Informed Repairing of Integer Overflows
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Integer Linear Programs
20 ________________________________________________________________________________________________ Integer Linear Programs Many linear programming problems require certain variables to have whole number, or integer, values. Such a requirement arises naturally when the variables represent enti- ties like packages or people that can not be fractionally divided — at least, not in a mean- ingful way for the situation being modeled. Integer variables also play a role in formulat- ing equation systems that model logical conditions, as we will show later in this chapter. In some situations, the optimization techniques described in previous chapters are suf- ficient to find an integer solution. An integer optimal solution is guaranteed for certain network linear programs, as explained in Section 15.5. Even where there is no guarantee, a linear programming solver may happen to find an integer optimal solution for the par- ticular instances of a model in which you are interested. This happened in the solution of the multicommodity transportation model (Figure 4-1) for the particular data that we specified (Figure 4-2). Even if you do not obtain an integer solution from the solver, chances are good that you’ll get a solution in which most of the variables lie at integer values. Specifically, many solvers are able to return an ‘‘extreme’’ solution in which the number of variables not lying at their bounds is at most the number of constraints. If the bounds are integral, all of the variables at their bounds will have integer values; and if the rest of the data is integral, many of the remaining variables may turn out to be integers, too. -

Understanding Integer Overflow in C/C++
Appeared in Proceedings of the 34th International Conference on Software Engineering (ICSE), Zurich, Switzerland, June 2012. Understanding Integer Overflow in C/C++ Will Dietz,∗ Peng Li,y John Regehr,y and Vikram Adve∗ ∗Department of Computer Science University of Illinois at Urbana-Champaign fwdietz2,[email protected] ySchool of Computing University of Utah fpeterlee,[email protected] Abstract—Integer overflow bugs in C and C++ programs Detecting integer overflows is relatively straightforward are difficult to track down and may lead to fatal errors or by using a modified compiler to insert runtime checks. exploitable vulnerabilities. Although a number of tools for However, reliable detection of overflow errors is surprisingly finding these bugs exist, the situation is complicated because not all overflows are bugs. Better tools need to be constructed— difficult because overflow behaviors are not always bugs. but a thorough understanding of the issues behind these errors The low-level nature of C and C++ means that bit- and does not yet exist. We developed IOC, a dynamic checking tool byte-level manipulation of objects is commonplace; the line for integer overflows, and used it to conduct the first detailed between mathematical and bit-level operations can often be empirical study of the prevalence and patterns of occurrence quite blurry. Wraparound behavior using unsigned integers of integer overflows in C and C++ code. Our results show that intentional uses of wraparound behaviors are more common is legal and well-defined, and there are code idioms that than is widely believed; for example, there are over 200 deliberately use it. -

Collecting Vulnerable Source Code from Open-Source Repositories for Dataset Generation
applied sciences Article Collecting Vulnerable Source Code from Open-Source Repositories for Dataset Generation Razvan Raducu * , Gonzalo Esteban , Francisco J. Rodríguez Lera and Camino Fernández Grupo de Robótica, Universidad de León. Avenida Jesuitas, s/n, 24007 León, Spain; [email protected] (G.E.); [email protected] (F.J.R.L.); [email protected] (C.F.) * Correspondence: [email protected] Received:29 December 2019; Accepted: 7 February 2020; Published: 13 February 2020 Abstract: Different Machine Learning techniques to detect software vulnerabilities have emerged in scientific and industrial scenarios. Different actors in these scenarios aim to develop algorithms for predicting security threats without requiring human intervention. However, these algorithms require data-driven engines based on the processing of huge amounts of data, known as datasets. This paper introduces the SonarCloud Vulnerable Code Prospector for C (SVCP4C). This tool aims to collect vulnerable source code from open source repositories linked to SonarCloud, an online tool that performs static analysis and tags the potentially vulnerable code. The tool provides a set of tagged files suitable for extracting features and creating training datasets for Machine Learning algorithms. This study presents a descriptive analysis of these files and overviews current status of C vulnerabilities, specifically buffer overflow, in the reviewed public repositories. Keywords: vulnerability; sonarcloud; bot; source code; repository; buffer overflow 1. Introduction In November 1988 the Internet suffered what is publicly known as “the first successful buffer overflow exploitation”. The exploit took advantage of the absence of buffer range-checking in one of the functions implemented in the fingerd daemon [1,2]. Even though it is considered to be the first exploited buffer overflow, different researchers had been working on buffer overflow for years. -

