MP/M II Operating System USER's GUIDE
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

GBCC-CIS-1 Page 1 Micro-Soft’S Macro-Impact
CIS111 GBCC Renee Dodge CIS111 Mid-Term – Fall 2010 For your mid-term, I would like you to conduct some research on the history of computers. Select a milestone or event that you feel had a significant impact on the overall development of computers and how we use computers today. Be sure you not only provide your opinion as to why you feel this milestone is significant, but also provide historical proof - actual facts as to how this event shaped the development and use of computers. For this assignment, please complete the following: 1. Choose a topic 2. Research your topic and locate at least 5 different sources of information, overall. o At least 3 sources should be Internet websites. o Remember: Wikipedia is NOT an acceptable research source. 3. In addition to the Internet, you should also utilize the library online resources (EBSCO database, e-Books, etc). o At least 2 different sources of information should be online library resources. o If you have never used the library online resources before, you may ask me for a brief overview of how to use them or see Becky Clerkin in the library for help. 4. Include your research findings in a 5-page paper and be sure to properly cite where you found your information. If you are not sure how to cite references check out the following link: How to Cite Books, Magazines, and Web Sites in a Research Paper: http://www.lib.duke.edu/libguide/works_cited.htm 5. Upload your research paper to the Digital Drop BoX no later than Wednesday, October 27th at 11:59pm. -

A Guide to Discuss Ethical Issues in Digital Research Second Edition
Ethical challenges in digital research 2nd edition ETHICAL CHALLENGES IN DIGITAL RESEARCH A guide to discuss ethical issues in digital research Second edition Ethical challenges in digital research 2nd edition Ethical challenges in digital research – A guide to discuss ethical issues in digital research Second edition January 2020 Developed by DIGETIK at Aalborg University as part of DIGHUMLAB Authors Line Lisberg Christensen, Research Assistant Malene Charlotte Larsen, Associate Professor Layout Steffen Madsen, DIGHUMLAB i Ethical challenges in digital research 2nd edition I. Introduction to document The ever-changing development of digital technologies and digital infrastructure makes it necessary for us as researchers to change approaches to digital research within the humanities. In terms of research ethics, we can no longer use traditional laws and guidelines that only match the non-digital world. In a time where it is necessary to change and re-think our ways of doing research, we bring to you this second version of Ethical Challenges in Digital Research to initiate discussions about ethical research and to help guide you in your digital research. The compound may serve you as a guideline to ethical research, a helpful tool to those in need of inspiration or merely as a list of literature that is relevant to your field, whether that is: big data, surveillance, privacy, games and gamification, ethics in studies with children and adolescents, health research, journalism, ethnographic studies, visual methods, vulnerable groups, web archives, economy, risky business for researchers or one of the many other categories in this collection of ethical digital research. We initially created this document with the intention of helping scholars reflect and discuss the ethical dimensions of their digital research, whilst providing guidance and insight about how to deal with these issues. -

Concurrent CP/M-86 User's Guide 1.1 What Concurrent CP/M-86 Is
Concurrent CP/M-86™ Operating System Concurrent CP/M-86™ Operating System User's Guide Copyright © 1982 Digital Research P.O. Box -579 160 Central Avenue Pacific Grove, CA 93950 (408) 649-3896 TWX 910 360 5001 All Rights Reserved COPYRIGHT Copyr ight © 1982 by Digi tal Research. All r igh ts reserved. No part of this pUblication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language or compu ter language, in any form or by any means, electronic, mechanical, magnetic, optical, chemical, manual or otherwise, without the prior written permiss ion of Digital Research, Post Off ice Box 579, Pacific Grove, California, 93950. This manual is, however, tutorial in nature. Thus, the reader is granted permission to include the example programs, either in whole or in part, in his own programs. DISCLAIMER Digital Research makes no representations or warranties with respect to the contents hereof and specifically disclaims any ,implied warranties of merchantabil i ty or fitness for any particular purpose. Further, Digital Research reserves the right to revise this publication and to make changes f rom time to time in the content hereof wi thou t obligation of Digital Research to notify any person of such revision or changes. TRADEMARKS CP/M is a registered trademark of Digital Research. ASM-86, CP/M-86, Concurrent CP/M-86 and DDT-86 are trademarks of Digital Research. ED and TEX are utilities of Digital Research. Intel is a registered trademark of Intel Corporation. The IBM Personal Computer is a trade name of International Business Machines. -

