Internet Věcí (Internet of Things) a Jeho Bezpečnost
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Transactional Concurrency Control for Intermittent, Energy-Harvesting Computing Systems
PLDI ’19, June 22ś26, 2019, Phoenix, AZ, USA Emily Ruppel and Brandon Lucia 52, 55, 82] and preserving progress [6, 7, 53]. Recent work sequences of multiple tasks to execute atomically with re- addressed input/output (I/O), ensuring that computations spect to events. Coati’s support for events and transactions were timely in their consumption of data collected from sen- is the main contribution of this work. Coati provides the sors [15, 31, 86]. However, no prior work on intermittent critical ability to ensure correct synchronization across re- computing provides clear semantics for programs that use gions of code that are too large to complete in a single power event-driven concurrency, handling asynchronous I/O events cycle. Figure 1 shows a Coati program with three tasks con- in interrupts that share state with transactional computa- tained in a transaction manipulating related variables x, y, tions that execute in a main control loop. The idiomatic use of and z, while an asynchronous event updates x and y. Coati interrupts to collect, process, and store sensor results is very ensures atomicity of all tasks in the figure, even if any task common in embedded systems. The absence of this event- individually is forced to restart by a power failure. driven I/O support in intermittent systems is an impediment This work explores the design space of transaction, task, to developing batteryless, energy-harvesting applications. and event implementations by examining two models that Combining interrupts and transactional computations in make different trade-offs between complexity and latency. an intermittent system creates a number of unique problems Coati employs a split-phase model that handles time-critical that we address in this work using new system support. -

Design, the Future and the Human Spirit Victor Margolin
Design, the Future and the Human Spirit Victor Margolin Introduction Designers, like everyone else on the planet, have good reason to be concerned about the future. The world is volatile, and the ability of the human race to make a healthy home for itself is at stake. Threats from global warming, poor nutrition, disease, terrorism, and nuclear weapons challenge the potential of everyone to exercise productive energies for the common good. Designers are certainly among those whose positive contribu- tions are essential to the building of a more humane world. Trained in many disciplines—whether product design, architecture, engi- neering, visual communication, or software development—they are responsible for the artifacts, systems, and environments that make up the social world—bridges, buildings, the Internet, transportation, advertising, and clothing, to cite only a few examples. Companies would have nothing to manufacture without designers, nor would they have services to offer. Paradoxically, designers united as a professional class could be inordinately powerful and yet their voices in the various fora where social policies and plans are discussed and debated are rarely present. While the world has heard many calls for social change, few have come from designers themselves, in part because the design community has not produced its own arguments about what kinds of change it would like to see. Notwithstanding the discursive and practical potential to address this issue, the worldwide design community has yet to generate profession-wide visions of how its energies might be harnessed for social ends.1 As creators of models, prototypes, and propositions, design- ers occupy a dialectical space between the world that is and the world that could be. -

Beyond Interoperability – Pushing the Performance of Sensor Network IP Stacks
Industry: Beyond Interoperability – Pushing the Performance of Sensor Network IP Stacks JeongGil Ko Joakim Eriksson Nicolas Tsiftes Department of Computer Science Swedish Institute of Computer Swedish Institute of Computer Johns Hopkins University Science (SICS) Science (SICS) Baltimore, MD 21218, USA Box 1263, SE-16429 Kista, Box 1263, SE-16429 Kista, [email protected] Sweden Sweden [email protected] [email protected] Stephen Dawson-Haggerty Jean-Philippe Vasseur Mathilde Durvy Computer Science Division Cisco Systems Cisco Systems University of California, Berkeley 11, Rue Camille Desmoulins, Issy 11, Rue Camille Desmoulins, Issy Berkeley, CA 94720, USA Les Moulineaux, 92782, France Les Moulineaux, 92782, France [email protected] [email protected] [email protected] Abstract General Terms Interoperability is essential for the commercial adoption Experimentation, Performance, Standardization of wireless sensor networks. However, existing sensor net- Keywords work architectures have been developed in isolation and thus IPv6, 6LoWPAN, RPL, IETF, Interoperability, Sensor interoperability has not been a concern. Recently, IP has Network, TinyOS, Contiki been proposed as a solution to the interoperability problem of low-power and lossy networks (LLNs), considering its open 1 Introduction and standards-based architecture at the network, transport, For wireless sensor networks to be widely adopted by and application layers. We present two complete and in- the industry, hardware and software implementations from teroperable implementations of the IPv6 protocol stack for different vendors need to interoperate and perform well to- LLNs, one for Contiki and one for TinyOS, and show that gether. While IEEE 802.15.4 has emerged as a common the cost of interoperability is low: their performance and physical layer that is used both in commercial sensor net- overhead is on par with state-of-the-art protocol stacks cus- works and in academic research, interoperability at the phys- tom built for the two platforms. -

