Technical Proposal for Digital Imaging Center
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Title Title: Subtitle March 2007
sub title The Title Title: Subtitle March 2007 Copyright c 2006-2007 BSD Certification Group, Inc. Permission to use, copy, modify, and distribute this documentation for any purpose with or without fee is hereby granted, provided that the above copyright notice and this permission notice appear in all copies. THE DOCUMENTATION IS PROVIDED "AS IS" AND THE AUTHOR DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS DOCUMENTATION INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR ANY SPECIAL, DIRECT, INDIRECT, OR CON- SEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEG- LIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS DOCUMENTATION. NetBSD and pkgsrc are registered trademarks of the NetBSD Foundation, Inc. FreeBSD is a registered trademark of the FreeBSD Foundation. Contents Introduction vii 1 Installing and Upgrading the OS and Software 1 1.1 Recognize the installation program used by each operating system . 2 1.2 Recognize which commands are available for upgrading the operating system 6 1.3 Understand the difference between a pre-compiled binary and compiling from source . 8 1.4 Understand when it is preferable to install a pre-compiled binary and how to doso ...................................... 9 1.5 Recognize the available methods for compiling a customized binary . 10 1.6 Determine what software is installed on a system . 11 1.7 Determine which software requires upgrading . 12 1.8 Upgrade installed software . 12 1.9 Determine which software have outstanding security advisories . -

Active-Active Firewall Cluster Support in Openbsd
Active-Active Firewall Cluster Support in OpenBSD David Gwynne School of Information Technology and Electrical Engineering, University of Queensland Submitted for the degree of Bachelor of Information Technology COMP4000 Special Topics Industry Project February 2009 to leese, who puts up with this stuff ii Acknowledgements I would like to thank Peter Sutton for allowing me the opportunity to do this work as part of my studies at the University of Queensland. A huge thanks must go to Ryan McBride for answering all my questions about pf and pfsync in general, and for the many hours working with me on this problem and helping me test and debug the code. Thanks also go to Theo de Raadt, Claudio Jeker, Henning Brauer, and everyone else at the OpenBSD network hackathons who helped me through this. iii Abstract The OpenBSD UNIX-like operating system has developed several technologies that make it useful in the role of an IP router and packet filtering firewall. These technologies include support for several standard routing protocols such as BGP and OSPF, a high performance stateful IP packet filter called pf, shared IP address and fail-over support with CARP (Common Address Redundancy Protocol), and a protocol called pfsync for synchronisation of the firewalls state with firewalls over a network link. These technologies together allow the deployment of two or more computers to provide redundant and highly available routers on a network. However, when performing stateful filtering of the TCP protocol with pf, the routers must be configured in an active-passive configuration due to the current semantics of pfsync. -

Opnsense Your Next Open Source Firewall
OPNsense Your next open source firewall www.rhinolabsinc.com About OPNsense Highlights Businesses ProtEct your businEss nEtwork and sEcurE your connEctions. From thE stateful inspection firewall to thE inline intrusion detection & prevention systEm EvErything is includEd for frEE.UsE thE traffic shaper to EnhancE nEtwork pErformancE and prioritisE Businesses you voicE ovEr ip abovE othEr traffic. Backup your configuration to thE cloud automatically, no nEEd for manual backups anymorE! School Networks Limit and share available bandwidth evenly amongst studEnts and utilisE thE category based web filtering to filtEr unwantEd traffic such as adult contEnt and malicious wEbsitEs. Its Easy to sEtup as no additional plugins nor packagEs arE School Networks rEquirEd. TEach about sEcurity or usE our dEvElopmEnt documEntation to show how an ModEl ViEwEr ControllEr works. You and your studEnts arE invitEd to join thE Effort and OPNsEnsE community! About OPNsense Highlights Hotels & Campings Hotels and campIngs usually utIlIse a captIve portal to allow guests (paId) access to Internet for a lImIted duratIon. Guests need to logIn usIng a voucher that they can eIther buy or Hotels and Camping obtaIn for free at the receptIon. OPNsense has a buIlt-In captive portal wIth voucher support and can easIly create them on the fly. On The Road Even on the road OPNsense Is a great asset to your busIness as It offers OpenVPN and IPSec VPN solutIon wIth road warrior support. The easy client exporter make On The Road configurIng your OpenVPN SSL clIent setup a breeze. Remote Offices & SOHO UtIlIse the Integrated sIte to sIte VPN (IPsec or SSL VPN) to create a secure network connectIon to and from your remote offices. -

