Openvms Advanced Server and Linux SAMBA with Windows Clients Chpt8 Apache Web Server for Openvms and Linux
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Flashboot User Manual
FlashBoot User Manual © 2015 Mikhail Kupchik Contents 3 Table of Contents Foreword 0 Part I Introduction 5 1 Product................................................................................................................................... Overview 5 2 Why USB................................................................................................................................... Flash Disks? 5 3 Why FlashBoot?................................................................................................................................... 6 4 System................................................................................................................................... Requirements 7 5 Limitations................................................................................................................................... of Demo Version 8 6 Demo Version................................................................................................................................... -> Full Version 8 7 Support................................................................................................................................... & Feedback 8 Part II CD/DVD to USB conversions 9 1 Install ...................................................................................................................................full Win8/8.1/10 -> USB [BIOS mode] 9 2 Install................................................................................................................................... full -

Level One Benchmark Windows NT 4.0 Operating Systems V1.0.5
Level One Benchmark Windows NT 4.0 Operating Systems V1.0.5 Copyright 2003, The Center for Internet Security www.cisecurity.org Page 2 of 32 Terms of Use Agreement Background. CIS provides benchmarks, scoring tools, software, data, information, suggestions, ideas, and other services and materials from the CIS website or elsewhere (“Products”) as a public service to Internet users worldwide. Recommendations contained in the Products (“Recommendations”) result from a consensus-building process that involves many security experts and are generally generic in nature. The Recommendations are intended to provide helpful information to organizations attempting to evaluate or improve the security of their networks, systems and devices. Proper use of the Recommendations requires careful analysis and adaptation to specific user requirements. The Recommendations are not in any way intended to be a “quick fix” for anyone’s information security needs. No representations, warranties and covenants. CIS makes no representations, warranties or covenants whatsoever as to (i) the positive or negative effect of the Products or the Recommendations on the operation or the security of any particular network, computer system, network device, software, hardware, or any component of any of the foregoing or (ii) the accuracy, reliability, timeliness or completeness of any Product or Recommendation. CIS is providing the Products and the Recommendations “as is” and “as available” without representations, warranties or covenants of any kind. User agreements. By using the Products and/or the Recommendations, I and/or my organization (“we”) agree and acknowledge that: 1. No network, system, device, hardware, software or component can be made fully secure; 2. -

04 ISC 265 TESIS .Pdf
Sistema Académico Web SAITICC UNIVERSIDAD TÉCNICA DEL NORTE FACULTAD DE INGENIERÍA EN CIENCIAS APLICADAS CARRERA DE INGENIERÍA EN SISTEMAS COMPUTACIONALES TRABAJO DE GRADO PREVIO A LA OBTENCIÓN DEL TÍTULO EN INGENIERÍA EN SISTEMAS COMPUTACIONALES TEMA “SISTEMA ACADÉMICO WEB UTILIZANDO SOFTWARE LIBRE” AUTOR: Edwin Fernando Valencia Pavón. DIRECTOR: Ing. Pedro Granda. Ibarra - Ecuador 2012 – 2013 Fernando Valencia Pavón ii Sistema Académico Web SAITICC CERTIFICACIÓN Certifico que el trabajo de Tesis ― IMPLEMENTACIÓN DE UN SISTEMA ACADEMICO WEB PARA EL INSTITUTO TECNOLÓGICO SUPERIOR DE LA INDUSTRIA DEL CUERO DEL CANTÓN COTACACHI” con el aplicativo "DISEÑO E IMPLEMENTACION DELSISTEMA ACADEMICO WEB PARA EL INSTITUTO TECNOLOGICO DE LA INSDUSTRIA DEL CUERO. ha sido realizado en su totalidad por la señor: Edwin Fernando Valencia Pavón ………………………………………… Ing. Pedro Granda Director de la Tesis. Fernando Valencia Pavón iii Sistema Académico Web SAITICC UNIVERSIDAD TÉCNICA DEL NORTE BIBLIOTECA UNIVERSITARIA AUTORIZACIÓN DE USO Y PUBLICACIÓN A FAVOR DE LA UNIVERSIDAD TÉCNICA DEL NORTE IDENTIFICACIÓN DE LA OBRA La Universidad Técnica del Norte dentro del proyecto Repositorio Digital Institucional, determino la necesidad de disponer de textos completos en formato digital con la finalidad de apoyar los procesos de investigación, docencia y extensión de la Universidad. Por medio del presente documento dejo sentada mi voluntad de participar en este proyecto, para lo cual pongo a disposición la siguiente información: DATOS DE CONTACTO CÉDULA DE IDENTIDAD: 100316986-7 APELLIDOS Y NOMBRES: Valencia Pavón Edwin Fernando DIRECCIÓN: Urbanización María José EMAIL: [email protected] TELÉFONO FIJO: 062928-583 TELÉFONO MÓVIL (0968398896) DATOS DE LA OBRA TÍTULO: SISTEMA ACADÉMICO WEB UTILIZANDO SOFTWARE LIBRE. AUTOR: EDWIN FERNANDO VALENCIA PAVÓN FECHA: Julio-2013 PROGRAMA: PREGRADO TÍTULO POR EL QUE INGENIERÍA EN SISTEMAS COMPUTACIONALES OPTA: DIRECTOR: ING. -

