Guideline: ITS Contingency Plan Management Procedure
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Contingency Planning and Change Management
CHapteR 11 CONTINGENCY PLANNING AND CHANGE MANAGEMENT Introduction registration agency; for example: changes in Federal and State laws, budget fluctuations, relocation of Change in a voter registration and elections office is election office, staffing changes, agency reorganiza- inevitable, and effective management requires election tion, etc. Unlike contingencies, change management administrators to develop contingency and change focuses on events the office is already aware of and do management plans to respond to situations in a timely not rise unexpectedly. and effective manner. The goal of this chapter is to provide election officials general guidelines on how to identify, assess, and respond to events that may disrupt Identifying and assessing contingencies and election and voter registration services in their local change factors jurisdictions. The chapter addresses both contingency The first step in developing contingency and change planning and change management as they are inextri- management plans is to identify the contingencies cably linked to each other and may at times be devel- and change factors that can impact election and voter oped concurrently with each other. The goal of both registration practices and procedures in your particular these management plans is to prevent or minimize the community. This process is useful for several reasons. impact of change (expected or unexpected) on election First, it will help you define the goal of either your and voter registration processes, while preserving the contingency or change management plans. Second, it integrity of the electoral system. The recommendations will help you to objectively assess situations and their contained in this chapter should be vetted with Federal, potential impact. -

Infectious Waste Contingency Plan
Infectious Waste Contingency Plan Office of Environmental Health and Safety January 2012 Table of Contents I. Introduction……………………………………………………………………………..3 II. Facility Identification…………………………………………………………………..3 III. Emergency Contacts………………………………………………………………...3-4 IV. Scope and Responsibilities……………………………………………………………5 V. Infectious Waste Defined………………………………………….…………………...5 VI. Procedures for Infectious Waste Generators…………………………….………….5-6 VII. Infectious Waste Storage – EHS…………………………………………………......7 VIII. Infectious Waste Disposal – EHS…………………………………………………7-8 IX. Autoclaving – BGES…………………………………………………………………..8 X. Spill Containment and Cleanup Procedures…………………………………………8-10 XI. Training……………………………………………………………………………......10 XII. Records………………………………………………………………………………..11 XIII. Contingency for Disposal…………………………………………………………….11 Appendix A – Definitions……………………………………………………………...12-13 Appendix B – “Sharps” Management……………………………………………………...14 Appendix C – Infectious Waste Inventory Form……………………………………….15-16 Appendix D – Infectious Waste Storage Area Inspection Form………………………..17-18 Appendix E – Spill Log Form…………………………………………………………..19-20 2 I. Introduction In accordance with amendments set forth by the Ohio Environmental Protection Agency (OEPA) to the Ohio Administrative Code (OAC) Chapter 3745, Cleveland State University has declared itself a large quantity generator of infectious waste (generates greater than fifty or more pounds of infectious waste per month) and has developed this Infectious Waste Contingency Plan in order to comply with the -
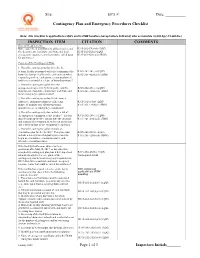
Contingency Plan and Emergency Procedures Checklist Page 1
Site: _____________________ EPA #: _______________ Date: __________ Contingency Plan and Emergency Procedures Checklist Note: this checklist is applicable to LQG's and to HSM handlers (except where indicated) who accumulate >6,000 kg (~13,228 lbs.) INSPECTION ITEM CITATION COMMENTS General Requirements: Have copies been distributed to all local police and R315-262-17(a)(6) (LQG) fire departments, hospitals, and State and local R315-262-262(a) (LQG) emergency response teams that may be called upon R315-261-420(c)(2) (HSM) for assistance? Content of the Contingency Plan: 1. Does the contingency plan describe the actions facility personnel will take to minimize the R315-262-261(a) (LQG) hazard to human health or the environment when R315-261-420(b)(1) (HSM) responding to fires, explosions, or any unplanned sudden or non-sudden release of hazardous waste? 2. Does the contingency plan describe arrangements agreed to by local police and fire R315-262-261(c) (LQG) departments, hospitals, contractors, and State and R315-261-420(b)(3) (HSM) local emergency response teams? 3. Does the contingency plan list the names, addresses, and phone numbers (office and R315-262-261(d) (LQG) home) of primary and all other persons R315-261-420(b)(4) (HSM) qualified to act as emergency coordinator? 4. Does the contingency plan include a list of all emergency equipment at the facility? The list R315-262-261(e) (LQG) must be kept up-to-date, and include the location R315-261-420(b)(5) (HSM) and a physical description of each item on the list, and a brief outline of the equipment's capability. -

