Me and My Research
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Building Blocks for Tomorrow's Mobile App Store
Building Blocks for Tomorrow’s Mobile App Store by Justin G. Manweiler Department of Computer Science Duke University Date: Approved: Romit Roy Choudhury, Supervisor Jeffrey S. Chase Landon P. Cox Victor Bahl Dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the Department of Computer Science in the Graduate School of Duke University 2012 Abstract (0984) Building Blocks for Tomorrow’s Mobile App Store by Justin G. Manweiler Department of Computer Science Duke University Date: Approved: Romit Roy Choudhury, Supervisor Jeffrey S. Chase Landon P. Cox Victor Bahl An abstract of a dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the Department of Computer Science in the Graduate School of Duke University 2012 Copyright c 2012 by Justin G. Manweiler All rights reserved Abstract In our homes and in the enterprise, in our leisure and in our professions, mobile computing is no longer merely “exciting;” it is becoming an essential, ubiquitous tool of the modern world. New and innovative mobile applications continue to inform, entertain, and surprise users. But, to make the daily use of mobile technologies more gratifying and worthwhile, we must move forward with new levels of sophistication. The Mobile App Stores of the future must be built on stronger foundations. This dissertation considers a broad view of the challenges and intuitions behind a diverse selection of such new primitives. Some of these primitives will mitigate exist- ing and fundamental challenges of mobile computing, especially relating to wireless communication. Others will take an application-driven approach, being designed to serve a novel purpose, and be adapted to the unique and varied challenges from their disparate domains. -

Annual Report
ANNUAL REPORT 2019FISCAL YEAR ACM, the Association for Computing Machinery, is an international scientific and educational organization dedicated to advancing the arts, sciences, and applications of information technology. Letter from the President It’s been quite an eventful year and challenges posed by evolving technology. for ACM. While this annual Education has always been at the foundation of exercise allows us a moment ACM, as reflected in two recent curriculum efforts. First, “ACM’s mission to celebrate some of the many the ACM Task Force on Data Science issued “Comput- hinges on successes and achievements ing Competencies for Undergraduate Data Science Cur- creating a the Association has realized ricula.” The guidelines lay out the computing-specific over the past year, it is also an competencies that should be included when other community that opportunity to focus on new academic departments offer programs in data science encompasses and innovative ways to ensure at the undergraduate level. Second, building on the all who work in ACM remains a vibrant global success of our recent guidelines for 4-year cybersecu- the computing resource for the computing community. rity curricula, the ACM Committee for Computing Edu- ACM’s mission hinges on creating a community cation in Community Colleges created a related cur- and technology that encompasses all who work in the computing and riculum targeted at two-year programs, “Cybersecurity arena” technology arena. This year, ACM established a new Di- Curricular Guidance for Associate-Degree Programs.” versity and Inclusion Council to identify ways to create The following pages offer a sampling of the many environments that are welcoming to new perspectives ACM events and accomplishments that occurred over and will attract an even broader membership from the past fiscal year, none of which would have been around the world. -

Victor Bahl Microsoft Corporation
Victor Bahl Microsoft Corporation SIGCOMM MobiArch 2007, August 2007 Source: Victoria Poncini, MS IT ~7, 000 Access Points ~65,000 XP & Vista Clients December 2006 ~40,000 connections/day ~35,000 handheld devices 100% 80% 39,6% 37,3% 42,2% 45,8% 47,1% 60% 40% 39,8% 39,7% 34,2% 44,2% 35,3% 20% 18,1% 20,1% 16,2% 17,6% 22,9% 0% Worldwide Americas w/o PS Puget Sound EMEA APJ Very SfSatisfied SSfSomewhat Satisfied SfSomewhat Dissatisfied or Very Dissati fied 2 Victor Bahl Microsoft’s IT Dept. logs several hundred complaints / month 70% calls are about client connectivity issues (e. g. ping-ponging between APs) 30% (and growing) are about performance problems due to interference End-users complain about Lack of RF coverage, performance & reliability Connectivity & authentication problems Network administrators worry about Providing adequate coverage, performance Security and unauthorized access Corporations spend lots of $$ on WLAN infrastructure WLAN hardware business to reach $2.6 billion in 2007. (Forester 2006) Heavy VC funding in this area (e.g. AirTight $36M in the last 16 months) 3 Victor Bahl 4 Victor Bahl FY05 Cost Element View Functional View Breakdown People 72% Applications 60% Data & Voice 16% App Development (29%) App Support (31%) Hardware 5% Facilities 5% Infrastructure 40% Software* 2% Network (14%) * 5% If MS software were included Data Center (7%) Employee Services (5%) Voice (5%) 30% Helpdesk (5%) New Increases Security (3%) Capability value 45% New 70% Capability Sustaining & Running Decreases Existing maintenance 55% Capability delivery Existing Capability 5 Victor Bahl Timeline HotNets’05 , MobiSys’ 06, NSDI ‘07 ACM CCR ’ 06 MobiCom’ 04 MobiSys’ 06 6 Victor Bahl Heterogeneous world Multiple technologies: 802. -

