Servicio De Escritorio Remoto En Cluster Virtualizado Usando Tecnología Xen Server Y Windows 2012
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Embedded Linux for Thin Clients Next Generation (Elux® NG) Version 1.25
Embedded Linux for Thin Clients Next Generation (eLux® NG) Version 1.25 Administrator’s Guide Build Nr.: 23 UniCon Software GmbH www.myelux.com eLux® NG Information in this document is subject to change without notice. Companies, names and data used in examples herein are fictitious unless otherwise noted. No part of this document may be reproduced or transmitted in any form or by any means, electronic or mechanical, for any purpose, without the express consent of UniCon Software GmbH. © by UniCon 2005 Software GmbH. All rights reserved eLux is a registered trademark of UniCon Software GmbH in Germany. Accelerated-X is a trademark of Xi Graphics, Inc. Adobe, Acrobat Reader and PostScript are registered trademarks of Adobe Systems Incorporated in the United States and/or other countries. Broadcom is a registered trademark of Broadcom Corporation in the U.S. and/or other countries. CardOS is a registered trademark and CONNECT2AIR is a trademark of Siemens AG in Germany and/or other countries. Cisco and Aironet are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and certain other countries. Citrix, Independent Computing Architecture (ICA), Program Neighborhood, MetaFrame, and MetaFrame XP are registered trademarks or trademarks of Citrix Systems, Inc. in the United States and other countries. CUPS and the Common UNIX Printing System are the trademark property of Easy Software Products. DivX is a trademark of Project Mayo. Ericom and PowerTerm are registered trademarks of Ericom Software in the United States and/or other countries. Gemplus is a registered trademark and GemSAFE a trademark of Gemplus. -

Institutionen För Datavetenskap Department of Computer and Information Science
Institutionen för datavetenskap Department of Computer and Information Science Final thesis Implementing extended functionality for an HTML5 client for remote desktops by Samuel Mannehed LIU-IDA/LITH-EX-A—14/015--SE 6/28/14 Linköpings universitet Linköpings universitet SE-581 83 Linköping, Sweden 581 83 Linköping Final thesis Implementing extended functionality for an HTML5 client for remote desktops by Samuel Mannehed LIU-IDA/LITH-EX-A--14/015--SE June 28, 2014 Supervisors: Peter Åstrand (Cendio AB), Maria Vasilevskaya (IDA) Examiner: Prof. Simin Nadjm-Tehrani På svenska Detta dokument hålls tillgängligt på Internet – eller dess framtida ersättare – under en längre tid från publiceringsdatum under förutsättning att inga extra-ordinära omständigheter uppstår. Tillgång till dokumentet innebär tillstånd för var och en att läsa, ladda ner, skriva ut enstaka kopior för enskilt bruk och att använda det oförändrat för ickekommersiell forskning och för undervisning. Överföring av upphovsrätten vid en senare tidpunkt kan inte upphäva detta tillstånd. All annan användning av dokumentet kräver upphovsmannens medgivande. För att garantera äktheten, säkerheten och tillgängligheten finns det lösningar av teknisk och administrativ art. Upphovsmannens ideella rätt innefattar rätt att bli nämnd som upphovsman i den omfattning som god sed kräver vid användning av dokumentet på ovan beskrivna sätt samt skydd mot att dokumentet ändras eller presenteras i sådan form eller i sådant sammanhang som är kränkande för upphovsmannens litterära eller konstnärliga anseende eller egenart. För ytterligare information om Linköping University Electronic Press se förlagets hemsida http://www.ep.liu.se/ In English The publishers will keep this document online on the Internet - or its possible replacement - for a considerable time from the date of publication barring exceptional circumstances. -
IGEL Universal Desktop Linux User Guide