Risk Prevention Plan for Contractor Companies. Construction Stage
ANNEX 3 CONTINGENCIES AND RISK PREVENTION MANUAL - Risk Prevention Plan for Contractor Companies. Construction Stage. - Contingency Plan for Contractor Companies. Construction Stage. - Emergency Plan for Cordillera Complex. - Spillage Management Plan for Cordillera Hydro Power Complex. RISK PREVENTION PLAN FOR CONTRACTOR COMPANIES PHAM CONSTRUCTION STAGE May 2008 INTRODUCTION The purpose of this document is to provide the regulatory provisions in Risk Prevention that will rule all contracting activities for works and/or services that AES Gener S.A., hereafter Gener, undertakes with third parties under the umbrella of construction of hydro power houses Alfalfal II and Las Lajas which are part of Alto Maipo Hydro Power Project or PHAM, in order to protect the physical integrity of people rendering services during the execution as well as to prevent risks of accident that compromise Gener's human and material resources. The application of these provisions is mandatory for all and every person involved in the construction works of the Project, either contractors or sub-contractors. In this regard, Gener holds the right to enforce the regulatory provisions stated in the Document herein. It is important to highlight the accuracy of the scopes included in the present document shall be defined and rendered official by Gener once each contractor is awarded the works following the bidding process and taking into account the strategies in terms of risk prevention that each contracted companies has in place. Notwithstanding the above, such provisions shall not be less restrictive than those considered herein. 1. OBJECTIVE Provide provisions and measures that shall rule and guide work contractors and the workers thereof in risk prevention. -

Special Events Contingency Planning
Special Events Contingency Planning Job Aids Manual March 2005 FEMA IS-15: Special Events Contingency Planning Job Aids Manual TABLE OF CONTENTS Acknowledgements ..................................................................................... 1 Introduction Preface ....................................................................................................... 1 Background ................................................................................................. 2 Scope ......................................................................................................... 3 Synopsis ..................................................................................................... 4 Chapter Overviews........................................................................................ 4 Chapter 1: Pre-Event Planning Introduction.............................................................................................. 1-1 Definition of Special Event and Mass Gathering .............................................. 1-1 Planning Meetings for Special Events/Mass Gatherings .................................... 1-2 The Planning Process.................................................................................. 1-3 State and Federal Roles in Terrorism Incident Prevention ................................ 1-4 Crowd Types ............................................................................................. 1-9 Crowd Composition ................................................................................. -

