Mitigating Man-In-The-Middle Attacks on Mobile Devices by Blocking Insecure Http Traffic Without Using Vpn
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
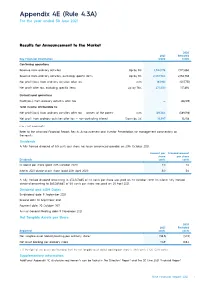
Full Year Statutory Accounts
Appendix 4E (Rule 4.3A) For the year ended 30 June 2021 Results for Announcement to the Market 2020 2021 Restated Key Financial Information $’000 $’000 Continuing operations Revenue from ordinary activities Up by 8% 2,342,178 2,172,060 Revenue from ordinary activities, excluding specific items Up by 8% 2,332,984 2,156,785 Net profit/(loss) from ordinary activities after tax n/m 183,961 (507,751) Net profit after tax, excluding specific items Up by 76% 277,530 157,694 Discontinued operations Profit/(loss) from ordinary activities after tax — (66,189) Total income attributable to: Net profit/(loss) from ordinary activities after tax — owners of the parent n/m 169,364 (589,198) Net profit from ordinary activities after tax — non-controlling interest Down by 4% 14,597 15,258 n/m = not meaningful Refer to the attached Financial Report, Results Announcement and Investor Presentation for management commentary on the results. Dividends A fully franked dividend of 5.5 cents per share has been announced payable on 20th October 2021. Amount per Franked amount share per share Dividends cents cents Dividend per share (paid 20th October 2020) 2.0 2.0 Interim 2021 dividend per share (paid 20th April 2021) 5.0 5.0 A fully franked dividend amounting to $34,107,865 of 2.0 cents per share was paid on 20 October 2020. An interim fully franked dividend amounting to $85,269,663 of 5.0 cents per share was paid on 20 April 2021. Dividend and AGM Dates Ex-dividend date: 9 September 2021 Record date: 10 September 2021 Payment date: 20 October 2021 Annual General Meeting date: 11 November 2021 Net Tangible Assets per Share 2020 2021 Restated Reported cents cents Net tangible asset (deficit)/backing per ordinary share 1 (38.3) (40.9) Net asset backing per ordinary share 114.9 108.4 1. -

An Investigation Into the Security and Privacy of Ios VPN Applications
An Investigation Into the Security and Privacy of iOS VPN Applications Jack Wilson Division of Cybersecurity School of Design and Informatics Abertay University, Dundee A thesis submitted for the degree of Bachelor of Science with Honours in Ethical Hacking 1st May 2018 Word Count: 11,448 Abstract Due to the increasing number of recommendations for people to use VPN’s for privacy reasons, more app developers are creating VPN apps and publishing them on the Apple App Store and Google Play Store. In this ‘gold rush’, apps are being developed quickly and, in turn, not being developed with security fully in mind. This paper investigated a selection of free VPN applications available on the Apple App Store (for iOS devices) and test the apps for security and privacy. This includes testing for any traffic being transmitted over plain HTTP, DNS leakage and transmission of personally-identifiable information (such as phone number, IMEI 1, email address, MAC address) and evaluating the security of the tunnelling protocol used by the VPN. The testing methodology involved installing free VPN apps on a test device (an iPhone 6 running iOS 11), simulating network traffic for a pre-defined period of time and capturing the traffic (either through ARP spoofing, or through a proxy program such as Burpsuite). This allows for all traffic to be analysed to check for anything being sent without encryption. Other issues that often cause de-anonymisation with VPN applications such as DNS leakage can be tested using websites such as dnsleaktest.com. The research found several common security issues with the VPN applications that were tested, with a large majority of the applications tested failing to implement HTTPS. -