IGEL Thin Clients Universal Desktop User Guide For IGEL Thin Clients with IGEL Flash Linux Copyright © 2009 IGEL Technology Ver. UD-LX 4.02.100 12/2009 Important Information Copyright This publication is protected under international copyright laws, with all rights reserved. No part of this manual, including the products and software described in it, may be reproduced, manipulated, transmitted, transcribed, stored in a retrieval system, or translated into any language in any form or by any means, except documentation kept by the purchaser for backup purposes, without the express written permission of IGEL Technology GmbH. Disclaimer The information in this document is subject to change without notice. IGEL Technology GmbH makes no representations or warranties with respect to the contents hereof and specifically disclaim any implied warranties of merchantability or fitness for any particular purpose. Further, IGEL Technology GmbH reserves the right to revise this publication and to make changes from time to time in the content hereof without obligation of IGEL Technology GmbH to notify any person of such revision or changes. Trademark Recognition IGEL is a registered trademark of IGEL Technology GmbH. MicrosoftTM WindowsTM is a registered trademark of Microsoft Corporation. JavaTM is a registered trademark of Sun Microsystems, Inc. VMwareTM is a registered trademark of VMware, Inc. PowerTermTM WebConnectTM and PowerTermTM InterConnectTM are registered trademarks of Ericom Software. CUPSTM and the CUPS logo are trademarks of Apple Inc. All other products and corporate names appearing in this manual may or may not be registered trademarks or copyrights of their respective companies, and are used only for identification or explanation and to the owner’s benefit. -

Unpermitted Resources
Process Check and Unpermitted Resources Common and Important Virtual Machines Parallels VMware VirtualBox CVMCompiler Windows Virtual PC Other Python Citrix Screen/File Sharing/Saving .exe File Name VNC, VPN, RFS, P2P and SSH Virtual Drives ● Dropbox.exe ● Dropbox ● OneDrive.exe ● OneDrive ● <name>.exe ● Google Drive ● etc. ● iCloud ● etc. Evernote / One Note ● Evernote_---.exe ● onenote.exe Go To Meeting ● gotomeeting launcher.exe / gotomeeting.exe TeamViewer ● TeamViewer.exe Chrome Remote ● remoting_host.exe www.ProctorU.com ● [email protected] ● 8883553043 Messaging / Video (IM, IRC) / .exe File Name Audio Bonjour Google Hangouts (chrome.exe - shown as a tab) (Screen Sharing) Skype SkypeC2CPNRSvc.exe Music Streaming ● Spotify.exe (Spotify, Pandora, etc.) ● PandoraService.exe Steam Steam.exe ALL Processes Screen / File Sharing / Messaging / Video (IM, Virtual Machines (VM) Other Saving IRC) / Audio Virtual Box Splashtop Bonjour ● iChat ● iTunes ● iPhoto ● TiVo ● SubEthaEdit ● Contactizer, ● Things ● OmniFocuse phpVirtualBox TeamViewer MobileMe Parallels Sticky Notes Team Speak VMware One Note Ventrilo Windows Virtual PC Dropbox Sandboxd QEM (Linux only) Chrome Remote iStumbler HYPERBOX SkyDrive MSN Chat Boot Camp (dual boot) OneDrive Blackboard Chat CVMCompiler Google Drive Yahoo Messenger Office (Word, Excel, Skype etc.) www.ProctorU.com ● [email protected] ● 8883553043 2X Software Notepad Steam AerooAdmin Paint Origin AetherPal Go To Meeting Spotify Ammyy Admin Jing Facebook Messenger AnyDesk -

Igel Os: Questions & Answers
Q & A IGEL OS: QUESTIONS & ANSWERS What is IGEL OS? What is the IGEL UD Pocket? IGEL OS is a Linux-based operating system optimized The IGEL UD Pocket is a portable and powerful end- for secure, scalable delivery of virtual desktops and point solution. No larger than a paper clip, it allows you cloud workspaces. Referred to as “firmware”, IGEL to boot from the local operating system on a PC, laptop OS replaces (permanent or temporary) an existing or other compatible endpoint device. operating system, which means the legacy operating system will be permanently removed from the device’s hard disk. How is the UD Pocket started? Simply insert the UD Pocket into the USB port of the How can I get IGEL OS? host device. The device boots from the UD Pocket to access the IGEL OS and user interface. IGEL OS is part of the IGEL Workspace Edition, a bundled license offer, together with IGEL’s manage- ment software IGEL Universal Management Suite How is IGEL OS installed and deployed? (UMS), a multimedia Codec pack, high availability The most common way to install IGEL OS in a single functionality and a REST API. device is to start the target PC, laptop, or thin client using a bootable USB stick that runs the IGEL OS How can I get IGEL OS on my endponts? Creator tool. If you want to install IGEL OS on several devices, please use the OS Deployment Appliance. First identify the devices if you want to convert, either Comprehensive support is provided by the IGEL permanently or temporarily, into IGEL-managed end- Knowledge Base. -

