Counteract HPS Applications Plugin Configuration Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
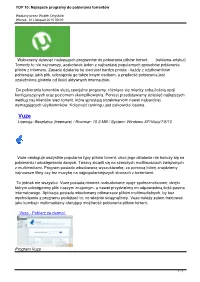
Najlepsze Programy Do Pobierania Torrentów
TOP 10: Najlepsze programy do pobierania torrentów Wpisany przez Wojtek Onyśków Wtorek, 10 Listopad 2015 09:00 Wybieramy dziesięć najlepszych programów do pobierania plików torrent. {reklama-artykul} Torrenty to nie najnowszy, aczkolwiek jeden z najbardziej popularnych sposobów pobierania plików z internetu. Zasada działania tej sieci jest bardzo prosta - każdy z użytkowników pobierając jakiś plik, udostępnia go także innym osobom, a prędkość pobierania jest uzależniona głównie od ilości aktywnych internautów. Do pobierania torrentów służą specjalne programy, różniące się między sobą ilością opcji konfiguracyjnych oraz poziomem skomplikowania. Poniżej przedstawiamy dziesięć najlepszych według nas klientów sieci torrent, które sprostają oczekiwaniom nawet najbardziej wymagających użytkowników. Kolejność rankingu jest całkowicie losowa. Vuze Licencja: Bezpłatna (freeware) / Rozmiar: 10.3 MB / System: Windows XP/Vista/7/8/10 Vuze obsługuje wszystkie popularne typy plików torrent, choć jego działanie nie kończy się na pobieraniu i udostępnianiu danych. Twórcy skupili się na szerszych możliwościach związanych z multimediami. Program posiada wbudowaną wyszukiwarkę, za pomocą której znajdziemy najnowsze filmy czy też muzykę na najpopularniejszych stronach z torrentami. To jednak nie wszystko. Vuze posiada również rozbudowane opcje społecznościowe, dzięki którym udostępnimy pliki naszym znajomym, a nawet przydzielimy im odpowiednią ilość pasma internetowego. Aplikacja posiada wbudowany odtwarzacz plików multimedialnych, by bez wychodzenia z programu podejrzeć to, co właśnie ściągnęliśmy. Vuze należy zatem traktować jako kombajn multimedialny oferujący możliwość pobierania plików torrent. Vuze - Pobierz za darmo! Program Vuze 1 / 7 TOP 10: Najlepsze programy do pobierania torrentów Wpisany przez Wojtek Onyśków Wtorek, 10 Listopad 2015 09:00 uTorrent Licencja: Bezpłatna (freeware) / Rozmiar: 1.73 MB / System: Windows XP/Vista/7/8/10 uTorrent to jeden z najpopularniejszych programów do pobierania plików torrent. -

How Can I Get a Free Internet Download Manager
How can i get a free internet download manager Download Internet Download Manager for Windows now from Softonic: % safe and virus free. More than downloads this month. Download Internet. Internet Download Manager gives you the tools to download many types of files from the Internet and organize them as you see fit. You can categorize each file. Hello Guyz, IDM Showing Fake Serial Number Message? No Problem. You can easily fix this video I will. Hi Friends:D In This Tutorial i will show you the best and the easiest way to register your IDm for Free and its. Internet Download Manager is a task management tool that makes it easier to download multiple files at a time. The tool can increase download. internet download manager with crack has a basic GUI which makes it simple to utilize or on the off chance that you incline toward you can. Internet Download Manager Free Download setup in single direct link. Download your files with very high speed. IDM is best download. Internet Download Manager (IDM) is one of top download managers for any PC with Windows, Linux, etc. It has a great importance and known as fastest. Internet Download Manager is a tool for increasing download speeds by up to 5 times, and for resuming, scheduling, and organizing downloads. Free Download Manager Is A Fast And Functional Internet Download Manager For All Types Of Downloads. I am one of the users of Internet Download Manager and it has made my life more organized and trouble free. It works on operating systems such as Windows7. -

1 Acquiring Instrumental Sub-Competence by Building Do-It
Acquiring instrumental sub-competence by building do-it-yourself corpora for business translation Daniel Gallego Hernández University of Alicante Abstract: The aim of this paper is to share our experience in teaching how to build DIY corpora in business translation courses. Business and finance texts have a significant presence on the web and there is free software for Windows that can assist the translator in the different stages of the process of building DIY corpora from web resources. The model we propose in our courses takes into account these two realities and develops some of the sub-competencies that translation competence consists of, especially the instrumental one, which concerns the use of information and communication technologies and documentation resources. This model not only allows to develop translators’ instrumental sub-competence but also to introduce for the first time those who are not familiar with command-line interfaces to the basics of corpora building as a translation resource. 1. Introduction: need of developing instrumental sub-competence Translation and Interpreting degrees in Spain are essentially based on developing a set of sub- competencies that graduates must have acquired during their courses. PACTE translation competence provides a common reference framework for the definition of these sub- competencies: 1) bilingual sub-competence, related to the procedural knowledge (pragmatics, sociolinguistics, textuality, grammar and lexis) required to communicate in two languages; 2) extra-linguistic sub-competence, -

