PDF Download Avoid Being a Secret Agent in the Second World War!
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The History of Dunedin Income Growth Investment Trust
The History of Dunedin Income Growth Investment Trust PLC The first investment trust launched in Scotland, 1873 – 2018 Dunedin Income Growth Trust Investment Income Dunedin Foreword 1873 – 2018 This booklet, written for us by John Newlands, It is a particular pleasure for me, as Chairman of DIGIT describes the history of Dunedin Income Growth and as former employee of Robert Fleming & Co to be Investment Trust PLC, from its formation in Dundee able to write a foreword to this history. It was Robert in February 1873 through to the present day. Fleming’s vision that established the trust. The history Launched as The Scottish American Investment Trust, of the trust and its role in making professional “DIGIT”, as the Company is often known, was the first investment accessible is as relevant today as it investment trust formed in Scotland and has been was in the 1870s when the original prospectus was operating continuously for the last 145 years. published. I hope you will find this story of Scottish enterprise, endeavour and vision, and of investment Notwithstanding the Company’s long life, and the way over the past 145 years interesting and informative. in which it has evolved over the decades, the same The Board of DIGIT today are delighted that the ethos of investing in a diversified portfolio of high trust’s history has been told as we approach the quality income-producing securities has prevailed 150th anniversary of the trust’s formation. since the first day. Today, while DIGIT invests predominantly in UK listed companies, we, its board and managers, maintain a keen global perspective, given that a significant proportion of the Company’s revenues are generated from outside of the UK and that many of the companies in which we invest have very little exposure to the domestic economy. -

Military History Anniversaries 0101 Thru 0131
Military History Anniversaries 1 thru 31 January Events in History over the next 30 day period that had U.S. military involvement or impacted in some way on U.S military operations or American interests Jan 00 1944 – WW2: USS Scorpion (SS–278). Date of sinking unknown. Most likely a Japanese mine in Yellow or East China Sea. 77 killed. Jan 00 1945 – WW2: USS Swordfish (SS–193) missing. Possibly sunk by Japanese Coast Defense Vessel No. 4 on 5 January or sunk by a mine off Okinawa on 9 January. 89 killed. Jan 01 1942 – WW2: The War Production Board (WPB) ordered the temporary end of all civilian automobile sales leaving dealers with one half million unsold cars. Jan 01 1945 – WW2: In Operation Bodenplatte, German planes attack American forward air bases in Europe. This is the last major offensive of the Luftwaffe. Jan 02 1777 – American Revolution: American forces under the command of George Washington repulsed a British attack at the Battle of the Assunpink Creek near Trenton, New Jersey. Casualties and losses: US 7 to 100 - GB 55 to 365. Jan 02 1791 – Big Bottom massacre (11 killed) in the Ohio Country, marking the beginning of the Northwest Indian War. Jan 02 1904 – Latin America Interventions: U.S. Marines are sent to Santo Domingo to aid the government against rebel forces. Jan 02 1942 – The Federal Bureau of Investigation (FBI) convicts 33 members of a German spy ring headed by Fritz Joubert Duquesne in the largest espionage case in United States history-the Duquesne Spy Ring. Jan 02 1942 – WW2: In the Philippines, the city of Manila and the U.S. -

Military History Anniversaries 1 Thru 15 January
Military History Anniversaries 1 thru 15 January Events in History over the next 15 day period that had U.S. military involvement or impacted in some way on U.S military operations or American interests Jan 00 1944 – WW2: USS Scorpion (SS–278). Date of sinking unknown. Most likely a Japanese mine in Yellow or East China Sea. 77 killed. Jan 00 1945 – WW2: USS Swordfish (SS–193) missing. Possibly sunk by Japanese Coast Defense Vessel No. 4 on 5 January or sunk by a mine off Okinawa on 9 January. 89 killed. Jan 01 1781 – American Revolution: Mutiny of the Pennsylvania Line – 1,500 soldiers from the Pennsylvania Line (all 11 regiments under General Anthony Wayne’s command) insist that their three-year enlistments are expired, kill three officers in a drunken rage and abandon the Continental Army’s winter camp at Morristown, New Jersey. Jan 01 1883 – Civil War: President Abraham Lincoln signs the final Emancipation Proclamation, which ends slavery in the rebelling states. The proclamation freed all slaves in states that were still in rebellion as of 1 JAN. Jan 01 1915 – WWI: The 15,000-ton British HMS class battleship Formidable is torpedoed by the German submarine U-24 and sinks in the English Channel, killing 547 men. The Formidable was part of the 5th Battle Squadron unit serving with the Channel Fleet. Jan 01 1942 – WW2: The War Production Board (WPB) ordered the temporary end of all civilian automobile sales leaving dealers with one half million unsold cars. Jan 01 1942 – WW2: United Nations – President Franklin D. -

