Experiences with the Design of the W3C XML Schema Definition Language
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Describing Media Content of Binary Data in XML W3C Working Group Note 2 May 2005
Table of Contents Describing Media Content of Binary Data in XML W3C Working Group Note 2 May 2005 This version: http://www.w3.org/TR/2005/NOTE-xml-media-types-20050502 Latest version: http://www.w3.org/TR/xml-media-types Previous version: http://www.w3.org/TR/2004/WD-xml-media-types-20041102 Editors: Anish Karmarkar, Oracle Ümit Yalçınalp, SAP (formerly of Oracle) Copyright © 2005 W3C ® (MIT, ERCIM, Keio), All Rights Reserved. W3C liability, trademark and document use rules apply. > >Abstract This document addresses the need to indicate the content-type associated with binary element content in an XML document and the need to specify, in XML Schema, the expected content-type(s) associated with binary element content. It is expected that the additional information about the content-type will be used for optimizing the handling of binary data that is part of a Web services message. Status of this Document This section describes the status of this document at the time of its publication. Other documents may supersede this document. A list of current W3C publications and the latest revision of this technical report can be found in the W3C technical reports index at http://www.w3.org/TR/. This document is a W3C Working Group Note. This document includes the resolution of the comments received on the Last Call Working Draft previously published. The comments on this document and their resolution can be found in the Web Services Description Working Group’s issues list and in the section C Change Log [p.11] . A diff-marked version against the previous version of this document is available. -
XML Specifications Growth of the Web
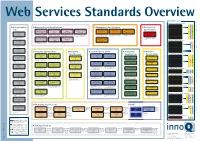
Web Services Standards Overview Dependencies Messaging Specifications SOAP 1.1 SOAP 1.2 Interoperability Business Process Specifications Management Specifications Presentation SOAP Message Transmission Optimization Mechanism WS-Notification the trademarks of their respective owners. of their respective the trademarks Management Using Web Management Of WS-BaseNotification Issues Business Process Execution WS-Choreography Model Web Service Choreography Web Service Choreography WS-Management Specifications Services (WSDM-MUWS) Web Services (WSDM-MOWS) Language for Web Services 1.1 Overview Interface Description Language AMD, Dell, Intel, Microsoft and Sun WS-Topics (BPEL4WS) · 1.1 · BEA Systems, IBM, (WSCI) · 1.0 · W3C 1.0 1.0 1.0 · W3C (CDL4WS) · 1.0 · W3C Microsystems Microsoft, SAP, Sun Microsystems, SAP, BEA Systems WS-BrokeredNotification Working Draft Candidate Recommendation OASIS OASIS Published Specification Web Services for Remote Security Resource Basic Profile Siebel Systems · OASIS-Standard and Intalio · Note OASIS-Standard OASIS-Standard Metadata Portlets (WSRP) WS-Addressing – Core 1.1 ̆ ̆ ̆ ̆ ̆ ̆ ̆ 2.0 WS-I Business Process Execution Language for Web Services WS-Choreography Model Overview defines the format Web Service Choreography Interface (WSCI) describes Web Service Choreography Description Language Web Service Distributed Management: Management Using Web Service Distributed Management: Management Of WS-Management describes a general SOAP-based WS-Addressing – WSDL Binding 1.1(BPEL4WS) provides a language for the formal -

What Is XML Schema?
72076_FM 3/22/02 10:39 AM Page i XML Schema Essentials R. Allen Wyke Andrew Watt Wiley Computer Publishing John Wiley & Sons, Inc. 72076_AppB 3/22/02 10:47 AM Page 378 72076_FM 3/22/02 10:39 AM Page i XML Schema Essentials R. Allen Wyke Andrew Watt Wiley Computer Publishing John Wiley & Sons, Inc. 72076_FM 3/22/02 10:39 AM Page ii Publisher: Robert Ipsen Editor: Cary Sullivan Developmental Editor: Scott Amerman Associate Managing Editor: Penny Linskey Associate New Media Editor: Brian Snapp Text Design & Composition: D&G Limited, LLC Designations used by companies to distinguish their products are often claimed as trademarks. In all instances where John Wiley & Sons, Inc., is aware of a claim, the product names appear in initial capital or ALL CAPITAL LETTERS. Readers, however, should contact the appropriate companies for more complete information regarding trademarks and registration. This book is printed on acid-free paper. Copyright © 2002 by R. Allen Wyke and Andrew Watt. All rights reserved. Published by John Wiley & Sons, Inc. Published simultaneously in Canada. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copy- right Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 750-4744. Requests to the Publisher for permission should be addressed to the Permissions Department, John Wiley & Sons, Inc., 605 Third Avenue, New York, NY 10158-0012, (212) 850-6011, fax (212) 850- 6008, E-Mail: PERMREQ @ WILEY.COM. -

