Registry Edits for Windows XP
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Text File Converted with Freeware Acropad
XP Tips & Tweaks These tips and tweaks have come from hundreds of individuals across the internet. I have included some of web sites links (below) that cover this popular topic. I have not tried most of these tips, so let me know if some don't work or have mistakes. Tips & Tweaks Links TipsDr Paul Thurrott's Supersite for Windows - XP Tips & Tricks Microsoft WinXP Support Center Microsoft WinXP Professional Microsoft WinXP Home Microsoft WinXP Knowledge Base Articles Microsoft Power Toys for Windows XP Microsoft Windows XP Tips Microsoft Windows XP User Tips Archive Microsoft Windows XP Professional Tips Microsoft Windows XP Home Edition Tips Microsoft Tips & Tricks for Windows XP Professional Microsoft Tips for Techies Stop Jerky Graphics If you are connected to a LAN and have problems with jerky graphics, this might be the solution: ·Right-click "My Computer". ·Select "Manage". ·Click on "Device Manager". ·Double-click on your NIC under "Network Adapters". ·In the new window, select the "Advanced" tab. ·Select "Connection Type" and manually set the value of your NIC. (Not "Auto Sense" which is default.). ·You should reboot. Shutdown XP Faster Like previous versions of windows, it takes long time to restart or shutdown windows XP when the "Exit Windows" sound is enabled. To solve this problem you must disable this useless sound. ·Click Start button. ·Go to settings > Control Panel > Sound, Speech and Audio devices > Sounds and Audio Devices > Sounds. ·Then under program events and windows menu click on "Exit Windows" sub-menu and highlight it. Now from sounds you can select, choose "none" and then click Apply and OK. -

Restoration Onto Different Hardware (PDF)
Restoration onto different Hardware Quick and easy system restore with O&O DiskImage Table of contents System restoration using boot media ...................................................................................... 1 Restoration onto different hardware ....................................................................................... 2 Limitations when restoring onto different hardware ................................................................................................................. 3 Automatic update............................................................................................................................... ............................................. 3 Manual adaptation .......................................................................................................................................................................... 4 Enable automatic adaptation on changed hardware (M.I.R.) .................................................................................................... 4 Assistance when error messages occur during booting .......................................................... 7 I System restoration using boot media Disks where you save your private and business data can be quickly imaged and restored in the event of a crash or hardware damage. Creating an image of your entire computer or the system partition is also very easy. To restore an image of a Windows system, you’ll need to start O&O DiskImage directly from a bootable medium *. *Note You’ll need to -

Ubuntu Kung Fu
Prepared exclusively for Alison Tyler Download at Boykma.Com What readers are saying about Ubuntu Kung Fu Ubuntu Kung Fu is excellent. The tips are fun and the hope of discov- ering hidden gems makes it a worthwhile task. John Southern Former editor of Linux Magazine I enjoyed Ubuntu Kung Fu and learned some new things. I would rec- ommend this book—nice tips and a lot of fun to be had. Carthik Sharma Creator of the Ubuntu Blog (http://ubuntu.wordpress.com) Wow! There are some great tips here! I have used Ubuntu since April 2005, starting with version 5.04. I found much in this book to inspire me and to teach me, and it answered lingering questions I didn’t know I had. The book is a good resource that I will gladly recommend to both newcomers and veteran users. Matthew Helmke Administrator, Ubuntu Forums Ubuntu Kung Fu is a fantastic compendium of useful, uncommon Ubuntu knowledge. Eric Hewitt Consultant, LiveLogic, LLC Prepared exclusively for Alison Tyler Download at Boykma.Com Ubuntu Kung Fu Tips, Tricks, Hints, and Hacks Keir Thomas The Pragmatic Bookshelf Raleigh, North Carolina Dallas, Texas Prepared exclusively for Alison Tyler Download at Boykma.Com Many of the designations used by manufacturers and sellers to distinguish their prod- ucts are claimed as trademarks. Where those designations appear in this book, and The Pragmatic Programmers, LLC was aware of a trademark claim, the designations have been printed in initial capital letters or in all capitals. The Pragmatic Starter Kit, The Pragmatic Programmer, Pragmatic Programming, Pragmatic Bookshelf and the linking g device are trademarks of The Pragmatic Programmers, LLC. -
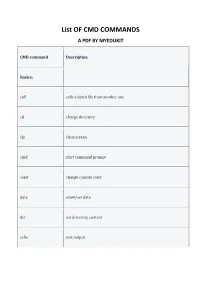
List of CMD COMMANDS a PDF by MYEDUKIT
List OF CMD COMMANDS A PDF BY MYEDUKIT CMD command Description Basics: call calls a batch file from another one cd change directory cls clear screen cmd start command prompt color change console color date show/set date dir list directory content echo text output exit exits the command prompt or a batch file find find files hostname display host name pause pauses the execution of a batch file and shows a message runas start a program as another user shutdown shutdown the computer sort sort the screen output start start an own window to execute a program or command taskkill terminate a process or an application tasklist display applications and related tasks time display/edit the system time timeout wait any time title set title for prompt ver display operating system version w32tm setting time synchronisation/time server/time zone Network: ftp transfer files to an FTP server ftype display file type and mapping getmac display MAC address ipconfig display IP network settings netsh configure/control/display network components netstat display TCP/IP connections and status nslookup query the DNS pathping test the connection to a specific IP address ping pings the network route display network routing table, add static routes systeminfo displays computer-specific properties and configurations telnet establish a Telnet connection tftp transfer files to a TFTP server tracert trace routes similar to patchping Files: attrib display file attributes comp compare file contents compact display/change file compression copy / xcopy copy files diskcomp -