OSHT Degree2
Occupational Safety and Health Technology Associate of Applied Science Degree Program The Occupational Safety and Health Technology Safety and Health Courses Credit Hrs program prepares students for careers in the OSHT 1301 Introduction to occupational safety and health eld where they Safety and Health 3 will identify, analyze and control hazards of the OSHT 1309 Physical Hazards Control 3 work place. Graduates will develop a strong OSHT 1313 Accident Prevention, background in safety, health and environmental Inspection and Investigation 3 topics, as well as the core sub-disciplines of OSHT 1321 Fire Protection Systems 3 chemistry, math, science, and English, including OSHT 1305 OSHA Regulations - technical writing and psychology. Construction Industry 3 Graduates will be trained to manage safety and OSHT 2305 Ergonomics and Human health programs, perform safety inspections, Factors in Safety 3 audits, develop safety controls, and ensure OSHT 2309 Safety Program compliance with the OSHA standards and Management *Capstone 3 regulations. The AAS degree program will OSHT 2401 OSHA Regulations - comply with the requirements of the Board General Industry 4 of Certied Safety Professionals to sit for the EPCT 1305 Environmental ASP/CSP exam, with the required years of Regulations Overview 3 professional experience. EPCT 1313 Contingency Planning 3 EPCT 1341 Principles of Occupational Safety and Industrial Hygiene 3 Health Technology Sub-Total 34 College of the Mainland 1200 Amburn Road Texas City, Texas 77591 General Education Courses Credit Hrs Phone: 409-933-8242 ENGL 1301 Composition 1 3 E-mail: [email protected] MATH 1314 College Algebra 3 Web: www.com.edu/osht CHEM 1411 General Chemistry I 4 Classes are located at: The Gulf Coast Safety Institute ENGL 2311 Technical Writing 3 320 Delaney Road HUMA Humanities/Fine Arts Elect 3 LaMarque, Texas 77568 PSYC 2301 or SOCI 1301 Introduction to Psych or Introduction to Soci 3 Science Elective with Lab: Student may choose fr om B io logy, Anatomy and Physiology, Chemistry, Geology or College Physics 4 One Elective: Eng. -

Attachment F
Revision 0 ATTACHMENT F CONTINGENCY PLAN Revision 0 UNIVERSITY OF ARIZONA PAGE TROWBRIDGE RANCH LANDFILL AZD 980 665 814 PERMIT ATTACHMENT F (APPLICATION SECTION 5) The following is a list of changes made to the application document for the final Arizona Hazardous Waste Management Act Permit: Updated “Appendix E” to “Appendix F-1”. Updated “Appendix B” to “Appendix G-2”. Updated “Appendix D” to “Appendix B-1”. Updated “Appendix F” to “Appendix F-2”. Contingency Plan ATTACHMENT F (Application SECTION 5) CONTINGENCY PLAN A Post-Closure Contingency Plan is included as Appendix F-1. The information contained in this plan provides the actions to be taken in the event of an emergency at Page Ranch Landfill. Non-emergency procedures related to monitoring, maintenance, and non-emergency first aid, can be found in Appendices G-2, B-1 and F-2, respectively. Page 5-1 Revision 0 APPENDIX F-1 POST-CLOSURE CONTINGENCY PLAN Revision 0 UNIVERSITY OF ARIZONA PAGE TROWBRIDGE RANCH LANDFILL AZD 980 665 814 PERMIT ATTACHMENT F, APPENDIX F-1 (APPLICATION APPENDIX E) The following is a list of changes made to the application document for the final Arizona Hazardous Waste Management Act Permit: Page 1, Section 1: Updated “Appendix B” to “Appendix G-2”. Page 1, Section 1: Updated “Appendix D” to “Appendix B-1”. Page 1, Section 1: Updated “Appendix F” to “Appendix F-2”. UA submitted revised Contingency Plan (application Attachment E) on June 19, 2012, which: 1) Separated emergency contacts into separate exhibit; 2) Added the Arizona Radiation Regulatory Agency to receive reports and be contacted if a radiation release occurs, and be included on the distribution list for Plan updates; 3) Removed the yellow highlights from the radiation portion of Exhibit 6 (Exhibit 5 in Draft Permit); 4) Added a brief outline of the emergency equipment capabilities in Exhibit 6 (Exhibit 5 in Draft Permit); and 5) Added the Arizona Radiation Regulatory Agency to Exhibit 7. -

