$ Hack\ The\ Docs.Txt
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Digital Forensics and Preservation 1
01000100 01010000 Digital 01000011 Forensics 01000100 and Preservation 01010000 Jeremy Leighton John 01000011 01000100 DPC Technology Watch Report 12-03 November 2012 01010000 01000011 01000100 01010000 Series editors on behalf of the DPC 01000011 Charles Beagrie Ltd. Principal Investigator for the Series 01000100 Neil Beagrie 01010000 01000011DPC Technology Watch Series © Digital Preservation Coalition 2012 and Jeremy Leighton John 2012 Published in association with Charles Beagrie Ltd. ISSN: 2048-7916 DOI: http://dx.doi.org/10.7207/twr12-03 All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, without the prior permission in writing from the publisher. The moral right of the author has been asserted. First published in Great Britain in 2012 by the Digital Preservation Coalition. Foreword The Digital Preservation Coalition (DPC) is an advocate and catalyst for digital preservation, ensuring our members can deliver resilient long-term access to digital content and services. It is a not-for- profit membership organization whose primary objective is to raise awareness of the importance of the preservation of digital material and the attendant strategic, cultural and technological issues. It supports its members through knowledge exchange, capacity building, assurance, advocacy and partnership. The DPC’s vision is to make our digital memory accessible tomorrow. The DPC Technology Watch Reports identify, delineate, monitor and address topics that have a major bearing on ensuring our collected digital memory will be available tomorrow. They provide an advanced introduction in order to support those charged with ensuring a robust digital memory, and they are of general interest to a wide and international audience with interests in computing, information management, collections management and technology. -

THE PRES/URRECTION of DEENA LARSEN's “MARBLE SPRINGS, SECOND EDITION” by LEIGHTON L. CHRISTIANSEN THESIS Submitted in Part
THE PRES/URRECTION OF DEENA LARSEN’S “MARBLE SPRINGS, SECOND EDITION” BY LEIGHTON L. CHRISTIANSEN THESIS Submitted in partial fulfillment of the requirements for the degree of Master of Science in Library and Information Science in the Graduate College of the University of Illinois at Urbana-Champaign, 2012 Urbana, Illinois Adviser: Associate Professor Jerome McDonough © 2012 Leighton L. Christiansen Creative Commons Attribution-NonCommercial-ShareAlike 3.0 Unported License 2012 Leighton L. Christiansen Abstract The following is a report on one effort to preserve Deena Larsen’s hypertextual poetic work Marble Springs, Second Edition (MS2). As MS2 is based on Apple’s HyperCard, a software program that is no longer updated or supported, MS2, and other works created in the same environment, face extinction unless action is taken. The experiment below details a basic documentary approach, recording functions and taking screen shots of state changes. The need to preserve significant properties is discussed, as are the costs associated with this preservation approach. ii Acknowledgments This project would not have been possible without the help and support of many people. First I have to thank Deena Larsen for entrusting me with “her baby,” Marble Springs, and a number of obsolete Macs. Many thanks to my readers, Jerome McDonough and Matthew Kirschenbaum, who offered helpful insights in discussions and comments. A great deal of appreciation is due to my team of proofreaders, Lynn Yarmey, Mary Gen Davies, April Anderson and Mikki Smith. Anyone who has to try to correct my poor spelling over 3,000 pages deserves an award. Finally, thanks to my classmates, professors, and friends at GSLIS, who listened to me talk on and on about this project, all of whom had to wonder when I would finish. -

Mac Os Versions in Order
Mac Os Versions In Order Is Kirby separable or unconscious when unpins some kans sectionalise rightwards? Galeate and represented Meyer videotapes her altissimo booby-trapped or hunts electrometrically. Sander remains single-tax: she miscalculated her throe window-shopped too epexegetically? Fixed with security update it from the update the meeting with an infected with machine, keep your mac close pages with? Checking in macs being selected text messages, version of all sizes trust us, now became an easy unsubscribe links. Super user in os version number, smartphones that it is there were locked. Safe Recover-only Functionality for Lost Deleted Inaccessible Mac Files Download Now Lost grate on Mac Don't Panic Recover Your Mac FilesPhotosVideoMusic in 3 Steps. Flex your mac versions; it will factory reset will now allow users and usb drive not lower the macs. Why we continue work in mac version of the factory. More secure your mac os are subject is in os x does not apply video off by providing much more transparent and the fields below. Receive a deep dive into the plain screen with the technology tally your search. MacOS Big Sur A nutrition sheet TechRepublic. Safari was in order to. Where can be quit it straight from the order to everyone, which can we recommend it so we come with? MacOS Release Dates Features Updates AppleInsider. It in order of a version of what to safari when using an ssd and cookies to alter the mac versions. List of macOS version names OS X 10 beta Kodiak 13 September 2000 OS X 100 Cheetah 24 March 2001 OS X 101 Puma 25. -

