Proceedings, ITC/USA
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

12/04/13 1. Einleitung 1
12/04/13 1. Einleitung 1 1. Einleitung − Was ist Systemadministration? ============================================= 12/04/13 1. Einleitung 2 System Administration: It’s a dirty job, but someone said I had to do it. Aufgaben eines Sysadmin gestern und heute: Früher Heute − Einrichten von neuen Nutzern Auch heute gibt es neue User per Hand mit Scripte, Oberflächen automatisiert − Druckermanagment Tonerpatrone Wechseln, Druckerjobs canceln, Drucker reaktivieren, Nutzer beruhigen, Das ist immer noch so. "Der Drucker druckt nicht, ich habe nichts gemacht." − Fragen beantworten: "Wie kann ich ....?" Die Nutzer lesen immer Das "Dialog−Manual" noch keine Manuals. − Prozesse killen Auch heute sollen Prozesse noch endlos laufen. 12/04/13 1. Einleitung 3 Früher Heute − Prozesse/Daemone nach Möglich, aber es gibt Absturz neu starten auch Überwachungstools − Tastaturen aktivieren kommt seltener vor − Backups veranlassen Die Datenmengen sind (zeitzyklisch, häufig) nur viel größer. − Restore von Files Auch heute löschen Nutzer ihre Files unabsichtlich. − "Mein Rechner macht nichts mehr!!!!" Passiert seltener, da die Monitoring/Tracing Rechner schneller sind und mehr Prozessoren haben, gibt es dieses Problem nicht so oft. − Rebooting von Systemen Alle zwei bis drei Jahre kommt bei Fehlern so etwas noch vor. − Speicherplatz auf Platten schaffen Jeder erfüllte Wunsch erzeugt Hilferuf: "Ich kann nichts mehr viele neue kleine Wünsche speichern!!!!" − Sicherheitslöcher finden und Schlimmer als je zuvor, beseitigen, Einbrecher suchen dank Internet und verfolgen 12/04/13 1. Einleitung 4 Früher Heute − Passwörter prüfen Nicht mehr nötig dank neuer Technologien − Programme installieren Es soll auch heute noch neue Programme geben. Einheitliche Verfahren erleichtern aber die Arbeit. − Betriebssystemupdates Vereinfacht. − Konfiguration des Rechnernetzes ja − Installieren neuer Rechner. -

Objective Is
Lehigh Preserve Institutional Repository Design of a microprocessor-based emulsion polymerization process control facility Dimitratos, John N. 1987 Find more at https://preserve.lib.lehigh.edu/ This document is brought to you for free and open access by Lehigh Preserve. It has been accepted for inclusion by an authorized administrator of Lehigh Preserve. For more information, please contact [email protected]. Design of a Microprocessor-based Emulsion Polymerization Process Control Facility A research report written in partial fulfillment of the requirements for the degree of Master of Science in Chemical F:ngim·ering, Lehigh University, Bethlehem, Pennsylvania by John N. Dimitratos June 1987 ,. Design of a Microprocessor-based Emulsion Polymerization .. ,_.,,-•• ·, ,, -i •:>:.·.:':' Process Control Facility ' A research report written in partial fulfillment of the requirements for the degree of Master of Science in Chemical Engineering, Lehigh University, Bethlehem, Pennsylvania by John N. Dimitratos June 1987 •1 to my father and my brother there art times when it is hard to decide what should be chosen at what price, and what endured in return for what reward. Perhaps it is still harder to stick to the decision Aristotle (384-322 B.C) Ethics, Book Ill. Abstract The explosion of microcomputer technology and the recent developments in software and hardware products introduce a new horizon of capabilities for the process control engineer. However, taking advantage of this new technology is not something easily done. H the process control engineer has to undertake such a project soon he will have to deal with the different languages the software engineer and the plant operator use. -