Ipfire Duobox Business, 4 GB RAM, 64 GB SSD
Item no.: 323825 IPFire DuoBox Business, 4 GB RAM, 64 GB SSD from 462,37 EUR Item no.: 323825 shipping weight: 1.20 kg Manufacturer: IPFire Product Description IPFire DuoBox Business, 4 GB RAM, 64 GB SSDThis Firewall version was specifically designed for small offices und home offices, in which a stable and fast Internet connection is essential. The Duo Box Business provides you with fast Internet, while being low-cost and energy-efficient. It keeps your business connected and, most importantly, it keeps your network safe. Main Features: ● 2x Gigabit Ethernet for LAN and WAN ● 1x 300 Mbit dual-band Wi-Fi with access point mode ● optionally upgradeable with LTE Scope of Delivery: ● System ● Power Cable ● PSU ● 2x WLAN antennas Specifications Application: Firewall application for SOHO, branch offices and IoT Type: aluminum profile construction without venting holes, black anodized Dimensions (W x D x H): 134 x 108 x 55 mm Weight: 1.2 kg Cooling: directly attached to chassis Operating conditions: 0 - 50 °C / 80 % rel. humidity CPU: Intel Pentium 3558U, 2x 1.7 GHz RAM: 4 GB DDR3L Mainboard: customized eNUC platform I/O front (standard): 1x RS232, 1x USB 3.0, 1x Audio I/O back: 2x HDMI, 2x USB 3.0, 2x RJ45 (Realtek GLAN) I/O internal: internal I/O might be occupied - depending on your configuration, 1x mSATA/mPCIe full size, 2x USB 2.0 Storage: 1x 2.5" 64 GB SSD (industrial, MLC, 0 - +70 °C ) Graphics: Intel HD, up to 2 independend displays supported, max. resolution: 3840 x 2160 px Wireless LAN, Unex DNUR-S2 300 Mbit dual-band WLAN module LTE: Huawei 909u-5214G LTE (FDD) B1/B2/B3/B5/B7/B8/B203G DC-HSPA+/HSPA+/HSPA/UMTS B1/B2/B5/B82G EDGE/ GPRS/ GSM - 850/900/1800/1900MHz Power-In: DC wide-input 9..19V, 5.5 x 2.5 mm plug PSU: FSP060-DHAN3; external AC/DC adapterInput: 90 to 264 V ACOutput: 12 V / 60 W Power consumption: Idle 6 W, 100% load (Cel.) 11 W OS compatibility: IPFire, OPNSense, PFSense, Ubuntu Linux Scan this QR code to view the product All details, up-to-date prices and availability Powered by TCPDF (www.tcpdf.org). -

David Gwynne <[email protected]>
firewalling with OpenBSD's pf and pfsync David Gwynne <[email protected]> Thursday, 17 January 13 introduction ‣ who am i? ‣ what is openbsd? ‣ what are pf and pfsync? ‣ how do i use them? ‣ ask questions whenever you want Thursday, 17 January 13 who am i? ‣ infrastructure architect in EAIT at UQ ‣ i do stuff, including run the firewalls ‣ a core developer in openbsd ‣ i generally play with storage ‣ but i play with the network stack sometimes Thursday, 17 January 13 what is openbsd? ‣ open source general purpose unix-like operating system ‣ descended from the original UNIX by way of berkeley and netbsd ‣ aims for “portability, standardization, correctness, proactive security and integrated cryptography.” ‣ supports various architectures/platforms Thursday, 17 January 13 what is openbsd? ‣ one source tree for everything ‣ kernel, userland, doco ‣ bsd/isc/mit style licenses on all code (with some historical exceptions) ‣ 6 month dev cycle resulting in a release ‣ 3rd party software via a ports tree ‣ emergent focus on network services Thursday, 17 January 13 what is openbsd? ‣ it is very aggressive ‣ changes up and down the stack (compiler to kernel) to make a harsher, stricter, and less predictable runtime environment ‣ minimal or no backward compatibility as things move forward ‣ whole tree is checked for new bugs ‣ randomise as much as possible all over Thursday, 17 January 13 what is openbsd? ‣ it is extremely conservative ‣ tree must compile and work at all times ‣ big changes go in at the start of the cycle ‣ we’re not afraid to back stuff out ‣ peer review is necessary ‣ we do back away from some tweaks for the sake of usability Thursday, 17 January 13 what is pf? ‣ short for packet filter ‣ the successor to IP Filter (ipf) ‣ ipf was removed due to license issues ‣ the exec summary is that it is a stateful filter for IP (v4 and v6) traffic ‣ does a little bit more than that though.. -