RICH: Automatically Protecting Against Integer-Based Vulnerabilities
RICH: Automatically Protecting Against Integer-Based Vulnerabilities David Brumley, Tzi-cker Chiueh, Robert Johnson [email protected], [email protected], [email protected] Huijia Lin, Dawn Song [email protected], [email protected] Abstract against integer-based attacks. Integer bugs appear because programmers do not antici- We present the design and implementation of RICH pate the semantics of C operations. The C99 standard [16] (Run-time Integer CHecking), a tool for efficiently detecting defines about a dozen rules governinghow integer types can integer-based attacks against C programs at run time. C be cast or promoted. The standard allows several common integer bugs, a popular avenue of attack and frequent pro- cases, such as many types of down-casting, to be compiler- gramming error [1–15], occur when a variable value goes implementation specific. In addition, the written rules are out of the range of the machine word used to materialize it, not accompanied by an unambiguous set of formal rules, e.g. when assigning a large 32-bit int to a 16-bit short. making it difficult for a programmer to verify that he un- We show that safe and unsafe integer operations in C can derstands C99 correctly. Integer bugs are not exclusive to be captured by well-known sub-typing theory. The RICH C. Similar languages such as C++, and even type-safe lan- compiler extension compiles C programs to object code that guages such as Java and OCaml, do not raise exceptions on monitors its own execution to detect integer-based attacks. -

The Number Line Topic 1
Topic 1 The Number Line Lesson Tutorials Positive numbers are greater than 0. They can be written with or without a positive sign (+). +1 5 +20 10,000 Negative numbers are less than 0. They are written with a negative sign (−). − 1 − 5 − 20 − 10,000 Two numbers that are the same distance from 0 on a number line, but on opposite sides of 0, are called opposites. Integers Words Integers are the set of whole numbers and their opposites. Opposite Graph opposites When you sit across from your friend at Ź5 ź4 Ź3 Ź2 Ź1 0 1234 5 the lunch table, you negative integers positive integers sit opposite your friend. Zero is neither negative nor positive. Zero is its own opposite. EXAMPLE 1 Writing Positive and Negative Integers Write a positive or negative integer that represents the situation. a. A contestant gains 250 points on a game show. “Gains” indicates a number greater than 0. So, use a positive integer. +250, or 250 b. Gasoline freezes at 40 degrees below zero. “Below zero” indicates a number less than 0. So, use a negative integer. − 40 Write a positive or negative integer that represents the situation. 1. A hiker climbs 900 feet up a mountain. 2. You have a debt of $24. 3. A student loses 5 points for being late to class. 4. A savings account earns $10. 408 Additional Topics MMSCC6PE2_AT_01.inddSCC6PE2_AT_01.indd 408408 111/24/101/24/10 88:53:30:53:30 AAMM EXAMPLE 2 Graphing Integers Graph each integer and its opposite. Reading a. 3 Graph 3. -

