Java Bytecode Manipulation Framework
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Web Vmstat Any Distros, Especially Here’S Where Web Vmstat Comes Those Targeted at In
FOSSPICKS Sparkling gems and new releases from the world of FOSSpicks Free and Open Source Software Mike Saunders has spent a decade mining the internet for free software treasures. Here’s the result of his latest haul… Shiny statistics in a browser Web VMStat any distros, especially Here’s where Web VMStat comes those targeted at in. It’s a system monitor that runs Madvanced users, ship an HTTP server, so you can connect with shiny system monitoring tools to it via a web browser and see on the desktop. Conky is one such fancy CSS-driven charts. Before you tool, while GKrellM was all the rage install it, you’ll need to get the in the last decade, and they are websocketd utility, which you can genuinely useful for keeping tabs find at https://github.com/ on your boxes, especially when joewalnes/websocketd. Helpfully, you’re an admin in charge of the developer has made pre- various servers. compiled executables available, so Now, pretty much all major you can just grab the 32-bit or distros include a useful command 64-bit tarball, extract it and there line tool for monitoring system you have it: websocketd. (Of course, Here’s the standard output for vmstat – not very interesting, right? resource usage: vmstat. Enter if you’re especially security vmstat 1 in a terminal window and conscious, you can compile it from copy the aforementioned you’ll see a regularly updating (once its source code.) websocketd into the same place. per second) bunch of statistics, Next, clone the Web VMStat Git Then just enter: showing CPU usage, free RAM, repository (or grab the Zip file and ./run swap usage and so forth. -
20 Linux System Monitoring Tools Every Sysadmin Should Know by Nixcraft on June 27, 2009 · 315 Comments · Last Updated November 6, 2012
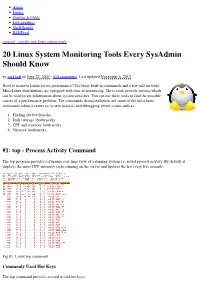
About Forum Howtos & FAQs Low graphics Shell Scripts RSS/Feed nixcraft - insight into linux admin work 20 Linux System Monitoring Tools Every SysAdmin Should Know by nixCraft on June 27, 2009 · 315 comments · Last updated November 6, 2012 Need to monitor Linux server performance? Try these built-in commands and a few add-on tools. Most Linux distributions are equipped with tons of monitoring. These tools provide metrics which can be used to get information about system activities. You can use these tools to find the possible causes of a performance problem. The commands discussed below are some of the most basic commands when it comes to system analysis and debugging server issues such as: 1. Finding out bottlenecks. 2. Disk (storage) bottlenecks. 3. CPU and memory bottlenecks. 4. Network bottlenecks. #1: top - Process Activity Command The top program provides a dynamic real-time view of a running system i.e. actual process activity. By default, it displays the most CPU-intensive tasks running on the server and updates the list every five seconds. Fig.01: Linux top command Commonly Used Hot Keys The top command provides several useful hot keys: Hot Usage Key t Displays summary information off and on. m Displays memory information off and on. Sorts the display by top consumers of various system resources. Useful for quick identification of performance- A hungry tasks on a system. f Enters an interactive configuration screen for top. Helpful for setting up top for a specific task. o Enables you to interactively select the ordering within top. r Issues renice command. -

MANNING Greenwich (74° W
Object Oriented Perl Object Oriented Perl DAMIAN CONWAY MANNING Greenwich (74° w. long.) For electronic browsing and ordering of this and other Manning books, visit http://www.manning.com. The publisher offers discounts on this book when ordered in quantity. For more information, please contact: Special Sales Department Manning Publications Co. 32 Lafayette Place Fax: (203) 661-9018 Greenwich, CT 06830 email: [email protected] ©2000 by Manning Publications Co. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by means electronic, mechanical, photocopying, or otherwise, without prior written permission of the publisher. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in the book, and Manning Publications was aware of a trademark claim, the designations have been printed in initial caps or all caps. Recognizing the importance of preserving what has been written, it is Manning’s policy to have the books we publish printed on acid-free paper, and we exert our best efforts to that end. Library of Congress Cataloging-in-Publication Data Conway, Damian, 1964- Object oriented Perl / Damian Conway. p. cm. includes bibliographical references. ISBN 1-884777-79-1 (alk. paper) 1. Object-oriented programming (Computer science) 2. Perl (Computer program language) I. Title. QA76.64.C639 1999 005.13'3--dc21 99-27793 CIP Manning Publications Co. Copyeditor: Adrianne Harun 32 Lafayette -

IBM Unica Campaign: Administrator's Guide to Remove a Dimension Hierarchy
IBM Unica Campaign Version 8 Release 6 February, 2013 Administrator's Guide Note Before using this information and the product it supports, read the information in “Notices” on page 385. This edition applies to version 8, release 6, modification 0 of IBM Unica Campaign and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright IBM Corporation 1998, 2013. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Chapter 1. Administration in IBM Unica To view system table contents .......27 Campaign ..............1 Working with user tables ..........28 Campaign-related administrative tasks in IBM Unica About working with user tables ......28 Marketing ...............1 Guidelines for mapping user tables .....28 To access data sources from within a flowchart 29 Chapter 2. Managing security in IBM Working with user tables while editing a flowchart ..............29 Unica Campaign ...........3 Working with user tables from the Campaign About security policies ...........3 Settings page .............30 The global security policy .........3 Working with data dictionaries ........39 How Campaign evaluates permissions.....4 To open a data dictionary.........39 Using the Owner and Folder Owner roles . 4 To apply changes to a data dictionary ....40 Guidelines for designing security policies....5 When to use a data dictionary .......40 Security scenarios.............5 Data dictionary syntax..........40 Scenario 1: Company with a single division . 5 To manually create a new data dictionary . 40 Scenario 2: Company with multiple separate Working with table catalogs .........41 divisions...............7 To access table catalogs .........41 Scenario 3: Restricted access within a division . -