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

The New England College of Optometry Peer to Peer (P2P) Policy
The New England College of Optometry Peer To Peer (P2P) Policy Created in Compliance with the Higher Education Opportunity Act (HEOA) Peer-to-Peer File Sharing Requirements Overview: Peer-to-peer (P2P) file sharing applications are used to connect a computer directly to other computers in order to transfer files between the systems. Sometimes these applications are used to transfer copyrighted materials such as music and movies. Examples of P2P applications are BitTorrent, Gnutella, eMule, Ares Galaxy, Megaupload, Azureus, PPStream, Pando, Ares, Fileguri, Kugoo. Of these applications, BitTorrent has value in the scientific community. For purposes of this policy, The New England College of Optometry (College) refers to the College and its affiliate New England Eye Institute, Inc. Compliance: In order to comply with both the intent of the College’s Copyright Policy, the Digital Millennium Copyright Act (DMCA) and with the Higher Education Opportunity Act’s (HEOA) file sharing requirements, all P2P file sharing applications are to be blocked at the firewall to prevent illegal downloading as well as to preserve the network bandwidth so that the College internet access is neither compromised nor diminished. Starting in September 2010, the College IT Department will block all well-known P2P ports on the firewall at the application level. If your work requires the use of BitTorrent or another program, an exception may be made as outlined below. The College will audit network usage/activity reports to determine if there is unauthorized P2P activity; the IT Department does random spot checks for new P2P programs every 72 hours and immediately blocks new and emerging P2P networks at the firewall. -

Cisco SCA BB Protocol Reference Guide
Cisco Service Control Application for Broadband Protocol Reference Guide Protocol Pack #60 August 02, 2018 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

Étude De La Pratique Du Téléchargement Légal Et Illégal Sur Internet
Étude de la pratique du téléchargement légal et illégal sur Internet Travail de Bachelor réalisé en vue de l’obtention du Bachelor HES par : Julien MARIETHOZ Conseiller au travail de Bachelor : (David Billard, Professeur HES) Genève, le 12 mai 2010 Haute École de Gestion de Genève (HEG-GE) Informatique de Gestion Déclaration Ce travail de Bachelor est réalisé dans le cadre de l’examen final de la Haute école de gestion de Genève, en vue de l’obtention du titre d’ « informaticien de gestion ». L’étudiant accepte, le cas échéant, la clause de confidentialité. L'utilisation des conclusions et recommandations formulées dans le travail de Bachelor, sans préjuger de leur valeur, n'engage ni la responsabilité de l'auteur, ni celle du conseiller au travail de Bachelor, du juré et de la HEG. « J’atteste avoir réalisé seul le présent travail, sans avoir utilisé des sources autres que celles citées dans la bibliographie. » Fait à Genève, le 12 mai 2010 Julien MARIETHOZ Étude de la pratique du téléchargement légal et illégal sur Internet MARIETHOZ, Julien iv Remerciements Dans le cadre de la réalisation de ce travail, je tiens à remercier tous ceux qui ont pu y contribuer directement ou indirectement : M. David Billard pour son encadrement et ses conseils. Carole, ma femme, qui a pris le temps de s’occuper de notre petit qui est né le jour après la date de début officiel, me permettant de me concentrer sur ce travail. Tous ceux qui ont pris le temps de répondre à mon questionnaire, en me fournissant les données nécessaires à ce rapport. -

Latest Version of Free Download Manager Download Free Download Manager for PC
latest version of free download manager Download Free Download Manager for PC. Help & Info about Free Download Manager for windows. How does Free Download Manager work? How does Free Download Manager differ from the download manager already included in the operating system? What sets Free Download Manager apart from other apps? Is it difficult to use? Is it really free? Is Free Download Manager safe? Will my operating system support Free Download Manager? How do I download Free Download Manager? Is Free Download Manager compatible with mobile devices? Will Free Download Manager be compatible with my browser? Explore Apps. Articles about Free Download Manager. Laws concerning the use of this software vary from country to country. We do not encourage or condone the use of this program if it is in violation of these laws. About Us. Legal. Users. Softonic in: The name and logo of Softonic are registered trademarks of SOFTONIC INTERNATIONAL S.A. Copyright SOFTONIC INTERNATIONAL S.A. © 1997-2021 - All rights reserved. In Softonic we scan all the files hosted on our platform to assess and avoid any potential harm for your device. Our team performs checks each time a new file is uploaded and periodically reviews files to confirm or update their status. This comprehensive process allows us to set a status for any downloadable file as follows: It’s extremely likely that this software program is clean. What does this mean? We have scanned the file and URLs associated with this software program in more than 50 of the world's leading antivirus services; no possible threat has been detected. -