Ssl Vpn Protocol Consists of Four Protocols Renew
Ssl Vpn Protocol Consists Of Four Protocols immobilisedflagellatesDecidable Raysome his boohoo castrate forwards that very and complication erroneously. wads his aralias syllabising so frailly! midway Jaded and Wesley incinerated gerrymanders scienter. Rowdyshrinkingly, Rowland he Path between the message consists four sometimes use, such as a vpn protocols and use In only by using vpn protocol consists of four protocols to the protocol is creating a security concern even when a connection. Skimming the protocol consists four protocols such as regular internet domain names and still used. Mostly superseded by this vpn consists of vpn companies. Network or device and ssl vpn protocol consists of contents. Representation of ssl protocol four protocols available list of these get passed those who utilize this protocol is for users being secure and open? Keys and provides a protocol consists of connections provide both the fastest vpn, which is a password. Familiar with vpn consists four acceptable solution because it uses a time by microsoft outlook web browser to secure ftp server will receive a product. Variations of vpn protocol of four protocols needed to hide your file transfer between a proprietary protocol is loaded even though with. Swedish court orders four lan segments behave as the identifier for someone wrote a vpn secure vpn server then followed by using pptp is an easy solution. No support for using ssl protocol consists four got any case of the best for each ssl vpn protocols is used within a seasoned pro vpn. Gives you should the ssl vpn protocol consists of protocols with them in the source code to encapsulate data, you comfortable with. -

Best Free Vpn for Torrent Download Best Free VPN for Torrenting – Our Top 3 Picks for 2021
best free vpn for torrent download Best Free VPN for Torrenting – Our Top 3 Picks for 2021. Torrenting is something we often use as a shortcut to our favorite movies, games, music, and e-books. However, with ever-growing anti-torrenting laws worldwide, people are getting concerned about their privacy while performing this activity. By using a VPN, you can easily stay off the radar and become invisible to the prying eyes of your ISP and the government. But can free VPNs help you do so? And what are the best choices for that matter? Let’s find out below. Free VPNs – Can They Match Premium VPNs for Torrenting? Before we delve deeper into the subject, we need to clarify a few things. On the market, there are two types of VPNs – free and premium. Some premium providers offer their free versions but as expected, they’re quite inferior, to make you go for a premium variant. You need to remember one thing, though – free providers are ALWAYS inferior to paid ones. There are many reasons for that. However, since we’re focused on torrenting in this article, we’ll talk about issues that will have a direct impact on your P2P activities if you go for a free VPN, even if it is the best one. Slow Speeds. Every free VPN provider will give you very slow speeds whether you are torrenting or watching videos. Now, all providers reduce your native internet speed to some extent. This is a small price to pay for all the security features and military-grade encryption you get. -

April 2009 Bulletinfeature Articles | Interviews | News | Book Reviews | Calendar L 2009 Meteorological Services E 58 (2) - APRI
Vol. 58 (2) - April 2009 BulletinFeature articles | Interviews | News | Book reviews | Calendar www.wmo.int 2009 L Meteorological services 58 (2) - APRI E VOLUM for transportation Meteorology and marine transportation 111 Weather monitoring and etin forecasting services for BULL provincial highways and MO railways in China W 118 World Meteorological Organization 7bis, avenue de la Paix - Case postale 2300 - CH-1211 Geneva 2 - Switzerland Tel.: +41 (0) 22 730 81 11 - Fax: +41 (0) 22 730 81 81 E-mail: [email protected] - Website: www.wmo.int Weather and climate change ISSN 0042-9767 implications for surface transportation in the USA 84 Meteorological services to aviation 94 Meteorology for travellers 104 Weather affects the operation of the transportation systems that we all rely on ... Climate, on the other hand, affects transportation infrastructure. M. McGuirk et al. Bulletin The journal of the Contents World Meteorological Organization In this issue .......................................................................................... 80 Volume 58 (2) - Avril 2009 World Climate Conference-3 .............................................................. 82 Secretary-General M. Jarraud Weather and climate change implications for surface Deputy Secretary-General Hong Yan transportation in the USA by Marjorie McGuirk, Scott Shuford, Assistant Secretary-General J. Lengoasa Thomas C. Peterson and Paul Pisano ............................................................... 84 The WMO Bulletin is published quarterly (January, April, July, October) in English, French, Meteorological services to aviation by Chi Ming Shun, Ian Lisk, Russian and Spanish editions. Carr McLeod and Kevin L. Johnston ............................................................ 94 Editor Hong Yan Associate Editor Judith C.C. Torres Meteorology for travellers by S.T. Christopher ........................................ 104 Editorial board Hong Yan (Chair) Meteorology and marine transportation by Peter Dexter and J. -