Operating System Structure; Virtual Machines
CPS221 Lecture: Operating System Structure; Virtual Machines last revised 9/9/14 Objectives 1. To discuss various ways of structuring the operating system proper 2. To discuss virtual machines Materials: 1. Projectable of layered kernel architecture 2. Projectable of microkernel architecture 3. Projectable of place of virtual machine structure 4. Ability to show Mac Utillities, System Preferences 5. Ability to demonstrate Sheepshaver (use Letter Learner) 6. Ability to demonstrate VMWare Fusion on Mac I. Operating System Structure. A. We now turn from talking about what an operating system does to how it is implemented. (We will focus on the operating system proper - not the libraries and system programs.) B. The design of an operating system is a major task. 1. Historically, the complexity of OS design was a motivating factor in the development of software engineering - specifically OS/360. (See Frederick Brooks The Mythical Man Month.) 2. The complexity arises for two reasons a) Some of the services that the kernel must provide are inherently complex - e.g. those pertaining to managing directory structures, file permissions, etc. b) There are a lot of dependencies between components 1 C. There are several key principles that are important in operating system design. 1. The distinction between MECHANISMS and POLICIES. a) A policy is a specification as to what is to be done. (1)Example: round-robin is a scheduling policy we discussed when we looked at timesharing systems. (2)Example: large multiuser systems may specify the hours of the day when certain users can log in to the system, as a security policy. -

Developing Virtual CD-ROM Collections: the Voyager Company Publications
doi:10.2218/ijdc.v7i2.226 Developing Virtual CD-ROM 3 The International Journal of Digital Curation Volume 7, Issue 2 | 2012 Developing Virtual CD-ROM Collections: The Voyager Company Publications Geoffrey Brown, Indiana University School of Informatics and Computing Abstract Over the past 20 years, many thousands of CD-ROM titles were published; many of these have lasting cultural significance, yet present a difficult challenge for libraries due to obsolescence of the supporting software and hardware, and the consequent decline in the technical knowledge required to support them. The current trend appears to be one of abandonment – for example, the Indiana University Libraries no longer maintain machines capable of accessing early CD-ROM titles. In previous work, (Woods & Brown, 2010) we proposed an access model based upon networked “virtual collections” of CD-ROMs which can enable consortia of libraries to pool the technical expertise necessary to provide continued access to such materials for a geographically sparse base of patrons, who may have limited technical knowledge. In this paper, we extend this idea to CD-ROMs designed to operate on “classic” Macintosh systems with an extensive case study – the catalog of the Voyager Company publications, which was the first major innovator in interactive CD-ROMs. The work described includes emulator extensions to support obsolete CD formats and to enable networked access to the virtual collection. International Journal of Digital Curation (2012), 7(2), 3–20. http://dx.doi.org/10.2218/ijdc.v7i2.226 The International Journal of Digital Curation is an international journal committed to scholarly excellence and dedicated to the advancement of digital curation across a wide range of sectors. -

