Digital Forensic Approaches for Amazon Alexa Ecosystem
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

19STCV20E05 21 Guardian, Steve Altes, Individually and on Behalf of All Others Similarly Situated
1 Andrew H. Schapiro (pro hac vice forthcoming) [email protected] 2 Stephen A. Swedlow (pro hac vice forthcoming) [email protected] 3 QUINN EMANUEL URQUHART & SULLIVAN, LLP 4 191 N. Wacker Drive, Suite 2700 Chicago, Illinois 60606-1881 If) 5 Telephone: (312)705-7400 Fax: (312) 705-7401 6 o Joseph C. Sarles (Bar No. 254750) o 7 [email protected] GS 8 QUINN EMANUEL URQUHART & SULLIVAN, LLP o 865 South Figueroa Street, 10th Floor •ss. Los Angeles, California 90017-2543 o 9 o Telephone: (213) 443-3000 10 Fax: (213)443-3100 11 Ashley C. Keller (pro hac vice forthcoming) [email protected] 12 KELLER LENKNER LLC 150 N. Riverside Plaza, Suite 4270 13 Chicago, IL 60606 14 Telephone: (312)741-5222 Fax: (312) 970-3502 15 [Additional Counsel Appear on Signature Page] 16 Attorneys for Plaintiff and the Putative Class 17 SUPERIOR COURT OF THE STATE OF CALIFORNIA 18 COUNTY OF LOS ANGELES 19 CENTRAL DISTRICT 20 R.A., a minor, by and through his CASE NO. 19STCV20E05 21 guardian, Steve Altes, individually and on behalf of all others similarly situated. CLASS ACTION COMPLAINT 22 AND DEMAND FOR JURY TRIAL Plaintiff, 23 V. 24 AMAZON.COM, INC., a Delaware 25 corporation, and A2Z DEVELOPMENT 26 CENTER, INC., a Delaware corporation. 27 Defendants. 28 -1- CLASS ACTION COMPLAINT AND DEMAND FOR JURY TRIAL 1 Millions of Americans use Amazon’s smart-speaker technology (“Alexa”) in their homes. 2 People speak to Alexa-enabled devices such as the Echo or Echo Dot about everything from the 3 mundane (“Alexa, what’s the weather?”) to the deeply personal (“Alexa, what are the symptoms 4 of depression?”). -

Reinventing Product Design with AWS
Reinventing Product Design with AWS Ramzi BEN ROMDHANE AWS Industry Lead Manufacturing France © 2020, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark. Manufacturing Webinar Series MON AWS in Manufacturing Oct 19 TUE Reinventing Product Design with AWS Oct 20 WED Smart Factory & AWS Oct 21 THU Supply Chain Reinvention Oct 22 FRI SAP in the Cloud for Manufacturers Oct 23 © 2020, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark. Agenda 1. PLM digital threads on AWS Walker Stemple WW lead Industry R&D Solutions Amazon Web Services 2. Remote CAD & CAE Jörg Krall Amir Javanshir Sr. Sales Specialist ProViz DACH Region Senior SA – ISV Partner Nvidia Amazon Web Services Please post your questions for Q&A into the webinar chat © 2020, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark. PLM digital threads on AWS PLM -Product Lifecycle Management Walker Stemple WW lead Industry R&D Solutions Amazon Web Services October 2020 © 2020, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Agenda 01 Industry challenges 02 Best practices with AWS 03 Solution overview 04 How to get started 05 Appendix © 2020, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Perceived barriers to PLM modernization efforts 50% of industrial firms have been using their current PLM for over 5 years & 22% for 10 years old or greater Source. : June 2018 —CIMdata Cloud PLM: Understanding Adoption Prospects • Reliability must be maintained • Training is required for designers, engineers, analysts • PLM is tightly integrated with other critical IT systems like ERP, MES, SCM • Heavy migration of legacy data (reuse design) • Many customized and legacy engineering services built on it + Modernization projects would last years & cost several hundreds thousand of dollars. -