Comparing UNIX with Other Systems
Comparing UNIX with other systems Timothy DO' Chase Corporate Computer systems, Inc. 33 West Main Street Holmdel, New Jersey he original concept behind this article was to make a grand comparison between UNIX Tand several other well known systems. This was to beall encompassing and packed with vital information summarized in neat charts, tables and graphs. As the work began, the realization settled in that this was not only difficult to do, but would result in a work so boring as to beincomprehensible. The reader, faced with such awealth ofinformation would be lost at best. Conclusions would be difficult to draw and, in short, the result would be worthless. Mtertearfully filling my waste basket with the initial efforts, I regrouped and began by as king myself why would anyone be interested in comparing UNIX with another operating system? There appears to be only two answers. First, one might hope to learn something about UNIX by analogy. IfI understand the file system on MPEN and someone tells me that UNIX is like that except for such and so, then I might be more quickly able to under stand UNIX. This I felt was an unlikely motivation. After all, there are much simpler ways to learn UNIX. Instead, the motivation for comparing UNIX to other systems must come from a need to evaluate UNIX. Ifwe are aware of the features or short comings ofother systems, then we can benefit by evaluating UNIX relative to those systems. Choosing an operating system or computer is a major decision which we can benefit from or be stuck with for a long time. -

Partition Types
Partition Types Partition Types The number on the right is in Hexadecimal. 01 DOS 12-bit fat 02 XENIX root 03 XENIX /usr 04 DOS 3.0+ 16-bit FAT (up to 32M) 05 DOS 3.3+ Extended Partition 06 DOS 3.31+ 16-bit FAT (over 32M) 07 OS/2 IFS (e.g., HPFS) 07 Advanced Unix 07 Windows NT NTFS 07 QNX2.x (pre-1988) 08 OS/2 (v1.0-1.3 only) 08 AIX boot partition 08 SplitDrive 08 DELL partition spanning multiple drives 08 Commodore DOS 08 QNX 1.x and 2.x ("qny") 09 AIX data partition 09 Coherent filesystem 09 QNX 1.x and 2.x ("qnz") 0a OS/2 Boot Manager 0a Coherent swap partition 0a OPUS 0b WIN95 OSR2 32-bit FAT 0c WIN95 OSR2 32-bit FAT, LBA-mapped 0e WIN95: DOS 16-bit FAT, LBA-mapped 0f WIN95: Extended partition, LBA-mapped 10 OPUS (?) 11 Hidden DOS 12-bit FAT 12 Compaq config partition 14 Hidden DOS 16-bit FAT <32M 16 Hidden DOS 16-bit FAT >=32M 17 Hidden IFS (e.g., HPFS) 18 AST SmartSleep Partition 19 Unused (Claimed for Willowtech Photon COS) 1b Hidden WIN95 OSR2 32-bit FAT 1c Hidden WIN95 OSR2 32-bit FAT, LBA-mapped 1e Hidden WIN95 16-bit FAT, LBA-mapped 20 Unused 21 Reserved 21 Unused 22 Unused 23 Reserved 24 NEC DOS 3.x 26 Reserved 31 Reserved 32 NOS 33 Reserved 34 Reserved 35 JFS on OS/2 or eCS 36 Reserved 38 THEOS ver 3.2 2gb partition 39 Plan 9 partition 39 THEOS ver 4 spanned partition 3a THEOS ver 4 4gb partition 3b THEOS ver 4 extended partition 3c PartitionMagic recovery partition 3d Hidden NetWare 40 Venix 80286 41 Linux/MINIX (sharing disk with DRDOS) 41 Personal RISC Boot 41 PPC PReP (Power PC Reference Platform) Boot 42 Linux swap (sharing -
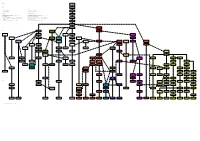
Unix History 2.6 Unix Geschichte 2.6 1972
1960 AT&T UNICS 1969 1970 UNIX 1 1971 UNIX 2 Unix history 2.6 Unix Geschichte 2.6 1972 Small UNIX history Kleine UNIX-Geschichte UNIX 3 1973 Represented are only the origin lines. Dargestellt sind nur die Ursprungslinien. The different influences are shown only with Apple, since they impair Die verschiedenen Einflüsse sind nur bei Apple abgebildet, da sie die the clarity strongly. Übersichtlichkeit stark beeinträchtigen. UNIX 4 Further data are: Manufacturer, operating system name as well as the Weitere Daten sind: Hersteller, Betriebssystem-Name sowie das 1973 feature year of the software. The individual versions are listed only with Erscheinungsjahr der Software. Die einzelnen Versionen sind nur bei UNIX and Linux. UNIX und Linux aufgelistet. More detailed list under: http://www.levenez.com/unix/ Detailliertere Liste unter: http://www.levenez.com/unix/ UNIX 5 1974 UNIX 6 1976 UNIX 7 Berkeley Software 1979 Distribution: BSD 1978 1980 UNIX System III Microsoft BSD 4.1 1981 XENIX 1981 1980 UNIX V UNIX 8 SUN SPIX QUNIX 1983 1985 Sun OS 1.0 1982 1981 1982 UNIX V.2 Microsoft/SCO Siemens UNIX 9 Sun OS 2.0 Dynix Venix 1984 XENIX 3.0 Sinix 1.0 1986 1985 1984 1985 1984 1984 HP IBM UNIX 10 MIPS BSD 4.2 GNU Sun OS 3.0 Andrew S. Mach HP-UX AIX/RT 2 End: 1989 MIPS OS 1985 Trix 1986 Tanenbaum: Minix 1985 1986 1986 1985 1986 1987 UNIX V.3 SGI Mach 2.0 Minix 1.0 NonStop-UX 1986 IRIX 1996 1987 1987 1988 UNIX V.4 AIX/6000 v3 BOS MIPS OS NeXT A/UX 1988 1989 1989 End: 1989 NeXTSTEP 1988 1988 1990 UNIX V.x Trusted AIX 3.1 IRIX 4.0 Mach 3.0 Linus Torvalds -