Ask Bjørn Hansen Develooper LLC
If this text is too small to read, move closer! http://groups.google.com/group/scalable Real World Web: Performance & Scalability Ask Bjørn Hansen Develooper LLC http://develooper.com/talks/ April 14, 2008 – r17 Hello. • I’m Ask Bjørn Hansen perl.org, ~10 years of mod_perl app development, mysql and scalability consulting YellowBot • I hate tutorials! • Let’s do 3 hours of 5 minute° lightning talks! ° Actual number of minutes may vary Construction Ahead! • Conflicting advice ahead • Not everything here is applicable to everything • Ways to “think scalable” rather than be-all-end-all solutions • Don’t prematurely optimize! (just don’t be too stupid with the “we’ll fix it later” stuff) Questions ... • How many ... • ... are using PHP? Python? Python? Java? Ruby? C? • 3.23? 4.0? 4.1? 5.0? 5.1? 6.x? • MyISAM? InnoDB? Other? • Are primarily “programmers” vs “DBAs” • Replication? Cluster? Partitioning? • Enterprise? Community? • PostgreSQL? Oracle? SQL Server? Other? Seen this talk before? Slide count 200 No, you haven’t. • 150 • :-) 100 • ~266 people * 3 hours = half a work year! 50 0 2001 2004 2006 2007 2008 Question Policy! http://groups.google.com/group/scalable • Do we have time for Slides per minute questions? 1.75 • Yes! (probably) • Quick questions anytime • Long questions after 1.00 • or on the list! • (answer to anything is likely “it depends” or “let’s talk about it 0.25 after / send me an email”) 2001 2002 2004 2005 2006 2007 2008 • The first, last and only lesson: • Think Horizontal! • Everything in your architecture, not just the front end web servers • Micro optimizations and other implementation details –– Bzzzzt! Boring! (blah blah blah, we’ll get to the cool stuff in a moment!) Benchmarking techniques • Scalability isn't the same as processing time • Not “how fast” but “how many” • Test “force”, not speed. -

Kratka Povijest Unixa Od Unicsa Do Freebsda I Linuxa
Kratka povijest UNIXa Od UNICSa do FreeBSDa i Linuxa 1 Autor: Hrvoje Horvat Naslov: Kratka povijest UNIXa - Od UNICSa do FreeBSDa i Linuxa Licenca i prava korištenja: Svi imaju pravo koristiti, mijenjati, kopirati i štampati (printati) knjigu, prema pravilima GNU GPL licence. Mjesto i godina izdavanja: Osijek, 2017 ISBN: 978-953-59438-0-8 (PDF-online) URL publikacije (PDF): https://www.opensource-osijek.org/knjige/Kratka povijest UNIXa - Od UNICSa do FreeBSDa i Linuxa.pdf ISBN: 978-953- 59438-1- 5 (HTML-online) DokuWiki URL (HTML): https://www.opensource-osijek.org/dokuwiki/wiki:knjige:kratka-povijest- unixa Verzija publikacije : 1.0 Nakalada : Vlastita naklada Uz pravo svakoga na vlastito štampanje (printanje), prema pravilima GNU GPL licence. Ova knjiga je napisana unutar inicijative Open Source Osijek: https://www.opensource-osijek.org Inicijativa Open Source Osijek je član udruge Osijek Software City: http://softwarecity.hr/ UNIX je registrirano i zaštićeno ime od strane tvrtke X/Open (Open Group). FreeBSD i FreeBSD logo su registrirani i zaštićeni od strane FreeBSD Foundation. Imena i logo : Apple, Mac, Macintosh, iOS i Mac OS su registrirani i zaštićeni od strane tvrtke Apple Computer. Ime i logo IBM i AIX su registrirani i zaštićeni od strane tvrtke International Business Machines Corporation. IEEE, POSIX i 802 registrirani i zaštićeni od strane instituta Institute of Electrical and Electronics Engineers. Ime Linux je registrirano i zaštićeno od strane Linusa Torvaldsa u Sjedinjenim Američkim Državama. Ime i logo : Sun, Sun Microsystems, SunOS, Solaris i Java su registrirani i zaštićeni od strane tvrtke Sun Microsystems, sada u vlasništvu tvrtke Oracle. Ime i logo Oracle su u vlasništvu tvrtke Oracle. -