Upgrading and Performance Analysis of Thin Clients in Server Based Scientific Computing
Institutionen för Systemteknik Department of Electrical Engineering Examensarbete Upgrading and Performance Analysis of Thin Clients in Server Based Scientific Computing Master Thesis in ISY Communication System By Rizwan Azhar LiTH-ISY-EX - - 11/4388 - - SE Linköping 2011 Department of Electrical Engineering Linköpings Tekniska Högskola Linköpings universitet Linköpings universitet SE-581 83 Linköping, Sweden 581 83 Linköping, Sweden Upgrading and Performance Analysis of Thin Clients in Server Based Scientific Computing Master Thesis in ISY Communication System at Linköping Institute of Technology By Rizwan Azhar LiTH-ISY-EX - - 11/4388 - - SE Examiner: Dr. Lasse Alfredsson Advisor: Dr. Alexandr Malusek Supervisor: Dr. Peter Lundberg Presentation Date Department and Division 04-02-2011 Department of Electrical Engineering Publishing Date (Electronic version) Language Type of Publication ISBN (Licentiate thesis) X English Licentiate thesis ISRN: Other (specify below) X Degree thesis LiTH-ISY-EX - - 11/4388 - - SE Thesis C-level Thesis D-level Title of series (Licentiate thesis) 55 Report Number of Pages Other (specify below) Series number/ISSN (Licentiate thesis) URL, Electronic Version http://www.ep.liu.se Publication Title Upgrading and Performance Analysis of Thin Clients in Server Based Scientific Computing Author Rizwan Azhar Abstract Server Based Computing (SBC) technology allows applications to be deployed, managed, supported and executed on the server and not on the client; only the screen information is transmitted between the server and client. This architecture solves many fundamental problems with application deployment, technical support, data storage, hardware and software upgrades. This thesis is targeted at upgrading and evaluating performance of thin clients in scientific Server Based Computing (SBC). Performance of Linux based SBC was assessed via methods of both quantitative and qualitative research. -

Interactive HPC Computation with Open Ondemand and Fastx
Interactive HPC Computation with Open OnDemand and FastX eResearchNZ, February, 2021 [email protected] More Data, More Complexity ● Datasets and problem complexity [1] is growing faster than performance of personal computational systems. ● In late 2018 a predictive study [2] of what was described as "the Global Datasphere", data that is "created, captured, or replicated ... will grow from 33 Zettabytes (ZB) in 2018 to 175 ZB by 2025". ● Performance improvements gained by increased clock-speed on a processor come at a cost of additional heat, causing a breakdown in Dennard scaling in the early 2000s [3], that has continued to contemporary times. ● There have been several technological improvements over the decades that have mitigated what would otherwise be a very unfortunate situation for the processing of large datasets (multicore, GPUs, parallel programming, SSD, NVMe, high-speed interconnect etc) ● A preferred choice is high performance computing (HPC) which, due to its physical architecture, operating system, and optimised application installations, is best suited for such processing. ● Command-line Tools can be 235x Faster than your Hadoop Cluster (https://adamdrake.com/command-line-tools-can-be-235x-faster-than-your-hadoop- cluster.html). SQL query runtime from 380 hours to 12 with two Unix commands (https://www.spinellis.gr/blog/20180805/) More Data, More Complexity Compute on HPC, visualise locally ● The motto of his Richard Hamming's Numerical Methods for Scientists and Engineers (1962) was "The purpose of computing is insight, not numbers". How is this insight to be achieved? From raw data can you mentally create a real-world mental image of what the data represents? ● Complexity will be beyond most people's cognitive capacity, leading to the need for computer graphics as a requisite heuristic. -

List of TCP and UDP Port Numbers from Wikipedia, the Free Encyclopedia