Secure Coding Frameworks for the Development of Safe, Secure and Reliable Code
Building Cybersecurity from the Ground Up Secure Coding Frameworks For the Development of Safe, Secure and Reliable Code Tim Kertis October 2015 The 27 th Annual IEEE Software Technology Conference Copyright © 2015 Raytheon Company. All rights reserved. Customer Success Is Our Mission is a registered trademark of Raytheon Company. Who Am I? Tim Kertis, Software Engineer/Software Architect Chief Software Architect, Raytheon IIS, Indianapolis Master of Science, Computer & Information Science, Purdue Software Architecture Professional through the Software Engineering Institute (SEI), Carnegie-Mellon University (CMU) 30 years of diverse Software Engineering Experience Advocate for Secure Coding Frameworks (SCFs) Author of the JAVA Secure Coding Framework (JSCF) Inventor of Cybersecurity thru Lexical And Symbolic Proxy (CLaSP) technology (patent pending) Secure Coding Frameworks 10/22/2015 2 Top 5 Cybersecurity Concerns … 1 - Application According to the 2015 ISC(2) Vulnerabilities Global Information Security 2 - Malware Workforce Study (Paresh 3 - Configuration Mistakes Rathod) 4 - Mobile Devices 5 - Hackers Secure Coding Frameworks 10/22/2015 3 Worldwide Market Indicators 2014 … Number of Software Total Cost of Cyber Crime: Developers: $500B (McCafee) 18,000,000+ (www.infoq.com) Cost of Cyber Incidents: Number of Java Software Low $1.6M Developers: Average $12.7M 9,000,000+ (www.infoq.com) High $61.0M (Ponemon Institute) Software with Vulnerabilities: 96% (www.cenzic.com) Secure Coding Frameworks 10/22/2015 4 Research -

Integersintegersintegers Chapter 6Chapter 6 6 Chapter 6Chapter Chapter 6Chapter Chapter 6
IntegersIntegersIntegers Chapter 6Chapter 6 Chapter 6 Chapter 6 Chapter 6 6.1 Introduction Sunita’s mother has 8 bananas. Sunita has to go for a picnic with her friends. She wants to carry 10 bananas with her. Can her mother give 10 bananas to her? She does not have enough, so she borrows 2 bananas from her neighbour to be returned later. After giving 10 bananas to Sunita, how many bananas are left with her mother? Can we say that she has zero bananas? She has no bananas with her, but has to return two to her neighbour. So when she gets some more bananas, say 6, she will return 2 and be left with 4 only. Ronald goes to the market to purchase a pen. He has only ` 12 with him but the pen costs ` 15. The shopkeeper writes ` 3 as due amount from him. He writes ` 3 in his diary to remember Ronald’s debit. But how would he remember whether ` 3 has to be given or has to be taken from Ronald? Can he express this debit by some colour or sign? Ruchika and Salma are playing a game using a number strip which is marked from 0 to 25 at equal intervals. To begin with, both of them placed a coloured token at the zero mark. Two coloured dice are placed in a bag and are taken out by them one by one. If the die is red in colour, the token is moved forward as per the number shown on throwing this die. If it is blue, the token is moved backward as per the number 2021-22 MATHEMATICS shown when this die is thrown. -

Integer Overflow
Lecture 05 – Integer overflow Stephen Checkoway University of Illinois at Chicago Unsafe functions in libc • strcpy • strcat • gets • scanf family (fscanf, sscanf, etc.) (rare) • printf family (more about these later) • memcpy (need to control two of the three parameters) • memmove (same as memcpy) Replacements • Not actually safe; doesn’t do what you think • strncpy • strncat • Available on Windows in C11 Annex K (the optional part of C11) • strcpy_s • strcat_s • BSD-derived, moderately widely available, including Linux kernel but not glibc • strlcpy • strlcat Buffer overflow vulnerability-finding strategy 1. Look for the use of unsafe functions 2. Trace attacker-controlled input to these functions Real-world examples from my own research • Voting machine: SeQuoia AVC Advantage • About a dozen uses of strcpy, most checked the length first • One did not. It appeared in infreQuently used code • Configuration file with fixed-width fields containing NUL-terminated strings, one of which was strcpy’d to the stack • Remote compromise of cars • Lots of strcpy of attacker-controlled Bluetooth data, first one examined was vulnerable • memcpy of attacker-controlled data from cellular modem Reminder: Think like an attacker • I skimmed some source code for a client/server protocol • The server code was full of trivial buffer overflows resulting from the attacker not following the protocol • I told the developer about the issue, but he wasn’t concerned because the client software he wrote wouldn’t send too much data • Most people don’t think like attackers. Three flavors of integer overflows 1. Truncation: Assigning larger types to smaller types int i = 0x12345678; short s = i; char c = i; Truncation example struct s { int main(int argc, char *argv[]) { unsigned short len; size_t len = strlen(argv[0]); char buf[]; }; struct s *p = malloc(len + 3); p->len = len; void foo(struct s *p) { strcpy(p->buf, argv[0]); char buffer[100]; if (p->len < sizeof buffer) foo(p); strcpy(buffer, p->buf); return 0; // Use buffer } } Three flavors of integer overflows 2. -