Windows Intruder Detection Checklist
Windows Intruder Detection Checklist http://www.cert.org/tech_tips/test.html CERT® Coordination Center and AusCERT Windows Intruder Detection Checklist This document is being published jointly by the CERT Coordination Center and AusCERT (Australian Computer Emergency Response Team). printable version A. Introduction B. General Advice Pertaining to Intrusion Detection C. Look for Signs that Your System may have been Compromised 1. A Word on Rootkits 2. Examine Log Files 3. Check for Odd User Accounts and Groups 4. Check All Groups for Unexpected User Membership 5. Look for Unauthorized User Rights 6. Check for Unauthorized Applications Starting Automatically 7. Check Your System Binaries for Alterations 8. Check Your Network Configurations for Unauthorized Entries 9. Check for Unauthorized Shares 10. Check for Any Jobs Scheduled to Run 11. Check for Unauthorized Processes 12. Look Throughout the System for Unusual or Hidden Files 13. Check for Altered Permissions on Files or Registry Keys 14. Check for Changes in User or Computer Policies 15. Ensure the System has not been Joined to a Different Domain 16. Audit for Intrusion Detection 17. Additional Information D. Consider Running Intrusion Detection Systems If Possible 1. Freeware/shareware Intrusion Detection Systems 2. Commercial Intrusion Detection Systems E. Review Other AusCERT and CERT Documents 1. Steps for Recovering from a Windows NT Compromise 2. Windows NT Configuration Guidelines 3. NIST Checklists F. Document Revision History A. Introduction This document outlines suggested steps for determining whether your Windows system has been compromised. System administrators can use this information to look for several types of break-ins. We also encourage you to review all sections of this document and modify your systems to address potential weaknesses. -

Infosec Year in Review -- 1999
InfoSec Year In Review -- 1999 M. E. Kabay, PhD, CISSP. Security Leader, INFOSEC Group, AtomicTangerine Inc. Category 11 Breaches of confidentiality Date 1999-01-29 Keyword data leakage privacy confidentiality control Web Source, Vol, No. RISKS 20 18 The Canadian consumer-tracking service Air Miles inadvertently left 50,000 records of applicants for its loyalty program publicly accessible on their Web site for an undetermined length of time. The Web site was offline as of 21 January until the problem was fixed. Date 1999-02-03 Keyword data leakage Web script QA vulnerability confidentiality Source, Vol, No. WIRED via PointCast An error in the configuration or programming of the F. A. O. Schwarz Web site resulted paradoxically in weakening the security of transactions deliberately completed by FAX instead of through SSL. Customers who declined to send their credit-card numbers via SSL ended up having their personal details — address and so forth — stored in a Web page that could be accessed by anyone entering a URL with an appropriate (even if randomly chosen) numerical component. Date 1999-02-10 Keyword e-commerce credit card personal information password privacy Source, Vol, No. RISKS 20 20 Prof. Ross Anderson of Cambridge University analyzed requirements on the AMAZON.COM online bookstore for credit card number, password, and personal details such as phone number. He identified several risks: (1) merchant retention of credit card numbers poses a far higher risk of capture than of capture in transit; (2) adding a password increases the likelihood of compromise because so many naïve users choose bad passwords and then write them down; (3) even the British site for Amazon contravenes European rules on protecting consumer privacy; (3) such practices make it easier for banks to reject their clients' claims of fraudulent use of their credit-card numbers. -