(Cloudlets/Edges) for Mobile Computing
emergence of micro datacenter (cloudlets/edges) for mobile computing Victor Bahl Wednesday, May 13, 2015 what if our computers could see? Microsoft’s’s HoloLens who? where? what? Video credits: Matthai Philipose Microsoft Research seeing is for real MSR’s Glimpse project vision is demanding recognition using deep neural networks face1 [1] scene [2] object2[3] memory (floats) 103M 76M 138M compute 1.00 GFLOPs 2.54 GFLOPs 30.9 GFLOPs accuracy 97% 51% 94% (top 5) 1: 4000 people; 2: 1000 objects from ImageNet, top 5: one of your top 5 matches human-level accuracy, heavy resource demands … offloading computation is highly desirable [1] Y. Taigman et al. DeepFace: Closing the Gap to Human-Level Performance in Face Verification. In CVPR 2014. (Facebook) [2] B. Zhou et al. Learning deep features for scene recognition using places database. In NIPS, 2014. [MIT, Princeton, ..] [3] K. Simonyan & A. Zisserman. Very deep convolutional networks for large-scale image recognition. 2014 [Google, Oxford] under review recognition: server versus mobile road sign recognition1 stage Mobile server Spedup (Samsung Galaxy Nexus) (i7, 3.6GHz, 4-core) (server:mobile) detection 2353 +/- 242.4 ms 110 +/- 32.1 ms ~15-16X feature extraction 1327.7 +/- 102.4 ms 69 +/- 15.2 ms ~18X recognition2 162.1 +/- 73.2 ms 11 +/- 1.6 ms ~14X Energy used 11.32 Joules 0.54 Joules ~21X 1convolution neural networks 2classifying 1000 objects with 4096 features using a linear SVM how long does it take to reach the cloud? 3g networks 4g-lte networks T-Mobile 450ms AT&T 350ms MobiSys 2010 -

Building Aggressively Duty-Cycled Platforms to Achieve Energy Efficiency
UNIVERSITY OF CALIFORNIA, SAN DIEGO Building Aggressively Duty-Cycled Platforms to Achieve Energy Efficiency A dissertation submitted in partial satisfaction of the requirements for the degree Doctor of Philosophy in Computer Science (Computer Engineering) by Yuvraj Agarwal Committee in charge: Rajesh Gupta, Chair Paramvir Bahl William Hodgkiss Stefan Savage Alex Snoeren Geoff Voelker 2009 Copyright Yuvraj Agarwal, 2009 All rights reserved. The dissertation of Yuvraj Agarwal is approved, and it is acceptable in quality and form for publication on mi- crofilm and electronically: Chair University of California, San Diego 2009 iii DEDICATION To Dadi, Shyam Babaji, Papa and Ma. iv TABLE OF CONTENTS Signature Page .................................. iii Dedication ..................................... iv Table of Contents ................................. v List of Figures .................................. ix List of Tables ................................... xi Acknowledgements ................................ xii Vita and Publications .............................. xv Abstract of the Dissertation ........................... xvi Chapter 1 Introduction ............................ 1 1.1 Reducing the Energy Consumption of Computing Devices 3 1.2 Using Collaboration to Aggressively Duty-Cycle Platforms 5 1.3 Contributions ........................ 7 1.4 Organization ......................... 8 Chapter 2 Background and Related Work .................. 9 2.1 Mobile Platforms ...................... 9 2.2 Power and Energy ...................... 12 2.2.1 Measuring Power and Energy Consumption .... 13 2.3 Related Work ........................ 14 2.3.1 Power Management in Mobile Devices ....... 14 2.3.2 Power Management in Laptops and Desktop PCs 17 Chapter 3 Radio Collaboration - Cellular and LAN Data Radios ..... 20 3.1 Overview of a VoIP Deployment .............. 23 3.2 Alternatives to VoIP over Wi-Fi Radios .......... 24 3.2.1 Cellular Data vs. Wi-Fi .............. 25 3.2.2 Smartphone Power Measurements ......... 28 3.3 Cell2Notify Architecture ................. -