OS 386 Multiuser/Multitasking Operating System
OS 386 Multiuser/Multitasking Operating System REFERENCE GUIDE [Q] DIGITAL RESEARCH@ os REFERENCE GUIDE [jill DIGITAL RESEARCH~ COPYRIGHT Copyright © 1987 Digital Research Inc. All rights reserved. No part of this publication may be reproduced, transcribed, stored in a retrieval system, or translated into any language or computer language, in any form or by any means, electronic, mechanical, magnetic, optical, chemical, manual or otherwise without the prior written permission of Digital Research Inc, 60 Garden Court, Box DRI, Monterey, California 93942 DISCLAIMER DIGITAL RESEARCH MAKES NO REPRESENTATIONS OR WARRANTIES WITH RESPECT TO THE CONTENTS HEREOF AND SPECIFICALLY DISCLAIMS ANY IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR ANY PARTICULAR PURPOSE. Further Digital Research Inc. reserves the right to revise this publication and to make changes from time to time in the content hereof without obligation of Digital Research Inc to notify any person of such revision or changes. NOTICE TO USER This manual should not be construed as any representation or warranty with respect to the software named herein. Occasionally changes or variations exist in the software that are not reflected in the manual. Generally, if such changes or variations are known to exist and to affect the product significantly, a release note or READ.ME file accompanies the manual and the distribution disks. In that event, be sure to read the release note or READ.ME file before using the product. ii TRADEMARKS Digital Research and its logo, CP/M, and CP/M-86 are registered trademarks of Digital Research Inc. Cardfile, Concurrent, Concurrent DOS 386, Concurrent DOS XM, DR EDIX, DOS Plus and MP/M-86 are trademarks of Digital Research Inc. -

DR DOS for the Zfx86
DR DOS for the ZFx86 Cost Effective, Reliable, Rapid Deployment of Embedded Systems w DR DOS on the ZFx86 gets products to market quickly at the lowest development and ownership cost. w Thousands of compatible applications, drivers and utilities available free or at minimal cost. w Full documentation available. DR DOS 7.03 Key Features of DR DOS Online Manual - DRDOS is supplied with a complete The ideal embedded DOS system, online manual that contains detailed information about all designed for out-of-the-box of the features of the operating system including the basic implementation into ROM or Flash commands, and the advanced utilities. It also has online ROM with tools and associated help available for all its commands. documents available in the DRDOS Memory Management - Memory management features OEM Documentation Kit. include a set of device drivers and commands that enable w 100% MS-DOS 6.22 compatible.. you to manage memory efficiently and make as much memory as possible available to your applications. w Comprehensive DOS utility set DOS Protected Mode Services - DOS Protected Mode w Multitasking, with API for developers Services (DPMS) interface allows specially-implemented w DPMS memory manager in addition to DPMI device drivers and TSRs to operate in extended memory. w Stacker disk compression This makes more memory within the first megabyte w NWCACHE - disk caching program available to applications and other conventionally-written drivers and TSRs. Both Stacker* (the disk compression w EMM386 memory manager program), and NWCACHE (the disk cache) use DPMS. w DOS Protected Mode Services (DPMS) Disk Compression - The disk compression component w Multitasking enables you to store more information by compressing the w DR-DOS provides a full multitasking environment data. -

Microsoft Plays Hardball: Use of Exclusionary Pricing and Technical
Antitrust Bulletin, XL:2, Summer 1995, 265-315 MICROSOFT PLAYS HARDBALL: The Use of Exclusionary Pricing and Technical Incompatibility to Maintain Monopoly Power in Markets for Operating System Software† by KENNETH C. BASEMAN* FREDERICK R. WARREN-BOULTON* and GLENN A. WOROCH** May 1995 ___________________ * Principals, MiCRA: Microeconomic Consulting and Research Associates, Inc., Washington, DC. ** University of California, Berkeley. † Forthcoming, Antitrust Bulletin, June 1995. We would like to express our appreciation for helpful comments and other assistance to Sturge Sobin, Linnet Harlan, Paul Dennis and the participants at the Columbia Business School's Institute for Tele-Information's Seminar on Sustaining Competition in Network Industries through Regulating and Pricing Access, especially Janusz Ordover and Bobby Willig. TABLE OF CONTENTS I. INTRODUCTION AND SUMMARY ................................... 1 II. BACKGROUND .................................................... 3 A. THE MARKET FOR PERSONAL COMPUTER OPERATING SYSTEMS ............................................................ 3 TABLE: NEW SHIPMENTS OF PERSONAL COMPUTER OPERATING SYSTEMS .............................................. 8 B. MICROSOFT'S PRACTICES ..................................... 9 III. FIRST-DEGREE PRICE DISCRIMINATION vs. INEFFICIENT SUBSTITUTION ................................................... 15 A. FIRST-DEGREE PRICE DISCRIMINATION ........................ 16 B. INEFFICIENT SUBSTITUTION ................................. 20 IV. ANTIFRAUD AND ANTIPIRACY -