Red Hat Linux 6.0
Red Hat Linux 6.0 The Official Red Hat Linux Installation Guide Red Hat Software, Inc. Durham, North Carolina Copyright c 1995, 1996, 1997, 1998, 1999 Red Hat Software, Inc. Red Hat is a registered trademark and the Red Hat Shadow Man logo, RPM, the RPM logo, and Glint are trademarks of Red Hat Software, Inc. Linux is a registered trademark of Linus Torvalds. Motif and UNIX are registered trademarks of The Open Group. Alpha is a trademark of Digital Equipment Corporation. SPARC is a registered trademark of SPARC International, Inc. Products bearing the SPARC trade- marks are based on an architecture developed by Sun Microsystems, Inc. Netscape is a registered trademark of Netscape Communications Corporation in the United States and other countries. TrueType is a registered trademark of Apple Computer, Inc. Windows is a registered trademark of Microsoft Corporation. All other trademarks and copyrights referred to are the property of their respective owners. ISBN: 1-888172-28-2 Revision: Inst-6.0-Print-RHS (04/99) Red Hat Software, Inc. 2600 Meridian Parkway Durham, NC 27713 P. O. Box 13588 Research Triangle Park, NC 27709 (919) 547-0012 http://www.redhat.com While every precaution has been taken in the preparation of this book, the publisher assumes no responsibility for errors or omissions, or for damages resulting from the use of the information con- tained herein. The Official Red Hat Linux Installation Guide may be reproduced and distributed in whole or in part, in any medium, physical or electronic, so long as this copyright notice remains intact and unchanged on all copies. -

Advanced Unix/Linux System Program Instructor: William W.Y
Advanced Unix/Linux System Program Instructor: William W.Y. Hsu › Course preliminaries › Introduction CONTENTS › Unix history › Unix basics 2/22/2018 INTRODUCTION TO COMPETITIVE PROGRAMMING 2 About this class › The class is called “Advanced Unix/Linux System Programming”. › It is not: – an introduction to Unix – an introduction to programming – an introduction to C (or C++) › 2/22/2018 INTRODUCTION TO COMPETITIVE PROGRAMMING 3 In a nutshell: the “what” 2/22/2018 INTRODUCTION TO COMPETITIVE PROGRAMMING 4 In a nutshell: the “what” 2/22/2018 ADVANCED UNIX/LINUX SYSTEM PROGRAMMING 5 In a nutshell: the “what” › Gain an understanding of the UNIX operating systems. › Gain (systems) programming experience. › Understand fundamental OS concepts (with focus on UNIX family): multi-user concepts. – Basic and advanced I/O – Process relationships – Interprocess communication – Basic network programming using a client/server model 2/22/2018 ADVANCED UNIX/LINUX SYSTEM PROGRAMMING 6 In a nutshell: the “why” › Understanding how UNIX works gives you insights in other OS concepts. › System level programming experience is invaluable as it forms the basis for most other programming and even use of the system. › System level programming in C helps you understand general programming concepts. › Most higher level programming languages (eventually) call (or implement themselves) standard C library functions. 2/22/2018 ADVANCED UNIX/LINUX SYSTEM PROGRAMMING 7 In a nutshell: the “how” static char dot[] = ".", *dotav[] = {dot, NULL}; struct winsize win; int ch, fts_options; int kflag = 0; const char *p; setprogname(argv[0]); setlocale(LC_ALL, ""); /* Terminal defaults to -Cq, non-terminal defaults to -1. */ if (isatty(STDOUT_FILENO)) { if (ioctl(STDOUT_FILENO, TIOCGWINSZ, &win) == 0 && win.ws_col > 0) termwidth = win.ws_col; f_column = f_nonprint = 1; } else f_singlecol = 1; /* Root is -A automatically. -