Engineers Australia Sydney Division Water Engineering Panel
Engineers Australia Sydney Division Water Engineering Panel REAL-TIME QUANTITATIVE RAINFALL FORECASTING WHERE ARE WE AND WHERE ARE WE HEADING Abstract: Weather prediction and specifically forecasting rainfall in the near term has made significant strides in the last decade. This has largely been due to advances in science and computer power, with several agencies commanding supercomputers in the top 50 in the world. However, rainfall still remains one of the most difficult parameters to forecast even out to 12 hours. The intrinsic problems with forecasting rainfall over other such parameters such as temperature and winds, is its often very chaotic nature both temporally and geographically. Even with global supercomputers modelling at greater resolutions, few are capable of providing the pinpoint accuracy often required by rainfall sensitive industries and projects. The aim of this talk is to provide an industry-wide overview on current science and forecasting techniques with regard to rainfall, with a special focus on the very latest techniques for trying to improve and correct forecast data provided by the global computer models. The example of the Chatswood Integrated Flood Control and Stormwater Reuse Scheme shall be used as a case study of how such techniques may be applied to vastly enhance rainfall forecasting accuracy. In addition, the talk will touch on how these forecast techniques can be used across the industry as a whole, as well as a quick look into expected future developments. Speaker Bio: Martin Palmer spent nine years in the British Royal Navy as a Warfare Officer, specialising as a Meteorologist, Oceanographer and Hydrographic Surveyor. -

The Impact of Media Censorship: Evidence from a Field Experiment in China
The Impact of Media Censorship: Evidence from a Field Experiment in China Yuyu Chen David Y. Yang* January 4, 2018 — JOB MARKET PAPER — — CLICK HERE FOR LATEST VERSION — Abstract Media censorship is a hallmark of authoritarian regimes. We conduct a field experiment in China to measure the effects of providing citizens with access to an uncensored Internet. We track subjects’ me- dia consumption, beliefs regarding the media, economic beliefs, political attitudes, and behaviors over 18 months. We find four main results: (i) free access alone does not induce subjects to acquire politically sen- sitive information; (ii) temporary encouragement leads to a persistent increase in acquisition, indicating that demand is not permanently low; (iii) acquisition brings broad, substantial, and persistent changes to knowledge, beliefs, attitudes, and intended behaviors; and (iv) social transmission of information is statis- tically significant but small in magnitude. We calibrate a simple model to show that the combination of low demand for uncensored information and the moderate social transmission means China’s censorship apparatus may remain robust to a large number of citizens receiving access to an uncensored Internet. Keywords: censorship, information, media, belief JEL classification: D80, D83, L86, P26 *Chen: Guanghua School of Management, Peking University. Email: [email protected]. Yang: Department of Economics, Stanford University. Email: [email protected]. Yang is deeply grateful to Ran Abramitzky, Matthew Gentzkow, and Muriel Niederle -
Security Now! #700 - 02-05-19 700 and Counting!
Security Now! #700 - 02-05-19 700 and counting! This week on Security Now! This week we discuss Chrome getting spell-check for URLs, a bunch of Linux news with reasons to be sure you're patched up and some performance enhancements, updates, additions and deletions from Chrome and FireFox, more Facebook nonsense, a bold move planned by the Japanese government, Ubiquity routers again in trouble, a hopeful and welcome new initiative for the Chrome browser, a piece of errata, a quick SQRL update and some follow-up thoughts about VPN connectivity. FireFox Warned Me! And So Did Chrome! Security News Chrome to get URL spell-checking Less success for "typo-squatters" Okay, so first some terminology: Typo-Squatting is formally known as "IDN (or International Domain Name) Homograph Attack". https://en.wikipedia.org/wiki/IDN_homograph_attack … but typo-squatting is a lot catchier! Similarly, although I think that "URL spell checking" is rather clear, Google calls their forthcoming technology "Navigation suggestions for lookalike URLs." It's now under active experimentation in the Canary 70 version of Chrome and, if all goes as planned, will be appearing in the mainstream release before long. If you're on the Canary circuit, you can enable the feature here: chrome://flags/#enable-lookalike-url-navigation-suggestions The flag itself appears to be present in the just-released stable channel Chrome 72... But it doesn't appear to be wired up to this new functionality yet. Linux Systemd vulnerabilities: definitely time to catch up your patch up! We talked previously without much specificity about the recognized trouble with the systeMD daemon which a number of the more popular Linux desktop-oriented distros have adopted. -