Bruce Sterling, July 2019
Science Fiction Book Club Interview with Bruce Sterling, July 2019 Bruce Sterling is a prominent science fiction writer and a pioneer of the cyberpunk genre. Novels like Heavy Weather (1994), Islands in the Net (1988), Schismatrix (1985), The Artificial Kid (1980) earned him the nickname “Chairman Bruce”. Apart from his writings, Bruce Sterling is also a professor of internet studies and science fiction at the European Graduate School. He has contributed to several projects within the scheme of futurist theory, founded an environmental aesthetic movement, edited anthologies and he still continues to write for several magazines including Wired, Discover, Architectural Record and The Atlantic. David Stuckey: Have you considered a return to the world of “The Difference Engine” for stories or another novel? Bruce Sterling: That won’t happen. David Stuckey: If you were going to write “Involution Ocean” today, what would you change or do differently? Bruce Sterling: Well, alien planet adventures are a really dated form of space opera. On the other hand, they’re great when you’re 20 years old. If I were doing a project like that today I might make it a comic book. Or a webcomic. It might make a nice anime cartoon. Richard Whyte: In the 2018 ‘State of the World’ conversation on the Well, you said you were in Ibiza working on a novel. Are you able to tell us anything about it yet? Bruce Sterling: I dunno if I’m ever gonna finish this epic novel about the history of the city of Turin, but I seem to get a lot of work done on it when I’m in Ibiza. -

Coap Based Acute Parking Lot Monitoring System Using Sensor Networks
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Directory of Open Access Journals ISSN: 2229-6948(ONLINE) ICTACT JOURNAL ON COMMUNICATION TECHNOLOGY: SPECIAL ISSUE ON ADVANCES IN WIRELESS SENSOR NETWORKS, JUNE 2014, VOLUME: 05, ISSUE: 02 COAP BASED ACUTE PARKING LOT MONITORING SYSTEM USING SENSOR NETWORKS R. Aarthi1 and A. Pravin Renold2 TIFAC-CORE in Pervasive Computing Technologies, Velammal Engineering College, India E-mail: [email protected], [email protected] Abstract it to aid in overall management and planning. Sensor networks Vehicle parking is the act of temporarily maneuvering a vehicle in to are a natural candidate for car-park management systems [6], a certain location. To deal with parking monitoring system issue such because they allow status to be monitored very accurately - for as traffic, this paper proposes a vision of improvements in monitoring each parking space, if desired. the vehicles in parking lots based on sensor networks. Most of the existing paper deals with that of the automated parking which is of cluster based and each has its own overheads like high power, less energy efficiency, incompatible size of lots, space. The novel idea in this work is usage of CoAP (Constrained Application Protocol) which is recently created by IETF (draft-ietf-core-coap-18, June 28, 2013), CoRE group to develop RESTful application layer protocol for communications within embedded wireless networks. This paper deals with the enhanced CoAP protocol using multi hop flat topology, which makes the acuters feel soothe towards parking vehicles. We aim to minimize the time consumed for finding free parking lot as well as increase the energy efficiency. -

English Version
Deloitte Perspective Deloitte Can the Punch Bowl Really Be Taken Away? The Future of Shared Mobility in China Perspective Gradual Reform Across the Value Chain 2018 (Volume VII) 2018 (Volume VII) 2018 (Volume About Deloitte Global Deloitte refers to one or more of Deloitte Touche Tohmatsu Limited, a UK private company limited by guarantee (“DTTL”), its network of member firms, and their related entities. DTTL and each of its member firms are legally separate and independent entities. DTTL (also referred to as “Deloitte Global”) does not provide services to clients. Please see www.deloitte.com/about to learn more about our global network of member firms. Deloitte provides audit & assurance, consulting, financial advisory, risk advisory, tax and related services to public and private clients spanning multiple industries. Deloitte serves nearly 80 percent of the Fortune Global 500® companies through a globally connected network of member firms in more than 150 countries and territories bringing world-class capabilities, insights, and high-quality service to address clients’ most complex business challenges. To learn more about how Deloitte’s approximately 263,900 professionals make an impact that matters, please connect with us on Facebook, LinkedIn, or Twitter. About Deloitte China The Deloitte brand first came to China in 1917 when a Deloitte office was opened in Shanghai. Now the Deloitte China network of firms, backed by the global Deloitte network, deliver a full range of audit & assurance, consulting, financial advisory, risk advisory and tax services to local, multinational and growth enterprise clients in China. We have considerable experience in China and have been a significant contributor to the development of China's accounting standards, taxation system and local professional accountants. -