A Counterintelligence Reader, Volume 2 Chapter 1, CI in World
CI in World War II 113 CHAPTER 1 Counterintelligence In World War II Introduction President Franklin Roosevelts confidential directive, issued on 26 June 1939, established lines of responsibility for domestic counterintelligence, but failed to clearly define areas of accountability for overseas counterintelligence operations" The pressing need for a decision in this field grew more evident in the early months of 1940" This resulted in consultations between the President, FBI Director J" Edgar Hoover, Director of Army Intelligence Sherman Miles, Director of Naval Intelligence Rear Admiral W"S" Anderson, and Assistant Secretary of State Adolf A" Berle" Following these discussions, Berle issued a report, which expressed the Presidents wish that the FBI assume the responsibility for foreign intelligence matters in the Western Hemisphere, with the existing military and naval intelligence branches covering the rest of the world as the necessity arose" With this decision of authority, the three agencies worked out the details of an agreement, which, roughly, charged the Navy with the responsibility for intelligence coverage in the Pacific" The Army was entrusted with the coverage in Europe, Africa, and the Canal Zone" The FBI was given the responsibility for the Western Hemisphere, including Canada and Central and South America, except Panama" The meetings in this formative period led to a proposal for the organization within the FBI of a Special Intelligence Service (SIS) for overseas operations" Agreement was reached that the SIS would act -
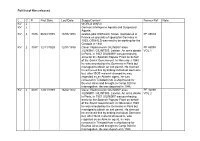
Full List of Files Released L C P First Date Last Date Scope/Content
Full list of files released L C P First Date Last Date Scope/Content Former Ref Note KV 2 WORLD WAR II KV 2 German Intelligence Agents and Suspected Agents KV 2 3386 06/03/1935 18/08/1953 Greta Lydia OSWALD: Swiss. Imprisoned in PF 45034 France on grounds of spying for Germany in 1935, OSWALD was said to be working for the Gestapo in 1941 KV 2 3387 12/11/1929 12/01/1939 Oscar Vladimirovich GILINSKY alias PF 46098 JILINSKY, GILINTSIS: Latvian. An arms dealer VOL 1 in Paris, in 1937 GILINSKY was purchasing arms for the Spanish Popular Front on behalf of the Soviet Government. In November 1940 he was arrested by the Germans in Paris but managed to obtain an exit permit. He claimed he achieved this by bribing individual Germans but, after ISOS material showed he was regarded as an Abwehr agent, he was removed in Trinidad from a ship bound for Buenos Aires and brought to Camp 020 for interrogation. He was deported in 1946 KV 2 3388 13/01/1939 16/02/1942 Oscar Vladimirovich GILINSKY alias PF 46098 JILINSKY, GILINTSIS: Latvian. An arms dealer VOL 2 in Paris, in 1937 GILINSKY was purchasing arms for the Spanish Popular Front on behalf of the Soviet Government. In November 1940 he was arrested by the Germans in Paris but managed to obtain an exit permit. He claimed he achieved this by bribing individual Germans but, after ISOS material showed he was regarded as an Abwehr agent, he was removed in Trinidad from a ship bound for Buenos Aires and brought to Camp 020 for interrogation. -