Unit 5 Windows 2000/XP History, and Data Management
Unit 5 Windows 2000/XP History, and Data Management Copyright © 2002 Heathkit Company, Inc. All rights reserved. Microsoft Windows98 Microsoft WindowsMe Microsoft Windows 2000 Professional Microsoft WindowsXP 2 Windows 2000/XP or Windows 9x (95/98/Me)? Windows 9x Windows 2000/XP Runs on today’s Runs on “nearly any hardware, doesn’t run old hardware” well or at all on marginal hardware Secure, more difficult to Open, easy to configure configure Supports lots of Device support somewhat devices limited, so far 3 Windows XP or Windows 9x? If you need: Choose: Reliable, solid security Windows 2000/XP “Crash-proof” system Windows 2000/XP Support for older/slower Windows 9x machines Easy setup and configuration Windows 9x Support for that older scanner, Windows 9x CD Writer, NIC, Video, etc. 4 The Windows Business Consumer Universe 1990 Windows 3.1 Windows NT 3.51 Windows for Workgroups Windows NT 4 Windows 95 Windows 98 Windows 2000 Windows Me Today Windows XP Pro/Home 5 The Windows Business Consumer Universe 1990 Windows 3.1 Windows NT 3.51 Windows for Workgroups Windows NT 4 Windows 95 Windows 98 Windows 2000 Windows Me Today Windows XP Pro/Home 6 The TheWindows Windows Business Universe Consumer Universe 1990 Windows 3.1 Windows NT 3.51 Windows for Workgroups Windows NT 4 Windows 95 Windows 98 Windows 2000 Windows Me Today Windows XP Pro/Home 7 Windows XP Flavors • Windows XP Professional • Windows XP Home • Windows 2003 Server • Windows 2003 Enterprise Server • Windows 2003 Datacenter Server 8 Windows Package Types • Upgrade • Full Version -
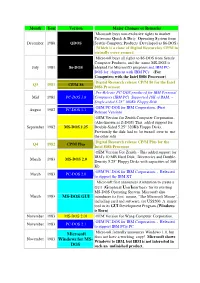
Microsoft Windows for MS
Month Year Version Major Changes or Remarks Microsoft buys non-exclusive rights to market Pattersons Quick & Dirty Operating System from December 1980 QDOS Seattle Computer Products (Developed as 86-DOS) (Which is a clone of Digital Researches C P/M in virtually every respect) Microsoft buys all rights to 86-DOS from Seattle Computer Products, and the name MS-DOS is July 1981 86-DOS adopted for Microsoft's purposes and IBM PC- DOS for shipment with IBM PCs (For Computers with the Intel 8086 Processor) Digital Research release CP/M 86 for the Intel Q3 1981 CP/M 86 8086 Processer Pre-Release PC-DOS produced for IBM Personal Mid 1981 PC-DOS 1.0 Computers (IBM PC) Supported 16K of RAM, ~ Single-sided 5.25" 160Kb Floppy Disk OEM PC-DOS for IBM Corporation. (First August 1982 PC-DOS 1.1 Release Version) OEM Version for Zenith Computer Corporation.. (Also known as Z-DOS) This added support for September 1982 MS-DOS 1.25 Double-Sided 5.25" 320Kb Floppy Disks. Previously the disk had to be turned over to use the other side Digital Research release CP/M Plus for the Q4 1982 CP/M Plus Intel 8086 Processer OEM Version For Zenith - This added support for IBM's 10 MB Hard Disk, Directories and Double- March 1983 MS-DOS 2.0 Density 5.25" Floppy Disks with capacities of 360 Kb OEM PC-DOS for IBM Corporation. - Released March 1983 PC-DOS 2.0 to support the IBM XT Microsoft first announces it intention to create a GUI (Graphical User Interface) for its existing MS-DOS Operating System. -

