Coding Conventions 1 Contents
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Glib/GTK+ Development Platform
The GLib/GTK+ Development Platform A Getting Started Guide Version 0.8 Sébastien Wilmet March 29, 2019 Contents 1 Introduction 3 1.1 License . 3 1.2 Financial Support . 3 1.3 Todo List for this Book and a Quick 2019 Update . 4 1.4 What is GLib and GTK+? . 4 1.5 The GNOME Desktop . 5 1.6 Prerequisites . 6 1.7 Why and When Using the C Language? . 7 1.7.1 Separate the Backend from the Frontend . 7 1.7.2 Other Aspects to Keep in Mind . 8 1.8 Learning Path . 9 1.9 The Development Environment . 10 1.10 Acknowledgments . 10 I GLib, the Core Library 11 2 GLib, the Core Library 12 2.1 Basics . 13 2.1.1 Type Definitions . 13 2.1.2 Frequently Used Macros . 13 2.1.3 Debugging Macros . 14 2.1.4 Memory . 16 2.1.5 String Handling . 18 2.2 Data Structures . 20 2.2.1 Lists . 20 2.2.2 Trees . 24 2.2.3 Hash Tables . 29 2.3 The Main Event Loop . 31 2.4 Other Features . 33 II Object-Oriented Programming in C 35 3 Semi-Object-Oriented Programming in C 37 3.1 Header Example . 37 3.1.1 Project Namespace . 37 3.1.2 Class Namespace . 39 3.1.3 Lowercase, Uppercase or CamelCase? . 39 3.1.4 Include Guard . 39 3.1.5 C++ Support . 39 1 3.1.6 #include . 39 3.1.7 Type Definition . 40 3.1.8 Object Constructor . 40 3.1.9 Object Destructor . -

Clutter Version 1.10.0, Updated 9 May 2012
Guile-GNOME: Clutter version 1.10.0, updated 9 May 2012 Matthew Allum and OpenedHand LTD Intel Corporation This manual is for (gnome clutter) (version 1.10.0, updated 9 May 2012) Copyright 2006,2007,2008 OpenedHand LTD Copyright 2009,2010,2011,2012 Intel Corporation Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.1 or any later version published by the Free Software Foundation with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. You may obtain a copy of the GNU Free Documentation License from the Free Software Foundation by visiting their Web site or by writing to: The Free Software Foundation, Inc., 59 Temple Place - Suite 330, Boston, MA 02111-1307, USA i Short Contents 1 Overview :::::::::::::::::::::::::::::::::::::::::::: 1 2 ClutterAction :::::::::::::::::::::::::::::::::::::::: 2 3 ClutterActorMeta ::::::::::::::::::::::::::::::::::::: 3 4 ClutterActor ::::::::::::::::::::::::::::::::::::::::: 5 5 ClutterAlignConstraint:::::::::::::::::::::::::::::::: 63 6 ClutterAlpha :::::::::::::::::::::::::::::::::::::::: 65 7 ClutterAnimatable ::::::::::::::::::::::::::::::::::: 68 8 Implicit Animations :::::::::::::::::::::::::::::::::: 69 9 ClutterAnimator ::::::::::::::::::::::::::::::::::::: 76 10 ClutterBackend :::::::::::::::::::::::::::::::::::::: 82 11 ClutterBinLayout :::::::::::::::::::::::::::::::::::: 84 12 ClutterBindConstraint :::::::::::::::::::::::::::::::: 87 13 Key Bindings:::::::::::::::::::::::::::::::::::::::: 90 -

Pygtk GUI Programming Pygtk GUI Programming Table of Contents Pygtk GUI Programming
PyGTK GUI programming PyGTK GUI programming Table of Contents PyGTK GUI programming...............................................................................................................................1 Chapter 1. Introduzione....................................................................................................................................2 1.1. Primo approccio...............................................................................................................................2 1.2. Il toolkit PyGTK..............................................................................................................................2 1.3. PyGTK e Glade................................................................................................................................2 1.4. IDE o editor......................................................................................................................................4 1.5. Installazione.....................................................................................................................................6 1.5.1. Installazione su piattaforma GNU/Linux...............................................................................6 1.5.2. Installazione su piattaforma Windows...................................................................................6 1.6. Supporto e help................................................................................................................................6 Chapter 2. I Widget, le classi ed un -