Documento Completo
UNIVERSIDAD AUTÓNOMA DE CIUDAD JUÁREZ Instituto de Ingeniería y Tecnología Departamento de Ingeniería Eléctrica y Computación Caracterización de firewall de alta disponibilidad con filtro de contenido en un ambiente virtualizado. Reporte Técnico de Investigación presentado por: Alejandra Juana Torres Pérez 98709 Lucero Martínez Castrillo 98750 Requisito para la obtención del título de INGENIERO EN SISTEMAS COMPUTACIONALES Profesor Responsable: Mtro. Eduardo Castillo Luna Mayo de 2015 ii iii iv Índice de contenidos Autorización de Impresión…………………………………………………………....¡Error! Marcador no definido. Declaración de Originalidad………………………………………………………….¡Error! Marcador no definido. Lista de Figuras ... ……………………………………………………………………….viii Lista de Tablas .... ………………………………………………………………………..iix Introducción ......…………………………………………………………………………...1 Capítulo 1. Planteamiento del problema ......………………………………………………2 1.1 Antecedentes ......……………………………………………………………………2 1.2 Definición del problema......………………………………………………………...4 1.3 Objetivos de la investigación .....…………………………………………………....4 1.4 Preguntas de investigación.....……………………………………………………....5 1.5 Justificación de la investigación ....………………………………………………....5 1.6 Limitaciones y delimitaciones de la investigación ....……………………………...6 Capítulo 2. Marco Teórico .....……………………………………………………………..7 2.1 Seguridad informática ....……………………………………………………………7 2.1.1 Tipos de Seguridad……………………………………………………………..8 2.1.2 Seguridad en redes de comunicación………………………………………......9 2.2 Firewall ......………………………………………………………………………..10 2.2.1 -

AMD EPYC™ Performance. Rack Mountable Appliance, the Full Package at an Affordable Price
OPNsense® Rack Security Appliance DEC3800 Series (c) 2021 Deciso B.V., All Rights Reserved. [rev.300821] (c) 2021 Deciso B.V., AMD EPYC™ Performance. Rack mountable appliance, the full package at an affordable price. Exceptional performance for businesses & enterprises. Guard Web Access 17Gbps Throughput Filtering (SSL) Proxy 1.5 Mega Packets per Second Captive Portal with Voucher support 512GB SSD ~2Gbps Inline Intrusion Prevention Offering Sufficient Space for Logging & Reporting Fast Filtering System wide two-factor Up to 50.000 Connections per authentication. Second Compatible with Google Authenticator. Hardware Assisted Encryption 2.5Gbps IPsec (AES256GCM16) Securing Networks™ DATASHEET Deciso Sales B.V. • +31 187 744 020 • [email protected] • www.deciso.com CERTIFIED HARDWARE FROM THE DEVELOPERS - MADE IN THE NETHERLANDS DEC3800 SERIES Bundled with a free year OPNsense® Business Edition √ Commercial firmware repository √ Free GeoIP database √ Official OPNsense Open Virtualization Image √ Free professional plugins (OPNcentral, Proxy Access) √ Free E-Book ( English & German ) Securing Networks™ Deciso Sales B.V. • +31 187 744 020 • [email protected] • www.deciso.com SOFTWARE VERSATILE - OPEN SOURCE - FULLY FEATURED OPNsense is Deciso’s fast growing open source firewall and security platform released under an Open Source Initiative approved license. Its rich feature set is combined with the benefits of open and verifiable sources. All features can be used from within the easy to use graphical interface, equipped with a build-in search feature for quick navigation. Protecting your network has never been this easy with features such as; the integrated intrusion prevention system and two-factor authentication for safely connecting mobile users. OPNsense® Secure Your Network With Ease™ Businesses Protect your business network and secure your connections. -

The Book of PF Covers the Most • Stay in Control of Your Traffic with Monitoring and Up-To-Date Developments in PF, Including New Content PETER N.M
EDITION3RD BUILD A Covers OpenBSD 5.6, MORE SECURE FreeBSD 10.x, and NETWORK EDITION NETWORK 3RD NetBSD 6.x WITH PF THETHE BOOKBOOK THE BOOK OF PF OF THE BOOK THE BOOK OF PF OF THE BOOK OFOF PFPF OpenBSD’s stateful packet filter, PF, is the heart of • Build adaptive firewalls to proactively defend against A GUIDE TO THE the OpenBSD firewall. With more and more services attackers and spammers NO-NONSENSE placing high demands on bandwidth and an increas- OPENBSD FIREWALL • Harness OpenBSD’s latest traffic-shaping system ingly hostile Internet environment, no sysadmin can to keep your network responsive, and convert your afford to be without PF expertise. existing ALTQ configurations to the new system The third edition of The Book of PF covers the most • Stay in control of your traffic with monitoring and up-to-date developments in PF, including new content PETER N.M. HANSTEEN visualization tools (including NetFlow) on IPv6, dual stack configurations, the “queues and priorities” traffic-shaping system, NAT and redirection, The Book of PF is the essential guide to building a secure wireless networking, spam fighting, failover provision- network with PF. With a little effort and this book, you’ll ing, logging, and more. be well prepared to unlock PF’s full potential. You’ll also learn how to: ABOUT THE AUTHOR • Create rule sets for all kinds of network traffic, whether Peter N.M. Hansteen is a consultant, writer, and crossing a simple LAN, hiding behind NAT, traversing sysadmin based in Bergen, Norway. A longtime DMZs, or spanning bridges or wider networks Freenix advocate, Hansteen is a frequent lecturer on OpenBSD and FreeBSD topics, an occasional • Set up wireless networks with access points, and contributor to BSD Magazine, and the author of an lock them down using authpf and special access often-slashdotted blog (http://bsdly.blogspot.com/ ). -

