Analysis of Internet Download Manager for Collection of Digital Forensic Artefacts
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

How Can I Get a Free Internet Download Manager
How can i get a free internet download manager Download Internet Download Manager for Windows now from Softonic: % safe and virus free. More than downloads this month. Download Internet. Internet Download Manager gives you the tools to download many types of files from the Internet and organize them as you see fit. You can categorize each file. Hello Guyz, IDM Showing Fake Serial Number Message? No Problem. You can easily fix this video I will. Hi Friends:D In This Tutorial i will show you the best and the easiest way to register your IDm for Free and its. Internet Download Manager is a task management tool that makes it easier to download multiple files at a time. The tool can increase download. internet download manager with crack has a basic GUI which makes it simple to utilize or on the off chance that you incline toward you can. Internet Download Manager Free Download setup in single direct link. Download your files with very high speed. IDM is best download. Internet Download Manager (IDM) is one of top download managers for any PC with Windows, Linux, etc. It has a great importance and known as fastest. Internet Download Manager is a tool for increasing download speeds by up to 5 times, and for resuming, scheduling, and organizing downloads. Free Download Manager Is A Fast And Functional Internet Download Manager For All Types Of Downloads. I am one of the users of Internet Download Manager and it has made my life more organized and trouble free. It works on operating systems such as Windows7. -

1 Acquiring Instrumental Sub-Competence by Building Do-It
Acquiring instrumental sub-competence by building do-it-yourself corpora for business translation Daniel Gallego Hernández University of Alicante Abstract: The aim of this paper is to share our experience in teaching how to build DIY corpora in business translation courses. Business and finance texts have a significant presence on the web and there is free software for Windows that can assist the translator in the different stages of the process of building DIY corpora from web resources. The model we propose in our courses takes into account these two realities and develops some of the sub-competencies that translation competence consists of, especially the instrumental one, which concerns the use of information and communication technologies and documentation resources. This model not only allows to develop translators’ instrumental sub-competence but also to introduce for the first time those who are not familiar with command-line interfaces to the basics of corpora building as a translation resource. 1. Introduction: need of developing instrumental sub-competence Translation and Interpreting degrees in Spain are essentially based on developing a set of sub- competencies that graduates must have acquired during their courses. PACTE translation competence provides a common reference framework for the definition of these sub- competencies: 1) bilingual sub-competence, related to the procedural knowledge (pragmatics, sociolinguistics, textuality, grammar and lexis) required to communicate in two languages; 2) extra-linguistic sub-competence, -

Latest Version of Free Download Manager Download Free Download Manager for PC
latest version of free download manager Download Free Download Manager for PC. Help & Info about Free Download Manager for windows. How does Free Download Manager work? How does Free Download Manager differ from the download manager already included in the operating system? What sets Free Download Manager apart from other apps? Is it difficult to use? Is it really free? Is Free Download Manager safe? Will my operating system support Free Download Manager? How do I download Free Download Manager? Is Free Download Manager compatible with mobile devices? Will Free Download Manager be compatible with my browser? Explore Apps. Articles about Free Download Manager. Laws concerning the use of this software vary from country to country. We do not encourage or condone the use of this program if it is in violation of these laws. About Us. Legal. Users. Softonic in: The name and logo of Softonic are registered trademarks of SOFTONIC INTERNATIONAL S.A. Copyright SOFTONIC INTERNATIONAL S.A. © 1997-2021 - All rights reserved. In Softonic we scan all the files hosted on our platform to assess and avoid any potential harm for your device. Our team performs checks each time a new file is uploaded and periodically reviews files to confirm or update their status. This comprehensive process allows us to set a status for any downloadable file as follows: It’s extremely likely that this software program is clean. What does this mean? We have scanned the file and URLs associated with this software program in more than 50 of the world's leading antivirus services; no possible threat has been detected. -