Multiplatformní GUI Toolkity GTK+ a Qt
Multiplatformní GUI toolkity GTK+ a Qt Jan Outrata KATEDRA INFORMATIKY UNIVERZITA PALACKÉHO V OLOMOUCI GUI toolkit (widget toolkit) (1) = programová knihovna (nebo kolekce knihoven) implementující prvky GUI = widgety (tlačítka, seznamy, menu, posuvník, bary, dialog, okno atd.) a umožňující tvorbu GUI (grafického uživatelského rozhraní) aplikace vlastní jednotný nebo nativní (pro platformu/systém) vzhled widgetů, možnost stylování nízkoúrovňové (Xt a Xlib v X Windows System a libwayland ve Waylandu na unixových systémech, GDI Windows API, Quartz a Carbon v Apple Mac OS) a vysokoúrovňové (MFC, WTL, WPF a Windows Forms v MS Windows, Cocoa v Apple Mac OS X, Motif/Lesstif, Xaw a XForms na unixových systémech) multiplatformní = pro více platforem (MS Windows, GNU/Linux, Apple Mac OS X, mobilní) nebo platformově nezávislé (Java) – aplikace může být také (většinou) událostmi řízené programování (event-driven programming) – toolkit v hlavní smyčce zachytává události (uživatelské od myši nebo klávesnice, od časovače, systému, aplikace samotné atd.) a umožňuje implementaci vlastních obsluh (even handler, callback function), objektově orientované programování (objekty = widgety aj.) – nevyžaduje OO programovací jazyk! Jan Outrata (Univerzita Palackého v Olomouci) Multiplatformní GUI toolkity duben 2015 1 / 10 GUI toolkit (widget toolkit) (2) language binding = API (aplikační programové rozhraní) toolkitu v jiném prog. jazyce než původní API a toolkit samotný GUI designer/builder = WYSIWYG nástroj pro tvorbu GUI s využitím toolkitu, hierarchicky skládáním prvků, z uloženého XML pak generuje kód nebo GUI vytvoří za běhu aplikace nekomerční (GNU (L)GPL, MIT, open source) i komerční licence např. GTK+ (C), Qt (C++), wxWidgets (C++), FLTK (C++), CEGUI (C++), Swing/JFC (Java), SWT (Java), JavaFX (Java), Tcl/Tk (Tcl), XUL (XML) aj. -

Building a 3D Graphic User Interface in Linux
Freescale Semiconductor Document Number: AN4045 Application Note Rev. 0, 01/2010 Building a 3D Graphic User Interface in Linux Building Appealing, Eye-Catching, High-End 3D UIs with i.MX31 by Multimedia Application Division Freescale Semiconductor, Inc. Austin, TX To compete in the market, apart from aesthetics, mobile Contents 1. X Window System . 2 devices are expected to provide simplicity, functionality, and 1.1. UI Issues . 2 elegance. Customers prefer attractive mobile devices and 2. Overview of GUI Options for Linux . 3 expect new models to be even more attractive. For embedded 2.1. Graphics Toolkit . 3 devices, a graphic user interface is essential as it enhances 2.2. Open Graphics Library® . 4 3. Clutter Toolkit - Solution for GUIs . 5 the ease of use. Customers expect the following qualities 3.1. Features . 5 when they use a Graphical User Interface (GUI): 3.2. Clutter Overview . 6 3.3. Creating the Scenegraph . 7 • Quick and responsive feedback for user actions that 3.4. Behaviors . 8 clarifies what the device is doing. 3.5. Animation by Frames . 9 • Natural animations. 3.6. Event Handling . 10 4. Conclusion . 10 • Provide cues, whenever appropriate, instead of 5. Revision History . 11 lengthy textual descriptions. • Quick in resolving distractions when the system is loading or processing. • Elegant and beautiful UI design. This application note provides an overview and a guide for creating a complex 3D User Interface (UI) in Linux® for the embedded devices. © Freescale Semiconductor, Inc., 2010. All rights reserved. X Window System 1 X Window System The X Window system (commonly X11 or X) is a computer software system and network protocol that implements X display protocol and provides windowing on bitmap displays. -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -
GTK+ Properties
APPENDIX A ■ ■ ■ GTK+ Properties GObject provides a property system, which allows you to customize how widgets interact with the user and how they are drawn on the screen. In the following sections, you will be provided with a complete reference to widget and child properties available in GTK+ 2.10. GTK+ Properties Every class derived from GObject can create any number of properties. In GTK+, these properties store information about the current state of the widget. For example, GtkButton has a property called relief that defines the type of relief border used by the button in its normal state. In the following code, g_object_get() was used to retrieve the current value stored by the button’s relief property. This function accepts a NULL-terminated list of properties and vari- ables to store the returned value. You can also use g_object_set() to set each object property as well. g_object_get (button, "relief", &value, NULL); There are a great number of properties available to widgets; Tables A-1 to A-90 provide a full properties list for each widget and object in GTK+ 2.10. Remember that object properties are inherited from parent widgets, so you should investigate a widget’s hierarchy for a full list of properties. For more information on each object, you should reference the API documentation. Table A-1. GtkAboutDialog Properties Property Type Description artists GStrv A list of individuals who helped create the artwork used by the application. This often includes information such as an e-mail address or URL for each artist, which will be displayed as a link. -