List of TCP and UDP port numbers From Wikipedia, the free encyclopedia This is a list of Internet socket port numbers used by protocols of the transport layer of the Internet Protocol Suite for the establishment of host-to-host connectivity. Originally, port numbers were used by the Network Control Program (NCP) in the ARPANET for which two ports were required for half- duplex transmission. Later, the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) needed only one port for full- duplex, bidirectional traffic. The even-numbered ports were not used, and this resulted in some even numbers in the well-known port number /etc/services, a service name range being unassigned. The Stream Control Transmission Protocol database file on Unix-like operating (SCTP) and the Datagram Congestion Control Protocol (DCCP) also systems.[1][2][3][4] use port numbers. They usually use port numbers that match the services of the corresponding TCP or UDP implementation, if they exist. The Internet Assigned Numbers Authority (IANA) is responsible for maintaining the official assignments of port numbers for specific uses.[5] However, many unofficial uses of both well-known and registered port numbers occur in practice. Contents 1 Table legend 2 Well-known ports 3 Registered ports 4 Dynamic, private or ephemeral ports 5 See also 6 References 7 External links Table legend Official: Port is registered with IANA for the application.[5] Unofficial: Port is not registered with IANA for the application. Multiple use: Multiple applications are known to use this port. Well-known ports The port numbers in the range from 0 to 1023 are the well-known ports or system ports.[6] They are used by system processes that provide widely used types of network services. -

IGEL Technology to Launch Latest All-In-One UD9 Thin Client with Large Integrated Flat Panel Display Submitted By: the Amber Group Thursday, 25 March 2010
IGEL Technology to launch latest all-in-one UD9 thin client with large integrated flat panel display Submitted by: The Amber Group Thursday, 25 March 2010 The new IGEL Universal Desktop 9 is ideal for the Retail, Leisure, Manufacturing and Health industries with its large LCD screen, small desktop footprint, touchscreen and wireless capabilities Reading, UK, 25th March 2010 - IGEL Technology today announced its new integrated 21,5 inch (54cm) flat panel LCD thin client, designed for customer-facing businesses and space-constrained environments. The UD9 is powered by a 1.6 Ghz Intel Atom processor and comes available with Linux or Windows Embedded Standard operating systems and options for touchscreen display, wireless LAN capability and an integrated smartcard reader. These features, as part of the integrated design, make the UD9 perfect for use at retail points of sale, in public areas such as libraries and council information points, on space-constrained manufacturing lines and hospital wards. The product will be available from May 2010. The UD9 comes with the IGEL Advanced Pack firmware that can connect to almost any application, media or peripheral. It includes support for Citrix® ICA and Microsoft® RDP as well as VMware View and the Leostream® VDI client for connecting to virtual desktops. The Advanced firmware pack also supports services such as Flash, VoIP (Linux only), a native SAP GUI, NoMachine NX and ThinLinc printing as well as other web, multi-media, video conferencing and peripheral controls. Bundled with every UD9 is a full version of the IGEL Universal Management Suite. This powerful yet easy-to-use tool enables the centralised remote management of all IGEL clients, saving money, time and hassle. -
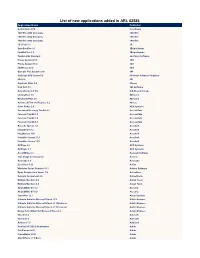
List of New Applications Added in ARL #2586
List of new applications added in ARL #2586 Application Name Publisher NetCmdlets 2016 /n software 1099 Pro 2009 Corporate 1099 Pro 1099 Pro 2020 Enterprise 1099 Pro 1099 Pro 2008 Corporate 1099 Pro 1E Client 5.1 1E SyncBackPro 9.1 2BrightSparks FindOnClick 2.5 2BrightSparks TaxAct 2002 Standard 2nd Story Software Phone System 15.5 3CX Phone System 16.0 3CX 3CXPhone 16.3 3CX Grouper Plus System 2021 3M CoDeSys OPC Server 3.1 3S-Smart Software Solutions 4D 15.0 4D Duplicate Killer 3.4 4Team Disk Drill 4.1 508 Software NotesHolder 2.3 Pro A!K Research Labs LibraryView 1.0 AB Sciex MetabolitePilot 2.0 AB Sciex Advanced Find and Replace 5.2 Abacre Color Picker 2.0 ACA Systems Password Recovery Toolkit 8.2 AccessData Forensic Toolkit 6.0 AccessData Forensic Toolkit 7.0 AccessData