Lab – Testing Network Connectivity with Ping and Traceroute
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Commands to Control Device
Commands to Control Device New OTA firmware upgrade command. To try it via over-the-air update, use these commands: > fwe > fwd B6FMA186 The board will reboot after the first command, this is normal. After the second command wait 1-3 minutes (seems like a long time). After it resets again, go back to BlueFruit and press "info" the software should be 3.0.186 The default wakeup interval is still 4 hours (14400 seconds). To configure a unit for a different wakeup interval: >wakt 600 (this would be 60*10 = 10 minutes) No beeps (Command to turn off the beeps) nvap 6 120000 14400000 15000 5000 0 223 1 3 Command to Restore Beeps nvap 6 120000 14400000 15000 5000 0 223 1 65535 Main Menu commands ---- SubMenus -------------------------- >i - I2C menu >l - Log menu >M - Modem menu ---- Device Control Cmds --------------- >D [n] - set debug level to [n] >info - Show device info >cota - CDMA OTA reprovision >svrm [name] - Set server main >nvmr - Non-volatile memory revert >t - show system uptime >rst - Hard reset ---- General Cmds ---------------------- >c [str] - Execute remote command manually >batq - Query battery state >slp - Go to sleep immediately >slpt [n] - Set sleep timeout to [n] seconds >wakt [n] - Set wake timeout to [n] hours >sus - Suspend immediately >sts - Show statistics and send to server >bt [n] - Bluetooth disable/enable: n=0/1 >dsms [n] - DebugSMS configure 0/1=disabled/enabled >wss [p] [s] - WiMM Server Send [p]ort, [s]tring >wsr - WiMM Server Recv ---- Pos/Log Cmds ---------------------- >pn - Position now >plc {i} {t} - Position log ctrl, [i]nterval, [t]ripId Stop Logging >pla {i} {t} - Position log auto, [i]nterval, [t]ripId >plb {n} - Position log batch [n] records >ple - Position log erase --- Alarm Cmds ------------------------ >alm [m] - Alarm mode: m=0/1/2: Off/On/FireNow ---- Firmware Cmds --------------------- >fwd [v] - Firmware Download (WIMM{v}.hex) >fwl {i} - Firmware Launch (i=0/1: ImgA/B) >fwe - Firmware Erase (ImgB) To change the alarm delay You must be running firmware 145 or later. -
Administering Unidata on UNIX Platforms
C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta UniData Administering UniData on UNIX Platforms UDT-720-ADMU-1 C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Notices Edition Publication date: July, 2008 Book number: UDT-720-ADMU-1 Product version: UniData 7.2 Copyright © Rocket Software, Inc. 1988-2010. All Rights Reserved. Trademarks The following trademarks appear in this publication: Trademark Trademark Owner Rocket Software™ Rocket Software, Inc. Dynamic Connect® Rocket Software, Inc. RedBack® Rocket Software, Inc. SystemBuilder™ Rocket Software, Inc. UniData® Rocket Software, Inc. UniVerse™ Rocket Software, Inc. U2™ Rocket Software, Inc. U2.NET™ Rocket Software, Inc. U2 Web Development Environment™ Rocket Software, Inc. wIntegrate® Rocket Software, Inc. Microsoft® .NET Microsoft Corporation Microsoft® Office Excel®, Outlook®, Word Microsoft Corporation Windows® Microsoft Corporation Windows® 7 Microsoft Corporation Windows Vista® Microsoft Corporation Java™ and all Java-based trademarks and logos Sun Microsystems, Inc. UNIX® X/Open Company Limited ii SB/XA Getting Started The above trademarks are property of the specified companies in the United States, other countries, or both. All other products or services mentioned in this document may be covered by the trademarks, service marks, or product names as designated by the companies who own or market them. License agreement This software and the associated documentation are proprietary and confidential to Rocket Software, Inc., are furnished under license, and may be used and copied only in accordance with the terms of such license and with the inclusion of the copyright notice. -
(2) G: 9 Timeout Error Layer —T