Prospector 1955-2014 Remembrance on Rediscovery October 8, 2014 Volume 108 Edition 1 Carroll College Helena, Montana Page 7
Dedicated to the life The and work of Mike Franklin Prospector 1955-2014 Remembrance on Rediscovery October 8, 2014 Volume 108 Edition 1 Carroll College Helena, Montana page 7 Student Hunthausen Activity Center groundbreaking Columnist JOSH MCCORMICK Hello fellow peers, my name is Josh McCormick and I am a junior here at Carroll College. I am currently majoring in creative alternatives to homework and vibe exploration. I get asked frequently, “what do you plan on doing with that?” I typically reply, “what can’t I do with that?” Though I also study communications and philosophy, my inner ¿re is fueled by forming relationships with others, interacting with nature, sharing laughs, listening to music (preferably with juicy bass), and deepening my understanding of the semi-crazy yet loving creature I call me. Over the course of this year I am excited to share some of my thoughts and inner world with you via my column “Rediscovery.” There are many elements of one’s relationships, the world around, inner being, and daily activities that are Digital rendition of north perspective of future activity center, photo courtesy of Patty White. taken for granted or go unnoticed. I hope to bring to light some of these beautiful Nate Kavanagh commitment of the board of trustees and that responds to the needs of our time.” complexities of everyday life and make donors to the project and “how much they Matz stated it is ¿tting that the building the ordinary a wonder to rediscover. Lead Writer believe in the school and its students.” be named after Hunthausen citing his Enjoy! Evans opened up the ceremony with “pastoral care in and out of the classroom Students, faculty, staff, board members, The other day as I awoke from a excitement. -

Geanypy Documentation Release 1.0
GeanyPy Documentation Release 1.0 Matthew Brush <[email protected]> February 17, 2017 Contents 1 Introduction 3 2 Installation 5 2.1 Getting the Source............................................5 2.2 Dependencies and where to get them..................................5 2.3 And finally ... installing GeanyPy....................................7 3 Getting Started 9 3.1 What the heck is GeanyPy, really?....................................9 3.2 Python Console..............................................9 3.3 Future Plans............................................... 10 4 Writing a Plugin - Quick Start Guide 11 4.1 The Plugin Interface........................................... 11 4.2 Real-world Example........................................... 12 4.3 Logging.................................................. 13 5 API Documentation 15 5.1 The app module............................................. 15 5.2 The dialogs module.......................................... 16 5.3 The document module......................................... 17 5.4 The geany package and module.................................... 19 6 Indices and tables 21 Python Module Index 23 i ii GeanyPy Documentation, Release 1.0 Contents: Contents 1 GeanyPy Documentation, Release 1.0 2 Contents CHAPTER 1 Introduction GeanyPy allows people to write their Geany plugins in Python making authoring a plugin much more accessible to non C programmers. What follows is a description of installing and using the GeanyPy plugin, paving the way for the rest of the documentation to covert the details of programming with the GeanyPy bindings of the Geany API. 3 GeanyPy Documentation, Release 1.0 4 Chapter 1. Introduction CHAPTER 2 Installation Currently there are no binary packages available for installing GeanyPy so it must be installed from source. The following instructions will describe how to do this. Getting the Source The best way currently to get GeanyPy is to check it out from it’s repository on GitHub.com. -
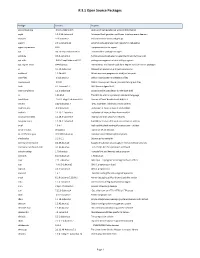
R 3.1 Open Source Packages
R 3.1 Open Source Packages Package Version Purpose accountsservice 0.6.15-2ubuntu9.3 query and manipulate user account information acpid 1:2.0.10-1ubuntu3 Advanced Configuration and Power Interface event daemon adduser 3.113ubuntu2 add and remove users and groups apport 2.0.1-0ubuntu12 automatically generate crash reports for debugging apport-symptoms 0.16 symptom scripts for apport apt 0.8.16~exp12ubuntu10.27 commandline package manager aptitude 0.6.6-1ubuntu1 Terminal-based package manager (terminal interface only) apt-utils 0.8.16~exp12ubuntu10.27 package managment related utility programs apt-xapian-index 0.44ubuntu5 maintenance and search tools for a Xapian index of Debian packages at 3.1.13-1ubuntu1 Delayed job execution and batch processing authbind 1.2.0build3 Allows non-root programs to bind() to low ports base-files 6.5ubuntu6.2 Debian base system miscellaneous files base-passwd 3.5.24 Debian base system master password and group files bash 4.2-2ubuntu2.6 GNU Bourne Again Shell bash-completion 1:1.3-1ubuntu8 programmable completion for the bash shell bc 1.06.95-2 The GNU bc arbitrary precision calculator language bind9-host 1:9.8.1.dfsg.P1-4ubuntu0.16 Version of 'host' bundled with BIND 9.X binutils 2.22-6ubuntu1.4 GNU assembler, linker and binary utilities bsdmainutils 8.2.3ubuntu1 collection of more utilities from FreeBSD bsdutils 1:2.20.1-1ubuntu3 collection of more utilities from FreeBSD busybox-initramfs 1:1.18.5-1ubuntu4 Standalone shell setup for initramfs busybox-static 1:1.18.5-1ubuntu4 Standalone rescue shell with tons of built-in utilities bzip2 1.0.6-1 High-quality block-sorting file compressor - utilities ca-certificates 20111211 Common CA certificates ca-certificates-java 20110912ubuntu6 Common CA certificates (JKS keystore) checkpolicy 2.1.0-1.1 SELinux policy compiler command-not-found 0.2.46ubuntu6 Suggest installation of packages in interactive bash sessions command-not-found-data 0.2.46ubuntu6 Set of data files for command-not-found. -