The Heritage, Volume 46-2019
The Heritage HOT SPRING COUNTY OBITUARY LIST - 2018 This list is to be considered a supplement to the 2019 Heritage Index in which the names are not duplicated. Name Abbott, Joel Abernathy, Bobbie Adams-Thorne, Eva Eunice Ainsworth, Fred Robert Allen, Bobby Joe Allen, Obedia Jordan Allen, Peggy Lee (Loy) Allred, Aaron Andrew Alston, Roxie F. Arguello, Esteban Gracia Ashcraft, Ronald Burton Ashley, Doyle Freeman Avery, Mary Jo Bailey, Glenda Jean Baker, Margrette J. Barbary, Brian Patrick, Sr. Bass, Vera Faye Batchelor, Gene Baugh, Sandra Bealle, Robert F. “Bob” Beason, Carroll Gene Beason, Verla M. Hodges Bellomy, Mary Francis Vaudean Bennett, Charles W. “Butch”, Jr. Bennett, Jeffery Wade “Papaw” Billingsly, Charlotte Annette Bittinger, Robert Charles Bivens, Lisa Renee Black, Jerrold Harrison Boone, Doris Linwood Boshears, James Lloyd “Bo” Bosley, Ella Branham Bowen, Mary JoAnn Strong Bowline, Cheryl Lynn Bratton Branch, Betty J. Schlenker Bray, Nancy Sullivan Brooks, Christopher Shawn Brown, Bobbie Linnes Thrash Brown, Bobby “Bear” Eugene ~ 185 ~ Hot Spring County, Arkansas Historical Society ©2019 The Heritage Bryant, Bill C. Bryant, Carl Nadine Buck, Judith Lynn McGriff Buck, Shirley Jean Langley Bunn, Rachel Alberta Burks, Lynda Gail Burns, Wanda King Burrell, Loretta Moore Burris, Leslie “Sonny” Burris, Mitchell Alvin Callahan, Charles Houston Campbell, Aline Dixon Todd Campbell, Ruby Jewell Gilstrap Campos, Ernest “Joe”, Jr. Cannon, Robert Carson, Christine B. Broomfield Carter, Lena Sapphire Tidwell Cash, Lorene Bryant Cates, Donald R. Caver, James Henry “J. H.” Chancellor, Ernestine Cheatham, Irene Smith Clardy, Chrystal A. Baxter Clary Jeannie Cloninger, Marilyn Robbins Cockrell, Mary Frances Collins, Corey Collins, Minnie Bell Combs, Maude Marie Honeycutt Coney, Dallas Ford Cook, Lynzi Annice Copeland, Claudine E. -

International Spy Museum
International Spy Museum Searchable Master Script, includes all sections and areas Area Location, ID, Description Labels, captions, and other explanatory text Area 1 – Museum Lobby M1.0.0.0 ΚΑΤΆΣΚΟΠΟΣ SPY SPION SPIJUN İSPİYON SZPIEG SPIA SPION ESPION ESPÍA ШПИОН Language of Espionage, printed on SCHPION MAJASUSI windows around entrance doors P1.1.0.0 Visitor Mission Statement For Your Eyes Only For Your Eyes Only Entry beyond this point is on a need-to-know basis. Who needs to know? All who would understand the world. All who would glimpse the unseen hands that touch our lives. You will learn the secrets of tradecraft – the tools and techniques that influence battles and sway governments. You will uncover extraordinary stories hidden behind the headlines. You will meet men and women living by their wits, lurking in the shadows of world affairs. More important, however, are the people you will not meet. The most successful spies are the unknown spies who remain undetected. Our task is to judge their craft, not their politics – their skill, not their loyalty. Our mission is to understand these daring professionals and their fallen comrades, to recognize their ingenuity and imagination. Our goal is to see past their maze of mirrors and deception to understand their world of intrigue. Intelligence facts written on glass How old is spying? First record of spying: 1800 BC, clay tablet from Hammurabi regarding his spies. panel on left side of lobby First manual on spy tactics written: Over 2,000 years ago, Sun Tzu’s The Art of War. 6 video screens behind glass panel with facts and images. -

