How to Enable AMD IOMMU in Coreboot
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Opnsense Your Next Open Source Firewall
OPNsense Your next open source firewall www.rhinolabsinc.com About OPNsense Highlights Businesses ProtEct your businEss nEtwork and sEcurE your connEctions. From thE stateful inspection firewall to thE inline intrusion detection & prevention systEm EvErything is includEd for frEE.UsE thE traffic shaper to EnhancE nEtwork pErformancE and prioritisE Businesses you voicE ovEr ip abovE othEr traffic. Backup your configuration to thE cloud automatically, no nEEd for manual backups anymorE! School Networks Limit and share available bandwidth evenly amongst studEnts and utilisE thE category based web filtering to filtEr unwantEd traffic such as adult contEnt and malicious wEbsitEs. Its Easy to sEtup as no additional plugins nor packagEs arE School Networks rEquirEd. TEach about sEcurity or usE our dEvElopmEnt documEntation to show how an ModEl ViEwEr ControllEr works. You and your studEnts arE invitEd to join thE Effort and OPNsEnsE community! About OPNsense Highlights Hotels & Campings Hotels and campIngs usually utIlIse a captIve portal to allow guests (paId) access to Internet for a lImIted duratIon. Guests need to logIn usIng a voucher that they can eIther buy or Hotels and Camping obtaIn for free at the receptIon. OPNsense has a buIlt-In captive portal wIth voucher support and can easIly create them on the fly. On The Road Even on the road OPNsense Is a great asset to your busIness as It offers OpenVPN and IPSec VPN solutIon wIth road warrior support. The easy client exporter make On The Road configurIng your OpenVPN SSL clIent setup a breeze. Remote Offices & SOHO UtIlIse the Integrated sIte to sIte VPN (IPsec or SSL VPN) to create a secure network connectIon to and from your remote offices. -

Ipfire Duobox Business, 4 GB RAM, 64 GB SSD
Item no.: 323825 IPFire DuoBox Business, 4 GB RAM, 64 GB SSD from 462,37 EUR Item no.: 323825 shipping weight: 1.20 kg Manufacturer: IPFire Product Description IPFire DuoBox Business, 4 GB RAM, 64 GB SSDThis Firewall version was specifically designed for small offices und home offices, in which a stable and fast Internet connection is essential. The Duo Box Business provides you with fast Internet, while being low-cost and energy-efficient. It keeps your business connected and, most importantly, it keeps your network safe. Main Features: ● 2x Gigabit Ethernet for LAN and WAN ● 1x 300 Mbit dual-band Wi-Fi with access point mode ● optionally upgradeable with LTE Scope of Delivery: ● System ● Power Cable ● PSU ● 2x WLAN antennas Specifications Application: Firewall application for SOHO, branch offices and IoT Type: aluminum profile construction without venting holes, black anodized Dimensions (W x D x H): 134 x 108 x 55 mm Weight: 1.2 kg Cooling: directly attached to chassis Operating conditions: 0 - 50 °C / 80 % rel. humidity CPU: Intel Pentium 3558U, 2x 1.7 GHz RAM: 4 GB DDR3L Mainboard: customized eNUC platform I/O front (standard): 1x RS232, 1x USB 3.0, 1x Audio I/O back: 2x HDMI, 2x USB 3.0, 2x RJ45 (Realtek GLAN) I/O internal: internal I/O might be occupied - depending on your configuration, 1x mSATA/mPCIe full size, 2x USB 2.0 Storage: 1x 2.5" 64 GB SSD (industrial, MLC, 0 - +70 °C ) Graphics: Intel HD, up to 2 independend displays supported, max. resolution: 3840 x 2160 px Wireless LAN, Unex DNUR-S2 300 Mbit dual-band WLAN module LTE: Huawei 909u-5214G LTE (FDD) B1/B2/B3/B5/B7/B8/B203G DC-HSPA+/HSPA+/HSPA/UMTS B1/B2/B5/B82G EDGE/ GPRS/ GSM - 850/900/1800/1900MHz Power-In: DC wide-input 9..19V, 5.5 x 2.5 mm plug PSU: FSP060-DHAN3; external AC/DC adapterInput: 90 to 264 V ACOutput: 12 V / 60 W Power consumption: Idle 6 W, 100% load (Cel.) 11 W OS compatibility: IPFire, OPNSense, PFSense, Ubuntu Linux Scan this QR code to view the product All details, up-to-date prices and availability Powered by TCPDF (www.tcpdf.org). -