Guile-Gnome-Glib.Pdf
Guile-GNOME: GLib version 2.16.2, updated 9 December 2011 Owen Taylor Matthias Clasen Andy Wingo (many others) This manual is for (gnome glib) (version 2.16.2, updated 9 December 2011) Copyright 1999-2007 Owen Taylor, Matthias Clasen and others This work may be reproduced and distributed in whole or in part, in any medium, physical or electronic, so as long as this copyright notice remains intact and unchanged on all copies. Commercial redistribution is permitted and encouraged, but you may not redistribute, in whole or in part, under terms more restrictive than those under which you received it. If you redistribute a modified or translated version of this work, you must also make the source code to the modified or translated version available in electronic form without charge. However, mere aggregation as part of a larger work shall not count as a modification for this purpose. All code examples in this work are placed into the public domain, and may be used, modified and redistributed without restriction. BECAUSE THIS WORK IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY FOR THE WORK, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED IN WRIT- ING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES PROVIDE THE WORK "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. SHOULD THE WORK PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY REPAIR OR CORREC- TION. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR REDISTRIBUTE THE WORK AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAM- AGES ARISING OUT OF THE USE OR INABILITY TO USE THE WORK, EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

Estensione Dell'editor Bluefish Per Il Linguaggio Descrittivo Di Robot
Estensione dell'editor Bluefish per il linguaggio descrittivo di robot didattico NXT-GTD Valentini Riccardo Indice Sommario 3 1 Introduzione 4 1.1 Scopo . .4 1.2 Il linguaggio NXT-GTD . .5 1.3 Aspetti generali del linguaggio . .5 1.4 Esempi di comandi . .6 2 L'ambiente di sviluppo Bluefish 8 2.1 L'editor . .8 2.2 Caratteristiche dell'editor . 10 2.3 Altre funzionalit`a. 11 3 Il linguaggio Bflang2 (Bluefish language 2) 13 3.1 Qualche cenno su XML . 13 3.2 Bflang2 Schema . 17 3.2.1 header . 18 3.2.2 properties . 19 3.2.3 definition . 20 3.3 Descrizione del linguaggio XML mediante bflang . 25 4 Dalla sintassi al file .bflang2 28 4.1 Header . 28 4.2 Properties . 30 4.3 Definition . 30 5 Estensione dell'editor 37 Conclusioni 41 1 Bibliografia 42 Siti internet 43 2 Sommario Il linguaggio NXT-GTD `ela versione testuale del linguaggio visuale NXT usato per la programmazione dei robot didattici prodotti dalla LEGO R . La presenza di una versione testuale `edovuta alla necessit`adi documentare programmi relativamente complessi e resi in NXT-G che `eun linguaggio grafico-iconico. Per questo linguaggio tuttavia, non esistono ad ora editor in grado di riconoscerlo. Per questo motivo si `edeciso di fornire un ambiente di sviluppo che permetta di avere le stesse facilitazioni disponibili per gli altri linguaggi di programmazione. Per far ci`o`estato usato come base l'editor Bluefish, il quale permette la definizione di sintassi personali mediante la creazione di un file in formato bflang2, dalla struttura molto simile ad XML.