Solve Errors Caused by Corrupt System Files
System File Corruption Errors Solved S 12/1 Repair Errors Caused by Missing or Corrupt System Files With the information in this article you can: • Find out whether corrupt system files could be causing all your PC problems • Manually replace missing system files using your Windows installation CD • Use System File Checker to repair broken Windows system files • Boost the memory available to Windows File Protection for complete system file protection Missing or corrupt system files can cause many problems when using your PC, from cryptic error messages to mysterious system crashes. If one of the key files needed by Windows has gone missing or become corrupt, you may think that the only way to rectify the situation is to re-install Windows. Fortunately, nothing that drastic is required, as Microsoft have included several tools with Windows that allow you to replace corrupt or missing files with new, fresh copies directly from your Windows installation CD. Now, whenever you find that an important .DLL file has been deleted or copied over, you won’t have to go to the trouble of completely re-installing your system – simply replace the offending file with a new copy. Stefan Johnson: “One missing file can lead to your system becoming unstable and frequently crashing. You may think that the only way to fix the problem is to re-install Windows, but you can easily replace the offending file with a fresh copy from your Windows installation CD.” • Solve errors caused by corrupt system files ................... S 12/2 • How to repair your missing system file errors .............. -

Windows Messenger Live Msn Download
Windows messenger live msn download Windows Live Messenger latest version: See. Hear. Share. Instantly.. Windows Live Messenger previously known as MSN Messenger, was renamed as part of. MSN Messenger is an instant messaging program that lets you send instant messages to your friends, and much more. Previously known as MSN Messenger, Windows Live Messenger is Microsoft's answer to instant messaging. While largely the same as its predecessor. Windows Live Messenger free download. on their MSN or Hotmail account, as the integration with the email accounts can be. Mobile and web: Using a public computer without Messenger? No problem! You can chat on the web from Windows Live Hotmail or use. Share photos: Look at photos together, right in the conversation window and Messenger tells you when people you know post new photos on Windows Live. Microsoft Windows live messenger free Download Link: Latest Version. Old Version of MSN (Live) Messenger. Website. Developer. Microsoft Corporation. Latest Version. Windows. Messenger, which offers the user the same functionalities as Windows Live Messenger. Windows Live Messenger Final Deutsch: Der Windows Live Messenger, Nachfolger des MSN Messenger, in der Version: - vom How to Download and Install Windows Live Messenger. Windows Live Messenger is a great way to talk to people online. You can now have a personal picture. Windows 7 by default is installed without Windows Live Messenger. So to get it, we will need to download and install it. select, like setting Bing as the default search provider and setting MSN as your browser home page. is a free, personal email service from Microsoft. -

Prepare Customer Site Servers
Prepare Customer Site Servers • Prepare Customer Site Servers, on page 1 • Prepare Cisco UCS C-Series Customer Site Servers, on page 1 • Prepare HyperFlex M5 series Customer Site Servers, on page 3 • NTP and Time Synchronization, on page 4 • Global Catalog Requirements, on page 5 Prepare Customer Site Servers Perform all the procedures in this section on the Side A and the Side B servers. Prepare Cisco UCS C-Series Customer Site Servers Configure RAID for C240 M4SX The disk array configuration for the C240 M4SX is already set up to match what is required for Packaged CCE. Verify the settings as follows. Using Cisco Integrated Management Controller, check that the following settings are configured correctly: • Virtual Drive Info: RAID 5 with 5 (Physical Disks) * 4 (Virtual Drives/Datastores) • Stripe Size: 128KB • Write Policy: Write Back with BBU • Read Policy: Read Ahead Always For more information regarding RAID configuration for C240 M4SX in Configure RAID with GUI (UCS C-Series M4 Servers) section, see Cisco Collaboration on Virtual Servers Guide at: https://www.cisco.com/ c/en/us/td/docs/voice_ip_comm/cucm/virtual/CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers/ CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers_chapter_01.html#CUCM_TK_C2DC4F2D_ 00. Prepare Customer Site Servers 1 Prepare Customer Site Servers Run the RAID Config Validator Utility Run the RAID Config Validator Utility After you set up RAID configuration and add the datastores, run the RAID Config Validator utility to ensure that your datastore configuration is correct. Before you begin To run the utility, Java 7 (any update) must be installed. Java 8 and later releases are not supported. -