CVPR), July, 1996
Vishal Misra Professor [email protected] Department of Computer Science http://www.cs.columbia.edu/∼misra/ Columbia University Work : (212) 939 7061 New York, NY 10027-7003 EDUCATION University of Massachusetts Amherst Amherst, MA Ph.D. in Electrical Engineering May 2000 Advisor: Wei-Bo Gong University of Massachusetts Amherst Amherst, MA M.S. in Electrical Engineering May, 1996 Advisor: Lewis E. Franks Indian Institute of Technology Mumbai, India Bachelor of Technology in Electrical Engineering 1992 EXPERIENCE Columbia University New York, NY Professor, Dept. of Computer Science Spring 2016 - Present Vice Chair, Dept. of Computer Science July 2009 - June 2012 Associate Professor, Dept. of Computer Science Spring 2006 - Fall 2015 Assistant Professor, Dept. of Computer Science Fall 2001 - Fall 2005 Google New York, NY Visiting Scientist July 2017 - Present Infinio Inc. Cambridge, MA Founder and CEO June 2011 - October 2012 Founder and CTO October 2012 - June 2014 Founder and Chief Scientist June 2014 - March 2017 University of Massachusetts Amherst, MA Post-Doctoral Research Associate, Computer Networks Research Group 2000-Fall 2001 Research Assistant, Complex Systems Modeling and Control Lab 1996-2000 Verizon (formerly Nynex Science & Technology) White Plains , NY Student Intern Summer 1994, 1995 CricInfo (http://espncricinfo.com) London, UK Founding CTO 1993-1998 Indian Institute of Technology Mumbai, India Research Associate 1992-93 Vishal Misra page 2 AWARDS • Distinguished Alumnus Award, IIT Bombay, 2019 • Elected ACM Fellow, 2018 • Elected IEEE Fellow, 2016 • Elected Chair, ACM Sigmetrics, 2015-2017 • Outstanding Young Alumni Award, UMass-Amherst College of Engineering, 2014 • Elected Vice Chair, ACM Sigmetrics, 2011-2015 • Elected to the Board of Directors, ACM Sigmetrics, 2007-2011 • Elected Member, IFIP Working Group 7.3 on Computer Performance Modeling and Analysis, 2005. -

Mobile Edge Computing Empowers Internet of Things
IEICE TRANS. ??, VOL.Exx–??, NO.xx XXXX 200x 1 INVITED PAPER Mobile Edge Computing Empowers Internet of Things Nirwan ANSARIya) and Xiang SUNyb), SUMMARY In this paper, we propose a Mobile Edge Internet of Things lored for IoT devices is critical to empowering the current (MEIoT) architecture by leveraging the fiber-wireless access technology, IoT system. In addition, only providing interconnections to the cloudlet concept, and the software defined networking framework. The share raw data among IoT devices is not enough to gain the MEIoT architecture brings computing and storage resources close to Internet of Things (IoT) devices in order to speed up IoT data sharing and analytics. insight behind the big IoT data; the insight is more valuable Specifically, the IoT devices (belonging to the same user) are associated to for the society as a whole. Thus, it is beneficial to provision a specific proxy Virtual Machine (VM) in the nearby cloudlet. The proxy the IoT system with a comprehensive cognitive capability VM stores and analyzes the IoT data (generated by its IoT devices) in real- such that high-level knowledge can be extracted from the time. Moreover, we introduce the semantic and social IoT technology in the context of MEIoT to solve the interoperability and inefficient access big IoT raw data streams by applying various types of data control problem in the IoT system. In addition, we propose two dynamic mining and machine learning methods [3]. The data center proxy VM migration methods to minimize the end-to-end delay between infrastructure has been demonstrated to provision resources proxy VMs and their IoT devices and to minimize the total on-grid energy flexibly and efficiently [4]; meanwhile, various parallel com- consumption of the cloudlets, respectively. -