Digital Forensic Approaches for Amazon Alexa Ecosystem
Digital Investigation 22 (2017) S15eS25 Contents lists available at ScienceDirect Digital Investigation journal homepage: www.elsevier.com/locate/diin DFRWS 2017 USA d Proceedings of the Seventeenth Annual DFRWS USA Digital forensic approaches for Amazon Alexa ecosystem * Hyunji Chung, Jungheum Park, Sangjin Lee Center for Information Security Technologies (CIST), Korea University, 145 Anam-ro, Seongbuk-Gu, Seoul, 02841, South Korea abstract Keywords: Internet of Things (IoT) devices such as the Amazon Echo e a smart speaker developed by Amazon e are Internet of Things undoubtedly great sources of potential digital evidence due to their ubiquitous use and their always-on Cloud-based IoT mode of operation, constituting a human-life's black box. The Amazon Echo in particular plays a centric Intelligent virtual assistant (IVA) role for the cloud-based intelligent virtual assistant (IVA) Alexa developed by Amazon Lab126. The Alexa- Amazon Alexa Amazon Echo enabled wireless smart speaker is the gateway for all voice commands submitted to Alexa. Moreover, the Cloud native forensics IVA interacts with a plethora of compatible IoT devices and third-party applications that leverage cloud Client centric forensics resources. Understanding the complex cloud ecosystem that allows ubiquitous use of Alexa is paramount CIFT on supporting digital investigations when need raises. This paper discusses methods for digital forensics pertaining to the IVA Alexa's ecosystem. The primary contribution of this paper consists of a new efficient approach of combining cloud-native forensics with client-side forensics (forensics for companion de- vices), to support practical digital investigations. Based on a deep understanding of the targeted ecosystem, we propose a proof-of-concept tool, CIFT, that supports identification, acquisition and analysis of both native artifacts from the cloud and client-centric artifacts from local devices (mobile applications and web browsers). -