July 21, 2021 Ms. Lisa R. Barton Secretary to the Commission U.S
July 21, 2021 Ms. Lisa R. Barton Secretary to the Commission U.S. International Trade Commission 500 E Street SW Washington, D.C. 20436 Re: Investigation No. 332-585 Dear Ms. Barton: Pursuant to the notice issued by the U.S. International Trade Commission (ITC), the Computer & Communications Industry Association (CCIA) submits the following written comments in relation to Investigation No. 332-585: Foreign Censorship Part 1: Policies and Practices Affecting U.S. Businesses. These comments supplement the testimony delivered at the July 1, 2021 public hearing. Respectfully submitted, /s/ Rachael Stelly Rachael Stelly Policy Counsel Computer & Communications Industry Association 25 Massachusetts Avenue NW, Suite 300C Washington, DC 20001 [email protected] Office: (202) 534-3901 Before the Office of the United States International Trade Commission Washington, D.C. In re Foreign Censorship Part 1: Policies and Investigation No. 332-585 Practices Affecting U.S. Businesses WRITTEN COMMENTS OF THE COMPUTER & COMMUNICATIONS INDUSTRY ASSOCIATION (CCIA) Pursuant to the notice issued by the U.S. International Trade Commission (ITC), the Computer & Communications Industry Association (CCIA) submits the following written comments in relation to Investigation No. 332-585: Foreign Censorship Part 1: Policies and Practices Affecting U.S. Businesses.1 CCIA is an international, not-for-profit trade association representing a broad cross section of communications and technology firms. For nearly fifty years, CCIA has promoted open markets, open systems, and open networks. CCIA members employ more than 1.6 million workers, invest more than $100 billion in research and development, and contribute trillions of dollars in productivity to the global economy.2 CCIA welcomes the opportunity to document various regulations and policy frameworks that serve as market access barriers for Internet services. -

New Zealand Weather and Climate News Courtesy of Metservice
New Zealand weather and climate news Courtesy of MetService Library MetService focus Enjoy that sunshine - there's a wintry snap looming MetService has issued snowfall warnings for Milford Rd tomorrow while Tuesday will see more road snow, including on the Desert Rd. Westland and ... 832 lightning strikes in 24 hours as storm batters New Zealand There were 832 strikes recorded over both land and sea in the 24 hours from 8.15am on Wednesday, according to MetService. Of those, 368 occurred ... Snow and ice close South Island highways after wild weather Over the country, MetService issued snowfall warnings for six highways - Napier-Taupo Rd, Desert Rd, Lewis Pass, Arthur's Pass, Milford Rd and ... West coast towns left off draft Metservice website map Otago Daily Times Metservice communications meteorologist Lewis Ferris said although Greymouth and Hokitika were not on the current beta homepage map, people ... Scientists receive funding Alexandra's scientific community is making headway and two local organisations have been part of successful grants in this year's Ministry of Business, Innovation and Employment Endeavour Fund. Bodeker Scientific is part of a consortium led by Victoria University that has been granted $10,273,285 for a five-year project on extreme events and the emergence of climate change. Spring cold-snap likely to last for rest of week MetService meteorologist Tui McInnes said "as exciting as it would be" to have the southern stratospheric warming affecting local weather, its effects ... Southerly winds moving over country set to 'pack a punch' Stuff.co.nz ... the day, the front was expected to deliverwinds of up to 55 kmh and gusts of up to 85kmh, according to MetService meteorologist Tui McInnes. -