CHOICE – the World's First Public Area Wifi Hot-Spot Network
An Overview of the CHOICE Network Victor Bahl http://research.microsoft.com/~bahl December 18, 2000 Demos you will see today CHOICE – Phase 1 Demo 1 – Network advertisement, user authentication, access enforcement, security, accounting, and mobility management CHOICE – Phase 2 Location based personalized services Demo 2 – Location based buddy list Demo 3 – Mall On-Sale Service Victor Bahl December 18, 2000 Broadband Wireless Internet Access in Public Places The CHOICE Network - Phase 1 Global authentication, Local access, First-hop security, Accounting, Differentiated Service, Mobility management & Auto-configuration The Choice Network Project: Motivation Enable high speed wireless internet access in public places (e.g. hotels, conferences, malls, airports) WLAN much faster than 3G cell phones Design, implement, and deploy a network service that grants secure, customized, and accountable network access to possibly unknown users A system that protects users and network operators supports different business models e.g. free intranet and/or fee-based internet access makes access seamless and robust Multiple authentication schemes for first-time users Bootstrap network accesses for mobile clients Scale to large network settings Tolerate system failures Victor Bahl December 18, 2000 Review: Existing Access Mechanisms Mostly built for enterprise networks Layer-2 Filtering MAC based filtering – is on its way out Shared key encryption – is being used today …but key management is broken Several Problems: Network can be compromised -
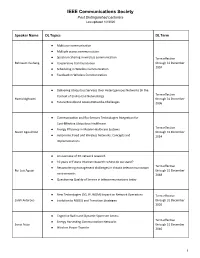
Past Distinguished Lecturers Last Updated 1/2/2020
IEEE Communications Society Past Distinguished Lecturers Last updated 1/2/2020 Speaker Name DL Topics DL Term ● Multiuser communication ● Multiple access communication ● Spectrum Sharing in wireless communication Term effective Behnaam Aazhang ● Cooperative Communication through 31 December 2007 ● Scheduling in Wireless Communication ● Feedback in Wireless Communication ● Delivering Ubiquitous Services Over Heterogeneous Networks (In the Term effective Context of End-to-End Networking) Hamid Aghvami through 31 December ● Future Broadband Access Networks-Challenges 2006 ● Communication and Bio-Sensors Technologies Integration for Cost-Effective Ubiquitous Healthcare Term effective ● Energy Efficiency in Mobile Healthcare Systems Nazim Agoulmine through 31 December ● Autonomic Fixed and Wireless Networks: Concepts and 2014 Implementations ● An overview of 5G network research ● 10 years of Future Internet research: where do we stand? Term effective ● Reconsidering management challenges in chaotic telecommunication Rui Luis Aguiar through 31 December environments 2018 ● Questioning Quality of Service in telecommunications today ● New Technologies (3G, IP, WDM) Impact on Network Operations Term effective Salah Aidarous ● Evolution to NGOSS and Transition Strategies through 31 December 2002 ● Cognitive Radio and Dynamic Spectrum Access Term effective ● Energy Harvesting Communication Networks Sonia Aissa through 31 December ● Wireless Power Transfer 2016 1 IEEE Communications Society Past Distinguished Lecturers Last updated 1/2/2020 ● Fundamentals -