Deployment Strategy
System Management Best Practices Bryan S Owen PE Copyright c 2004 OSIsoft Inc. All rights reserved. Richness & Reliability “Value Coefficients” • Quality – Across operations and data systems • Quantity – Across business needs and over time • Utilization – Across enterprise and just in time It all Starts with Great Software …and the Right Architecture • Visualization Tools • Availability • Reliability • Security Integrated Data Collection Proven: Cutting Edge: Integrated Interface Embedded Historian Embedded PI Historian • Continuous Historian for DeltaV Application Station http://www.easydeltav.com/pd/PDS_ApplicationStation.pdf • “56SAM” Historian for Allen-Bradley ControlLogix www.oldi.com • “Promoted” Interface Node • Also visit: www.echohistorian.com Fault Tolerant vs Redundant Incident Tolerant Redundant Environment Fault JJ JJJ Hardware Fault JJJ JJ Software Fault K J Administrative Error JK JJ Scheduled Down K JJJ “Smile” Points: 15/30 22/30 Redundant Architecture • Reliability – Build from the Data Up • Availability – Build from the Users Down You decide what comes first! Redundant Data Collection Dual Gateways Interface Node Failover Redundant Data Service Dual PI Servers Dual PI Clients Redundant Architecture No single point of failure sounds great, what’s the catch? • Interface Support • History Recovery • Gap Filling • Client Impact • Fugitive Data Fugitive Data Capture Essential for rich content but… 1% of the data causes 99% perspiration! • Manual Entry Systems • Custom Applications • Isolated Point to Point Links Solution: -

Microsoft Windows Server 2019 Version 1809 Hyper-V
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

IIS Security and Programming Countermeasures
IIS Security and Programming Countermeasures By Jason Coombs ([email protected]) Introduction This is a book about how to secure Microsoft Internet Information Services for administrators and programmers whose work includes a requirement for information security, a computer industry specialty field commonly referred to as infosec. In this book the terms information security and infosec are used interchangeably with the more friendly term data security. This is not a book about hacking, cracking, and the tools and techniques of the bad guys, the so-called black hat hackers. This book teaches computer professionals and infosec specialists how to build secure solutions using IIS. It is your duty to secure and defend networked information systems for the benefit of the good guys who are your end users, clients, or less technical coworkers. There is nothing you can do that will transform a programmable computer running Microsoft Windows from its vulnerable condition to an invulnerable one. Every general purpose programmable computer is inherently vulnerable because it is controlled by software and is designed to allow new software to be installed or executed arbitrarily. Network computing based on programmable general purpose computers will never be safe from an information security perspective. Eliminating the feature of general purpose programmability from a networked computer and replacing its software with firmware reduces but does not eliminate vulnerabilities. These are immutable realities of present day computing and, as always, reality represents your biggest challenge. Microsoft is in business to get as much of your money as possible using whatever means will work at a given moment and in this respect they know virtually no equal in the software business. -

WAF/CDP V3.7.1 User Guide
WAFS/CDP v3.7.1 User Guide GlobalSCAPE, Inc. (GSB) 4500 Lockhill-Selma Road, Suite 150 Address: San Antonio, TX (USA) 78249 Sales: (210) 308-8267 Sales (Toll Free): (800) 290-5054 Technical Support: (210) 366-3993 Web Support: http://www.globalscape.com/support/ © 2004-2010 GlobalSCAPE, Inc. All Rights Reserved July 21, 2010 Table of Contents GlobalSCAPE Replication Software ............................................................................................................. 7 What's New? .............................................................................................................................................. 7 For the Best WAFS/CDP Experience .................................................................................................... 8 Getting Started .............................................................................................................................................. 9 WAFS Quick Start ..................................................................................................................................... 9 CDP Quick Start ...................................................................................................................................... 11 Quick Reference ...................................................................................................................................... 13 File-Naming Conventions ........................................................................................................................ 13 WAFS/CDP -

Operational and Administrative Guidance
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious.