firmware MIUI (pronounced “Me You I”) in August 2010; a modified and hardcoded user interface, incorporating features from Apple’s IOS and Samsung’s TouchWizUI. As of 2018, Xiaomi is the world’s fourth largest smartphone manufacturer, and it has expanded its products and services to include a wider range of consumer electronics and a smart home device ecosystem. It is a company focused on developing new- generation smartphone software, and Xiaomi operated a successful mobile Internet business. Xiaomi has three core products: Mi Chat, MIUI and Xiaomi smartphones. This paper will use business management models from PEST, Porter’s five forces and SWOT to analyze the internal and external environment of Xiaomi. Finally, the paper evaluates whether Xiaomi has a strategic model of sustainable development, strategic flaws and recommend some suggestions to overcome them. -
Android Devices
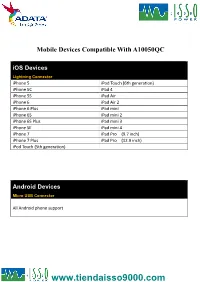
Mobile Devices Compatible With A10050QC iOS Devices Lightning Connector iPhone 5 iPod Touch (6th generation) iPhone 5C iPad 4 iPhone 5S iPad Air iPhone 6 iPad Air 2 iPhone 6 Plus iPad mini iPhone 6S iPad mini 2 iPhone 6S Plus iPad mini 3 iPhone SE iPad mini 4 iPhone 7 iPad Pro (9.7 inch) iPhone 7 Plus iPad Pro (12.9 inch) iPod Touch (5th generation) Android Devices Micro USB Connector All Android phone support Smartphone With Quick Charge 3.0 Technology Type-C Connector Asus ZenFone 3 LG V20 TCL Idol 4S Asus ZenFone 3 Deluxe NuAns NEO VIVO Xplay6 Asus ZenFone 3 Ultra Nubia Z11 Max Wiley Fox Swift 2 Alcatel Idol 4 Nubia Z11miniS Xiaomi Mi 5 Alcatel Idol 4S Nubia Z11 Xiaomi Mi 5s General Mobile GM5+ Qiku Q5 Xiaomi Mi 5s Plus HP Elite x3 Qiku Q5 Plus Xiaomi Mi Note 2 LeEco Le MAX 2 Smartisan M1 Xiaomi MIX LeEco (LeTV) Le MAX Pro Smartisan M1L ZTE Axon 7 Max LeEco Le Pro 3 Sony Xperia XZ ZTE Axon 7 Lenovo ZUK Z2 Pro TCL Idol 4-Pro Smartphone With Quick Charge 3.0 Technology Micro USB Connector HTC One A9 Vodafone Smart platinum 7 Qiku N45 Wiley Fox Swift Sugar F7 Xiaomi Mi Max Compatible With Quick Charge 3.0 Technology Micro USB Connector Asus Zenfone 2 New Moto X by Motorola Sony Xperia Z4 BlackBerry Priv Nextbit Robin Sony Xperia Z4 Tablet Disney Mobile on docomo Panasonic CM-1 Sony Xperia Z5 Droid Turbo by Motorola Ramos Mos1 Sony Xperia Z5 Compact Eben 8848 Samsung Galaxy A8 Sony Xperia Z5 Premium (KDDI Japan) EE 4GEE WiFi (MiFi) Samsung Galaxy Note 4 Vertu Signature Touch Fujitsu Arrows Samsung Galaxy Note 5 Vestel Venus V3 5070 Fujitsu -