Kratka Povijest Unixa Od Unicsa Do Freebsda I Linuxa
Kratka povijest UNIXa Od UNICSa do FreeBSDa i Linuxa 1 Autor: Hrvoje Horvat Naslov: Kratka povijest UNIXa - Od UNICSa do FreeBSDa i Linuxa Licenca i prava korištenja: Svi imaju pravo koristiti, mijenjati, kopirati i štampati (printati) knjigu, prema pravilima GNU GPL licence. Mjesto i godina izdavanja: Osijek, 2017 ISBN: 978-953-59438-0-8 (PDF-online) URL publikacije (PDF): https://www.opensource-osijek.org/knjige/Kratka povijest UNIXa - Od UNICSa do FreeBSDa i Linuxa.pdf ISBN: 978-953- 59438-1- 5 (HTML-online) DokuWiki URL (HTML): https://www.opensource-osijek.org/dokuwiki/wiki:knjige:kratka-povijest- unixa Verzija publikacije : 1.0 Nakalada : Vlastita naklada Uz pravo svakoga na vlastito štampanje (printanje), prema pravilima GNU GPL licence. Ova knjiga je napisana unutar inicijative Open Source Osijek: https://www.opensource-osijek.org Inicijativa Open Source Osijek je član udruge Osijek Software City: http://softwarecity.hr/ UNIX je registrirano i zaštićeno ime od strane tvrtke X/Open (Open Group). FreeBSD i FreeBSD logo su registrirani i zaštićeni od strane FreeBSD Foundation. Imena i logo : Apple, Mac, Macintosh, iOS i Mac OS su registrirani i zaštićeni od strane tvrtke Apple Computer. Ime i logo IBM i AIX su registrirani i zaštićeni od strane tvrtke International Business Machines Corporation. IEEE, POSIX i 802 registrirani i zaštićeni od strane instituta Institute of Electrical and Electronics Engineers. Ime Linux je registrirano i zaštićeno od strane Linusa Torvaldsa u Sjedinjenim Američkim Državama. Ime i logo : Sun, Sun Microsystems, SunOS, Solaris i Java su registrirani i zaštićeni od strane tvrtke Sun Microsystems, sada u vlasništvu tvrtke Oracle. Ime i logo Oracle su u vlasništvu tvrtke Oracle. -

AMD EPYC™ Performance. Rack Mountable Appliance, the Full Package at an Affordable Price
OPNsense® Rack Security Appliance DEC3800 Series (c) 2021 Deciso B.V., All Rights Reserved. [rev.300821] (c) 2021 Deciso B.V., AMD EPYC™ Performance. Rack mountable appliance, the full package at an affordable price. Exceptional performance for businesses & enterprises. Guard Web Access 17Gbps Throughput Filtering (SSL) Proxy 1.5 Mega Packets per Second Captive Portal with Voucher support 512GB SSD ~2Gbps Inline Intrusion Prevention Offering Sufficient Space for Logging & Reporting Fast Filtering System wide two-factor Up to 50.000 Connections per authentication. Second Compatible with Google Authenticator. Hardware Assisted Encryption 2.5Gbps IPsec (AES256GCM16) Securing Networks™ DATASHEET Deciso Sales B.V. • +31 187 744 020 • [email protected] • www.deciso.com CERTIFIED HARDWARE FROM THE DEVELOPERS - MADE IN THE NETHERLANDS DEC3800 SERIES Bundled with a free year OPNsense® Business Edition √ Commercial firmware repository √ Free GeoIP database √ Official OPNsense Open Virtualization Image √ Free professional plugins (OPNcentral, Proxy Access) √ Free E-Book ( English & German ) Securing Networks™ Deciso Sales B.V. • +31 187 744 020 • [email protected] • www.deciso.com SOFTWARE VERSATILE - OPEN SOURCE - FULLY FEATURED OPNsense is Deciso’s fast growing open source firewall and security platform released under an Open Source Initiative approved license. Its rich feature set is combined with the benefits of open and verifiable sources. All features can be used from within the easy to use graphical interface, equipped with a build-in search feature for quick navigation. Protecting your network has never been this easy with features such as; the integrated intrusion prevention system and two-factor authentication for safely connecting mobile users. OPNsense® Secure Your Network With Ease™ Businesses Protect your business network and secure your connections. -