Risk of Public Disclosure: Learning from Willy Wonka
Issue 20, 16 December 2014 WhiteNews Global corporate espionage news Editorial: WhiteRock Updates: All About Privacy 2 Threat: Are LinkedIn Contacts Trade Secrets? 3 News: $400 Bn Military Espionage; Code Fishing 4 News: Falcani Black List; Football Whistleblower 5 Feature: Willy Wonka’s Lessons in Espionage 6-7 Technology: Hearing Aid for Corporate Spies 8-9 Extra: FBI’s Untold Story; Spy on Your Rival 10-11 Letter From America: Spying Breakfast Club 12 Exclusive Reporting for WhiteRock’s Clients Risk of Public Disclosure: Learning from Willy Wonka Our feature story is seemingly seasonal and light-hearted, but the film ‘Charlie and the Chocolate Factory’ carries a very strong espionage message that is relevant even 50 years later. Willy Wonka was a brilliant CEO who knew that the only person who could protect his trade was himself. Wonka’s story translates superbly into today’s corporate world, and in this issue we are discussing how the contemporary big players are maintaining their edge and success over their competitors. This is equally relevant for small and medium-sized businesses, who really don’t prioritise their trade secrets, making their advantage extremely vulnerable. In the technology section we analyse the delicate matter of hearing aid systems. They’re everywhere, including in corporate meeting rooms, and nobody really considers these as a threat. We’re examining how to achieve a balance between protecting valuable corporate information without creating an embarrassing situation that in turn could lead to reputational damage! Our extra section may give you a wrong impression this time. No, we’re not teaching you how to spy, this is not our bag. -

Counterintelligence in the Kingdom and the States
Counterintelligence in the Kingdom and the States A Historical Comparison of the FBI and MI5 Matthew Kalkavage Master’s Thesis Advisor: Professor Arthur Hulnick Submitted: April 14, 2014 Executive Summary The United States and the United Kingdom have different kinds of organizations to defend their national security from espionage and terrorist threats. The US relies on the Federal Bureau of Investigation (FBI), a law enforcement agency with counterintelligence functions, while the UK depends on the Security Service (MI5), a purely counterintelligence agency without law enforcement powers, to meet these challenges. The purpose of this paper is to examine the benefits, detriments, and the key motivations behind each system’s development for the sake of showing that MI5 has ultimately served the UK better than the FBI has served the US in the realm of counterintelligence. The historical trajectory of the Security Service is one of constant honing of counterintelligence work from its very inception. The history of the FBI reveals an organization that was initially established for law enforcement purposes and has never completely abandoned its preference for that mission amid US governmental pressure to become more intelligence- driven in times of international crisis (especially during World War I, World War II, and parts of the Cold War). The counterintelligence practices of the Service and the Bureau throughout their histories illustrate the deficiencies and proficiencies of each, which mutually contribute to the understanding of key counterintelligence qualities that are presented in the final chapter. These attributes are an overall penchant for secrecy, an external orientation, and a preventative operational culture. -

UNIVERSITY of CALIFORNIA Los Angeles Security and United States Immigration Policy a Dissertation Submitted in Partial Satisfact
UNIVERSITY OF CALIFORNIA Los Angeles Security and United States Immigration Policy A dissertation submitted in partial satisfaction of the Requirements for the degree of Doctor of Philosophy in Political Science by Robbie James Totten 2012 © Copyright by Robbie James Totten 2012 ABSTRACT OF THE DISSERTATION Security and United States Immigration Policy by Robbie James Totten Doctor of Philosophy in Political Science University of California, Los Angeles, 2012 Professor Deborah Larson, Chair What is the relationship between security and immigration to the U.S? How do security objectives factor into U.S. immigration policy? These questions are significant for the U.S. because the volume of international migration has been increasing in recent years and without sound policy planning immigration will serve as a source of conflict with foreign states, tax the ability of domestic systems to assimilate diverse peoples without violence, and expose citizens and immigrants to crime, contagious disease, and terrorism. This dissertation answers the above questions and presents the strategic logic for U.S. immigration policy by providing a typology of security policy objectives for America in this area. It identifies three general categories of security objectives that U.S. leaders have attempted to reach with immigration from the colonial era to the present-day: (1) domestic security (prevent crime, espionage, and terrorism; epidemics; and ethnic violence); (2) foreign relations; and (3) material and military interests. The analyses accompanying the categories draw from government documents, International Relations (IR) and security studies theories, legal statutes, primary sources such as private letters, and works by demographers and historians to specify the relationships amongst the security areas and immigration, identify the policy ii instruments used by leaders to influence immigration for security, and present a large body of cases of historical U.S. -