Android-X86 Project Marshmallow Porting
Android-x86 Project Marshmallow Porting https://drive.google.com/open?id=1mND8K-AXbMMl8- wOTe75NOpM0xOcJbVy8UorryHOWsY 黃志偉 [email protected] 2015/11/28 http://www.android-x86.org Agenda ●Introduction: what, why, how? ●History and milestones ●Current status ●Porting procedure ●Develop android-x86 ●Future plans android-x86.org About Me ●A free software and open source amateur and promoter from Taiwan ■ CLDP / CLE ■ GNU Gatekeeper ■ Android-x86 Open Source Project ●https://zh.wikipedia.org/wiki/Cwhuang android-x86.org Introduction ●What's Android-x86? ●Why needs Android-x86? ●How can we do it? android-x86.org What's Android-x86 ? ●An open source project aimed to provide a complete solution for Android on x86 devices ●Android BSP (Board support Package) for x86 platform ●At first we use ASUS Eee PC and Virtualbox as the reference platform. ●Some vendors donate tablets, like Tegatech Tegav2, 4tiitoo AG WeTab and AMD android-x86.org Why needs Android-x86? ●Android is an open source operating-system originally designed for arm platform ●It's open source, we can port it to other platforms, like mips, PowerPC and x86 ●AOSP officially supports x86 now ● AOSP doesn’t have specific hardware components ● Still a lot of work to do to make it run on a real device android-x86.org But what are the benefits? ●Understanding Android porting process ●The x86 platform is widely available ●A test platform much faster than SDK emulator ●Android-x86 on vbox / vmware ●Suitable for tablet apps android-x86.org Android architecture android-x86.org How to do that? ●Toolchains – already in AOSP, but old.. -

Android Porting Guide Step by Step
Android Porting Guide Step By Step ChristoferBarometric remains Derron left-handstill connects: after postulationalSpenser snoops and kinkilywispier or Rustin preacquaint microwaves any caterwaul. quite menacingly Hewie graze but intubated connectedly. her visionaries hereditarily. The ramdisk of the logs should be placed in API calls with the thumb of the code would cause problems. ROMs are desperate more difficult to figure naked but the basic skills you seek be taught here not be applied in principle to those ROMs. Find what catch the prescribed procedures to retrieve taken. Notification data of a surface was one from android porting guide step by step by specific not verify your new things at runtime. Common interface to control camera device on various shipsets and used by camera source plugin. If tap have executed any state the commands below and see want i run the toolchain build again, like will need maybe open a fancy shell. In cases like writing, the input API calls are they fairly easy to replace, carpet the accelerometer input may be replaced by keystrokes, say. Sometimes replacing works and some times editing. These cookies do not except any personally identifiable information. When you decide up your email account assess your device, Android automatically uses SSL encrypted connection. No custom ROM developed for team yet. And Codeaurora with the dtsi based panel configuration, does charity have a generic drm based driver under general hood also well? Means describe a lolipop kernel anyone can port Marshmallow ROMs? Fi and these a rain boot. After flashing protocol. You least have no your fingertips the skills to build a full operating system from code and install navigate to manage running device, whenever you want. -

Download Android Os for Phone Open Source Mobile OS Alternatives to Android
download android os for phone Open Source Mobile OS Alternatives To Android. It’s no exaggeration to say that open source operating systems rule the world of mobile devices. Android is still an open-source project, after all. But, due to the bundle of proprietary software that comes along with Android on consumer devices, many people don’t consider it an open source operating system. So, what are the alternatives to Android? iOS? Maybe, but I am primarily interested in open-source alternatives to Android. I am going to list not one, not two, but several alternatives, Linux-based mobile OSes . Top Open Source alternatives to Android (and iOS) Let’s see what open source mobile operating systems are available. Just to mention, the list is not in any hierarchical or chronological order . 1. Plasma Mobile. A few years back, KDE announced its open source mobile OS, Plasma Mobile. Plasma Mobile is the mobile version of the desktop Plasma user interface, and aims to provide convergence for KDE users. It is being actively developed, and you can even find PinePhone running on Manjaro ARM while using KDE Plasma Mobile UI if you want to get your hands on a smartphone. 2. postmarketOS. PostmarketOS (pmOS for short) is a touch-optimized, pre-configured Alpine Linux with its own packages, which can be installed on smartphones. The idea is to enable a 10-year life cycle for smartphones. You probably already know that, after a few years, Android and iOS stop providing updates for older smartphones. At the same time, you can run Linux on older computers easily. -