Synthesizing Plausible Infrastructure Configurations for Evaluating Edge
Synthesizing Plausible Infrastructure Configurations for Evaluating Edge Computing Systems Thomas Rausch Clemens Lachner Pantelis A. Frangoudis Philipp Raith TU Wien TU Wien TU Wien TU Wien Schahram Dustdar TU Wien Abstract evaluating edge computing systems under different conditions This paper proposes a framework for synthesizing infrastruc- and parameters. We examine the commonalities of emerging ture configurations for evaluating edge computing systems application scenarios that leverage edge infrastructure in the under different conditions. There are a number of tools to sim- entire compute continuum, to elevate common concepts into ulate or emulate edge systems, and while they typically pro- our framework domain. The result is a set of primitives and vide ways of modeling infrastructure and network topologies, building blocks for generating edge infrastructure configura- they lack reusable building blocks common to edge scenarios. tions and topologies. Based on data we have gathered for the Consequently, most edge computing systems evaluations to scenarios, we identify a parameter space for these building this date rely on either highly application-specific testbeds, or blocks, to give researchers the ability to vary different aspects abstract scenarios and abstract infrastructure configurations. of the generated topology, s.t. the cluster topologies remain We analyze four existing or emerging edge infrastructure sce- plausible extensions of the original scenarios grounded in narios, from which we elicit common concepts. The scenarios empirical data. We demonstrate the applicability of our open- serve as input to synthesize plausible infrastructure config- source tool, ether [32], by synthesizing configurations for urations, that are parameterizable in cluster density, device selected scenarios, and showing how the synthetic configura- heterogeneity, and network topology. -

White Space Networking, Summer School in Networking, Bangalore, India (June 2009)
Victor Bahl Joint work with Paula Boyd, Ranveer Chandra, Paul Garnett, Thomas Moscibroda, and MSR Interns (Rohan Murty, George Nychis, Xiaohui Wang , Yuan Yuan) WS • Work with regulators to nail • Identify & solve technical down sensible problems specifications • Build proof-of-concept • Help achieve world-wide prototypes harmonization • Help policy teams with • Engage with silicon vendors recommendations based & system integrators on solid science •Build community mindshare Strategy Research & Policy Product Business • Gather requirements & nail down specs • Help create industry • Develop business Standards models • Harden research code, • Identify Applications & develop & test on Services Windows • Build alliances for greater connectivity Version 1: Ad hoc networking in white spaces 700 MHz operation, TV sensing capability, one-to-one opportunistic networking, control-channel based MAC, varying channel width operation, multi-radio design, design analysis through simulations Version 2: Infrastructure based networking (WhiteFi) White Space freq. operation, TV sensing Capability, limited microphone sensing, one-to-many opportunistic networking, Wi-Fi MAC, time-domain analysis (SIFT), demo-ed at Microsoft events (e.g. TechFest 2009) Version 3: Campus-wide backbone network (WhiteFi with Geolocation) All of V2 + geolocation DB, Windows network stack improvements, bridging between Wi-Fi and WhiteFi, coverage in MS Shuttles FCC Experimental License (Granted: July 6, 2009) Centered at (47.6442N, 122.1330W) Goal: Deploy a white space network -
Telecommunications Reclaimed: a Hands-On Guide to Networking Communities
1 2 3 TELECOMMUNICATIONS RECLAIMED: A HANDS-ON GUIDE TO NETWORKING COMMUNITIES MÉLANIE DULONG DE ROSNAY & FÉLIX TRÉGUER (EDS.) 4 Acknowledgements The research presented in this book, the writing residency and the editing process were funded by the Horizon 2020 programme of the European Union (Grant Number 688768), project netCommons Network Infrastructure as Commons (netcommons.eu). The production of this book was co-funded by the European project netCommons (see above) and published with the additional support of the Internet Society (Jane Coffin) and the Association for Progressive Communications (Flavia Fascendini and Carlos Rey- Moreno). ISBN 978-92-95113-15-2 Published by Internet Society Printed in the USA 2019 Disclaimer: The views expressed in this book are not necessarily the views of the Internet Society. This book is licensed under a Creative Commons Attribution- ShareAlike 4.0 available at International license www.creativecommons.org/ licenses/by-sa/4.0/. You can download this book at www.netcommons.eu/ telecommunications-reclaimed 5 Editors Illustrations and layout Mélanie Dulong de Rosnay, CNRS Sarah Viguer Félix Tréguer, CNRS Booksprint facilitator Authors Andreas Wichmann Panayotis Antoniadis, NetHood Ileana Apostol, NetHood Peer review Virginie Aubrée, University of Trento, Christian Fuchs, University of University of Paris Nanterre Westminster Adam Burns, free2air Renato Lo Cigno, University of Trento, Mélanie Dulong de Rosnay, CNRS University of Brescia Maria Michalis, University of Bruno Spiquel, SCANI Westminster