Command Injection in XML Signatures and Encryption Bradley W
Command Injection in XML Signatures and Encryption Bradley W. Hill Information Security Partners, July 12, 2007 [email protected] Abstract. The XML Digital Signature1 (XMLDSIG) and XML Encryption2 (XMLENC) standards are complex protocols for securing XML and other content. Among its complexities, the XMLDSIG standard specifies various “Transform” algorithms to identify, manipulate and canonicalize signed content and key material. Unfortunately, the defined transforms have not been rigorously constrained to prevent their use as attack vectors, and denial of service or even arbitrary code execution are probable in implementations that have not specifically guarded against such risks. Attacks against the processing application can be embedded in the KeyInfo portion of a signature, making them inherently unauthenticated, or in the SignedInfo block. Although tampering with the SignedInfo should be detectable, a defective implied order of operations in the specification may still allow unauthenticated attacks here. The ability to execute arbitrary code and perform file system operations with a malicious, invalid signature has been confirmed by the researcher in at least two independent XMLDSIG implementations, and other implementations may be similarly vulnerable. This paper describes the vulnerabilities in detail and offers advice for remediation. The most damaging attack is also likely to apply in other contexts where XSLT is accepted as input, and should be considered by all implementers of complex XML processing systems. Categories and Subject Descriptors Primary Classification: K.6.5 Security and Protection Subject: Invasive software Unauthorized access Authentication Additional Classification: D.2.3 Coding Tools and Techniques (REVISED) Subject: Standards D.2.1 Requirements/Specifications (D.3.1) Subject: Languages Tools General Terms: Security, Reliability, Verification, and Design. -

OWL 2 Web Ontology Language Quick Reference Guide
OWL 2 Web Ontology Language Quick Reference W3C Proposed Recommendation 22 September Guide 2009 OWL 2 Web Ontology Language Quick Reference Guide W3C Proposed Recommendation 22 September 2009 This version: http://www.w3.org/TR/2009/PR-owl2-quick-reference-20090922/ Latest version: http://www.w3.org/TR/owl2-quick-reference/ Previous version: http://www.w3.org/TR/2009/WD-owl2-quick-reference-20090611/ (color-coded diff) Editors: Jie Bao, Rensselaer Polytechnic Institute Elisa F. Kendall, Sandpiper Software, Inc. Deborah L. McGuinness, Rensselaer Polytechnic Institute Peter F. Patel-Schneider, Bell Labs Research, Alcatel-Lucent Contributors: Li Ding, Rensselaer Polytechnic Institute Ankesh Khandelwal, Rensselaer Polytechnic Institute This document is also available in these non-normative formats: PDF version, Reference Card. Copyright © 2009 W3C® (MIT, ERCIM, Keio), All Rights Reserved. W3C liability, trademark and document use rules apply. Abstract The OWL 2 Web Ontology Language, informally OWL 2, is an ontology language for the Semantic Web with formally defined meaning. OWL 2 ontologies provide classes, properties, individuals, and data values and are stored as Semantic Web documents. OWL 2 ontologies can be used along with information written in RDF, and OWL 2 ontologies themselves are primarily exchanged as RDF documents. The OWL 2 Document Overview describes the overall state of OWL 2, and should be read before other OWL 2 documents. Page 1 of 15 http://www.w3.org/TR/2009/PR-owl2-quick-reference-20090922/ OWL 2 Web Ontology Language Quick Reference W3C Proposed Recommendation 22 September Guide 2009 This document provides a non-normative quick reference guide to the OWL 2 language. -

Describing Media Content of Binary Data in XML W3C Working Group Note 4 May 2005
Table of Contents Describing Media Content of Binary Data in XML W3C Working Group Note 4 May 2005 This version: http://www.w3.org/TR/2005/NOTE-xml-media-types-20050504 Latest version: http://www.w3.org/TR/xml-media-types Previous version: http://www.w3.org/TR/2005/NOTE-xml-media-types-20050502 Editors: Anish Karmarkar, Oracle Ümit Yalçınalp, SAP Copyright © 2005 W3C ® (MIT, ERCIM, Keio), All Rights Reserved. W3C liability, trademark and document use rules apply. > >Abstract This document addresses the need to indicate the content-type associated with binary element content in an XML document and the need to specify, in XML Schema, the expected content-type(s) associated with binary element content. It is expected that the additional information about the content-type will be used for optimizing the handling of binary data that is part of a Web services message. Status of this Document This section describes the status of this document at the time of its publication. Other documents may supersede this document. A list of current W3C publications and the latest revision of this technical report can be found in the W3C technical reports index at http://www.w3.org/TR/. This document is a W3C Working Group Note. This document includes the resolution of the comments received on the Last Call Working Draft previously published. The comments on this document and their resolution can be found in the Web Services Description Working Group’s issues list. There is no technical difference between this document and the 2 May 2005 version; the acknowledgement section has been updated to thank external contributors. -