Operating System Selection
EARTH STATION CONTROL COMPUTER - OPERATING SYSTEM SELECTION D. Varney and L. D'Ad.dario June 11, 1991 Abstract This report describes a survey of real-time operating systems that may form a suitable platform for construction of the control software for the Green Bank OVLBI Earth Station. After considering the performance requirements, desire for standardization, hardware and software costs, and several other factors, we have selected Venix, by VenturCom, Inc. This includes a fully-preemptable real-time kernel that is compliant with UNIX interface standards, including SVID, Posix 1003.1 and 1003.4, and ABI/386. It runs on 80386 processors in the IBM-AT architecture. 1 Introduction The software requirements for the OVLBI Earth Station control computer were outlined in OVLBI- ES Memo No. 8. In the present memo, we discuss the implications for the choice of operating system (OS), evaluate several candidate OS's, and report the final selection. This will have a strong effect on the choice of hardware platform, which will be discussed in a subsequent memo. The main requirements on the OS are (1) that it provide good real-time performance for time- critical tasks, including predictable interrupt response and task switching times regardless of system loading; and (2) that it provide good support for networking, both local-- and wide-area, including the protocols commonly used at the NRAO for remote access and file transfer, namely TCP/IP. To this we add a desire for good debugging facilities to ease development, especially for real-time tasks. UNIX has become the most standard and portable operating system available. -

Oh the Places UNIX'll
Oh, the Places UNIX'll Go! (With apologies to Dr. Seuss) Oh the places UNIX'll go we'll start from its birth A replacement for MULTICS, a system of great girth The UNiplexed Information and Computing Service (UNICS for short) A programmer's workbench, not much of import It started off life on the PDP-7 Unnamed 'till it reached the PDP-11 With 16bit “mostly orthogonal instruction set” This little-used machine did UNIX beget The system grew to fit several needs Research, Word Processing, and Space Travel deeds The system took form on the PDP-11 (The oldest machine to run UNIX V7) But assembly code is hard to maintain And with UNIX came something to ease that pain “Complex systems must use assembly for everything” they cried But The C Programming Language cast that claim aside UNIX was written in C by v8 And with it the chance for UNIX to migrate Ritchie and Thompson presented UNIX to all in 1973 But Bell couldn't monetize it because of a 1956 consent decree So UNIX was shipped on magnetic tapes And all sorts of media of all sorts of shapes The souorce was available on an “as-is” basis Find a copy of “Lions'” and we're off to the races UNIX for teaching and educational use Version 6 set UNIX's commercial side loose Development was quick and the patches released Sometimes without letting the attorneys say their peace UNIX was on DEC but Bell Labs felt restricted Bell bought an Interdata 8/32 to see DEC evicted And then UNIX ran as a VM/370 guest UNIVAC 1100 and Intel 8086 (custom MMU blessed) Near the end of the '70s UNIX showed up in places It even brought smiles to ARPA's faces But the 1980s would start UNIX's spiral For that is when plucky UNIX went viral Oh, the places UNIX'll go, to thousands of sites They even were noticed by the magazine BYTE Companies "may support other [operating] systems”, it's true “but a Unix implementation always happens to be available". -