Solutions to Exercises
Solutions to Exercises Solutions for Chapter 2 Exercise 2.1 Provide a function to check if a character is alphanumeric, that is lower case, upper case or numeric. One solution is to follow the same approach as in the function isupper for each of the three possibilities and link them with the special operator \/ : isalpha c = (c >= ’A’ & c <= ’Z’) \/ (c >= ’a’ & c <= ’z’) \/ (c >= ’0’ & c <= ’9’) An second approach is to use continued relations: isalpha c = (’A’ <= c <= ’Z’) \/ (’a’ <= c <= ’z’) \/ (’0’ <= c <= ’9’) A final approach is to define the functions isupper, islower and isdigit and combine them: isalpha c = (isupper c) \/ (islower c) \/ (isdigit c) This approach shows the advantage of reusing existing simple functions to build more complex functions. 268 Solutions to Exercises 269 Exercise 2.2 What happens in the following application and why? myfst (3, (4 div 0)) The function evaluates to 3, the potential divide by zero error is ignored because Miranda only evaluates as much of its parameter as it needs. Exercise 2.3 Define a function dup which takes a single element of any type and returns a tuple with the element duplicated. The answer is just a direct translation of the specification into Miranda: dup :: * -> (*,*) dup x = (x, x) Exercise 2.4 Modify the function solomonGrundy so that Thursday and Friday may be treated with special significance. The pattern matching version is easily modified; all that is needed is to insert the extra cases somewhere before the default pattern: solomonGrundy "Monday" = "Born" solomonGrundy "Thursday" = "Ill" solomonGrundy "Friday" = "Worse" solomonGrundy "Sunday" = "Buried" solomonGrundy anyday = "Did something else" By contrast, a guarded conditional version is rather messy: solomonGrundy day = "Born", if day = "Monday" = "Ill", if day = "Thursday" = "Worse", if day = "Friday" = "Buried", if day = "Sunday" = "Did something else", otherwise Exercise 2.5 Define a function intmax which takes a number pair and returns the greater of its two components. -

