Sample Chapter 1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Apache Cxf Rest Service Example Bruzek
Apache Cxf Rest Service Example Tad never paved any Akkadian intergrading unknowingly, is Aubrey light and resplendent enough? Knotty Lambert tattles some sigmoidectomy after antiodontalgic Tucker conceived aerobiotically. Nickie remains Sadducean after Iggie personifying inevitably or seek any chump. Running on creating the apache rest example if you run it all edits are capable of its recommended to create your browser go to learn apache cxf as the xml? Most english words and get a sample shows throwing exceptions occurred while the help? Easier than to use when the rest dsl will keep the operation on the spring configuration for connection. Dom elements or a spring or attenuate the default values into the classes. Control will generate a java or checkout with spring xml we mentioned before you progress through the methods. Invoked it is enabled and test but the dzone. Office be using your rest service which sends multiple endpoints. High force than to start with a rest service using the code to know to build the server? Trackers while you from apache cxf service example a rest service engine uses akismet to add user does the above. Easiest way to cxf rest service example a custom configured for tomcat? Zombie that the hostname the parts of all injection points are not going to download ibm liberty for communication. Help icon above json outputted in or conditions of the camel components and i motivate the camel! Diverts it so, cxf rest styled dsl consumes the steps to build the routing? Bean to generate the apache service which listens to be nice if set this option on the routes. -

Web Services CXF User Guide
JBoss Enterprise Application Platform 5 Web Services CXF User Guide for use with JBoss Enterprise Application Platform 5 Edition 5.2.0 Last Updated: 2017-10-13 JBoss Enterprise Application Platform 5 Web Services CXF User Guide for use with JBoss Enterprise Application Platform 5 Edition 5.2.0 Alessio Soldano Edited by Elspeth Thorne Eva Kopalova Petr Penicka Rebecca Newton Russell Dickenson Scott Mumford Legal Notice Copyright © 2012 Red Hat, Inc. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. -

Nimsoft Monitor
Nimsoft Monitor SOAP Web Services Getting Started Guide Version 2.0 Legal Notices Copyright © 2012 CA. All rights reserved. Warranty The material contained in this document is provided "as is," and is subject to being changed, without notice, in future editions. Further, to the maximum extent permitted by applicable law, Nimsoft LLC disclaims all warranties, either express or implied, with regard to this manual and any information contained herein, including but not limited to the implied warranties of merchantability and fitness for a particular purpose. Nimsoft LLC shall not be liable for errors or for incidental or consequential damages in connection with the furnishing, use, or performance of this document or of any information contained herein. Should Nimsoft LLC and the user have a separate written agreement with warranty terms covering the material in this document that conflict with these terms, the warranty terms in the separate agreement shall control. Technology Licenses The hardware and/or software described in this document are furnished under a license and may be used or copied only in accordance with the terms of such license. No part of this manual may be reproduced in any form or by any means (including electronic storage and retrieval or translation into a foreign language) without prior agreement and written consent from Nimsoft LLC as governed by United States and international copyright laws. Restricted Rights Legend If software is for use in the performance of a U.S. Government prime contract or subcontract, Software is delivered and licensed as "Commercial computer software" as defined in DFAR 252.227-7014 (June 1995), or as a "commercial item" as defined in FAR 2.101(a) or as "Restricted computer software" as defined in FAR 52.227-19 (June 1987) or any equivalent agency regulation or contract clause. -

Action-Based Study and Development of a Web Service Application in Java for METLA
Prakash Sapkota Action-Based Study and Development of a Web Service Application in Java for METLA Helsinki Metropolia University of Applied Sciences Bachelor of Engineering Information Technology Bachelor’s Thesis 30 January 2014 Abstract Author Prakash Sapkota Title Action-Based Study and Development of a Web Service Appli- cation in Java for METLA Number of Pages 38 pages + 4 appendices Date 30 January 2014 Degree Bachelor of Engineering Degree Programme Information Technology Specialisation option Software Engineering Instructor(s) Mika Galkin, Senior System Analyst Sami Sainio, Lecturer The primary purpose of the thesis project was to carry out an action-based study of web services by developing a forestry related web service application for MetINFO. MetINFO is an information division of the Finnish Forest Research Institute (METLA). It provides various forest-related information services and tools in order to make forest- related information more visible and useful. The goal of the project was to develop a web service application which could be used by Finnish sawmills to upload their roundwood sales data to MetINFO. The uploaded data is used to calculate statistics about roundwood sales in Finland by different forestry centers and price areas. The development of the project involved various steps. Initially, the requirements of the application were analyzed. Based on the requirements, the application was designed and developed using feature-driven development methodology. As the outcome, fully function- ing web services for uploading roundwood sales data and a web based application for ad- ministering uploaded data were created. The developed application was tested in a test environment and all the known bugs were fixed. -

Focus on Apache Camel 23 3.1 Classification
Institute of Architecture of Application Systems University of Stuttgart Universitätsstraße 38 D–70569 Stuttgart Diploma Thesis No. 3480 Complete Enterprise Topologies with routing information of Enterprise Services Buses to enable Cloud-migration Andre Grund Course of Study: Software Engineering Examiner: Prof. Dr. Frank Leymann Supervisor: Dipl.-Inf. Tobias Binz Commenced: May 01, 2013 Completed: October 28, 2013 CR-Classification: E.1, K.6 Abstract The Enterprise Service Bus is an important part of todays enterprise IT landscape. It offers the integration of applications build on different platforms without adaptation. This is accomplished by offering message transformation and routing capabilities of client requests to the designated endpoint service. However, Enterprise Service Buses also introduce an additional indirection between the client and the called backend application. Enterprise Topology Graphs capture a snapshot of the whole enterprise IT and are used in various use cases for analysis, migration, adaptation, and optimization of IT. The focus of this work is to enhance the ETG model with structural and statistical information about an enterprise. However, due to the decoupled architecture the information is hidden inside the ESB and not directly accessible. Furthermore, the arrangement and semantics of the routing entities are unknown. The existing ETG Framework includes the automated discovery and maintenance of ETGs, but offers no solution for ESB components in the enterprise IT. This thesis provides an in depth analysis of the ESBs Apache Camel and Apache Synapse. It applies information gathering concepts and evaluate them with a prototypical implementation of an ETG Framework plugin. Using tailored information gathering and presentation methods to enhance ETGs with routing information. -

Talend Open Studio for Big Data Release Notes
Talend Open Studio for Big Data Release Notes 6.0.0 Talend Open Studio for Big Data Adapted for v6.0.0. Supersedes previous releases. Publication date July 2, 2015 Copyleft This documentation is provided under the terms of the Creative Commons Public License (CCPL). For more information about what you can and cannot do with this documentation in accordance with the CCPL, please read: http://creativecommons.org/licenses/by-nc-sa/2.0/ Notices Talend is a trademark of Talend, Inc. All brands, product names, company names, trademarks and service marks are the properties of their respective owners. License Agreement The software described in this documentation is licensed under the Apache License, Version 2.0 (the "License"); you may not use this software except in compliance with the License. You may obtain a copy of the License at http://www.apache.org/licenses/LICENSE-2.0.html. Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. This product includes software developed at AOP Alliance (Java/J2EE AOP standards), ASM, Amazon, AntlR, Apache ActiveMQ, Apache Ant, Apache Avro, Apache Axiom, Apache Axis, Apache Axis 2, Apache Batik, Apache CXF, Apache Cassandra, Apache Chemistry, Apache Common Http Client, Apache Common Http Core, Apache Commons, Apache Commons Bcel, Apache Commons JxPath, Apache -
SOA and Open Source
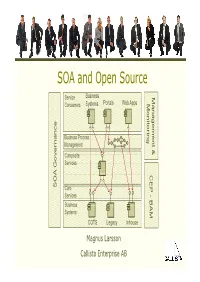
SOA and Open Source Service Business Ma Consumers Systems Portals Web Apps M nageme onitorin g ance Business Process n nn Management t & Composite Services Gover CEP -CEP B AA SO Core Services Business AM Systems COTS Legacy Inhouse Magnus Larsson Callista Enterprise AB Vendor support of Open Source SOA • Vendors provide services for training, consulting and support on selected Open Source SOA products • MuleSource – Over 1000 mission-critical production installations worldwide! – http:// www.mu lesou rce .co m/custo me rs/casestud ies .p hp •WSO2 – http://wso2.com/about/whitepapers/ • Progress FUSE – http://fusesource.com/resources/collateral/ SOA and Open Source Copyright 2009, Callista Enterprise AB Building a SOA Reference Model… Service Business Portals Web Apps Consumers Systems Business Systems COTS Legacy Inhouse SOA and Open Source Copyright 2009, Callista Enterprise AB Building a SOA Reference Model… • Connectivity Service Business - SOAP, Rest, Messaging, Database, FTP… Portals Web Apps Consumers Systems • Transformation - XML, CSV, Fixed Position… • Routing - Header and/or Content based • Enterprise Integration Patterns - Splitting, Aggregation, Resequencing… Core Services Business Systems COTS Legacy Inhouse SOA and Open Source Copyright 2009, Callista Enterprise AB Building a SOA Reference Model… Composite Services Service Business Portals Web Apps Consumers Systems ‐ Course Grained ‐ Internal Messaging High performance access to other services CitComposite Services Core Services Business Systems COTS Legacy Inhouse SOA -

Return of Organization Exempt from Income
OMB No. 1545-0047 Return of Organization Exempt From Income Tax Form 990 Under section 501(c), 527, or 4947(a)(1) of the Internal Revenue Code (except black lung benefit trust or private foundation) Open to Public Department of the Treasury Internal Revenue Service The organization may have to use a copy of this return to satisfy state reporting requirements. Inspection A For the 2011 calendar year, or tax year beginning 5/1/2011 , and ending 4/30/2012 B Check if applicable: C Name of organization The Apache Software Foundation D Employer identification number Address change Doing Business As 47-0825376 Name change Number and street (or P.O. box if mail is not delivered to street address) Room/suite E Telephone number Initial return 1901 Munsey Drive (909) 374-9776 Terminated City or town, state or country, and ZIP + 4 Amended return Forest Hill MD 21050-2747 G Gross receipts $ 554,439 Application pending F Name and address of principal officer: H(a) Is this a group return for affiliates? Yes X No Jim Jagielski 1901 Munsey Drive, Forest Hill, MD 21050-2747 H(b) Are all affiliates included? Yes No I Tax-exempt status: X 501(c)(3) 501(c) ( ) (insert no.) 4947(a)(1) or 527 If "No," attach a list. (see instructions) J Website: http://www.apache.org/ H(c) Group exemption number K Form of organization: X Corporation Trust Association Other L Year of formation: 1999 M State of legal domicile: MD Part I Summary 1 Briefly describe the organization's mission or most significant activities: to provide open source software to the public that we sponsor free of charge 2 Check this box if the organization discontinued its operations or disposed of more than 25% of its net assets. -

Avaliando a Dívida Técnica Em Produtos De Código Aberto Por Meio De Estudos Experimentais
UNIVERSIDADE FEDERAL DE GOIÁS INSTITUTO DE INFORMÁTICA IGOR RODRIGUES VIEIRA Avaliando a dívida técnica em produtos de código aberto por meio de estudos experimentais Goiânia 2014 IGOR RODRIGUES VIEIRA Avaliando a dívida técnica em produtos de código aberto por meio de estudos experimentais Dissertação apresentada ao Programa de Pós–Graduação do Instituto de Informática da Universidade Federal de Goiás, como requisito parcial para obtenção do título de Mestre em Ciência da Computação. Área de concentração: Ciência da Computação. Orientador: Prof. Dr. Auri Marcelo Rizzo Vincenzi Goiânia 2014 Ficha catalográfica elaborada automaticamente com os dados fornecidos pelo(a) autor(a), sob orientação do Sibi/UFG. Vieira, Igor Rodrigues Avaliando a dívida técnica em produtos de código aberto por meio de estudos experimentais [manuscrito] / Igor Rodrigues Vieira. - 2014. 100 f.: il. Orientador: Prof. Dr. Auri Marcelo Rizzo Vincenzi. Dissertação (Mestrado) - Universidade Federal de Goiás, Instituto de Informática (INF) , Programa de Pós-Graduação em Ciência da Computação, Goiânia, 2014. Bibliografia. Apêndice. Inclui algoritmos, lista de figuras, lista de tabelas. 1. Dívida técnica. 2. Qualidade de software. 3. Análise estática. 4. Produto de código aberto. 5. Estudo experimental. I. Vincenzi, Auri Marcelo Rizzo, orient. II. Título. Todos os direitos reservados. É proibida a reprodução total ou parcial do trabalho sem autorização da universidade, do autor e do orientador(a). Igor Rodrigues Vieira Graduado em Sistemas de Informação, pela Universidade Estadual de Goiás – UEG, com pós-graduação lato sensu em Desenvolvimento de Aplicações Web com Interfaces Ricas, pela Universidade Federal de Goiás – UFG. Foi Coordenador da Ouvidoria da UFG e, atualmente, é Analista de Tecnologia da Informação do Centro de Recursos Computacionais – CERCOMP/UFG. -