L38 Ñ Windows XP
History History (cont.) (Timeline from www.cgonline.com) 10/81 — IBM PC (“Personal Computer”) 10/88 — OS/2 1.1 (Windows-like GUI, end and PC-DOS 1.0 of collaboration when IBM gets upset with Microsoft for improving Windows) 3/83 — Microsoft MS-DOS 2.0 (hard disk, file system) 5/90 — Windows 3.0 (big success!) 11/83 — Windows announced (vaporware!) 4/92 — Windows 3.1 (bug fixes etc.) 11/84 — MS-DOS 3.1 10/92 — Windows for Workgroups 3.1 (adds networking, but fails in market) 11/85 — Windows 1.0 (tiled windows, doesn’t do well in market) 5/93 — Windows NT 3.1 (visually like Windows 3.1, but stable 32-bit platform) 4/87 — IBM & Microsoft OS/2 1.0 (next generation, DOS-like command lines) 11/93 — Windows for Workgroups 3.11 (precursor to Windows 95) 12/87 — Windows/386 (uses 80386’s virtual memory to allow safe “preemptive” 5/94 — MS-DOS 6.22 (DOS final version) multitasking) 9/94 — Windows NT 3.5 6/95 — Windows NT 3.51 (faster) 1 Fall 2002, Lecture 38 2 Fall 2002, Lecture 38 History (cont.) What is Windows XP? 8/95 — Windows 95 (originally Windows I 32/64 -bit preemptive multitasking 4.0) (long file names, plug and play operating system for AMD K6/7, Intel hardware, taskbar and Start menu, IA32/64 and later microprocessors HUGE success in market!) ● Replaces Windows 95/98/Me as well as Windows NT/200 7/96 — Windows NT 4.0 (Windows 95 GUI, first successful version of NT) I Key goals 6/98 — Windows 98 (Windows 95 + ● security, reliability, ease of use Internet Explorer 4.0, success in market) ● Windows and POSIX compliance ● high performance, extensibility 2/00 — Windows 2000 (Windows NT 4.0 + plug and play, DirectX, USB, etc.) ● portability, international support 9/00 — Windows Me (Millennium Edition) I Various versions: XP Personal, XP (Windows 98 + IE 5.0, media support, Professional, XP Server last version in Windows 9x line) I Uses a micro-kernel architecture 9/01 — Windows XP (combines Windows ● Subsystems to provide OS personalities 2000 and ME, but based on NT/2000) for Win32, POSIX, etc. -

MICROSOFT WINDOWS Early Versions Main Articles: Windows 1.0
MICROSOFT WINDOWS Early versions Main articles: Windows 1.0, Windows 2.0, and Windows 2.1x Windows 1.0, the first version, released in 1985 The history of Windows dates back to September 1981, when Chase Bishop, a computer scientist, designed the first model of an electronic device and project "Interface Manager" was started. It was announced in November 1983 (after the Apple Lisa, but before the Macintosh) under the name "Windows", but Windows 1.0 was not released until November 1985.[5] Windows 1.0 achieved little popularity and was to compete with Apple's own operating system. Windows 1.0 is not a complete operating system; rather, it extends MS-DOS. The shell of Windows 1.0 is a program known as the MS- DOS Executive. Components included Calculator, Calendar, Cardfile, Clipboard viewer, Clock, Control Panel, Notepad, Paint, Reversi, Terminal and Write. Windows 1.0 does not allow overlapping windows. Instead all windows are tiled. Only modal dialog boxes may appear over other windows. Windows 2.0 was released in December 1987 and was more popular than its predecessor. It features several improvements to the user interface and memory management.[citation needed] Windows 2.03 changed the OS from tiled windows to overlapping windows. The result of this change led to Apple Computer filing a suit against Microsoft alleging infringement on Apple's copyrights.[6][7] Windows 2.0 also introduced more sophisticated keyboard shortcuts and could make use of expanded memory. Windows 2.1 was released in two different versions: Windows/286 and Windows/386. Windows/386 uses the virtual 8086 mode of Intel 80386 to multitask several DOS programs and the paged memory model to emulate expanded memory using available extended memory. -