HISTORY 4816A / 9877A Digital Research Methods Fall/Winter 2020-21 4 Hours Per Week, No Fixed Times Scheduled, Offered Online Only
HISTORY 4816A / 9877A Digital Research Methods Fall/Winter 2020-21 4 hours per week, no fixed times scheduled, offered online only Instructor: Professor William J. Turkel Office Hours: Mondays through Thursdays, 5-5:45pm or by appointment, meeting online only Department of History, Office: Lawson Hall 2267 Email: [email protected] This is a draft syllabus. Please see your course OWL site for the final syllabus. This course will take place in a virtual, asynchronous format - on-line with no scheduled meeting time. Course Description: In this course students will learn how historical content is produced, presented and published online; how to find and evaluate digital primary and secondary sources; and how to use computational techniques to work with digital resources. No previous background in the subject area is required. Prerequisite(s): Registration in any academic program at the second-year level or above. Unless you have either the prerequisites for this course or written special permission from your Dean to enroll in it, you may be removed from this course and it will be deleted from your record. The decision may not be appealed. You will receive no adjustment to your fees in the event that you are dropped from a course for failing to have the necessary prerequisites. Antirequisite(s): Digital Humanities 2130A/B, Digital Humanities 3902F/G, the former History 2816F/G. Course Syllabus: Research of all kinds now crucially involves the acquisition and use of digital sources, both primary and secondary. In this course, you will learn to find, harvest, manage, excerpt, cluster and analyze digital materials throughout the research process, from initial exploratory forays through the production of an electronic article or monograph which is ready to submit for publication. -

Digital Researchtm Pl/I-80 Language Manual
LANGUAGE MANUAL [j]] DIGITAL RESEARCHTM PL/I-80 LANGUAGE MANUAL Copyright (c) 1980 Digital Research P.O. Box 579 801 Lighthouse Avenue Pacific Grove, CA 93950 (408) 649-3896 ~wx 910 360 5001 All Rights Reserved COPYRIGH"r Copyright (c) 1980 by Digital Research. All rights reserved. No part of this o~blication may be reproduced, transmitted, transcribed, stored 1n a retrieval system, or translated into any lanquaqe or computer lanquaqe, in any form or bv any means, electronic, mechanical, magnetic, optical, chemical, manual or otherwise, without the prior written permission of Digital Research, Post Office Box 579, Pacific Grove, California, 93950. ~his manual is, however, tutorial in nature. ~hus, permission is granted to reproduce or abstract the example programs shown in the enclosed figures for the ourposes of inclusion within the reader~s programs. Digital Research makes no representations or warranties with respect to the contents hereof and soecifically disclaims any implied warranties of merchantability or fitness for any particular putpose. Further, Digital Resea~ch reserves the right to revise this publication and to make changes from time to time in the content hereof without obligation of Digital Research to notify any person of such revision or changes. Ff1RADF.MARKS CP/M is a registered trademark of Digital Research. PL/I-80, ~P/M-80, RM.Ar., ~In, ZSID and "rEX are trademarks of Diqital Research. The "PL!I-80 Languaqe Manual" was prepared using the Digital Research "rEX ~ext formatter. ************************************ * Second Printing: December 1980 * ************************************ TABLE OF CONTENTS 1. BASIC STRUCTURE 3 1.1. The character set • 3 1.2. -

CONCURRENT DOS 8-16 INSTALLATION GUIDE Copyright
CONCURRENT DOS 8-16 INSTALLATION GUIDE Copyright 1985 Viasyn Corporation Hayward, CA 94545 r First Edition: December, 1984 Latest Printing: March, 1985 Document No: 15372 Filename: CDOS.MAN Version 3.1x DISCLAIMER - Viasyn Corporation makes no representations or warranties with respect to the contents hereof and specifically disclaims any implied warranties of merchantability or fitness for any particular purpose. Further, VIASYN reserves the right to revise this publication and to make any changes from time to time in the content hereof without obligation of VIASYN to notify any person of such revision or changes. Registered Trademarks: MDRIVE, Viasyn Corporation. IBM, Inter- national Business Machines, Inc. Televideo, Televideo, Inc. ' Zenith, Zenith Radio Corporation. Compound Trademarks: Concurrent DOS 8-16 is a compound trademark of Digital Research, Inc. and Viasyn Corporation. Trademarks: Concurrent CP/M, CP/M 80, Digital Research Inc. All rights reserved. No part of this publication may be reproduced or transmitted in any form, or by any means, without the written permission of VIASYN. Printed and assembled in the United States of America. TABLE OF CONTENTS 1. INTRODUCTION .......................................... 1 2. HARDWARE REQUIREMENTS .................................. 2-3 3. CONNECT, SET UP AND TEST YOUR SYSTEM .................... 3 Unpacking the System ........................................... 3 Unpacking the Floppy Disk Drives ................................ 4 Unpacking the Hard Disk Drive ....................... -