Forensic Toolkit 6.3 AccessData Barcode Xpress 7.0 AccuSoft ImageGear 17.2 AccuSoft ImagXpress 13.6 AccuSoft PrizmDoc Server 13.1 AccuSoft PrizmDoc Server 12.3 AccuSoft ACDSee 2.2 ACD Systems ACDSync 1.1 ACD Systems Ace Utilities 6.3 Acelogix Software True Image for Crucial 23. Acronis Acrosync 1.6 Acrosync Zen Client 5.10 Actian Windows Forms Controls 16.1 Actipro Software Opus Composition Server 7.0 ActiveDocs Network Component 4.6 ActiveXperts Multiple Monitors 8.3 Actual Tools Multiple Monitors 8.8 Actual Tools ACUCOBOL-GT 5.2 Acucorp ACUCOBOL-GT 8.0 Acucorp TransMac 12.1 Acute Systems Ultimate Suite for Microsoft Excel 13.2 Add-in Express Ultimate Suite for Microsoft Excel 21.1 Business Add-in Express Ultimate Suite for Microsoft Excel 21.1 Personal Add-in Express -
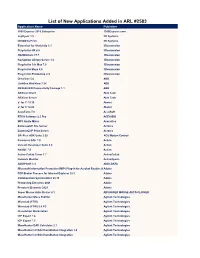
List of New Applications Added in ARL #2583
List of New Applications Added in ARL #2583 Application Name Publisher 1099 Express 2019 Enterprise 1099Express.com Lightyear 1.5 3D Systems DICOM to Print 3D Systems Extension for SketchUp 5.1 3Dconnexion Plug-In for NX 8.0 3Dconnexion 3DxWinCore 17.7 3Dconnexion Navigation Library Server 1.4 3Dconnexion Plug-In for 3ds Max 7.0 3Dconnexion Plug-In for Maya 6.0 3Dconnexion Plug-In for Photoshop 2.9 3Dconnexion DriveSize 5.6 ABB LinkOne WebView 3.24 ABB REX640 IED Connectivity Package 1.1 ABB ARXivar Client Able Tech ARXivar Server Able Tech a³ for C 19.10 AbsInt a³ for C 18.04 AbsInt AccuTerm 7.0 AccuSoft RTCA Software 2.3 Pro ACEA BIO MP3 Audio Mixer Acoustica ExtremeZ-IP File Server Acronis ExtremeZ-IP Print Server Acronis SPiiPlus ADK Suite 2.50 ACS Motion Control Pervasive.SQL 7.0 Actian Versant Developer Suite 6.0 Actian NoSQL 7.0 Actian Active Collab Timer 1.7 ActiveCollab Network Monitor ActiveXperts ADDIPACK 1.4 ADDI-DATA Microsoft Information Protection (MIP) Plug-in for Acrobat Reader 20.0Adobe PDF Broker Process for Internet Explorer 20.1 Adobe Collaboration Synchronizer 20.13 Adobe Photoshop Elements 2021 Adobe Premiere Elements 2021 Adobe Super Mouse Auto Clicker 4.1 ADVANCED MOUSE AUTO CLICKER MassHunter Mass Profiler Agilent Technologies MicroLab (FTIR) Agilent Technologies MicroLab (FTIR) 5.4 PC Agilent Technologies Dissolution Workstation Agilent Technologies ICP Expert 7.4 Agilent Technologies ICP Expert 7.3 Agilent Technologies MassHunter DAR Calculator 2.1 Agilent Technologies MassHunter LC/SQ ChemStation Integration -

Demystifying Africa's Cyber Security Poverty Line
Demystifying Africa’s Cyber Security Poverty Line Tanzania Chapter The Africa Cyber Immersion Centre is a state-of-the-art research, innovation and training facility that seeks to address Africa’s ongoing and long-term future needs through unique education, training, research, and practical applications. For more information Serianu Limited contact: [email protected] http://www.serianu.com Tanzania Cyber Security 3 Report Content Editor’s Note and Acknowledgement Cost of Cyber Crime We are excited to finally publish the 2nd edition of Tanzania We estimate that cyber-attacks cost Tanzanian 4 Cyber Security Report 2017. 54 businesses around $99.5 million a year. Foreword Sector Ranking in 2017 2017 has seen a jump in cyberattacks or cybercrimes. Cyber security is no longer a concern fof the Ransomware, DDoS attacks, data breaches were all financial & banking sectors only. 7 synonymous with 2017. 56 Executive Summary Home Security It is in our own best interests to make sure everyone – from the young to the old, on The global landscape of cyber threats is quickly changing. snapchat, facebook and twitter - know and 9 60 practice basic security habits. Top Trends Africa Cyber Security Framework We analysed incidents that occurred in 2017 and compiled Attackers are now launching increasingly a list of top trends that had a huge impact on the economic sophisticated attacks on everything from and social well-being of organisations and Tanzanian citizens. business critical infrastructure to everyday 13 69 devices such as mobile phones. Top Priorities for 2018 Appendixes 19 We have highlighted key priorities for 2018. 71 Cyber Intelligence Statistics, Analysis, & Trends References We have monitored organisations’ network for malware and cyber threat attacks such as brute-force attacks 25 against the organisation’s servers.