US007831732B1 (12) United States Patent (10) Patent No.: US 7,831,732 B1 Zilist et al. (45) Date of Patent: Nov. 9, 2010 (54) NETWORK CONNECTION UTILITY 6,018,724 A 1/2000 Arent 6,182,139 B1 1/2001 Brendel ...................... TO9,226 (75) Inventors: Ira Zilist, Chicago, IL (US); Daniel 6,338,094 B1* 1/2002 Scott et al. .................. 709/245 Reimann, Mt. Prospect, IL (US); Devin 6,393,581 B1 5, 2002 Friedman et al. 6,731,625 B1 5/2004 Eastep et al. Henkel, Chicago, IL (US); Gurpreet 6,742,015 B1 5/2004 Bowman-Amuah Singh, Clarendon Hills, IL (US) 7,082,454 B1* 7/2006 Gheith ....................... TO9,203 2002/0120800 A1* 8/2002 Sugahara et al. .. ... 710,260 (73) Assignee: Federal Reserve Bank of Chicago, 2004/0010546 A1* 1/2004 Kluget al. ............ ... 709,203 Chicago, IL (US) 2004/0192383 A1* 9, 2004 Zacks et al. ................. 455/557 (*) Notice: Subject to any disclaimer, the term of this patent is extended or adjusted under 35 * cited by examiner U.S.C. 154(b) by 1196 days. Primary Examiner Ario Etienne Assistant Examiner Avi Gold (21) Appl. No.: 11/192,991 (74) Attorney, Agent, or Firm—Brinks Hofer Gilson & Lione (22) Filed: Jul. 29, 2005 (57) ABSTRACT Int. C. (51) A system is disclosed for masking errors that may occur G06F 15/16 (2006.01) during a delay of a client connecting with a server on a (52) U.S. Cl. ........................ 709/237; 709/217; 709/219 network. A connection utility requests a connection with the (58) Field of Classification Search ................ -

RED HAT ENTERPRISE LINUX 5, 6, and 7 Common Administrative
RED HAT ENTERPRISE LINUX 5, 6, AND 7 SOFTWARE MANAGEMENT NETWORKING Common administrative commands TASK RHEL TASK RHEL yum install iptables and ip6tables 5 6 5 yum groupinstall /etc/sysconfig/ip*tables Install software iptables and ip6tables 1 Be aware of potential issues when using subscription-manager yum install 7 Configure firewall /etc/sysconfig/ip*tables 6 SYSTEM BASICS on Red Hat Enterprise Linux 5: https://access.redhat.com/ yum group install system-config-firewall solutions/129003. TASK RHEL yum info firewall-cmd 2 Subscription-manager is used for Satellite 6, Satellite 5.6 with 5 6 7 SAM and newer, and Red Hat’s CDN. yum groupinfo firewall-config /etc/sysconfig/rhn/systemid 5 3 RHN tools are deprecated on Red Hat Enterprise Linux 7. View software info /etc/hosts yum info 5 6 rhn_register should be used for Satellite server 5.6 and newer 7 /etc/resolv.conf /etc/sysconfig/rhn/systemid yum group info View subscription information 6 only. For details, see: Satellite 5.6 unable to register RHEL 7 Configure name subscription-manager identity client system due to rhn-setup package not included in Minimal resolution /etc/hosts installation (https://access.redhat.com/solutions/737373) Update software yum update 5 6 7 /etc/resolv.conf 7 subscription-manager identity 7 nmcli con mod rhn_register 5 Upgrade software yum upgrade 5 6 7 /etc/sysconfig/network 5 6 subscription-manager 1 Configure hostname hostnamectl rhn_register Configure software subscription-manager repos 5 6 7 /etc/hostname 7 rhnreg_ks 6 /etc/yum.repos.d/*.repo Configure -

Disk Clone Industrial
Disk Clone Industrial USER MANUAL Ver. 1.0.0 Updated: 9 June 2020 | Contents | ii Contents Legal Statement............................................................................... 4 Introduction......................................................................................4 Cloning Data.................................................................................................................................... 4 Erasing Confidential Data..................................................................................................................5 Disk Clone Overview.......................................................................6 System Requirements....................................................................................................................... 7 Software Licensing........................................................................................................................... 7 Software Updates............................................................................................................................. 8 Getting Started.................................................................................9 Disk Clone Installation and Distribution.......................................................................................... 12 Launching and initial Configuration..................................................................................................12 Navigating Disk Clone.....................................................................................................................14 -