Threat Detection of IPS in High Load Situation
Threat detection of IPS in high load situation Konsta Karttunen Master’s thesis April 2018 School of Technology, Communications and Transport Master’s Degree Programme in Information technology Cyber Security Description Author(s) Type of publication Date Karttunen Konsta Master’s thesis 4.2018 Language of publication: English Number of pages Permission for web 73 publication: x Title of publication Threat detection of IPS in high load situations Degree programme Information Technology, Cyber Security Supervisor(s) Kotikoski Sampo Assigned by Konsta Karttunen Abstract Commercial network security solutions are typically measured by the throughput of the device in megabytes per second. Throughput is also quite often used to compare the different vendors and to size the security solution so that the solution is able to handle the network traffic passing through. One method of avoiding a network security solution is to overwhelm the solution with excessive network traffic so that it either crashes or starts to bypass the traffic from the proper inspection. In a situation like this, more information about the performance of the solution would be extremely crucial. The goal was to investigate the behavior of the security features, especially intrusion prevention systems, in high load situations. The target systems were loaded with high traffic volume using Ixia's BreakingPoint tool, and the Attack Pack feature of the tool was used to evaluate the security capabilities under the load. The difference between low and high load situations was also observed. The results of the research revealed that different security solutions performed quite differently under heavy load. Additionally, it was noted that the measurement of the capabilities of a security product is not as straightforward as it might sound and comparing the results between different solutions poses a significant challenge. -
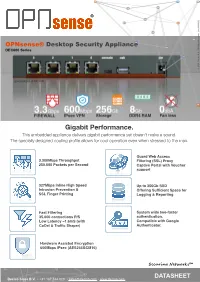
Gigabit Performance. This Embedded Appliance Delivers Gigabit Performance Yet Doesn't Make a Sound
OPNsense® Desktop Security Appliance DEC600 Series (c) 2021 Deciso B.V., All Rights Reserved. [rev.300821] (c) 2021 Deciso B.V., Gigabit Performance. This embedded appliance delivers gigabit performance yet doesn't make a sound. The specially designed cooling profile allows for cool operation even when stressed to the max. Guard Web Access 3.300Mbps Throughput Filtering (SSL) Proxy 250.000 Packets per Second Captive Portal with Voucher support 327Mbps Inline High Speed Up to 356Gb SSD Intrusion Prevention & Offering Sufficient Space for SSL Finger Printing Logging & Reporting Fast Filtering System wide two-factor 35.000 connections P/S authentication. Low Latency ~1.6mS (with Compatible with Google CoDel & Traffic Shaper) Authenticator. Hardware Assisted Encryption 600Mbps IPsec (AES256GCM16) Securing Networks™ DATASHEET Deciso Sales B.V. • +31 187 744 020 • [email protected] • www.deciso.com CERTIFIED HARDWARE FROM THE DEVELOPERS - MADE IN THE NETHERLANDS DEC600 SERIES Bundled with a free year OPNsense® Business Edition √ Commercial firmware repository √ Free GeoIP database √ Official OPNsense Open Virtualization Image √ Free professional plugins (OPNcentral, Proxy Access) √ Free E-Book ( English & German ) Securing Networks™ Deciso Sales B.V. • +31 187 744 020 • [email protected] • www.deciso.com SOFTWARE VERSATILE - OPEN SOURCE - FULLY FEATURED OPNsense is Deciso’s fast growing open source firewall and security platform released under an Open Source Initiative approved license. Its rich feature set is combined with the benefits of open and verifiable sources. All features can be used from within the easy to use graphical interface, equipped with a build-in search feature for quick navigation. Protecting your network has never been this easy with features such as; the integrated intrusion prevention system and two-factor authentication for safely connecting mobile users. -

The Open Source Firewall in Practice
OPNsense The open source fi rewall in practice Table of contents 1. How companies can benefit from OPNsense 3| 2. What makes OPNsense unique? 4| 2.1 The OPNsense Business Edition 3. A closer look at OPNsense 5| 3.1 Intrusion and malware detection 6| 3.2 Virtual Private Networking (VPN) 3.3 High availability 7| 3.4 Traffic analysis and traffic shaping 3.5 Further features in the core system 3.6 Plugins 8| 4. Hardware for OPNsense 8| 5. Using OPNsense 8| 5.1 Example customer A: 9| An SME specializing in the production of technical ropes 5.2 Example customer B: An SME consulting firm in the social sector 6. Plugins for OPNsense 9| 7. Transparent development model 10| 8. Plugins in an example scenario 10| 8.1 Centralized WLAN protection with the FreeRADIUS plugin 10| 8.2 Securing an Exchange Server with the Postfix plugin 14| 8.3 Monitoring with the Telegraf plugin 18| 8.4 NUT plugin for UPS integration 21| Summary 22| thomas-krenn.com | 3 OPNsense The open source fi rewall in practice Comprehensive IT security and fl exibly expandable plugins. IT managers regularly see the IT they manage intrusion detection & prevention, VPN, two- exposed to new threats. Having the latest fi rewall factor authentication and high availability. In this is no longer suffi cient. It is much more important e-book, we present OPNsense as an alternative to be able to react fl exibly to security risks. The to commercial fi rewall solutions. Our focus is on open source fi rewall OPNsense is a digital platform practical use cases in the SME context and on how that offers many additional features such as functionality can be expanded via plugins. -