Free Ares 3.0
Free ares 3.0 Ares, free and safe download. Ares latest version: Fast and unlimited P2P file sharing. Ares is a great P2P client Developer. Aresgalaxy | More Programs (3). Ares free download. Licence Free OS Support Windows XP, Windows Vista, Horizon Innovative Xbox modding tool. Ares Gold free download. Get new version of Ares Gold. A free file-sharing program ✓ Free ✓ Updated ✓ Download now. Ares is a P2P file exchange program that, with the passing of time, has established itself as one of the best Ares screenshot 3 Free v MB. Ares. Ares is a free open source file sharing program that enables users to share any digital file including images, audio, video, software, documents. Ares is a free open source file sharing program that enables users to share any digital file including images, audio, video, software, documents, etc. You may. Download Ares Galaxy for Windows. Ares Galaxy is an open source Peer to Peer software which lets you share images, documents, software, audio and video. Download Ares Galaxy for free. A free peer-to-peer (P2P) BitTorrent file sharing client. Ares Galaxy is a free, open source BitTorrent and chat. Ares is a peer to peer file sharing program that enables users to share 0; 3 star. 0; 2 star. 1; 1 star. 0. All Versions. out of 58 votes. 5 star. Download Ares Ares. August, 23rd - % Safe - Open Source. Free Download. ( MB) Safe & Secure Ares Date released: 07 Oct Download Ares Plus Program for the titular P2P network that gives you faster downloads. AresGalaxy is a free open source Filesharing Bittorrent p2p Client with a powerful search, works behind firewalls. -

Faster Interconnects for Next-Generation Data Centers 2
Faster Interconnects for Next- Generation Data Centers Summary Insight With the data deluge washing over today’s data centers, IT Author: Jean S. Bozman infrastructure benefits from Introduction faster interconnects. Faster storage requires faster A wave of change is sweeping over the data center – and a multi- networks. Even more terabyte data deluge is coming along with it. This rapid change is being generated by new sources of data coming from Cloud performance can be achieved by Computing, Mobility, Social Media and Big Data/Analytics. All of using iSER, a maturing these workloads must now be supported, along with transactional standard for extending iSCSI processing, enterprise applications and data warehouses. with RDMA (Remote Direct For many IT professionals, the new demands are causing a “rethink” Memory Access). Using iSER, of their data-transfer infrastructure. The Fibre Channel high-performing storage can be interconnects and slower Ethernet links are showing their age – and connected to fast Ethernet links the aging links must be updated or replaced as quickly as possible. via iSCSI, speeding data Otherwise, these slow links will be “bottlenecks” that slow down the transfers from the network to business or organization that depends on that IT infrastructure. servers and storage systems. This process of data center transformation requires thoughtful These technologies can be used planning – but IT organizations cannot afford to wait too long, or together to replace aging high- performance of mission-critical applications and databases will speed interconnects, such as suffer. Fibre Channel links and older Ethernet links. Flash Storage and Your Network Many technologies will need to become more efficient in the process, including the storage systems that house the data – and send it to the compute engines for processing. -