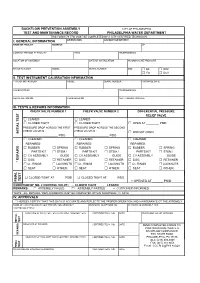
BFP Test Form
BACKFLOW PREVENTION ASSEMBLY CITY OF PHILADELPHIA TEST AND MAINTENANCE RECORD PHILADELPHIA WATER DEPARTMENT THIS FORM (79-770) MUST BE COMPLETED BY A CITY CERTIFIED TECHNICIAN I. GENERAL INFORMATION ORIENTATION ACCOUNT OR METER # NAME OF FACILITY ADDRESS ZIP CONTACT PERSON AT FACILITY TITLE TELEPHONE NO. LOCATION OF ASSEMBLY DATE OF INSTALLATION INCOMING LINE PRESSURE MANUFACTURER MODEL SERIAL NUMBER SIZE □ DS □ RPZ □ FS □ DCV II. TEST INSTRUMENT CALIBRATION INFORMATION TYPE OF INSTRUMENT MODEL SERIAL NUMBER PURCHASE DATE CALIBRATED BY TELEPHONE NO. REGISTRATION NO. CALIBRATED ON NEXT CALIBRATION DUE III. TESTS & REPAIRS INFORMATION CHECK VALVE NUMBER 1 CHECK VALVE NUMBER 2 DIFFERENTIAL PRESSURE RELIEF VALVE □ LEAKED □ LEAKED □ CLOSED TIGHT □ CLOSED TIGHT □ OPEN AT ________ PSID PRESSURE DROP ACROSS THE FIRST PRESSURE DROP ACROSS THE SECOND CHECK VALVE IS : CHECK VALVE IS : INITIAL TEST INITIAL □ DID NOT OPEN ______________________ PSID ______________________ PSID □ CLEANED □ CLEANED □ CLEANED REPAIRED: REPAIRED: REPAIRED: □ RUBBER □ SPRING □ RUBBER □ SPRING □ RUBBER □ SPRING PARTS KIT □ STEM / PARTS KIT □ STEM / PARTS KIT □ STEM / □ CV ASSEMBLY GUIDE □ CV ASSEMBLY GUIDE □ CV ASSEMBLY GUIDE □ DISC □ RETAINER □ DISC □ RETAINER □ DISC □ RETAINER * REPAIRS □ O - RINGS □ LOCKNUTS □ O - RINGS □ LOCKNUTS □ O - RINGS □ LOCKNUTS □ SEAT □ OTHER: □ SEAT □ OTHER: □ SEAT □ OTHER: □ CLOSED TIGHT AT ______ PSID □ CLOSED TIGHT AT ______ PSID TEST FINAL FINAL □ OPENED AT ______ PSID CONDITION OF NO. 2 CONTROL VALVE : □ CLOSED TIGHT □ LEAKED REMARKS : □ ASSEMBLY FAILED □ ASSEMBLY PASSED □ CUSTOMER INFORMED *NOTE : ALL REPAIRS / REPLACEMENTS MUST BE COMPLETED WITHIN FOURTEEN (14) DAYS IV. APPROVALS * I HEREBY CERTIFY THAT THIS DATA IS ACCURATE AND REFLECTS THE PROPER OPERATION AND MAINTENANCE OT THE ASSEMBLY NAME OF CERTIFIED BACKFLOW PREVENTION ASSEMBLY BUSINESS TELEPHONE NO. -

Don't Trust Traceroute (Completely)
Don’t Trust Traceroute (Completely) Pietro Marchetta, Valerio Persico, Ethan Katz-Bassett Antonio Pescapé University of Southern California, CA, USA University of Napoli Federico II, Italy [email protected] {pietro.marchetta,valerio.persico,pescape}@unina.it ABSTRACT In this work, we propose a methodology based on the alias resolu- tion process to demonstrate that the IP level view of the route pro- vided by traceroute may be a poor representation of the real router- level route followed by the traffic. More precisely, we show how the traceroute output can lead one to (i) inaccurately reconstruct the route by overestimating the load balancers along the paths toward the destination and (ii) erroneously infer routing changes. Categories and Subject Descriptors C.2.1 [Computer-communication networks]: Network Architec- ture and Design—Network topology (a) Traceroute reports two addresses at the 8-th hop. The common interpretation is that the 7-th hop is splitting the traffic along two Keywords different forwarding paths (case 1); another explanation is that the 8- th hop is an RFC compliant router using multiple interfaces to reply Internet topology; Traceroute; IP alias resolution; IP to Router to the source (case 2). mapping 1 1. INTRODUCTION 0.8 Operators and researchers rely on traceroute to measure routes and they assume that, if traceroute returns different IPs at a given 0.6 hop, it indicates different paths. However, this is not always the case. Although state-of-the-art implementations of traceroute al- 0.4 low to trace all the paths -

Webserver Cannot Be Started / No Web Access EAGLE20 / Eagleone