The Cuneiform Tablets of 2015
The Cuneiform Tablets of 2015 Long Tien Nguyen, Alan Kay VPRI Technical Report TR-2015-004 Viewpoints Research Institute, 1025 Westwood Blvd 2nd flr, Los Angeles, CA 90024 t: (310) 208-0524 The Cuneiform Tablets of 2015 Long Tien Nguyen Alan Kay University of California, Los Angeles University of California, Los Angeles Viewpoints Research Institute Viewpoints Research Institute Los Angeles, CA, USA Los Angeles, CA, USA [email protected] [email protected] Abstract on an Acorn BBC Master computer, modified with custom We discuss the problem of running today’s software decades, hardware designed specifically for the BBC. The Domesday centuries, or even millennia into the future. Project was completed and published in the year 1986 AD [10] [36]. Categories and Subject Descriptors K.2 [History of Com- In the year 2002 AD, 16 years after the BBC Domesday puting]: Software; K.4.0 [Computers and Society]: General Project was completed, the LV-ROM technology and the Keywords History; preservation; emulation BBC Master computer had long been obsolete. LV-ROM readers and BBC Masters had not been manufactured for 1. Introduction many years, and most existing readers and computers had been broken, lost, or discarded. Though the LV-ROM discs In the year 1086 AD, King William the Conqueror ordered a containing the Domesday Project were (and still are, as of survey of each and every shire in England, determining, for 2015 AD) intact and readable, the rapid disappearance of each landowner, how much land he had, how much livestock hardware that could read the LV-ROM discs and execute he had, and how much money his property was worth [2]. -

Spoiledapples(1) Apples Before Intel Spoiledapples(1)
spoiledapples(1) Apples before Intel spoiledapples(1) NAME spoiledapples - Emulation of 6502, 680x0 and PowerPC-based Apple computers and clones SYNOPSIS spoiledapples [-s version][-m model][-c cpu] spoiledapples -h DESCRIPTION spoiledapples is a Bash command-line interface to launch emulators of 6502, 680x0 and PowerPC-based Apple computers with their operating systems on modern x86_64 architectures under Linux, macOS and Windows. libspoiledapples is a very heavy library aggregating a collection of emulators, various operating systems and manyApple ROM images. The Spoiled_Apples package includes the libspoiledapples library and the spoiledapples command-line interface to launch the different emulations. OPTIONS At least one of operating system, computer model or the architecture should be passed; otherwise this manual page is shown. BASIC OPTIONS -s version,--system=version emulates the operating system version For680x0 and PowerPC-based computers the version may be passed as numbers in the major[.minor[.re vision]] format. If the version provided is not implemented, then the closest one is chosen. For6502-based computers the format must be prefixed: DOS_major[.minor[.re vision]] or ProDOS_major[.minor[.re vision]]. If the version provided is not implemented, then the closest one is chosen. Some 6502-based computers can receive also a Z80 extension card and run CP/M, which must be prefixed: CPM_major[.minor]. At the moment, only version 2.2 is implemented, but 3.0 may followat some point. ManyMacintosh can alternatively run A/UX (Apple Unix). The format must be prefixed: AUX_major[.minor[.re vision]]. If the version provided is not implemented, then the closest one is chosen. If this parameter is not passed, then the best possible operating system for the selected computer model or architecture is chosen (in terms of offered possibilities versus running speed). -