Major System Files, and Their Purpose: Windows 9X –Specific Files • IO.SYS the Io.Sys File Is an MS-DOS and Windows 9X
Major System Files, and their purpose: Windows 9x –specific files IO.SYS The io.sys file is an MS-DOS and Windows 9x hidden system file that is used to load the operating system each time the computer boots. The file is not editable using normal text editors. MSDOS.SYS The MSDOS.SYS file is a hidden system file created on the root of the boot drive. To edit this file, type edit msdos.sys. The PC boot environment can be changed by changing the file contents. Given below is a typicalMSDOS.SYS file: Below is a sample MSDOS.SYS File [Paths] WinDir=C:\WINDOWS WinBootDir=C:\WINDOWS HostWinBootDrv=C [Options] BootGUI=1 Network=1 BootMulti=1 ; ;The following lines are required for compatibility with other programs. ;Do not remove them (MSDOS.SYS needs to be >1024 bytes). AUTOEXEC.BAT An AUTOEXEC.BAT file contains DOS commands that are executed automatically when a PC boots. The file is usually located in the root directory of the hard drive of the computer. The AUTOEXEC.BAT file is used to set defaults and to run programs that should be executed during startup. Example: PROMPT $P$G Use the PROMPT command to alter the default DOS prompt. The above command makes the DOS prompt display the current path and drive, and is very useful. COMMAND.COM 1. It does: The file contains internal command set and error messages 2. Default Attributes: Nil 3. Is it required for OS Start up: YES 4. Responsible for displaying the command prompt in a DOS based computer. -

JAMS User Guide
JAMS User Guide Order Number: JAMS-UG-42 This manual provides a complete description of the Job Access & Management System. Revision/Update Information: This manual supersedes the Guide to the Job Access & Management System, Version 4.0. Operating System and Version: OpenVMS/VAX Version 6.2 or higher, OpenVMS/AXP V6.2 or higher Software Version: JAMS Version 4.2 The information in this document is subject to change without notice and should not be construed as a commitment by MVP Systems Incorporated. MVP Systems, Inc. assumes no responsibility for any errors that may appear in this document. The software described in this document is furnished under a license and may be used or copied only in accordance with the terms of this license. Restricted Rights Notice: Use, duplication, or disclosure by the U.S. Government is subject to restrictions set forth in subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013. All Rights Reserved. Printed in the U.S.A. If you have questions about JAMS please feel free to call JAMS technical support at (866) 259-5267. Technical support is available around the clock, 24 hours a day, 7 days a week. The mailing address is: TECHNICAL SUPPORT DEPT. MVP SYSTEMS INC. 2700 E. MAIN ST. SUITE 108 COLUMBUS, OH 43209 E-Mail: [email protected] WWW: http://JAMS.mvpsi.com WWW: http://www.mvpsi.com The following are trademarks of Hewlett-Packard Company: Alpha, DECnet, DECwindows, OpenVMS, VAX, VMS, VMScluster. Window and Windows NT are registered trademarks of Microsoft Corporation. -

Bill Gates' Original Dream When He Created Microsoft Was to Have
Bill Gates’ original dream when he created Microsoft was to have “a computer on every desk and i n every home, all running Microsoft software.” Clearly, he accomplished that goal. Depending on whose statistics you want to believe, Windows has a market share in the high 80% - low 90% rang e. So, unless you run Linux or prefer Mac OS X, chances are you’re a Windows user. When it comes to desktop operating systems, your choices are really pretty narrow. You either run Windows, or you do some Unix-like OS. There are the 12,000 different Linux distributions. There’ s always FreeBSD if you prefer your Unix without a Finnish flavor. You could go the vendor route and run AIX or HP-UX. Sun has Solaris, and as much as you might want to, you can’t forget SCO. And of course, there’s always Mac OS X. Although it may sound like variety when it comes down to it, it’s still Windows vs. Unix. There are other options, or at least there USED to be. Here are a list of five of the best operating s ystems that you probably never used. OS/2 No discussion can be had of Microsoft alternatives without mentioning OS/2. Until Microsoft ship ped Windows 2000 Professional, OS/2 4.0 was probably my desktop OS of choice. For the purpos es of this section, I’m referring to OS/2 2.0 and later, not IBM and Microsoft’s ill fated OS/2 1.x s eries. IBM billed OS/2 as being a “Better DOS than DOS” and a “Better Windows than Windows”.