Case 2:19-Cv-00910 Document 1 Filed 06/11/19 Page 1 of 15
Case 2:19-cv-00910 Document 1 Filed 06/11/19 Page 1 of 15 1 2 3 4 5 6 7 8 UNITED STATES DISTRICT COURT 9 FOR THE WESTERN DISTRICT OF WASHINGTON AT SEATTLE 10 C.O., a minor, by and through her guardian Case No.: 2:19-cv-910 11 Alison Hall-O’Neil, individually and on behalf 12 of all others similarly situated, CLASS ACTION COMPLAINT 13 Plaintiff, vs. AND DEMAND FOR JURY TRIAL 14 AMAZON.COM, INC., a Delaware 15 corporation, and A2Z DEVELOPMENT 16 CENTER, INC., a Delaware corporation, 17 Defendants. 18 CLASS ACTION COMPLAINT AND DEMAND FOR JURY TRIAL 19 Millions of Americans use Amazon’s smart-speaker technology (“Alexa”) in their homes. 20 People speak to Alexa-enabled devices such as the Echo or Echo Dot about everything from the 21 mundane (“Alexa, what’s the weather?”) to the deeply personal (“Alexa, what are the symptoms 22 of depression?”). 23 Most people believe that when they speak to an Alexa-enabled device, it converts their 24 voice into a set of digital computer instructions. They expect that this digital query is sent over 25 the internet for processing, that a digital response is returned, and that the device then converts 26 the response into Alexa’s voice. They do not expect that Alexa is creating and storing a 27 28 CLASS ACTION COMPL. QUINN EMANUEL URQUHART & SULLIVAN LLP CASE NO. 2:19-CV-910 - 1 600 UNIVERSITY STREET SUITE 2800 SEATTLE, WASHINGTON 98101 Tel: (206) 905-7000 Case 2:19-cv-00910 Document 1 Filed 06/11/19 Page 2 of 15 1 permanent recording of their voice. -
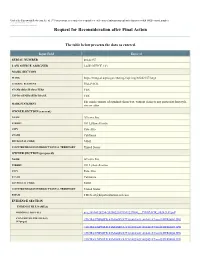
Request for Reconsideration After Final Action
Under the Paperwork Reduction Act of 1995 no persons are required to respond to a collection of information unless it displays a valid OMB control number. PTO Form 1960 (Rev 10/2011) OMB No. 0651-0050 (Exp 09/20/2020) Request for Reconsideration after Final Action The table below presents the data as entered. Input Field Entered SERIAL NUMBER 88242157 LAW OFFICE ASSIGNED LAW OFFICE 123 MARK SECTION MARK https://tmng-al.uspto.gov/resting2/api/img/88242157/large LITERAL ELEMENT PILLPACK STANDARD CHARACTERS YES USPTO-GENERATED IMAGE YES The mark consists of standard characters, without claim to any particular font style, MARK STATEMENT size or color. OWNER SECTION (current) NAME A9.com, Inc. STREET 101 Lytton Avenue CITY Palo Alto STATE California ZIP/POSTAL CODE 94301 COUNTRY/REGION/JURISDICTION/U.S. TERRITORY United States OWNER SECTION (proposed) NAME A9.com, Inc. STREET 101 Lytton Avenue CITY Palo Alto STATE California ZIP/POSTAL CODE 94301 COUNTRY/REGION/JURISDICTION/U.S. TERRITORY United States EMAIL [email protected] EVIDENCE SECTION EVIDENCE FILE NAME(S) ORIGINAL PDF FILE evi_38104128234-20200220191511227000_._PILLPACK_88242157.pdf CONVERTED PDF FILE(S) \\TICRS\EXPORT18\IMAGEOUT18\882\421\88242157\xml2\RFR0002.JPG (89 pages) \\TICRS\EXPORT18\IMAGEOUT18\882\421\88242157\xml2\RFR0003.JPG \\TICRS\EXPORT18\IMAGEOUT18\882\421\88242157\xml2\RFR0004.JPG \\TICRS\EXPORT18\IMAGEOUT18\882\421\88242157\xml2\RFR0005.JPG \\TICRS\EXPORT18\IMAGEOUT18\882\421\88242157\xml2\RFR0006.JPG \\TICRS\EXPORT18\IMAGEOUT18\882\421\88242157\xml2\RFR0007.JPG -

AI Companies
AI Companies AI Professionals’ Views on Working with the Department of Defense Authors: Catherine Aiken, Rebecca Kagan, and Michael Page Surveys were sent to a random sample of AI professionals from the following companies: Boston: >10k employees: Amazon Fidelity Investments Google IBM Microsoft 501-10k employees: Akamai Technologies Amazon Robotics Bose Corporation DataRobot DraftKings Inc. Draper iRobot MathWorks Novartis Institutes for BioMedical Research (NIBR) TripAdvisor Wayfair 10-500 employees: CCDS Charles River Analytics Interactions LLC MassChallenge Neurala Optimus Ride PathAI Recorded Future Center for Security and Emerging Technology | 1 Smartvid.io Systems & Technology Research Los Angeles: >10k employees: Amazon Amgen AT&T Google Northrop Grumman 501-10k employees: Blizzard Entertainment Capital Group Cylance Inc. Esri HRL Laboratories, LLC Hulu Netflix Panasonic Avionics Corporation ServiceTitan Snap Inc. 10-500 employees: Avenue i Media Beyond Limits Bird Factual Inc Information Sciences Institute ObEn, Inc Syntiant Corp Tinder Virtualitics, Inc. Zest AI New York: >10k employees: Bloomberg LP Goldman Sachs Google Center for Security and Emerging Technology | 2 IBM JPMorgan Chase & Co. Morgan Stanley 501-10k employees: Audible, Inc. Citadel Etsy FactSet Flatiron Health General Assembly Jet Millennium RBC Capital Markets Spotify Two Sigma WeWork 10-500 employees: ASAPP Cubist Systematic Strategies Dataminr Elemental Cognition Insight Data Science Kasisto, Inc Metis NYC Data Science Academy Rang Technologies Inc Reonomy -