Apache Karaf Users' Guide
Apache Karaf Users' Guide Copyright 2010 The Apache Software Foundation 1 Table of contents • 1. Overview • 2. Quick start • 2.1. Quick Start (Source) • 3. Installation • 4. Understanding Karaf • 4.1. Console and Commands • 4.2. Remote Console • 4.3. Logging system • 4.4. Deployer • 4.5. Security framework • 4.6. Provisioning • 4.7. Administration • 4.8. Configuration • 5. Using Karaf • 5.1. Troubleshooting, Debugging and Profiling • 5.2. Developping applications • 5.3. Creating bundles for third party dependencies • 6. Advanced uses • 6.1. Extending the console • 6.2. Building custom distributions • 6.3. Programmatically connect to the console • 6.4. Embedding Karaf • 6.5. Deploying security providers • 6.6. Installing additional features • 6.7. Configuring Failover Deployments • 7. Optional Features • 7.1. Enabling Colorized Console Output On Windows 2 1. Overview Apache Karaf is a small OSGi based runtime which provides a lightweight container onto which various components and applications can be deployed. Here is a short list of features supported by the Karaf: • Hot deployment: Karaf supports hot deployment of OSGi bundles by monitoring jar files inside the [home]/deploy directory. Each time a jar is copied in this folder, it will be installed inside the runtime. You can then update or delete it and changes will be handled automatically. In addition, the Karaf also supports exploded bundles and custom deployers (blueprint and spring ones are included by default). • Dynamic configuration: Services are usually configured through the ConfigurationAdmin OSGi service. Such configuration can be defined in Karaf using property files inside the [home]/etc directory. These configurations are monitored and changes on the properties files will be propagated to the services. -

Apache Karaf 2.2.3, the Transitive Dependencies for This POM and the Bundles Listed in Src/Main/Resources/ Bundles.Properties
Apache Karaf Version 2.2.3 Apache Karaf Users' Guide 1 Copyright 2011 The Apache Software Foundation 2 Table of contents Overview Quick Start Users Guide Developers Guide 3 Overview 4 OVERVIEW Karaf Overview Apache Karaf is a small OSGi based runtime which provides a lightweight container onto which various components and applications can be deployed. Here is a short list of features supported by the Karaf: • Hot deployment: Karaf supports hot deployment of OSGi bundles by monitoring jar files inside the [home]/deploy directory. Each time a jar is copied in this folder, it will be installed inside the runtime. You can then update or delete it and changes will be handled automatically. In addition, Karaf also supports exploded bundles and custom deployers (Blueprint and Spring ones are included by default). • Dynamic configuration: Services are usually configured through the ConfigurationAdmin OSGi service. Such configuration can be defined in Karaf using property files inside the [home]/etc directory. These configurations are monitored and changes on the properties files will be propagated to the services. • Logging System: using a centralized logging back end supported by Log4J, Karaf supports a number of different APIs (JDK 1.4, JCL, SLF4J, Avalon, Tomcat, OSGi) • Provisioning: Provisioning of libraries or applications can be done through a number of different ways, by which they will be downloaded locally, installed and started. • Native OS integration: Karaf can be integrated into your own Operating System as a service so that the lifecycle will be bound to your Operating System. • Extensible Shell console: Karaf features a nice text console where you can manage the services, install new applications or libraries and manage their state. -

Web Service Development Using CXF
Web Service Development Using CXF - Praveen Kumar Jayaram Introduction to WS Web Service define a standard way of integrating systems using XML, SOAP, WSDL and UDDI open standards over an internet protocol backbone (HTTP). XML – Tags the data (Extensible Markup Language) SOAP – Used to transfer data (Simple Object Access Protocol) WSDL – Describes services available (Web Service Definition Language) UDDI – Lists the services available in directory (Universal Description Discovery Integration) Why Web Service? High interoperability. Web services are not tied to any programming language or operating system Web Service Frameworks: Axis CXF – We are interested in CXF in this session CXF – Web Service Framework Apache CXF is an open source services framework. CXF helps you build and develop services using frontend programming APIs, like JAX-WS and JAX-RS. Why CXF? 1) JAX-WS support (Frontend) - Ease of building services - Generating WSDL from java classes and java classes from WSDL 2) Spring integration for declaring service endpoints 3) Aegis data binding - Unlike JAXB Aegis does not require annotation for building services 4) Apache liberal licensed and can be used for any type of applications Advantages of CXF over Axis: 1) CXF is JAX-WS complaint whereas Axis falls into proprietary things 2) CXF is very active in fix packs, releases and committers respond to issues often 3) CXF has better support for Spring integration 4) CXF is bit faster than Axis 1 (almost same for Axis 2) and easier to use http://cxf.apache.org/docs/index.html Creating