Threat Detection of IPS in High Load Situation
Threat detection of IPS in high load situation Konsta Karttunen Master’s thesis April 2018 School of Technology, Communications and Transport Master’s Degree Programme in Information technology Cyber Security Description Author(s) Type of publication Date Karttunen Konsta Master’s thesis 4.2018 Language of publication: English Number of pages Permission for web 73 publication: x Title of publication Threat detection of IPS in high load situations Degree programme Information Technology, Cyber Security Supervisor(s) Kotikoski Sampo Assigned by Konsta Karttunen Abstract Commercial network security solutions are typically measured by the throughput of the device in megabytes per second. Throughput is also quite often used to compare the different vendors and to size the security solution so that the solution is able to handle the network traffic passing through. One method of avoiding a network security solution is to overwhelm the solution with excessive network traffic so that it either crashes or starts to bypass the traffic from the proper inspection. In a situation like this, more information about the performance of the solution would be extremely crucial. The goal was to investigate the behavior of the security features, especially intrusion prevention systems, in high load situations. The target systems were loaded with high traffic volume using Ixia's BreakingPoint tool, and the Attack Pack feature of the tool was used to evaluate the security capabilities under the load. The difference between low and high load situations was also observed. The results of the research revealed that different security solutions performed quite differently under heavy load. Additionally, it was noted that the measurement of the capabilities of a security product is not as straightforward as it might sound and comparing the results between different solutions poses a significant challenge. -
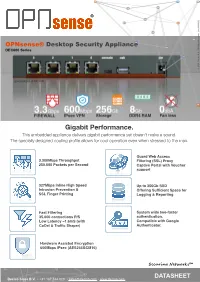
Gigabit Performance. This Embedded Appliance Delivers Gigabit Performance Yet Doesn't Make a Sound
OPNsense® Desktop Security Appliance DEC600 Series (c) 2021 Deciso B.V., All Rights Reserved. [rev.300821] (c) 2021 Deciso B.V., Gigabit Performance. This embedded appliance delivers gigabit performance yet doesn't make a sound. The specially designed cooling profile allows for cool operation even when stressed to the max. Guard Web Access 3.300Mbps Throughput Filtering (SSL) Proxy 250.000 Packets per Second Captive Portal with Voucher support 327Mbps Inline High Speed Up to 356Gb SSD Intrusion Prevention & Offering Sufficient Space for SSL Finger Printing Logging & Reporting Fast Filtering System wide two-factor 35.000 connections P/S authentication. Low Latency ~1.6mS (with Compatible with Google CoDel & Traffic Shaper) Authenticator. Hardware Assisted Encryption 600Mbps IPsec (AES256GCM16) Securing Networks™ DATASHEET Deciso Sales B.V. • +31 187 744 020 • [email protected] • www.deciso.com CERTIFIED HARDWARE FROM THE DEVELOPERS - MADE IN THE NETHERLANDS DEC600 SERIES Bundled with a free year OPNsense® Business Edition √ Commercial firmware repository √ Free GeoIP database √ Official OPNsense Open Virtualization Image √ Free professional plugins (OPNcentral, Proxy Access) √ Free E-Book ( English & German ) Securing Networks™ Deciso Sales B.V. • +31 187 744 020 • [email protected] • www.deciso.com SOFTWARE VERSATILE - OPEN SOURCE - FULLY FEATURED OPNsense is Deciso’s fast growing open source firewall and security platform released under an Open Source Initiative approved license. Its rich feature set is combined with the benefits of open and verifiable sources. All features can be used from within the easy to use graphical interface, equipped with a build-in search feature for quick navigation. Protecting your network has never been this easy with features such as; the integrated intrusion prevention system and two-factor authentication for safely connecting mobile users.