Wifi Open Firmware
Wifi open firmware click here to download Instead of trying to create a single, static firmware, OpenWrt provides a fully Like any open source project, OpenWrt thrives on the efforts of its users and. Wonder what are the advantages of open source router firmware? Learn the basics on the What is Open Source Firmware page. Wireless network cards for computers require control software to make them function (firmware, .. iwm · Intel Wireless WiFi Link ac/ ac/ ac, Integrated (since ), No, BSD, Antti Kantee, Stefan Sperling, Based on iwn, and iwlwifi. a mentorship program that aims to bring pre-university students into Open Source . Google Code-In. If you are a GCI student read our GCI quick-start!. Open FirmWare for WiFi networks: a UniBS NTW group project To understand how it works and to have access to patches and firmware for supporting The firmware (the main piece) allow simple deployment of auto-configurable, yet It is open, so anyone can connect to it if physically possible networks is by installing our own firmware to the devices (usually WiFi routers). Atheros has been more friendly towards Linux customers in recent years with open-source WiFi/network Linux drivers. Atheros has even been. Installing a custom firmware on your Wi-Fi router is like God Mode for your home network. You can see everything going on, boost your Wi-Fi. Linux and open source rule the wireless hotspot world, and Eric wanting to give away or charge your visitors for the wireless Internet, you. PacketFence is a fully supported, trusted, Free and Open Source network access control (NAC) solution. -

A Hybrid Loss-Delay Gradient Congestion Control Algorithm for the Internet
A Hybrid Loss-Delay Gradient Congestion Control Algorithm for the Internet Rasool Al-Saadi School of Software and Electrical Engineering Swinburne University of Technology This thesis is submitted for the degree of Doctor of Philosophy Faculty of Science, Engineering and October 2019 Technology I dedicate this thesis to my loving parents, my beloved wife Dalia and my sons Ridha and Yousif. Declaration I declare that this thesis submitted for the degree of Doctor of Philosophy contains no ma- terial that has been accepted for the award to the candidate of any other degree or diploma, except where due reference made a in the text of the examinable outcome. To the best of the candidate’s knowledge contains no material previously published or written by another person except where due reference is made in the text of the examinable outcome. Where the work is based on joint research or publications, discloses the relative contributions of the respective creators or authors. Rasool Al-Saadi October 2019 Acknowledgements I would like to express my thanks and appreciation to all the people and institutions who helped, guided, advised and supported me during my PhD journey. I would like to thank my supervisors Prof. Grenville Armitage, Dr. Jason But and Assoc. Prof. Philip Branch for their insight, patience, friendship, encouragement, continuous support and valuable advice during my PhD candidature. I had the honour of being a student under their wise supervision. Without their support, this work would never have seen the light of day. I am greatly indebted to my family, especially my wife Dalia Al-Zubaidy, my parents, my brother and my sister for their patience, persevering support and advice. -