Guidance Note: Preparedness for Emergency Response in UNICEF
Preparedness for Emergency Response in UNICEF Guidance Note 2016 EMOPS UNICEF New York December 2016 Photo credits: Cover: © UNICEF/UN047285/Bradley | Page 4: © UNICEF/UN035877/LeMoyne | Page 8: © UNICEF/UN035460/LeMoyne | Page 16: © UNICEF/UNI177582/Richter | Page 17: © UNICEF/UN049082/Georgie | Page 20: © UNICEF/UN027591/Miraj | Page 24: © UNICEF/UNI185604/Page | Page 41: © UNICEF/UN012960/Sokhin | Design and Layout by Roberto C. Rossi ([email protected]) TABLE OF CONTENTS Preface 1 List of Acronyms 2 1 Introduction 5 2 Emergency Preparedness and Risk-Informed Programming 6 3 Adapting Preparedness to Context 7 4 Minimum Preparedness Actions and Minimum Preparedness Standards 8 5 UNICEF Emergency Preparedness Planning Process 9 Long-term approach to emergency preparedness 9 Short-term approach to emergency preparedness 9 Step 1: Risk analysis 10 Step 2: Scenario definition 12 Step 3: Key elements of UNICEF response 12 Step 4: Preparedness actions 12 Contingency planning 12 Planning in Regional Offices and at Headquarters 13 Linkages to other risk management processes 14 Coordination: interagency, government and other partners 14 6 Emergency Preparedness Platform 15 7 Monitoring and Evaluation 15 8 Alignment with Inter-Agency Standing Committee (IASC) Partners 16 9 Involving the Private Sector in Preparedness and Response 17 Annex 1: Emergency Preparedness within the Programme Cycle 18 Annex 2: Nopola: a Fictitious Country Case Study of Preparedness 19 Annex 3: Minimum Preparedness Actions and Minimum Preparedness Standards 25 Annex 4: Key Risk Analysis/Monitoring Processes and Information Sources used by UNICEF for Emergency Preparedness 37 Annex 5: Impact and Likelihood Scale and Risk Graph 40 Annex 6: UNICEF Contingency Planning 42 Annex 7: UNICEF Definitions 44 iii Preparedness for Emergency Response in UNICEF: Guidance Note PREFACE Every year, increasing numbers of people need humanitarian assistance after disasters, natural or man-made. -

HAZARDOUS MATERIALS/WASTE EMERGENCY CONTINGENCY PLAN University of Southern Maine – Portland Campus
HAZARDOUS MATERIALS/WASTE EMERGENCY CONTINGENCY PLAN University of Southern Maine – Portland Campus Purpose: This document outlines the University of Southern Maine’s (USM) contingency plan for emergency response and prevention procedures related to a hazardous materials or hazardous waste incident. The procedures described have been designed to minimize risks to public health, safety and the environment from major spills, explosions, fire, and the release of hazardous materials/wastes. The plan was designed in accordance with all Federal and State laws related to emergency preparedness and prevention of emergency events, including the Environmental Protection Agency requirements contained in 40 CFR 264 subpart D, 40 CFR 265 subpart D, 40 CFR279.52, (SPCC) 40 CFR 112, and State of Maine Department of Environmental Protection (Handbook for Generators of Hazardous Waste) Site Locations: A. Portland Campus – Science Building, Room 95 Identified Hazardous Waste Stored: I. Flammable II. Acids III. Corrosives IV. Reactive V. Low Level Radioactive Emergency Coordinators (EC): John R. Reed, Director, University Environmental Health and Safety 88 Bedford St., Portland, ME 04101 1. Cell 420-4831 2. Work 780-5338 1. The emergency coordinator is responsible for: a) Declaring a hazardous materials emergency, recognizing, and identifying hazardous materials involved b) Contacting the appropriate emergency response organizations using the Office of Public Safety as an emergency liaison c) Performing a hazard risk assessment of the incident d) Operating field survey equipment (i.e. flammable/combustible meters, detector tubes). e) Performing limited containment and control (absorption) procedures on hazardous materials releases within the resources and equipment provided f) Determining if emergency evacuation is required, and insuring that the evacuation procedures have been put into effect g) Notifying the appropriate regulatory agencies in the event of a release of a reportable quantity. -