Knowledgebase > Products > Classic Firewalls > Webserver cannot be started / No web access EAGLE20 / EAGLEOne Webserver cannot be started / No web access EAGLE20 / EAGLEOne - 2018-02-09 - Classic Firewalls At the first startup of a brand new EAGLE or at the first startup after “clear certificates” the web certificates are generated. Affected products are EAGLE20 and EAGLEOne in rel. 05.3.00. If the power is removed during the certificate generation is in progress the webserver cannot be started and therefore no web access is possible. The cli command 'show login' displays the following output: !(Hirschmann EAGLE One) #show login Login parameters ---------------- Access per SSH..........................enabled SSH Access port number..................22 DSA Fingerprint for SSH.................""xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:ab:ab:ab:ab:0f "" RSA Fingerprint for SSH.................""xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:5e "" Access per Web (HTTPS)..................disabled Web Access port number (HTTPS)..........443 SNMP version 1..........................disabled SNMP version 2..........................disabled SNMP port number........................161 SNMP over HTTPS tunneling...............disabled RADIUS auth. of SNMP v3 local users.....disabled Inactivity timeout Web (minutes)........5 Inactivity timeout serial (minutes).....5 Inactivity timeout SSH (minutes)........5 Login prompt............................""Hirschmann EAGLE One"" Login banner............................"""" 23: 2013-01-01 01:00:01 [tCfgMgrTask, CRITICAL, WEB-S, 0x02080014] Web Server - start of web server failed 24: 2013-01-01 01:00:01 [tCfgMgrTask, ERROR, WEB-S, 0x02080028] Web Server - directory for https server certificate could not be created Possible solutions: 1. Reformat the flash file system in sysMon1 and to put the operating firmware on the device again. -

SLC Console Manager User Guide Available At
SLC™ Console Manager User Guide SLC8 SLC16 SLC32 SLC48 Part Number 900-449 Revision J July 2014 Copyright and Trademark © 2014 Lantronix, Inc. All rights reserved. No part of the contents of this book may be transmitted or reproduced in any form or by any means without the written permission of Lantronix. Lantronix is a registered trademark of Lantronix, Inc. in the United States and other countries. SLC, SLB, SLP, SLM, Detector and Spider are trademarks of Lantronix, Inc. Windows and Internet Explorer are registered trademarks of Microsoft Corporation. Firefox is a registered trademark of the Mozilla Foundation. Chrome is a trademark of Google, Inc. All other trademarks and trade names are the property of their respective holders. Warranty For details on the Lantronix warranty replacement policy, please go to our web site at http://www.lantronix.com/support/warranty. Open Source Software Some applications are Open Source software licensed under the Berkeley Software Distribution (BSD) license or the GNU General Public License (GPL) as published by the Free Software Foundation (FSF). Redistribution or incorporation of BSD or GPL licensed software into hosts other than this product must be done under their terms. A machine readable copy of the corresponding portions of GPL licensed source code may be available at the cost of distribution. Such Open Source Software is distributed WITHOUT ANY WARRANTY, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. See the GPL and BSD for details. A copy of the licenses is available from Lantronix. The GNU General Public License is available at http://www.gnu.org/licenses/. -

Your Performance Task Summary Explanation
Lab Report: 11.2.5 Manage Files Your Performance Your Score: 0 of 3 (0%) Pass Status: Not Passed Elapsed Time: 6 seconds Required Score: 100% Task Summary Actions you were required to perform: In Compress the D:\Graphics folderHide Details Set the Compressed attribute Apply the changes to all folders and files In Hide the D:\Finances folder In Set Read-only on filesHide Details Set read-only on 2017report.xlsx Set read-only on 2018report.xlsx Do not set read-only for the 2019report.xlsx file Explanation In this lab, your task is to complete the following: Compress the D:\Graphics folder and all of its contents. Hide the D:\Finances folder. Make the following files Read-only: D:\Finances\2017report.xlsx D:\Finances\2018report.xlsx Complete this lab as follows: 1. Compress a folder as follows: a. From the taskbar, open File Explorer. b. Maximize the window for easier viewing. c. In the left pane, expand This PC. d. Select Data (D:). e. Right-click Graphics and select Properties. f. On the General tab, select Advanced. g. Select Compress contents to save disk space. h. Click OK. i. Click OK. j. Make sure Apply changes to this folder, subfolders and files is selected. k. Click OK. 2. Hide a folder as follows: a. Right-click Finances and select Properties. b. Select Hidden. c. Click OK. 3. Set files to Read-only as follows: a. Double-click Finances to view its contents. b. Right-click 2017report.xlsx and select Properties. c. Select Read-only. d. Click OK. e. -
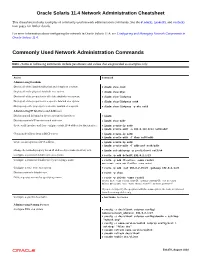
Oracle® Solaris 11.4 Network Administration Cheatsheet
Oracle Solaris 11.4 Network Administration Cheatsheet This cheatsheet includes examples of commonly used network administration commands. See the dladm(8), ipadm(8), and route(8) man pages for further details. For more information about configuring the network in Oracle Solaris 11.4, see Configuring and Managing Network Components in Oracle Solaris 11.4. Commonly Used Network Administration Commands Note - Some of following commands include parameters and values that are provided as examples only. Action Command Administering Datalinks Display all of the datalinks (physical and virtual) on a system. # dladm show-link Display all of the physical datalinks on a system. # dladm show-phys Display all of the properties for all of the datalinks on a system. # dladm show-linkprop Display all of the properties for a specific datalink on a system. # dladm show-linkprop net0 Display a specific property for a specific datalink on a system. # dladm show-linkprop -p mtu net0 Administering IP Interfaces and Addresses Display general information about a system's IP interfaces. # ipadm Display a system's IP interfaces and addresses. # ipadm show-addr Create an IP interface and then configure a static IPv4 address for that interface. # ipadm create-ip net0 # ipadm create-addr -a 203.0.113.0/24 net0/addr Obtain an IP address from a DHCP server. # ipadm create-ip net0 # ipadm create-addr -T dhcp net0/addr Create an auto-generated IPv6 address. # ipadm create-ip net0 # ipadm create-addr -T addrconf net0/addr Change the netmask property for an IP address object name (net3/v4) to 8. # ipadm set-addrprop -p prefixlen=8 net3/v4 Configure a persistent default route on a system. -

File Permissions Do Not Restrict Root
Filesystem Security 1 General Principles • Files and folders are managed • A file handle provides an by the operating system opaque identifier for a • Applications, including shells, file/folder access files through an API • File operations • Access control entry (ACE) – Open file: returns file handle – Allow/deny a certain type of – Read/write/execute file access to a file/folder by – Close file: invalidates file user/group handle • Access control list (ACL) • Hierarchical file organization – Collection of ACEs for a – Tree (Windows) file/folder – DAG (Linux) 2 Discretionary Access Control (DAC) • Users can protect what they own – The owner may grant access to others – The owner may define the type of access (read/write/execute) given to others • DAC is the standard model used in operating systems • Mandatory Access Control (MAC) – Alternative model not covered in this lecture – Multiple levels of security for users and documents – Read down and write up principles 3 Closed vs. Open Policy Closed policy Open Policy – Also called “default secure” • Deny Tom read access to “foo” • Give Tom read access to “foo” • Deny Bob r/w access to “bar” • Give Bob r/w access to “bar • Tom: I would like to read “foo” • Tom: I would like to read “foo” – Access denied – Access allowed • Tom: I would like to read “bar” • Tom: I would like to read “bar” – Access allowed – Access denied 4 Closed Policy with Negative Authorizations and Deny Priority • Give Tom r/w access to “bar” • Deny Tom write access to “bar” • Tom: I would like to read “bar” – Access