Terpening V. Amazon.Com, Inc
Case 5:21-cv-03739 Document 1 Filed 05/18/21 Page 1 of 21 CALEB MARKER (SBN 269721) 1 Email: [email protected] ZIMMERMAN REED, LLP 2 2381 Rosecrans Ave., Suite 328 Manhattan Beach, CA 90245 3 (877) 500-8780 Telephone (877) 500-8781 Facsimile 4 JASON P. JOHNSTON (Pro hac vice to be filed) 5 Email: [email protected] BRIAN C. GUDMUNDSON (Pro hac vice to be filed) 6 Email: [email protected] MICHAEL J. LAIRD (Pro hac vice to be filed) 7 Email: [email protected] ZIMMERMAN REED, LLP 8 80 South 8th Street, Suite 1100 Minneapolis, MN 55402 9 (612) 341-0400 Telephone (612) 341-0844 Facsimile 10 Attorneys for Plaintiff 11 12 13 UNITED STATES DISTRICT COURT 14 NORTHERN DISTRICT OF CALIFORNIA 15 DAVID TERPENING, individually and on CASE NO.: 5:21-CV-03739 behalf of all others similarly situated, 16 Plaintiff, COMPLAINT 17 v. (CLASS ACTION) 18 AMAZON.COM, INC., a Delaware 1. Violation of the Wiretap Act (18 U.S.C. §§ 19 corporation; and DOES 1-50, inclusive, 2511 et seq.) 2. Violation of the Washington Consumer 20 Defendants. Protection Act (Wash. Rev. Code §§ 19.86 et seq.) 21 3. Violation of the Washington Wiretapping Law (Wash. Rev. Code §§ 9.73.030 et seq.) 22 23 (Jury Trial Demanded) 24 25 26 27 28 1 CLASS ACTION COMPLAINT Case 5:21-cv-03739 Document 1 Filed 05/18/21 Page 2 of 21 1 Plaintiff David Terpening (“Plaintiff”) brings this Complaint, individually and on behalf of all 2 others similarly situated, against Defendant Amazon.com, Inc., (“Amazon” or “Defendant”), and alleges 3 upon personal knowledge as to his own actions, and upon information and belief as to counsel’s 4 investigations, and on information and belief as to all other matters, as follows: 5 NATURE OF ACTION 6 1. -

Myers, Angela G. Title: Content Analysis of Consumer Reviews Of
1 Author: Myers, Angela G. Title: Content Analysis of Consumer Reviews of the Amazon Echo Dot 2nd and 3rd Generations The accompanying research report is submitted to the University of Wisconsin-Stout, Graduate School in partial completion of the requirements for the Graduate Degree/ Major: MS Technical and Professional Communication Research Advisor: Daisy Pignetti, Ph.D. Submission Term/Year: Spring 2019 Number of Pages: 71 Style Manual Used: American Psychological Association, 6th edition I have adhered to the Graduate School Research Guide and have proofread my work. I understand that this research report must be officially approved by the Graduate School. Additionally, by signing and submitting this form, I (the author(s) or copyright owner) grant the University of Wisconsin-Stout the non-exclusive right to reproduce, translate, and/or distribute this submission (including abstract) worldwide in print and electronic format and in any medium, including but not limited to audio or video. If my research includes proprietary information, an agreement has been made between myself, the company, and the University to submit a thesis that meets course-specific learning outcomes and CAN be published. There will be no exceptions to this permission. I attest that the research report is my original work (that any copyrightable materials have been used with the permission of the original authors), and as such, it is automatically protected by the laws, rules, and regulations of the U.S. Copyright Office. My research advisor has approved the content and quality of this paper. STUDENT: NAME: Angela Myers DATE: April 19, 2019 ADVISOR: (Committee Chair if MS Plan A or EdS Thesis or Field Project/Problem): NAME: Daisy Pignetti, PhD DATE: April 19, 2019 -------------------------------------------------------------------------------------------------------------------- ------------- This section for MS Plan A Thesis or EdS Thesis/Field Project papers only Committee members (other than your advisor who is listed in the section above) 1.