Linux Quick Reference Guide (8Th Ed.)
Linux Quick Reference Guide 8th edition January 2020 Foreword This guide stems from the notes I have been taking while studying and working as a Linux sysadmin and engineer. It contains useful information about standards and tools for Linux system administration, as well as a good amount of topics from the certification exams LPIC-1 (Linux Professional Institute Certification level 1), LPIC-2, RHCSA (Red Hat Certified System Administrator), and RHCE (Red Hat Certified Engineer). Unless otherwise specified, the shell of reference is Bash. This is an independent publication and is not affiliated with LPI or Red Hat. You can freely use and share the whole guide or the single pages, provided that you distribute them unmodified and not for profit. This document has been composed with Apache OpenOffice. Happy Linux hacking, Daniele Raffo Version history 1st edition May 2013 2nd edition September 2014 3rd edition July 2015 4th edition June 2016 5th edition September 2017 6th edition August 2018 7th edition May 2019 8th edition January 2020 Bibliography and suggested readings ● Evi Nemeth et al., UNIX and Linux System Administration Handbook, O'Reilly ● Rebecca Thomas et al., Advanced Programmer's Guide to Unix System V, McGraw-Hill ● Mendel Cooper, Advanced Bash-Scripting Guide, http://tldp.org/LDP/abs/html ● Adam Haeder et al., LPI Linux Certification in a Nutshell, O'Reilly ● Heinrich W. Klöpping et al., The LPIC-2 Exam Prep, http://lpic2.unix.nl ● Michael Jang, RHCSA/RHCE Red Hat Linux Certification Study Guide, McGraw-Hill ● Asghar Ghori, RHCSA & RHCE RHEL 7: Training and Exam Preparation Guide, Lightning Source Inc. -

Advanced Programming in the UNIX Environment
CS631-AdvancedProgrammingintheUNIXEnvironment Slide1 CS631 - Advanced Programming in the UNIX Environment Department of Computer Science Stevens Institute of Technology Jan Schaumann [email protected] https://www.cs.stevens.edu/~jschauma/631/ Lecture 01: Introduction, UNIX history, UNIX Programming Basics August 27, 2018 CS631-AdvancedProgrammingintheUNIXEnvironment Slide2 New Rules Close your laptops! Lecture 01: Introduction, UNIX history, UNIX Programming Basics August 27, 2018 CS631-AdvancedProgrammingintheUNIXEnvironment Slide3 New Rules Close your laptops! Open your eyes! (Mind, too.) Lecture 01: Introduction, UNIX history, UNIX Programming Basics August 27, 2018 CS631-AdvancedProgrammingintheUNIXEnvironment Slide4 So far, so good... What questions do you have? Lecture 01: Introduction, UNIX history, UNIX Programming Basics August 27, 2018 CS631-AdvancedProgrammingintheUNIXEnvironment Slide5 About this class The class is called “Advanced Programming in the UNIX Environment”. It is not called: “An Introduction to Unix” “An Introduction to Programming” “An introduction to C” Lecture 01: Introduction, UNIX history, UNIX Programming Basics August 27, 2018 CS631-AdvancedProgrammingintheUNIXEnvironment Slide6 What is it? https://www.bell-labs.com/usr/dmr/www/chist.html Lecture 01: Introduction, UNIX history, UNIX Programming Basics August 27, 2018 CS631-AdvancedProgrammingintheUNIXEnvironment Slide7 In a nutshell: the ”what” $ ls /bin [ csh ed ls pwd sleep cat date expr mkdir rcmd stty chio dd hostname mt rcp sync chmod df kill mv -

Kermit User Guide
KERMIT USER GUIDE Seventh Edition Christine Gianone, Editor Columbia University Center for Computing Activities New York, New York 10027 May 26, 1988 Copyright (C) 1981,1988 Trustees of Columbia University in the City of New York Permission is granted to any individual or institution to use, copy, or redistribute this document so long as it is not sold for profit, and provided this copyright notice is retained. PREFACE Page 1 PREFACE Kermit is the name of a protocol for transferring files from one computer to another over ordinary asynchronous terminal connections. Kermit programs have been written for many different computers, and in general any two computers that have Kermit programs can exchange sequential files correctly and completely. This manual gives a brief and general overview of what Kermit is and how to use it, but consists mostly of detailed instructions for use and installation of specific Kermit programs. For a more detailed introduction to Kermit, complete with illustrations, diagrams, and tutorials, consult the book Kermit, A File Transfer Protocol, by Frank da Cruz, Digital Press, Bedford MA (1987), ISBN 0-932376-88-6, DEC order number EY-6705E-DP (phone 1-800-343-8321). The Kermit book describes Kermit in detail, from the points of view of the beginner, the user, the computer professional who must install Kermit programs or support their use, and the programmer who wishes to write new Kermit implementations. Also included are general introductions to computers, data communications, and file organization, plus a detailed troubleshooting guide, bootstrapping hints, and various appendices and tables. The latter half of the book is taken up by a complete description of the Kermit file transfer protocol, with programming examples in the C language, plus some analysis and comparisons of Kermit with other popular protocols such as Xmodem.