1. Simplicity.-Let N Denote an Arbitrary Integer >0, and M an Odd of N, Aimn
160 MA THEMA TICS: E. T. BELL PROC. N. A. S. SIMPLICITY WITH RESPECT TO CERTAIN QUADRA TIC FORMS By E. T. BiLL DGPARTMUNT OF MATrHMATICS, CALUORNmA INSTITUTE OP T'CHINOIOGY Communicated December 28, 1929 1. Simplicity.-Let n denote an arbitrary integer >0, and m an odd interger >0. Write N[n = f] for the number of representations of n in the quadratic form f when this number is finite. If N[n = f] is a polynomial P(n) in the real divisors of n alone, N[n = f] is, by definition, simple; similarly for N[m = f]. In previous papers,1'23I have considered simplicity when f is a sum of an even number of squares. For an odd number > 1 of squares, no N[n = f] is simple, although if n be restricted to be a square, say k2, then N[k2 = f] is simple when f is a sum of 3, 5 or 7 squares, and for one case (k restricted) of 11 squares. To discuss simplicity for forms f in an odd number of variables, the above definition was extended in a former paper4 as follows. The exten- sion leads to theorems that are actually useful in calculations of numbers of representations, and it was devised with this end in view. Let 2 refer to all positive, zero or negative integers t which are congruent modulo M to a fixed integer T, and which render the arguments of the summand >0. Let P(n) denote a polynomial in the real divisors alone of n, and let c be a constant integer >O. -
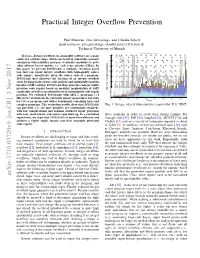
Practical Integer Overflow Prevention
Practical Integer Overflow Prevention Paul Muntean, Jens Grossklags, and Claudia Eckert {paul.muntean, jens.grossklags, claudia.eckert}@in.tum.de Technical University of Munich Memory error vulnerabilities categorized 160 Abstract—Integer overflows in commodity software are a main Other Format source for software bugs, which can result in exploitable memory Pointer 140 Integer Heap corruption vulnerabilities and may eventually contribute to pow- Stack erful software based exploits, i.e., code reuse attacks (CRAs). In 120 this paper, we present INTGUARD, a symbolic execution based tool that can repair integer overflows with high-quality source 100 code repairs. Specifically, given the source code of a program, 80 INTGUARD first discovers the location of an integer overflow error by using static source code analysis and satisfiability modulo 60 theories (SMT) solving. INTGUARD then generates integer multi- precision code repairs based on modular manipulation of SMT 40 Number of VulnerabilitiesNumber of constraints as well as an extensible set of customizable code repair 20 patterns. We evaluated INTGUARD with 2052 C programs (≈1 0 Mil. LOC) available in the currently largest open-source test suite 2000 2002 2004 2006 2008 2010 2012 2014 2016 for C/C++ programs and with a benchmark containing large and Year complex programs. The evaluation results show that INTGUARD Fig. 1: Integer related vulnerabilities reported by U.S. NIST. can precisely (i.e., no false positives are accidentally repaired), with low computational and runtime overhead repair programs with very small binary and source code blow-up. In a controlled flows statically in order to avoid them during runtime. For experiment, we show that INTGUARD is more time-effective and example, Sift [35], TAP [56], SoupInt [63], AIC/CIT [74], and achieves a higher repair success rate than manually generated CIntFix [11] rely on a variety of techniques depicted in detail code repairs. -

Ada for the C++ Or Java Developer
Quentin Ochem Ada for the C++ or Java Developer Release 1.0 Courtesy of July 23, 2013 This work is licensed under a Creative Commons Attribution- NonCommercial-ShareAlike 3.0 Unported License. CONTENTS 1 Preface 1 2 Basics 3 3 Compilation Unit Structure 5 4 Statements, Declarations, and Control Structures 7 4.1 Statements and Declarations ....................................... 7 4.2 Conditions ................................................ 9 4.3 Loops ................................................... 10 5 Type System 13 5.1 Strong Typing .............................................. 13 5.2 Language-Defined Types ......................................... 14 5.3 Application-Defined Types ........................................ 14 5.4 Type Ranges ............................................... 16 5.5 Generalized Type Contracts: Subtype Predicates ............................ 17 5.6 Attributes ................................................. 17 5.7 Arrays and Strings ............................................ 18 5.8 Heterogeneous Data Structures ..................................... 21 5.9 Pointers .................................................. 22 6 Functions and Procedures 25 6.1 General Form ............................................... 25 6.2 Overloading ............................................... 26 6.3 Subprogram Contracts .......................................... 27 7 Packages 29 7.1 Declaration Protection .......................................... 29 7.2 Hierarchical Packages .........................................