Tecnologías De Fuentes Abiertas Para Ciudades Inteligentes
Open Smart Cities Tecnologías de fuentes abiertas para ciudades inteligentes www.cenatic.es Abril 2013 Open Smart Cities Tecnologías de fuentes abiertas para ciudades inteligentes Título: Open Smart Cities: Tecnologías de fuentes abiertas para ciudades inteligentes Autora: Ana Trejo Pulido Abril 2012 Edita: CENATIC. Avda. Clara Campoamor s/n. 06200 Almendralejo (Badajoz). Primera Edición. ISBN-13: 978-84-15927-13-6 Los contenidos de esta obra está bajo una licencia Reconocimiento 3.0 España de Creative Commons. Para ver una copia de la licencia visite http://creativecommons.org/licenses/by/3.0/es/ www.cenatic.es Pág. 2 de 59 Open Smart Cities Tecnologías de fuentes abiertas para ciudades inteligentes Índice 1 Introducción...............................................................................................................6 2 La Internet de las Cosas: hacia la ciudad conectada.................................................7 3 Tecnologías de código abierto para la Internet de las Cosas.....................................9 3.1 Waspmote.................................................................................................................10 3.2 Arduino......................................................................................................................10 3.3 Dash7........................................................................................................................11 3.4 Rasberry Pi................................................................................................................11 -

A Fog Storage Software Architecture for the Internet of Things Bastien Confais, Adrien Lebre, Benoît Parrein
A Fog storage software architecture for the Internet of Things Bastien Confais, Adrien Lebre, Benoît Parrein To cite this version: Bastien Confais, Adrien Lebre, Benoît Parrein. A Fog storage software architecture for the Internet of Things. Advances in Edge Computing: Massive Parallel Processing and Applications, IOS Press, pp.61-105, 2020, Advances in Parallel Computing, 978-1-64368-062-0. 10.3233/APC200004. hal- 02496105 HAL Id: hal-02496105 https://hal.archives-ouvertes.fr/hal-02496105 Submitted on 2 Mar 2020 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. November 2019 A Fog storage software architecture for the Internet of Things Bastien CONFAIS a Adrien LEBRE b and Benoˆıt PARREIN c;1 a CNRS, LS2N, Polytech Nantes, rue Christian Pauc, Nantes, France b Institut Mines Telecom Atlantique, LS2N/Inria, 4 Rue Alfred Kastler, Nantes, France c Universite´ de Nantes, LS2N, Polytech Nantes, Nantes, France Abstract. The last prevision of the european Think Tank IDATE Digiworld esti- mates to 35 billion of connected devices in 2030 over the world just for the con- sumer market. This deep wave will be accompanied by a deluge of data, applica- tions and services. -

NSF Nets Small RUI: Wireless Sensor Network Project
NSF NeTs Small RUI: Wireless Sensor Network Project Federal Agency and Organization Element to Which Report is Submitted: 4900 Federal Grant or Other Identifying Number Assigned by Agency: 1816197 Project Title: NeTS: Small: RUI: Bulldog Mote- Low Power Sensor Node and design Methodologies for Wireless Sensor Networks PD/PI Name: Nan Wang, Principal Investigator Woonki Na, Co-Principal Investigator Recipient Organization: California State University-Fresno Foundation Project/Grant Period: 10/01/2018 - 09/30/2021 Reporting Period: 10/01/2018 - 09/30/2019 Student Assistant: Russel Schellenberg Calvin Jarrod Smith Department of Electrical and Computer Engineering Lyles College of Engineering Contents 1 Purpose 3 2 Current Projects 3 2.1 Bulldog Mote . .3 2.2 Wireless Gateway Implementation . .3 2.2.1 Tmote Sky Mote . .3 2.2.2 Gateway Website . .7 2.3 MANET Routing Protocols and Software . .8 2.3.1 Contiki OS . .8 3 HM-10 BLE Communication Module 10 3.1 Overview . 10 3.2 HM-10 Module Configuration . 16 3.3 Connecting Two HM-10 Devices . 17 3.3.1 Setting up Slave Device . 18 3.3.2 Setting up Master Device . 18 3.3.3 Discovery Connection . 19 3.4 Connecting to HM-10 from Android Phone . 23 4 Wireless Gateway Implementation 30 4.1 Gateway Operating System and Environment . 30 4.2 Required hardware: . 30 4.3 Installation . 30 4.4 Contiki Program . 31 4.5 Gateway Program . 32 4.6 Web Server . 32 5 One-Hop, Ad-Hoc Sensor Network with Cooja 36 5.1 Overview . 36 5.2 Peripheral Node Gateway Detection . -
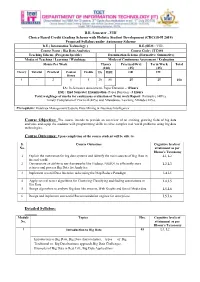
(CBCGS-H 2019) Proposed Syllabus Under Autonomy Scheme
B.E. Semester –VIII Choice Based Credit Grading Scheme with Holistic Student Development (CBCGS-H 2019) Proposed Syllabus under Autonomy Scheme B.E.( Information Technology ) B.E.(SEM : VIII) Course Name : Big Data Analytics Course Code : ITC801 Teaching Scheme (Program Specific) Examination Scheme (Formative/ Summative) Modes of Teaching / Learning / Weightage Modes of Continuous Assessment / Evaluation Hours Per Week Theory Practical/Oral Term Work Total (100) (25) (25) Theory Tutorial Practical Contact Credits IA ESE OR TW Hours 4 - 2 6 5 20 80 25 25 150 IA: In-Semester Assessment- Paper Duration – 1Hours ESE : End Semester Examination- Paper Duration - 3 Hours Total weightage of marks for continuous evaluation of Term work/Report: Formative (40%), Timely Completion of Practical (40%) and Attendance /Learning Attitude (20%). Prerequisite: Database Management System, Data Mining & Business Intelligence Course Objective: The course intends to provide an overview of an exciting growing field of big data analytics and equip the students with programming skills to solve complex real world problems using big data technologies. Course Outcomes: Upon completion of the course student will be able to: S. Course Outcomes Cognitive levels of No. attainment as per Bloom’s Taxonomy 1 Explain the motivation for big data systems and identify the main sources of Big Data in L1, L2 the real world. 2 Demonstrate an ability to use frameworks like Hadoop, NOSQL to efficiently store L2,L3 retrieve and process Big Data for Analytics. 3 Implement several Data Intensive tasks using the Map Reduce Paradigm L4,L5 4 Apply several newer algorithms for Clustering Classifying and finding associations in L4,L5 Big Data 5 Design algorithms to analyze Big data like streams, Web Graphs and Social Media data. -