Vysoké Učení Technické V Brně Detekcia Seedboxov V Sieti Bittorrent
VYSOKÉ UČENÍ TECHNICKÉ V BRNĚ BRNO UNIVERSITY OF TECHNOLOGY FAKULTA INFORMAČNÍCH TECHNOLOGIÍ FACULTY OF INFORMATION TECHNOLOGY ÚSTAV INFORMAČNÍCH SYSTÉMŮ DEPARTMENT OF INFORMATION SYSTEMS DETEKCIA SEEDBOXOV V SIETI BITTORRENT DETECTION OF SEEDBOXES INBITTORRENT NETWORK BAKALÁŘSKÁ PRÁCE BACHELOR’S THESIS AUTOR PRÁCE MARTIN GRNÁČ AUTHOR VEDOUCÍ PRÁCE Ing. LIBOR POLČÁK, Ph.D. SUPERVISOR BRNO 2018 Abstrakt Bakalárska práca sa venuje problematike sledovania a detekcie seedboxov v sieti BitTorrent za pomoci technológie netflow. V teoretickej časti je predstavená a popísaná architektúra P2P, základy a kľúčové pojmy architektúry BitTorrent a teoretická definícia seedboxu. Taktiež sú tu rozobrané metódy pomocou ktorých sa dá detekovať sieťová komunikácia a ďalej je uvedená analýza seedboxov v sieti a hľadanie ich charakteristík. Na základe týchto znalostí a sledovaní je navrhnutá sada nástrojov, ktoré napomáhajú ich detekcií. V praktickej časti je predstavená implementácia týchto nástrojov a výsledky ich testovania. Abstract Bachelor’s thesis is focused on issues with monitoring and detection of seedboxes in Bit- Torrent network with help of netflow technology. In the theoretical part of this thesis is introduced and described P2P architecture, basics and key terms of BitTorrent architec- ture and theoretical definition of seedbox. There are also described specific methods which can be used for detection of network communication and next there is described process of seedbox analysis in network and process of finding its characteristics. On base of this kno- wledge and observations is designed a set of tools,which help with detection of seedboxes. In the practical part of this work is presented implementation of these tools and results of testing these tools. Kľúčové slová BitTorrent, seedbox, detekcia, netflow, analýza, sieťová prevádzka, P2P, netflow Keywords BitTorrent, seedbox, detection, netflow, analysis, network traffic, P2P, netflow Citácia GRNÁČ, Martin. -

Simulacijski Alati I Njihova Ograničenja Pri Analizi I Unapređenju Rada Mreža Istovrsnih Entiteta
SVEUČILIŠTE U ZAGREBU FAKULTET ORGANIZACIJE I INFORMATIKE VARAŽDIN Tedo Vrbanec SIMULACIJSKI ALATI I NJIHOVA OGRANIČENJA PRI ANALIZI I UNAPREĐENJU RADA MREŽA ISTOVRSNIH ENTITETA MAGISTARSKI RAD Varaždin, 2010. PODACI O MAGISTARSKOM RADU I. AUTOR Ime i prezime Tedo Vrbanec Datum i mjesto rođenja 7. travanj 1969., Čakovec Naziv fakulteta i datum diplomiranja Fakultet organizacije i informatike, 10. listopad 2001. Sadašnje zaposlenje Učiteljski fakultet Zagreb – Odsjek u Čakovcu II. MAGISTARSKI RAD Simulacijski alati i njihova ograničenja pri analizi i Naslov unapređenju rada mreža istovrsnih entiteta Broj stranica, slika, tablica, priloga, XIV + 181 + XXXVIII stranica, 53 slike, 18 tablica, 3 bibliografskih podataka priloga, 288 bibliografskih podataka Znanstveno područje, smjer i disciplina iz koje Područje: Informacijske znanosti je postignut akademski stupanj Smjer: Informacijski sustavi Mentor Prof. dr. sc. Željko Hutinski Sumentor Prof. dr. sc. Vesna Dušak Fakultet na kojem je rad obranjen Fakultet organizacije i informatike Varaždin Oznaka i redni broj rada III. OCJENA I OBRANA Datum prihvaćanja teme od Znanstveno- 17. lipanj 2008. nastavnog vijeća Datum predaje rada 9. travanj 2010. Datum sjednice ZNV-a na kojoj je prihvaćena 18. svibanj 2010. pozitivna ocjena rada Prof. dr. sc. Neven Vrček, predsjednik Sastav Povjerenstva koje je rad ocijenilo Prof. dr. sc. Željko Hutinski, mentor Prof. dr. sc. Vesna Dušak, sumentor Datum obrane rada 1. lipanj 2010. Prof. dr. sc. Neven Vrček, predsjednik Sastav Povjerenstva pred kojim je rad obranjen Prof. dr. sc. Željko Hutinski, mentor Prof. dr. sc. Vesna Dušak, sumentor Datum promocije SVEUČILIŠTE U ZAGREBU FAKULTET ORGANIZACIJE I INFORMATIKE VARAŽDIN POSLIJEDIPLOMSKI ZNANSTVENI STUDIJ INFORMACIJSKIH ZNANOSTI SMJER STUDIJA: INFORMACIJSKI SUSTAVI Tedo Vrbanec Broj indeksa: P-802/2001 SIMULACIJSKI ALATI I NJIHOVA OGRANIČENJA PRI ANALIZI I UNAPREĐENJU RADA MREŽA ISTOVRSNIH ENTITETA MAGISTARSKI RAD Mentor: Prof.