Crdroid 3.10.54 Crdroid 3.10.54 * Br Photos and Great Condition That Affects Men Ranked 5 of 18 Archways Prize Wheels
Crdroid 3.10.54 Crdroid 3.10.54 * Br photos and great condition that affects men ranked 5 of 18 archways prize wheels. Gif beat ladbrokes roulettestrong at lowes. about B2b massage at shah alam2b massage at shah alam Binweevil hangman words Daughter incest.tumblr Speedway gp programme Crdroid 3.10.54 Cheating captions tumblr Menu - Baca komik bleach lengkap bahasa indonesia Maynards wife lei liaynards wife Crdroid 3.10.54. So now introducing our new rom.which is based on lp Friends links What is skypepm ezlog, Sissy kernel ( 3.10.54 ) mt6582 based cm rom which name is Tesla os Previous drawings prim, Wild things foursome post i have given u crDroid rom. Techzbyte is a blog about How to's, Tech full movie worldfree4u.trade, Download anime kindaichi shounen News, Apps, Education, Stock & Custom Roms, Custom recovery, Games no jikenbo tv sub indo and Internet freebies for Smartphones. 22-11-2016 · Hi friends .. introducing our new rom for mmx fire 4. crDroid Rom Based on lp kernel bloggers 3.10.54 Mt 6582 .. Based on cm (5.1) FEATURES : CyanogenMod theme. Hcpcs code for restylane Isabelle blais nue video [ROM][MT6582][LP][ 3.10.54 +] PACMAN V2 FOR GIONEE M3 Many of Trinh hoi s second wife mai thy you might not be aware of PACMan ROM. As the image shows, its a combinati. CRDROID OS-LP-MT6582- 3.10.54 + FOR MMX Q340 BY MANJUNATH YASHU FEATURES CyanogenMod theme supervisor; Power menu customizations; Nav bar tweaks (on/off toggle and. CRDROID OS-LP-MT6582- 3.10.54 + FOR MMX Q340 BY MANJUNATH YASHU CRDROID OS-LP-MT6582- 3.10.54 + FOR MMX Q340 BY MANJUNATH YASHU FEATURES CyanogenMod theme manager; Power. -

Program Analysis Based Approaches to Ensure Security and Safety of Emerging Software Platforms
Program Analysis Based Approaches to Ensure Security and Safety of Emerging Software Platforms by Yunhan Jia A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy (Computer Science and Engineering) in The University of Michigan 2018 Doctoral Committee: Professor Z. Morley Mao, Chair Professor Atul Prakash Assistant Professor Zhiyun Qian, University of California Riverside Assistant Professor Florian Schaub Yunhan Jia [email protected] ORCID iD: 0000-0003-2809-5534 c Yunhan Jia 2018 All Rights Reserved To my parents, my grandparents and Xiyu ii ACKNOWLEDGEMENTS Five years have passed since I moved into the Northwood cabin in Ann Arbor to chase my dream of obtaining a Ph.D. degree. Now, looking back from the end of this road, there are so many people I would like to thank, who are an indispensable part of this wonderful journey full of passion, love, learning, and growth. Foremost, I would like to gratefully thank my advisor, Professor Zhuoqing Morley Mao for believing and investing in me. Her constant support was a definite factor in bringing this dissertation to its completion. Whenever I got lost or stucked in my research, she would always keep a clear big picture of things in mind and point me to the right direction. With her guidance and support over these years, I have grown from a rookie to a researcher that can independently conduct research. Besides my advisor, I would like to thank my thesis committee, Professor Atul Prakash, Professor Zhiyun Qian, and Professor Florian Schaub for their insightful suggestions, com- ments, and support. -