Ethics Guidelines and Collated Resources for Digital Research Statement of Ethical Practice Annexe
Ethics Guidelines and Collated Resources for Digital Research Statement of Ethical Practice Annexe www.britsoc.co.uk BSA Statement of Ethical Practice Annexe Contents Introduction 3 An Overview of Web Research Guidance 4 Thinking Through Ethics: Starting 6 with Exemptions and Moving to Dialogue The Ethics of Care & Situational Ethics 11 Ethics Guidelines and Collated Resources for Digital Research 2 BSA Statement of Ethical Practice Annexe Ethics Guidelines and Collated Resources for Digital Research The following guidelines and resources were created by Huw Davies (University of Oxford), Susan Halford (University of Southampton), Christine Hine (University of Surrey), Christina Hotz (University of Newcastle), Our position is that Wendy Martin (Brunel University) and Lisa Sugiura our inviolable duty (University of Portsmouth). of care to our research Working with digital platforms, networks, and data often raises many new ethical concerns and unanticipated dilemmas. participants, and to For example, we have to rethink concepts of informed consent and confidentiality (including anonymity), work with new, messy ourselves, should be and often confusing definitions of the private and the public, and resolve unprecedented tensions between the researcher reflexively applied and the researched. The British Sociological Association (BSA) using ‘situational ethics’ cannot provide detailed prescriptive guidelines for ethical practice across this complex and often volatile domain. We can however that can allow for offer some guiding principles, methods of thinking through these challenges, and specific examples (see our associated case discretion, flexibility studies) of how these work in practice. Our principles accord with other respected professional statutory and funding bodies and innovation. (including HEFCE, the ESRC, and the AoIR). -
Microsoft Windows for MS
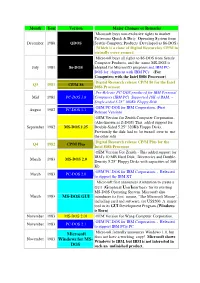
Month Year Version Major Changes or Remarks Microsoft buys non-exclusive rights to market Pattersons Quick & Dirty Operating System from December 1980 QDOS Seattle Computer Products (Developed as 86-DOS) (Which is a clone of Digital Researches C P/M in virtually every respect) Microsoft buys all rights to 86-DOS from Seattle Computer Products, and the name MS-DOS is July 1981 86-DOS adopted for Microsoft's purposes and IBM PC- DOS for shipment with IBM PCs (For Computers with the Intel 8086 Processor) Digital Research release CP/M 86 for the Intel Q3 1981 CP/M 86 8086 Processer Pre-Release PC-DOS produced for IBM Personal Mid 1981 PC-DOS 1.0 Computers (IBM PC) Supported 16K of RAM, ~ Single-sided 5.25" 160Kb Floppy Disk OEM PC-DOS for IBM Corporation. (First August 1982 PC-DOS 1.1 Release Version) OEM Version for Zenith Computer Corporation.. (Also known as Z-DOS) This added support for September 1982 MS-DOS 1.25 Double-Sided 5.25" 320Kb Floppy Disks. Previously the disk had to be turned over to use the other side Digital Research release CP/M Plus for the Q4 1982 CP/M Plus Intel 8086 Processer OEM Version For Zenith - This added support for IBM's 10 MB Hard Disk, Directories and Double- March 1983 MS-DOS 2.0 Density 5.25" Floppy Disks with capacities of 360 Kb OEM PC-DOS for IBM Corporation. - Released March 1983 PC-DOS 2.0 to support the IBM XT Microsoft first announces it intention to create a GUI (Graphical User Interface) for its existing MS-DOS Operating System. -

Digital Research Manager
DIGITAL RESEARCH MANAGER Role Digital Research Manager Division Communications, Education, Team Digital Research Networks and Technology Reports to Digital Research Lead Direct reports 2 Budgetary £200,000 + Resource SPSS subscription responsibility responsibility Contract Permanent, full-time Salary £35,000 - £45,000 About ISD ISD is a global counter-extremism organisation dedicated to powering solutions to hate and extremism. ISD has established itself as one of the leading global authorities on extremism and security. Combining research and analysis with government advisory work and programme delivery, ISD has been at the forefront of forging real-world, evidence-based responses to the challenges of integration, extremism and terrorism. As a global non-profit organisation with teams in London, Beirut, Toronto and Washington D.C., ISD enjoys strategic partnerships with the world’s leading technology companies and supports more than a dozen prominent governments and institutions in stemming the rise of violent extremism and hate speech. ISD’s research and policy team conducts qualitative and quantitative research on issues relating to terrorism, extremism and polarisation, including a significant body of work relating to the use of the internet and technology in these issue areas. This research feeds ongoing policy support to government, international institutions and the private sector to help challenge and counter extremism and threats to democracy and human rights. Role Purpose The manager will deliver research, project management,