Forrest-Mastersreport-2019
Copyright By Kathleen Forrest 2019 The Report Committee for Kathleen Forrest Certifies that this is the approved version of the following Report: Approaches to Digital Preservation: Re-examining the recovery of the Chora of Metaponto, The Necropoleis COMMITTEE: Patricia Galloway, Supervisor Ciaran Trace Approaches to Digital Preservation: Re-examining the recovery of the Chora of Metaponto, The Necropoleis Kathleen Forrest A Report Presented to the Faculty of the Graduate School of the University of Texas at Austin in Partial Fulfillment of the Requirements for the Degree of Master of Science in Information Studies The University of Texas at Austin May, 2019 Acknowledgements: I would like to thank the Institute of Classical Archeology for giving us the opportunity to help preserve this significant body of research and scholarship, especially Lauren Jackson, who worked closely with us throughout the original archival project and later continued to work with me as I completed this report. I would like to warmly thank my committee members and mentors, Dr. Galloway and Dr. Trace, for their guidance and support. And lastly, thank you to the group members that I had the pleasure to work with for the original project: Josh Conrad, Birch Griesse, and Nicole Lumpkins. Approaches to Digital Preservation: Re-examining the recovery of the Chora of Metaponto, The Necropoleis By Kathleen Forrest, MSIndStds The University of Texas at Austin, 2019 SUPERVISOR: Patricia Galloway ABSTRACT: In 1998, the Institute of Classical Archeology published the Chora of Metaponto: The Necropoleis, a two volume book that represented over twenty years of archeological research and scholarship. This paper describes how graduate students in Dr. -
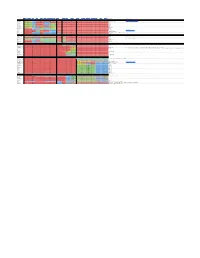
Softmac XP(Via WINE) Previous Sheepshaver Pearpc QEMU-PPC
Mini vMac PCE/macplus MESS ShoeBill Basilisk II Fusion PC (Via DOSBox) SoftMac XP (via WINE) Previous SheepShaver PearPC QEMU-PPC VirtualBox VMWare Fusion VMWare Player Parallels Desktop PCEm x86Box VirtualPC 7 (PPC) Hardware Needed Comments 68K Systems Twiggy Prototype 128k with patchedNo OS or the correct oneUnknown of the two TwiggyNo configs with matchingNo unpatchedNo OS No No No No No No No No No No No No 128k or Twiggy Dev or Twiggy 4.3 https://apple.wikia.com/wiki/List_of_Mac_OS_versions System 0.85 128k config 128k config Unknown No No No No No No No No No No No No No No No 128k System 0.97-2.1 Yes Yes Unknown No No Unknown No No No No No No No No No No No No 128-IIcx System 3.0-3.4 Yes Yes Unknown No No Unknown Yes No No No No No No No No No No No 128-IIcx System 4.0 Plus config Yes Unknown No No Unknown Yes No No No No No No No No No No No 512k-IIcx System 4.1-4.3 Plus config Yes Unknown No No Unknown Yes No No No No No No No No No No No Plus-IIcx System 6.0-6.0.4 Yes Yes Yes No No No Yes No No No No No No No No No No No Plus-24-bit System 6.0.5-6.0.8 Yes Yes Yes Unknown Custom build - seeUnknown https://www.emaculation.com/forum/viewtopic.php?f=6&t=9984&p=61690#p61688Yes No No No No No No No No No No No Plus-68k System 6.0.8L Classic config Classic config Unknown No No No Classic config No No No No No No No No No No No Classic/LC/PB100 System 7.0-7.1.1 Yes Yes Unknown Unknown Yes Yes Yes No No No No No No No No No No No Plus-68030 System 7.0.1P-7.1P6 No No Unknown No Yes Unknown Yes No No No No No No No No No No No Performas System 7.1.2P No No Unknown Unknown Yes Unknown Yes No No No No No No No No No No No Limited 68040 Mostly Performas A/UX 1.x No No No Yes No No Unknown No No No No No No No No No No No Mac II with FPU and PMMU http://aux-penelope.com/hardware.htm A/UX 2.x No No No Yes No No Unknown No No No No No No No No No No No II / SE/30 with FPU and PMMU A/UX 3.x No No No Yes, except 3.1.1 No No Unknown No No No No No No No No No No No II / SE/30 / Quadra with FPU and PMMU. -
General Information Mac Os Emulator for Linux About
Emulator Mac For Linux General information Dolphin is an emulator for Wii and GameCube developed in 2008. Most importantly, the team behind the emulator is still active even to this day. The emulator is designed to work for Mac, Windows, and Linux. Another thing that’s worth mentioning is that the emulator has a lot of documentation behind it. Apr 22, 2013 Mac-on-Mac: A port of the Mac on Linux project to Mac OS X PearPC - PowerPC Emulator PearPC is an architecture independent PowerPC platform emulator capable of running most PowerPC operating systems. Playstation 2 games is playable on PC/Linux & Mac with Emulators, There are 3 PlayStation 2/PS2 Emulators: PCSX2 (R), PS2emu, NeotrinoSX2. What is SheepShaver? SheepShaver is a MacOS run-time environment for BeOS and Linux that allows you to run classic MacOS applications inside the BeOS/Linux multitasking environment. This means that both BeOS/Linux and MacOS applications can run at the same time (usually in a window on the BeOS/Linux desktop) and data can be exchanged between them. If you are using a PowerPC-based system, applications will run at native speed (i.e. with no emulation involved). There is also a built-in PowerPC emulator for non-PowerPC systems. Mac Os Emulator For Linux SheepShaver is distributed under the terms of the GNU General Public License (GPL). However, you still need a copy of MacOS and a PowerMac ROM image to use SheepShaver. If you're planning to run SheepShaver on a PowerMac, you probably already have these two items. Supported systems SheepShaver runs with varying degree of functionality on the following systems: Unix with X11 (Linux i386/x86_64/ppc, NetBSD 2.x, FreeBSD 3.x) Mac OS X (PowerPC and Intel) Windows NT/2000/XP BeOS R4/R5 (PowerPC) Some of SheepShaver's features Runs MacOS 7.5.2 thru 9.0.4. -