Open Source Security Appliance Analisi Di Tre Piattaforme E Applicazioni Realizzate
Public Open Source Security Appliance analisi di tre piattaforme e applicazioni realizzate Gianluca Peco INFN CCR Workshop 24 maggio 2021 1 Public Public Introduzione 3 Evoluzione del perimetro e Zero trust 2 Panorama 2 INDICE Funzionalità 4 Confronto funzionalità 2 Applicazioni realizzate 4 Demo 5 min 24 maggio 2021 Gianluca Peco - CCR Workshop 2 Public Public Introduzione • L’ evoluzione delle applicazioni e dei sistemi, insieme all’introduzione delle tecnologie di virtualizzazione, container, etc. spingono verso le tecnologie che portano alla distribuzione e delocalizzazione delle rirorse. • IoT, diffusione dei sistemi mobili e delle tecnologie wifi e xG frammentano il perimetro tradizionale luogo deputato al controllo di sicurezza • Nasce l’esigenza di portare nella periferia dell’impero attività tipicamente svolte nelle province interne o nella capitale 24 maggio 2021 Gianluca Peco - CCR Workshop 3 Public Public Evoluzione del Zero trust architecture perimetro Layered security 24 maggio 2021 Gianluca Peco - CCR Workshop 4 Public Public Evoluzione del perimetro Punto di vista di alcuni vendor 24 maggio 2021 Gianluca Peco - CCR Workshop 5 Public Public NGFW Opensource: perchè potrebbero essere utili? • Molte funzioni devono essere “delocalizzate” • quelle classiche tradizionalmente centralizzate: Routing, Firewall, Proxy, Nat • altre più specifiche: Load Balancer, NIDS, IPS, Logging, Monitor, Flow analysis • Tali funzioni sono confluite nei NGFW, basati su HW dedicato e dotati di intelligenza fino al livello 7 • La virtualizzazione -

Opnsense Brochure
(c) 2018 Deciso B.V., All Rights Reserved. [rev.1620517] (c) 2018 Deciso B.V., OPNsense® Open Source Security High-end security made easy™ OPNsense is a fully featured security platform that secures your network with high-end features such as inline intrusion prevention, virtual private networking, two factor authentication, captive portal and filtering web proxy. The optional high availability setup ensures stable network performance with automatic failover and synchronised states, minimising disruption. Keep your network secure and the good packets flowing. Guard Web Access Stateful Inspection Firewall Filtering (SSL) Proxy Captive Portal with Voucher support Inline Intrusion Prevention & On system Logging & SSL Finger Printing Reporting including Netflow analyser (Insight) Fast Filtering System wide two-factor The Traffic Shaper eliminates authentication. buffer bloat and lower latency. Compatible with Google Authenticator. Virtual Private Networking Hardware Assisted Encryption Se#$%&n( Ne+w.k0 Deciso Sales B.V. • +31 187 744 020 • [email protected] • www.deciso.com INTRODUCING OPNsense® VERSATILE - OPEN SOURCE - FULLY FEATURED Insight Netflow Reporting OPNsense® is Deciso’s fast growing open source firewall and security platform released under an Open Source Initiative approved license. It’s rich feature set is combined with the benefits of open and verifiable sources. All features can be used from within the easy to use graphical interface, equipped with a build-in search feature for quick navigation. Protecting your network has never been this easy, utilise the integrated intrusion prevention capable of blacklisting based on SSL fingerprints and the two-factor authentication for safely connecting mobile users. Keep full insight on the traffic flowing trough your firewall at all times, with its advanced Netflow capture, aggregate & reporting tool ‘Insight’. -
Openbsd Routing with PF
OpenBSD Routing With PF OpenBSD Routing With PF 1 / 2 Hi misc@, I was wondering about the behavior of OpenBSD in this case (not a production case at this time). 2 WAN interfaces (Ethernet / IPv4 DHCP) , linked to .... An OpenBSD system doing NAT will have at least two network adapters, one to the ... Since NAT is almost always used on routers and network gateways, it will ... Packet Filter (from here on referred to as PF) is OpenBSD's system for filtering TCP/IP ... q destination address in route-to, reply-to, and dup-to filter rule options.. I run OpenBSD routers in production. When getting the lay of the land to set these up I came across OP's link as well as ... PF is a BSD licensed stateful packet filter, a central piece of software for firewalling. It is comparable to netfilter (iptables), ipfw, and ipfilter. PF was developed for OpenBSD, but has been ported to many other ... free open source FreeBSD based firewall/router; OPNSense free open source FreeBSD based firewall/router ... OpenBSD Routing With PF >>> http://picfs.com/1fcy6g Since FreeBSD 5.3, a ported ve.. The OpenBSD PF Guide: Macros shows a macro named ext_if. Using that ... echo lnklclrt = \ " ff02::2 \ " \ #link-local "All Routers Addresses" RFC 4291 S 2.7.1 p.. Setting up a home gateway with OpenBSD + other goodies ... a spare box with two or more NICs, you can turn it into a powerful OpenBSD router. ... /etc/pf.conf.. Mark's OpenBSD Router Guide. Turning a PC Engines ALIX.2D3 into an OpenBSD 4.8 home router.