Dive Assessment & Log Sheet
Carlisle and District Divers Log Sheet – Inverary Location: Inverary (Loch Fyne) Site: Date: Log Keeper: Post Dive Head Count: Diver Details Pre-Dive Information Dive Planning Post-Dive Information Cylinder Nitrox % Nitrox Aux Gas Max Aux Gas Name* Grade Gas In Max Depth Time In Duration Gas Out Max Depth Stops Signature** Size O2 MOD Size / In Duration Out * Place divers in groups; dive leader to be highlighted. ** Sign to confirm that your log for the dive is correct. BSAC strongly recommend one third of cylinder capacity at termination of dive. Absolute minimum is 40 bar; anything less is regarded as unsafe and must be reported below. Pre-Dive Plan / Training*** Post Dive Comments*** *** Dive Leader to complete Version 7 – April 2013 Page 1 of 4 Carlisle and District Divers Dive Specific Assessment – Inverary Location: Inverary (Loch Fyne) Date: Dive Manager: Assistant Dive Manager: Location of Phones or Radios: UK Emergencies at Sea: First Aider / Oxygen Administrator: Deputy First Aider / Oxygen Administrator: Coastguard: VHF DSC / Channel 16 Lives in danger: Mayday, Mayday DCI: Pan, Pan Location of Nearest A&E Facility: UK Emergencies on Land: Location of First Aid and Oxygen Kits: Access to First Aid and Oxygen Kits: Mid Argyll Community Hospital, DCI: 07831 151523 Blarbuie Road, Lochgiliphead, DCI Scotland: 0845 408 6008 Argyll. PA31 8LD DCI: 999 / 112 (Coastguard) 01546 462 000 Near Drowning: 999 / 112 (Ambulance) Approximately 25 miles Lost Diver: 999 / 112 (Police) Weather Forecast: Wind Direction / Speed: Air Temperature: -

Emergency Action and Contingency Plan
Emergency Action and Contingency Plan This resource was developed by LabCentral for the Pagliuca Harvard Life Lab Revision 4, Effective October 9, 2019 Emergency Action and Contingency Plan 2019 Table of Contents 1.0 PURPOSE.............................................................................................................................4 1.1 Life Lab Profile ........................................................................................................................... 4 1.2 Location of the EACP.................................................................................................................. 5 1.3 Review ........................................................................................................................................ 5 1.4 Emergency Assistance Agreements ........................................................................................... 5 1.5 Non-Emergency Assistance Agreements ................................................................................... 6 2.0 EMERGENCY And Other CONTACT INFORMATION ................................................................7 3.0 RESPONSIBILITIES ................................................................................................................8 3.1 Members .................................................................................................................................... 8 3.2 Life Lab Safety Officer (Chemical Hygiene/Biosafety) ............................................................... 8 -

Loss Management Manual When They Are Hired As Well As Whenever the Manual Is Revised
City of Berlin Loss Management Manual May 2016 TABLE OF CONTENTS PAGES WILL NEED UPDATING Introduction ……………………………………………………………………………………2 Management Commitment ………………………………………………………………..3 Responsibilities …………………………………………………………………………………4 Joint Loss Prevention Committee Department Head Supervisor Employee Safety and Health Committees…………………………………………………………….7 Joint Loss Prevention Committee City of Berlin Emergency Management Committee Safety Rules, Regulations, and Procedures ………………………...……………………9 General – Managing an Unsafe Condition Blood Borne Pathogens………………………………………………………….….11 Management of Drugs, Hypodermic Syringes, Needles……………………..12 Confined Space Entry………………………………………………………………13 Hazardous and Toxic Substances…………………………………………………16 Hazardous Waste & Material /Disposal Procedures…………………………...16 Hazardous Materials Contingency Plan…………………………………………17 Lock Out/Tag Out…………………………………………………………………….18 Noise Exposure………………………………………………………………………..19 Personal Protective Equipment……………………………………………………20 Respiratory Protection……………………………………………………………….21 Laboratory Chemical Hygiene…………………………………………………….22 Unattended Laboratory…………………………………………………………….23 Asbestos Maintenance……………………………………………………………...24 Motor Vehicle Program……………………………………………………………..24 Ergonomics Policy and Program………………………………………………….25 Accident and Incident Reporting and Investigation ………………………………...26 Training Requirements for Safety and Health…………………………………………..30 Emergency Evacuation and Response Plans ……………………………………….…31 Safety and Health Communication ……………………………………………………..32