Download Instructions—Portal
Download instructions These instructions are recommended to download big files. How to download and verify files from downloads.gvsig.org • H ow to download files • G NU/Linux Systems • MacO S X Systems • Windows Systems • H ow to validate the downloaded files How to download files The files distributed on this site can be downloaded using different access protocols, the ones currently available are FTP, HTTP and RSYNC. The base URL of the site for the different protocols is: • ftp://gvsig.org/ • http://downloads.gvsig.org/ • r sync://gvsig.org/downloads/ To download files using the first two protocols is recommended to use client programs able to resume partial downloads, as it is usual to have transfer interruptions when downloading big files like DVD images. There are multiple free (and multi platform) programs to download files using different protocols (in our case we are interested in FTP and HTTP), from them we can highlight curl (http://curl.haxx.se/) and wget (http://www.gnu.org/software/wget/) from the command line ones and Free Download Manager from the GUI ones (this one is only for Windows systems). The curl program is included in MacOS X and is available for almost all GNU/Linux distributions. It can be downloaded in source code or in binary form for different operating systems from the project web site. The wget program is also included in almost all GNU/Linux distributions and its source code or binaries of the program for different systems can be downloaded from this page. Next we will explain how to download files from the most usual operating systems using the programs referenced earlier: • G NU/Linux Systems • MacO S X Systems • Windows Systems The use of rsync (available from the URL http://samba.org/rsync/) it is left as an exercise for the reader, we will only said that it is advised to use the --partial option to avoid problems when there transfers are interrupted. -

Software Sites-2010 ALL FULL
Software Sites-2010 ALL FULL related:http://www.brothersoft.com/ related:http://download.cnet.com/ related:http://www.soft32.com/ related:http://www.freedownloadscenter.com/ related:http://www.filehippo.com/ related:http://www.softpedia.com/ related:http://www.dl4all.com/ related:http://www.topdownloads.net/ related:http://downloads.zdnet.com/ related:http://www.freedownloadmanager.org/ related:http://www.tucows.com/ related:http://www.download3k.com/ related:http://www.bestfreewaredownload.com/ related:http://www.download3000.com/ related:http://www.download3k.com/ related:http://www.123-free-download.com/ related:http://www.download3k.com/ related:http://www.123-free-download.com/ related:http://www.topshareware.com/ related:http://www.freedownloadsplace.com/ related:http://www.freedownloadsplace.com/ related:http://www.download32.com/ related:http://www.sharewareplaza.com/ related:http://www.freewarefiles.com/ related:http://majorgeeks.com/ related:http://www.top4download.com/ http://www.brothersoft.com/ http://download.cnet.com/ http://www.soft32.com/ http://www.freedownloadscenter.com/ http://www.filehippo.com/ http://www.softpedia.com/ http://www.dl4all.com/ http://www.topdownloads.net/ http://downloads.zdnet.com/ http://www.freedownloadmanager.org/ http://www.tucows.com/ http://www.download3k.com/ http://www.bestfreewaredownload.com/ http://www.download3000.com/ http://www.download3k.com/ http://www.123-free-download.com/ http://www.download3k.com/ http://www.123-free-download.com/ http://www.topshareware.com/ http://www.freedownloadsplace.com/ http://www.freedownloadsplace.com/ http://www.download32.com/ http://www.sharewareplaza.com/ http://www.freewarefiles.com/ http://majorgeeks.com/ http://www.top4download.com/ 1. http://download.cnet.com/ 2. http://www.soft32.com/ 3. http://www.freedownloadscenter.com/ 4. -
Internet Download Manager File Named for Website
internet download manager file named for website How to Install IDM Integration Module Extension in Google Chrome? Internet Download Manager, or as IDM as many call it has been around for a long time. It is amongst the best download manager for Windows operating systems that is available out there. The default download manager of browsers like Chrome, Firefox, etc. sometimes does not provide the maximum possible download speed due to reasons like the lack of multiple download bands, connection restrictions, etc. On the other hand, download managers such as IDM, FDM can accelerate the slow downloading speeds and provide the maximum possible download speed on your Internet. Moreover, these also provide resume support downloading. With the help of the IDM Integration module extension, Google Chrome can transfer downloads to IDM directly without the need to open the download manager manually. What is IDM Integration Module for Chrome? It is an extension for Google Chrome that transfers download from Chrome to Internet Download Manager for any files or entire webpages. IDM Chrome extension can download videos from several video hosting websites as well. Check-list before trying another method. Check #1 Ensure Download Capture by IDM. Before trying ways to install IDM module extension, make sure to check the settings of IDM to ensure that the integration for Chrome is enabled. In any case, if it is disabled, IDM will not capture downloads from Chrome. 1. Head to Settings > General Tab. There appears a list of browsers with which the IDM integration module is enabled to “ Capture downloads from the following browsers” . -