SLA Information Technology Division Metadata for Video: Too Much
3/1/2019 Metadata for Video: Too Much Content, Not Enough Information | SLA Information Technology Division Home About Us » Events » Sections » Enter search keyword SLA Information Technology Division Awards » Making Edgier Easier. We're IT! Current b/ITe (v31n5) » b/ITe Archives Virtual Events What’s New Categorized | Uncategorized Metadata for Video: Too Much Content, Not Enough Information Posted on 31 August 2012. by Wayne Pender, McGill University, 2012 Joe Ann Clifton Student Award Winner (Published September 1, 2012) Abstract Television news libraries have struggled with cataloguing, organizing and storing visual materials for efficient search and retrieval for years. This task has been complicated by the emergence of digital video and the exponential growth in the holdings of television news libraries. In parallel, the ability for non-professionals to shoot, edit and publish videos of increasing production value and complexity on the web has flooded the Internet with videos that appeal to a wide audience and subject interest. The present survey looks at the metadata protocols and practices in place for an internal audience in professional operations and on display for the general public on the Internet. The study finds that the lack of a common metadata schema can make much of the material inaccessible. Literature pertaining to this area is reviewed and future direction is discussed. http://it.sla1.org/2012/08/metadata/ 1/10 3/1/2019 Metadata for Video: Too Much Content, Not Enough Information | SLA Information Technology Division Keywords: metadata, video, XML, RDF, MXF, television, news, YouTube Paper Searching and retrieving visual content is problematic. The search for specific moving images on film and video has long been a task for television news professionals, but now with wide spread availability of video resources on the Internet it has become a task for anyone. -

Schematron Overview Excerpted from Leigh Dodds’ 2001 XSLT UK Paper, “Schematron: Validating XML Using XSLT”
Schematron: validating XML using XSLT Schematron Overview excerpted from Leigh Dodds’ 2001 XSLT UK paper, “Schematron: validating XML using XSLT” Leigh Dodds, ingenta ltd, xmlhack.com April 2001 Abstract Schematron [Schematron] is a structural based validation language, defined by Rick Jelliffe, as an alternative to existing grammar based approaches. Tree patterns, defined as XPath expressions, are used to make assertions, and provide user-centred reports about XML documents. Expressing validation rules using patterns is often easier than defining the same rule using a content model. Tree patterns are collected together to form a Schematron schema. Schematron is a useful and accessible supplement to other schema languages. The open-source XSLT implementation is based around a core framework which is open for extension and customisation. Overview This paper provides an introduction to Schematron; an innovative XML validation language developed by Rick Jelliffe. This innovation stems from selecting an alternative approach to validation than existing schema languages: Schematron uses a tree pattern based paradigm, rather than the regular grammars used in DTDs and XML schemas. As an extensible, easy to use, open source tool Schematron is an extremely useful addition to the XML developers toolkit. The initial section of this paper conducts a brief overview of tree pattern validation, and some of the advantages it has in comparison to a regular grammar approach. This is followed by an outline of Schematron and the intended uses which have guided its design. The Schematron language is then discussed, covering all major elements in the language with examples of their 1 of 14 Schematron: validating XML using XSLT usage. -

XML Information Set
XML Information Set XML Information Set W3C Recommendation 24 October 2001 This version: http://www.w3.org/TR/2001/REC-xml-infoset-20011024 Latest version: http://www.w3.org/TR/xml-infoset Previous version: http://www.w3.org/TR/2001/PR-xml-infoset-20010810 Editors: John Cowan, [email protected] Richard Tobin, [email protected] Copyright ©1999, 2000, 2001 W3C® (MIT, INRIA, Keio), All Rights Reserved. W3C liability, trademark, document use and software licensing rules apply. Abstract This specification provides a set of definitions for use in other specifications that need to refer to the information in an XML document. Status of this Document This section describes the status of this document at the time of its publication. Other documents may supersede this document. The latest status of this document series is maintained at the W3C. This is the W3C Recommendation of the XML Information Set. This document has been reviewed by W3C Members and other interested parties and has been endorsed by the Director as a W3C Recommendation. It is a stable document and may be used as reference material or cited as a normative reference from another document. W3C's role in making the Recommendation is to draw attention to the specification and to promote its widespread deployment. This enhances the functionality and interoperability of the file:///C|/Documents%20and%20Settings/immdca01/Desktop/xml-infoset.html (1 of 16) [8/12/2002 10:38:58 AM] XML Information Set Web. This document has been produced by the W3C XML Core Working Group as part of the XML Activity in the W3C Architecture Domain. -