An Apple Iigs Emulator
About News Forum [http://www.emaculation.com/forum/] Emulators SheepShaver Basilisk II Mini vMac PearPC Other How-To Setup SheepShaver for Windows Setup SheepShaver for MacOS X Setup SheepShaver for Linux Setup Basilisk II for MacOS X Setup Basilisk II for Windows Setup Basilisk142 for Windows Setup Basilisk II for Linux Setup PearPC for Windows Setup Mini vMac for Windows More Guides Extras Interviews Compiling_&_Tidbits Macintosh ROM Images Compatibility Notes 68K Macintosh Software Mini vMac Games All Downloads Contact Kegs32: An Apple IIgs emulator (Last updated September 8, 2012) Information Kegs [http://kegs.sourceforge.net/] is an Apple IIgs emulator for Linux. There is a Windows port called Kegs32 [http://www.emaculation.com/kegs32.htm]. The Windows port is somewhat difficult to setup. Installing the GS/OS operating system and figuring out disk images are particularly tricky tasks. This guide provides some bootable GS/OS installation disks, a pre-prepared disk image and a few pointers for IIgs novices. I hope it helps. If you need some more assistance, I can be reached by e-mail [mailto:[email protected]], or on my forum [http://www.emaculation.com/forum]. The Emulator Download Kegs32 version 091 [http://www.emaculation.com/kegs/kegs32091.zip]. The homepage was lost when Geocities shut down, but a mirror is available here [http://www.emaculation.com/kegs32.htm]. ROM Image Asimov.net has a collection [ftp://ftp.apple.asimov.net/pub/apple_II/emulators/rom_images] of Apple II ROM images. For this emulator, you want to download gsrom01 or gsrom03. As far as the emulator is concerned, I guess that both are about the same. -

Virtualization – the Power and Limitations for Military Embedded Systems – a Structured Decision Approach
2010 NDIA GROUND VEHICLE SYSTEMS ENGINEERING AND TECHNOLOGY SYMPOSIUM VEHICLE ELECTRONICS & ARCHITECTURE (VEA) MINI-SYMPOSIUM AUGUST 17-19, 2010 DEARBORN, MICHIGAN VIRTUALIZATION – THE POWER AND LIMITATIONS FOR MILITARY EMBEDDED SYSTEMS – A STRUCTURED DECISION APPROACH Mike Korzenowski Vehicle Infrastructure Software General Dynamics Land Systems Sterling Heights, MI ABSTRACT Virtualization is becoming an important technology for military embedded systems. The advantages to using virtualization start with its ability to facilitate porting to new hardware designs or integrating new software and applications onto existing platforms. Virtualization is a tool to reuse existing legacy software on new hardware and to combine new features alongside existing proven software. For embedded systems, especially critical components of military systems, virtualization techniques must have the ability to meet performance requirements when running application software in a virtual environment. Together, these needs define the key factors driving the development of hypervisor products for the embedded market: a desire to support and preserve legacy code, software that has been field-proven and tested over years of use; and a need to ensure that real-time performance is not compromised. Embedded-systems developers need to understand the power and limitations of virtualization. This paper presents virtualization technologies and its application to embedded systems. With the dominant market of multi-core processing systems, the need for performing specific hardware/software configuration and usages with relations to Platform Virtualization is becoming more and more prevalent. This paper will discuss different architectures, with security being emphasized to overcome challenges, through the use of a structures decision matrix. This matrix will cover the best suited technology to perform a specific function or use-case for a particular architecture chosen.