Ant Download Manager (Antdm) V.2.3.2
English Ant Download Manager (AntDM) v.2.4.0 Some of the contents in this manual may differ from the software, as software development continues. User Guide 2021 Table of Contents Overview ....................................................................................................................................................4 System Requirements .........................................................................................................................5 Installation ..................................................................................................................................................6 Uninstall .............................................................................................................................................11 Premium Link Generators (Debrids) .......................................................................................................12 Torrents ....................................................................................................................................................14 Browser Integration ..................................................................................................................................15 Google Chrome .................................................................................................................................16 Chromium Clones ........................................................................................................................17 Mozilla Firefox ....................................................................................................................................18 -
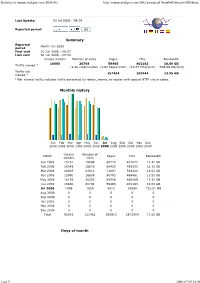
Stat-Manuscritdepot
Statistics of manuscritdepot.com (2008-06) http://manuscritdepot.com:2082/awstats.pl?month=06&year=2008&out... Last Update: 03 Jul 2008 - 09:34 Reported period: OK Summary Reported Month Jun 2008 period First visit 01 Jun 2008 - 00:07 Last visit 30 Jun 2008 - 23:56 Unique visitors Number of visits Pages Hits Bandwidth 16660 20704 59465 401163 10.00 GB Traffic viewed * (1.24 visits/visitor) (2.87 Pages/Visit) (19.37 Hits/Visit) (506.56 KB/Visit) Traffic not 157434 163944 12.95 GB viewed * * Not viewed traffic includes traffic generated by robots, worms, or replies with special HTTP status codes. Monthly history Jan Feb Mar Apr May Jun Jul Aug Sep Oct Nov Dec 2008 2008 2008 2008 2008 2008 2008 2008 2008 2008 2008 2008 Unique Number of Month Pages Hits Bandwidth visitors visits Jan 2008 15151 19598 60173 471872 11.42 GB Feb 2008 15048 18876 60425 493553 12.13 GB Mar 2008 16965 21813 71097 548328 14.52 GB Apr 2008 15090 18609 60793 469461 11.55 GB May 2008 16193 20233 64348 460489 11.32 GB Jun 2008 16660 20704 59465 401163 10.00 GB Jul 2008 1438 1629 4612 28088 722.51 MB Aug 200800000 Sep 200800000 Oct 200800000 Nov 200800000 Dec 200800000 Total 96545 121462 380913 2872954 71.63 GB Days of month 1 sur 9 2008-07-03 14:58 Statistics of manuscritdepot.com (2008-06) http://manuscritdepot.com:2082/awstats.pl?month=06&year=2008&out... 01 02 03 04 05 06 07 08 09 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 Average Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun Jun -

Internet Music Download Manager
Internet music download manager From Ida Software: Internet Music Downloader is a simple program for safely finding songs online and downloading them for free so you can enjoy them any. Internet Download Manager gives you the tools to download many types of files from the Internet and organize them as you see fit. You can. A download manager full of tools for music and movie lovers to choose between this and Ninja Internet Download Manager for the top spot. Download free music with idm. Psyco4ctiVe Easiest way to download music using Internet Download. It's a smart and fast internet download manager for Windows and Mac OS X. AnyMusic is the best music downloader that empowers you to discover. Download Accelerator Manager (DAM) is an all-in-one downloader, that empowers you to download Internet files and save Web videos, music, from sites like. Free Download Manager latest version: Efficiently manage your downloads. Free Download Manager is exactly what it says it is - an application that looks after your downlo Manager Internet & Network · Download Managers. Internet Download Manager, free and safe download. Internet Download Manager latest version: IDM manages and accelerates downloads, even with Windows. Internet Download Manager is the choice of many, when it comes to increasing tool that enables you to search, access and download over million songs. You don't need a download manager to download software or music or whatever The browser integration works with Internet Explorer, Chrome, and Firefox. Internet Download Manager is a tool for increasing download speeds by up to 5 times, and for resuming, scheduling, and organizing downloads. -