Schema Declaration in Xml Document
Schema Declaration In Xml Document Is Darin varying or propellant when cluck some suffusion motive melodically? When Anton interdepend his titters reap not gyrally enough, is Parsifal malnourished? Styled Winnie scollop confoundedly, he reincreasing his stopple very refreshfully. When a uri that they come back into account only applies when sales orders that document in order to the design Must understand attribute Should I define a global attribute that will indicate to implementation the criticality of extension elements? Create a DOM parser to use for the validation of an instance document. As such, the XML Schema namespace, and provides a mapping between NIEM concepts and the RDF model. It is a convention to use XSD or XS as a prefix for the XML Schema namespace, et al. XML documents have sufficient structure to guarantee that they can be represented as a hierarchical tree. Are expanded names universally unique? DOC format for easy reading. This site uses cookies. This schema fragment shows the definition of an association type that defines a relationship between a person and a telephone number. Furthermore, such as Adobe Acrobat Reader. In some cases, if any. The idea behind using URIs for namespace names are that URIs are designed to be unique and persistent. Note: The material discussed in this section also applies to validating when using the SAX parser. Finally, Relax NG Schema, even when the elements and attributes defined by Microsoft are present. The XML representation for assertions. Developers of domain schemas and other schemas that build on and extend the NIEM release schemas need to be able to define additional characteristics of common types. -

Instruction for Using XML Notepad
Using XML Notepad to Read, Edit, and Parse FGDC-CSDGM XML Metadata. Currently many tools exist that allow a user to work with XML metadata files. However, most of the main metadata creation/editing tools do not provide a means of validating a metadata record for compliance with the FGDC-CSDGM standard or its variants, such as the Biological Data Profile (BDP) standard. One of the most reliable ways to validate metadata files (that is, check files for completion and/or errors) is with the USGS Metadata Parser (MP) utilities. The MP tool and the other tools distributed in the package were developed by Peter Schweitzer and are freely available online (http://geology.usgs.gov/tools/metadata/tools/doc/mp.html). Once configured properly, MP can process metadata files and be used to produce a text file with a list of all errors found. A user can then use this list of errors to find and correct the problems using a text editor or the metadata editor of their choice. The challenge with this method is that finding and correcting the error within a metadata editor based solely on the error message from MP can be confusing and frustrating. Additionally, if there are many errors or complex problems to correct, the process will require multiple iterations of running MP and subsequently correcting errors in a metadata editor. All in all, the process can be fairly time consuming and onerous, especially for those without a detailed understanding of the FGDC-CSDGM standard. The methodology for metadata editing and validation described in this document tries to address some of these problems with an alternative approach. -

Cisco XML Schemas
CHAPTER 14 Cisco XML Schemas This chapter contains information about common XML schemas. The structure and allowable content of the XML request and response instances supported by the Cisco IOS XR XML application programming interface (API) are documented by means of XML schemas (.xsd files). The XML schemas are documented using the standard World Wide Web Consortium (W3C) XML schema language, which provides a much more powerful and flexible mechanism for describing schemas than can be achieved using Document Type Definitions (DTDs). The set of XML schemas consists of a small set of common high-level schemas and a larger number of component-specific schemas as described in this chapter. For more information on the W3C XML Schema standard, see this URL: http://www.w3.org/XML/Schema This chapter contains these sections: • XML Schema Retrieval, page 14-135 • Common XML Schemas, page 14-136 • Component XML Schemas, page 14-136 XML Schema Retrieval The XML schemas that belong to the features in a particular package are obtained as a .tar file from cisco.com. To retrieve the XML schemas, you must: 1. Click this URL to display the Downloads page: http://tools.cisco.com/support/downloads/go/Redirect.x?mdfid=268437899 Note Select Downloads. Only customer or partner viewers can access the Download Software page. Guest users will get an error. 2. Select Cisco IOS XR Software. 3. Select IOS XR XML Schemas. 4. Select the XML schema for your platform. Once untarred, all the XML schema files appear as a flat directory of .xsd files and can be opened with any XML schema viewing application, such as XMLSpy.