Spy Lingo — a Secret Eye
A Secret Eye SpyLingo A Compendium Of Terms Used In The Intelligence Trade — July 2019 — A Secret Eye . blog PUBLISHER'S NOTICE: Although the authors and publisher have made every eort to ensure that the information in this book was correct at press time, the authors and publisher do not assume and hereby disclaim any liability to any party for any loss, damage, or disruption caused by errors or omissions, whether such errors or omissions result from negligence, TEXTUAL CONTENT: Textual Content can be reproduced for all non-commercial accident, or any other cause. purposes as long as you provide attribution to the author / and original source where available. CONSUMER NOTICE: You should assume that the author of this document has an aliate relationship and/or another material connection to the providers of goods and services mentioned in this report THIRD PARTY COPYRIGHT: and may be compensated when you purchase from a To the extent that copyright subsists in a third party it provider. remains with the original owner. Content compiled and adapted by: Vincent Hardy & J-F Bouchard © Copyright 9218-0082 Qc Inc July 2019 — Spy Lingo — A Secret Eye Table Of Contents INTRODUCTION 4 ALPHA 5 Ab - Ai 5 Al - As 6 Au - Av 7 Bravo 8 Ba - Bl 8 Bl - Bre 9 Bri - Bu 10 CHARLIE 11 C3 - Can 11 Car - Chi 12 Cho - Cl 13 Cn - Com 14 Comp - Cou 15 Cov 16 Cu 17 DELTA 18 Da - De 18 De - Di 19 Di - Dru 20 Dry - Dz 21 Echo 22 Ea - Ex 22 Ey 23 FOXTROT 24 Fa - Fi 24 Fl - For 25 Fou - Fu 26 GOLF 27 Ga - Go 27 Gr - Gu 28 HOTEL 29 Ha - Hoo 29 Hou - Hv 30 INDIA 31 Ia -

Secret Operations of World War II. by Alexander Stillwell. London, United Kingdom: Amber Books Ltd, 2018
Journal of Strategic Security Volume 11 Number 4 Article 6 Secret Operations of World War II. By Alexander Stillwell. London, United Kingdom: Amber Books Ltd, 2018. Millard E. Moon U.S. Air Force Office of Special Investigations Follow this and additional works at: https://scholarcommons.usf.edu/jss pp. 89-93 Recommended Citation Moon, Millard E.. "Secret Operations of World War II. By Alexander Stillwell. London, United Kingdom: Amber Books Ltd, 2018.." Journal of Strategic Security 11, no. 4 (2019) : 89-93. DOI: https://doi.org/10.5038/1944-0472.11.4.1717 Available at: https://scholarcommons.usf.edu/jss/vol11/iss4/6 This Book Review is brought to you for free and open access by the Open Access Journals at Scholar Commons. It has been accepted for inclusion in Journal of Strategic Security by an authorized editor of Scholar Commons. For more information, please contact [email protected]. Secret Operations of World War II. By Alexander Stillwell. London, United Kingdom: Amber Books Ltd, 2018. This book review is available in Journal of Strategic Security: https://scholarcommons.usf.edu/jss/ vol11/iss4/6 Moon: Book Review: <i>Secret Operations of World War II</i> Secret Operations of World War II. By Alexander Stillwell. London, United Kingdom: Amber Books Ltd, 2018. ISBN 978-1- 78274-632-4. Photographs. Bibliography. Index. Pp. 224. $21.77. The author has done an excellent job of providing an overview of the most prominent secret operations, and the exploits of some of the most heroic, but little known, agents operating for the Allied forces in World War II.