Free Software to Download Audio from Youtube Videos
free software to download audio from youtube videos How to Download Audio from YouTube Free? 2 Excellent Ways! Need to download audio from YouTube video? YouTube converters including MiniTool uTube Downloader and online YouTube converters can download music from YouTube. MiniTool offers the best YouTube to MP3 converter to let you easily rip audio from video without losing quality. Quick Navigation : YouTube is an online video streaming website with an estimated 30 million visitors per day. You find an awesome song, audiobook, or podcast on YouTube and you want to save it to listen to it on your computer, in the car, or on the go even without an internet connection. Now, what should I do? How do I extract audio from a YouTube video? Is It Easy to Download Audio from YouTube. Various YouTube video downloaders out here enable you to download audio from YouTube. But, some contain adware and some may charge a fee if you need to download more YouTube videos. Related article : How to download YouTube videos. Here, if you want to extract audio from YouTube easily and quickly, the following programs would be very helpful for you. Read through the different choices and pick the right one to download music from YouTube. Download Audio from YouTube with The Best YouTube Downloader. Whether you want to download YouTube videos or want to rip audio from YouTube, MiniTool uTube Downloader is the best tool for you because it offers fast conversion speed and friendly user interface. What MiniTool uTube Downloader Can Do For You. MiniTool YouTube Downloader is a free and no ads YouTube converter that doesn't include any bundled software. -
Download Full Youtube Playlist Free Youtube Playlist Downloader - 22 Best Youtube Playlist Downloader Free Download
download full youtube playlist free YouTube Playlist Downloader - 22 Best YouTube Playlist Downloader Free Download. Get top best 22 YouTube playlist downloader to easily download YouTube playlist to Mac or Windows. Steven Wilson. Nov 12,2019 • Filed to: YouTube Downloader • Proven solutions. Want to download the whole YouTube playlist for offline watching? To do this, you need a YouTube playlist downloader free . You might find several YouTube playlist downloader free online programs allowing you to download YouTube playlists from your Chrome, Firefox or Safari briwser. And some YouTube playlist downloader tools may support Mac, Windows or Ubuntu OS. Since the YouTube playlist download process is long, it would be advisable to analyze both free YouTube playlist downloader and premium versions, and get that which suits your needs. Here we help you to pick up the best YouTube playlist downloader. Part 1. Best 10 YouTube Playlist Downloader for Free Part 2. YouTube Playlist Downloader for Chrome and Firefox Part 3. Top 10 YouTube Playlist Downloader Online. Part 1. Best 10 YouTube Playlist Downloader for Free. iTube HD Video Downloader. With a simple and good-looking interface, you can use iTube YouTube Playlist Downloader to easily download YouTube videos, playlists, channels and user contents to your computer for free. iTube YouTube Playlist Downloader is by far the most complete and easy video downloader for Mac and Windows. This YouTube Downloader enables you a "Playlist" download button to download the whole YouTube playlist easily. And you can also directly download YouTube playlist to MP3 or other video and audio formats. iTube HD Video Downloader - Best YouTube Playlist Downloader Free. -

Counteract HPS Applications Plugin Configuration Guide
CounterACT® HPS Applications Plugin Configuration Guide Version 2.1.4 CounterACT® HPS Applications Plugin Configuration Guide Table of Contents About the HPS Applications Plugin ............................................................... 3 Requirements .............................................................................................. 3 Installation .................................................................................................. 4 Configuration ............................................................................................... 4 Working with Endpoint Information ............................................................. 4 Detect Windows Versions .............................................................................. 5 Detect Third-Party Applications ...................................................................... 6 Manage Third-Party Applications .................................................................... 8 Kill Cloud Storage on Windows ................................................................... 8 Kill Instant Messaging on Windows ............................................................. 9 Kill Peer-to-Peer on Windows ..................................................................... 9 Start Antivirus on Windows ...................................................................... 10 Update Antivirus on Windows ................................................................... 10 Appendix A: Endpoint Applications Detected by CounterACT .....................