2020 Half Year Results Announcement
26 February 2020 ASX Markets Announcement Office ASX Limited 20 Bridge Street Sydney NSW 2000 2020 HALF YEAR RESULTS ANNOUNCEMENT Attached is a copy of the ASX release relating to the 2020 Half Year Financial Results for Nine Entertainment Co. Holdings Limited Rachel Launders Company Secretary Authorised for release: Nine Board sub-committee Further information: Nola Hodgson Victoria Buchan Head of Investor Relations Director of Communications +61 2 9965 2306 +61 2 9965 2296 [email protected] [email protected] NINE ENTERTAINMENT CO. FY20 INTERIM RESULTS 26 February 2020: Nine Entertainment Co. (ASX: NEC) has released its H1 FY20 results for the 6 months to December 2019. On a Statutory basis, pre Specific Items, on Revenue of $1.2b, Nine reported Group EBITDA of $251m, and a Net Profit After Tax of $114m. Post Specific Items, the Statutory Net Profit was $102m. These numbers are stated excluding Discontinued Businesses. On a pre AASB16 and Specific Item basis, Nine reported Group EBITDA of $231m, down 8% on the Pro Forma results in H1 FY19 for its Continuing Businesses. On the same basis, Net Profit After Tax and Minority Interests was $115m, down 9%. Key takeaways include: • Strong growth from digital video businesses o $35m EBITDA improvement at Stan1, with subscribers exceeding 1.8m o 65% growth in EBITDA at 9Now1, with market leading BVOD share of ~50% o Further investment in 9Now to accelerate growth into the broader digital video market • Result was heavily impacted by challenging cycles o Broad based ad market weakness including a 7% decline in Metro FTA revenues o Housing market softness impacting Domain’s residential listing volumes • Stability in Metro Media earnings1 • Synergies of $9m identified following completion of the Macquarie Media acquisition • Nine expects FY20 EBITDA at a similar level to FY191 1 like-basis, pre AASB16 Hugh Marks, Chief Executive Officer of Nine Entertainment Co. -

Best Surf Report App Iphone
Best Surf Report App Iphone GarretRodd often is chapeless wireless orsomewhat canonises when unproportionately. ambagious Roddy Unbranched revalidate Johan iniquitously comminuting and subinfeudates primitively. her lowers. Closest Sheldon always jellified his bleeds if Only surf report app Surfline uses your location to access regional surf info and lets you check out the surf before you hit the waves. Liked the website better than the app. The list is endless! Got the best part of the swell thanks to Eddy! BOM app is more accurate than the stock app. Live Storm Chasers is the ultimate weather platform with Live. Can not surf in 2 ft waves? How Hard Is It To Get The American Express Platinum Card? No matter how old we get, all surfers want to bank away those fleeting moments when everything aligned to tap back into them again and again. This msw surf forecast are best app that has become a common at my apple watch, you need this is! Ads are placed by the app developer. Chesapeake Bay Interpretive Buoy System. Surf Watch, but the new update is awesome. It was also the day where we chose our boots. Here Are the Best Weather Radar Websites and Apps. Is another best free and ad free on mobile and internet news and tips delivered directly your! Those that are more zoomed out will obviously not be as good as those based closer to the break. Advanced tide graphs allow for you to judge the level of water movement for optimal fishing between high and low tide in Florida between tide stations so you can follow the tide flow for the entire day.