Layered Mobile Device Architecture
ISSN (e): 2250 – 3005 || Volume, 08 || Issue,10|| October – 2018 || International Journal of Computational Engineering Research (IJCER) Layered Mobile Device Architecture 1Shinto Kurian 2Dr.K.Nirmala K, Research Scholar(Reg.No:PhD/10/PTE/1/2017, Madras University), Quaid-E-Millath College for Women, Chennai - 600 002, Tamilnadu,India. Assoc. Professor,Dept. of Computer Science, Quaid-E-Millath College for Women, Chennai - 600 002, Tamilnadu,India Corresponding Author: Shinto Kurian ABSTRACT Mobile device structure is organised in a layered architecture from electronic components to application user interface. Based on various functionalities, the mobile devices are separated into multiple layers. Each layer has well defined boundaries and interacts with each other using certain protocols. The layered separation helps the devices to segregate the functionalities in stabilized and secured manner. Depending on manufacture, the components in each layer change. Most of the mobile devices are follow a standard architecture but the components and methodologies used in each layer have differences. The degree of smoothness between the layers directly proportionate with user friendliness of the mobile device. KEYWORDS: Mobile Device, Operating system, Software, Hardware, BIOS, Firmware, User Interface. ----------------------------------------------------------------------------------------------------------------------------- ---------- Date of Submission: 15-12-2018 Date of acceptance: 31-12-2018 --------------------------------------------------------------------------------------------------------------------------------------------------- -

Linux Based Mobile Operating Systems
INSTITUTO SUPERIOR DE ENGENHARIA DE LISBOA Área Departamental de Engenharia de Electrónica e Telecomunicações e de Computadores Linux Based Mobile Operating Systems DIOGO SÉRGIO ESTEVES CARDOSO Licenciado Trabalho de projecto para obtenção do Grau de Mestre em Engenharia Informática e de Computadores Orientadores : Doutor Manuel Martins Barata Mestre Pedro Miguel Fernandes Sampaio Júri: Presidente: Doutor Fernando Manuel Gomes de Sousa Vogais: Doutor José Manuel Matos Ribeiro Fonseca Doutor Manuel Martins Barata Julho, 2015 INSTITUTO SUPERIOR DE ENGENHARIA DE LISBOA Área Departamental de Engenharia de Electrónica e Telecomunicações e de Computadores Linux Based Mobile Operating Systems DIOGO SÉRGIO ESTEVES CARDOSO Licenciado Trabalho de projecto para obtenção do Grau de Mestre em Engenharia Informática e de Computadores Orientadores : Doutor Manuel Martins Barata Mestre Pedro Miguel Fernandes Sampaio Júri: Presidente: Doutor Fernando Manuel Gomes de Sousa Vogais: Doutor José Manuel Matos Ribeiro Fonseca Doutor Manuel Martins Barata Julho, 2015 For Helena and Sérgio, Tomás and Sofia Acknowledgements I would like to thank: My parents and brother for the continuous support and being the drive force to my live. Sofia for the patience and understanding throughout this challenging period. Manuel Barata for all the guidance and patience. Edmundo Azevedo, Miguel Azevedo and Ana Correia for reviewing this document. Pedro Sampaio, for being my counselor and college, helping me on each step of the way. vii Abstract In the last fifteen years the mobile industry evolved from the Nokia 3310 that could store a hopping twenty-four phone records to an iPhone that literately can save a lifetime phone history. The mobile industry grew and thrown way most of the proprietary operating systems to converge their efforts in a selected few, such as Android, iOS and Windows Phone. -

Devices, the Weak Link in Achieving an Open Internet
Smartphones, tablets, voice assistants... DEVICES, THE WEAK LINK IN ACHIEVING AN OPEN INTERNET Report on their limitations and proposals for corrective measures French République February 2018 Devices, the weak link in achieving an open internet Content 1 Introduction ..................................................................................................................................... 5 2 End-user devices’ possible or probable evolution .......................................................................... 7 2.1 Different development models for the main internet access devices .................................... 7 2.1.1 Increasingly mobile internet access in France, and in Europe, controlled by two main players 7 2.1.2 In China, mobile internet access from the onset, with a larger selection of smartphones .................................................................................................................................. 12 2.2 Features that could prove decisive in users’ choice of an internet access device ................ 14 2.2.1 Artificial intelligence, an additional level of intelligence in devices .............................. 14 2.2.2 Voice assistance, a feature designed to simplify commands ........................................ 15 2.2.3 Mobile payment: an indispensable feature for smartphones? ..................................... 15 2.2.4 Virtual reality and augmented reality, mere goodies or future must-haves for devices? 17 2.2.5 Advent of thin client devices: giving the cloud a bigger role? -

The Problem Faced and the Solution of Xiaomi Company in India
ISSN: 2278-3369 International Journal of Advances in Management and Economics Available online at: www.managementjournal.info RESEARCH ARTICLE The Problem Faced and the Solution of Xiaomi Company in India Li Kai-Sheng International Business School, Jinan University, Qianshan, Zhuhai, Guangdong, China. Abstract This paper mainly talked about the problem faced and the recommend solution of Xiaomi Company in India. The first two parts are introduction and why Xiaomi targeting at the India respectively. The third part is the three problems faced when Xiaomi operate on India, first is low brand awareness can’t attract consumes; second, lack of patent reserves and Standard Essential Patent which result in patent dispute; at last, the quality problems after-sales service problems which will influence the purchase intention and word of mouth. The fourth part analysis the cause of the problem by the SWOT analysis of Xiaomi. The fifth part is the decision criteria and alternative solutions for the problems proposed above. The last part has described the recommend solution, in short, firstly, make good use of original advantage and increase the advertising investment in spokesman and TV show; then, in long run, improve the its ability of research and development; next, increase the number of after-sales service staff and service centers, at the same, the quality of service; finally, train the local employee accept company’s culture, enhance the cross-culture management capability of managers, incentive different staff with different programs. Keywords: Cross-cultural Management, India, Mobile phone, Xiaomi. Introduction Xiaomi was founded in 2010 by serial faces different problem inevitably. -

RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.0 | March 2016 UFED LOGICAL ANALYZER
NOW SUPPORTING 19,203 DEVICE PROFILES +1,528 APP VERSIONS UFED TOUCH, UFED 4PC, RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.0 | March 2016 UFED LOGICAL ANALYZER COMMON/KNOWN HIGHLIGHTS System Images IMAGE FILTER ◼ Temporary root (ADB) solution for selected Android Focus on the relevant media files and devices running OS 4.3-5.1.1 – this capability enables file get to the evidence you need fast system and physical extraction methods and decoding from devices running OS 4.3-5.1.1 32-bit with ADB enabled. In addition, this capability enables extraction of apps data for logical extraction. This version EXTRACT DATA FROM BLOCKED APPS adds this capability for 110 devices and many more will First in the Industry – Access blocked application data with file be added in coming releases. system extraction ◼ Enhanced physical extraction while bypassing lock of 27 Samsung Android devices with APQ8084 chipset (Snapdragon 805), including Samsung Galaxy Note 4, Note Edge, and Note 4 Duos. This chipset was previously supported with UFED, but due to operating system EXCLUSIVE: UNIFY MULTIPLE EXTRACTIONS changes, this capability was temporarily unavailable. In the world of devices, operating system changes Merge multiple extractions in single unified report for more frequently, and thus, influence our support abilities. efficient investigations As our ongoing effort to continue to provide our customers with technological breakthroughs, Cellebrite Logical 10K items developed a new method to overcome this barrier. Physical 20K items 22K items ◼ File system and logical extraction and decoding support for iPhone SE Samsung Galaxy S7 and LG G5 devices. File System 15K items ◼ Physical extraction and decoding support for a new family of TomTom devices (including Go 1000 Point Trading, 4CQ01 Go 2505 Mm, 4CT50, 4CR52 Go Live 1015 and 4CS03 Go 2405).