The 2009 Shift Index
Measuring the forces of long-term change The 2009 Shift Index Deloitte Center for the Edge John Hagel III, John Seely Brown, and Lang Davison Core Research Team Duleesha Kulasooriya Tamara Samoylova Brent Dance Mark Astrinos Dan Elbert Foreword A seemingly endless stream of books, articles, reports, applications, it may have more impact in how it changes and blogs make similar claims: The world is flattening; our conception of the economy. Interpreted through the the economy has picked up speed; computing power is lens of neoclassical economics, the Shift Index captures increasing; competition is intensifying. shifts in fundamentals, particularly on the cost side where technological changes allow firms to do more with less. Though we’re aware of these trends in the abstract, But, the Shift Index, by name alone, calls into question the we lack quantified measures. We know that a shift is neoclassical mindset that focuses on re-equilibration. underway, but we have no method of characterizing its speed or acceleration or making comparisons. Are The Shift Index resonates instead with a conceptual model rates of change increasing, decreasing, or settling into of the world economy based on complex dynamics. In stable patterns (e.g. Moore’s Law)? How do we compare this framework, the economy can be conceptualized as a exponential changes in bandwidth to linear increases complex adaptive system with diverse entities adaptively in Internet usage? Without times series data and a interacting to produce emergent patterns (and occasional methodology for integrating those data, we cannot large events). If one embraces the complex, dynamic identify, anticipate, or plan for change. -

Redefine Work: the Untapped Opportunity for Expanding Value
A report from the Deloitte Center for the Edge Redefine work The untapped opportunity for expanding value Deloitte Consulting LLP’s Human Capital practice focuses on optimizing and sustaining organiza- tional performance through their most important asset: their workforce. We do this by advising our clients on a core set of issues including: how to successfully navigate the transition to the future of work; how to create the “simply irresistible” experience; how to activate the digital orga- nization by instilling a digital mindset—and optimizing their human capital balance sheet, often the largest part of the overall P&L. The practice’s work centers on transforming the organization, workforce, and HR function through a comprehensive set of services, products, and world-class Bersin research enabled by our proprietary Human Capital Platform. The untapped opportunity for expanding value Contents Introduction: Opportunity awaits—down a different path | 2 A broader view of value | 4 Redefining work everywhere: What does the future of human work look like? | 6 Breaking from routine: Work that draws on human capabilities | 11 Focusing on value for others | 18 Making work context-specific | 21 Giving and exercising latitude | 25 How do we get started? | 31 Endnotes | 34 1 Redefine work Introduction: Opportunity awaits—down a different path Underneath the understandable anxiety about the future of work lies a significant missed opportunity. That opportunity is to return to the most basic question of all: What is work? If we come up with a creative answer to that, we have the potential to create significant new value for the enterprise.