Open Source Ethos Guiding Beliefs Or Ideals That Characterize a Community
Open Source Ethos guiding beliefs or ideals that characterize a community Patrick Masson Open Source Initiative [email protected] What is the mission of the conference? …bring smart and creative people together; …inspire and motivate them to create new and amazing things; …with an intimate group of like minded individuals. What is the mission of the conference? …bring smart and creative people together; …inspire and motivate them to create new and amazing things; …with an intimate group of like minded individuals. This is the open source ethos – guiding beliefs, ideals of a community It's a great time to be working with open source 1.5 Million Projects 78% of companies run on open source 64% of companies participate It's a great time to be working with open source 88% expect contributions to grow 66% consider before proprietary <3% Don't use OSS 2015 Future of Open Source Survey Black Duck, Northbridge It's a great time to be working with open source It's a great time to be working with open source It's a great time to be working with open source It's a great time to be working with open source Open-course/Open-source Marc Wathieu CC-BY-NC-SA https://www.flickr.com/photos/marcwathieu/2412755417/ _____ College first Massive Open source Online Course (MOOC) Are you seeing other examples of this Mini-MOOC trend (free, I began but did not finish my first The Gates grantees aren’t the only ones open source courses by a MOOC (Massive Open-Source, startup or organization)? Online Course). -

Katalog Elektronskih Knjiga
KATALOG ELEKTRONSKIH KNJIGA Br Autor Naziv Godina ISBN Str. Porijeklo izdavanja 1 Peter Kent Pay Per Click Search 2006 0-471-74594-3 130 Kupovina Engine Marketing for Dummies 2 Terry Large Access 1 2007 Internet Freeware 3 Kevin Smith Excel Lassons & Tutorials 2004 Internet Freeware 4 Terry Michael Photografy Tutorials 2006 Internet Freeware Janine Peterson Phil Pivnick 5 Jake Ludington Converting Vinyl LPs 2003 Internet Freeware to CD 6 Allen Wyatt Cleaning Windows XP 2004 0-7645-7311-X Poklon for Dummies 7 Peter Kent Sarch Engine Optimization 2006 0-4717-5441-2 Kupovina for Dummies 8 Terry Large Access 2 2007 Internet Freeware 9 Dirk Dupon How to write, create, 2005 Internet Freeware promote and sell E-books on the Internet 10 Chayden Bates eBook Marketing 2000 Internet Freeware Explained 11 Kevin Sinclair How To Choose A 1999 Internet Freeware Homebased Bussines 12 Bob McElwain 101 Newbie-Frendly Tips 2001 Internet Freeware 13 Windows Basics 2004 Poklon 14 Michael Abrash Zen of Graphic 2005 Poklon Programming, 2. izdanje 15 13 Hot Internet 2000 Internet Freeware Moneymaking Methods 16 K. Williams The Complete HTML 1998 Poklon Teacher 17 C. Darwin On the Origin of Species Internet Freeware 2/175 Br Autor Naziv Godina ISBN Str. Porijeklo izdavanja 18 C. Darwin The Variation of Animals Internet Freeware 19 Bruce Eckel Thinking in C++, Vol 1 2000 Internet Freeware 20 Bruce Eckel Thinking in C++, Vol 2 2000 Internet Freeware 21 James Parton Captains of Industry 1890 399 Internet Freeware 22 Bruno R. Preiss Data Structures and 1998 Internet -

Producing Open Source Software How to Run a Successful Free Software Project
Producing Open Source Software How to Run a Successful Free Software Project Karl Fogel Producing Open Source Software: How to Run a Successful Free Software Project by Karl Fogel Copyright © 2005-2018 Karl Fogel, under the CreativeCommons Attribution-ShareAlike (4.0) license. Version: 2.3098 Home site: http://producingoss.com/ Dedication This book is dedicated to two dear friends without whom it would not have been possible: Karen Under- hill and Jim Blandy. i Table of Contents Preface ............................................................................................................................. vi Why Write This Book? ............................................................................................... vi Who Should Read This Book? .................................................................................... vii Sources ................................................................................................................... vii Acknowledgements ................................................................................................... viii For the first edition (2005) ................................................................................ viii For the second edition (2017) ............................................................................... x Disclaimer .............................................................................................................. xiii 1. Introduction ................................................................................................................... -

Performance, Scalability on the Server Side
Performance, Scalability on the Server Side John VanDyk Presented at Des Moines Web Geeks 9/21/2009 Who is this guy? History • Apple // • Macintosh • Windows 3.1- Server 2008R2 • Digital Unix (Tru64) • Linux (primarily RHEL) • FreeBSD Systems Iʼve worked with over the years. Languages • Perl • Userland Frontier™ • Python • Java • Ruby • PHP Languages Iʼve worked with over the years (Userland Frontier™ʼs integrated language is UserTalk™) Open source developer since 2000 Perl/Python/PHP MySQL Apache Linux The LAMP stack. Time to Serve Request Number of Clients Performance vs. scalability. network in network out RAM CPU Storage These are the basic laws of physics. All bottlenecks are caused by one of these four resources. Disk-bound •To o l s •iostat •vmstat Determine if you are disk-bound by measuring throughput. vmstat (BSD) procs memory page disk faults cpu r b w avm fre flt re pi po fr sr tw0 in sy cs us sy id 0 2 0 799M 842M 27 0 0 0 12 0 23 344 2906 1549 1 1 98 3 3 0 869M 789M 5045 0 0 0 406 0 10 1311 17200 5301 12 4 84 3 5 0 923M 794M 5219 0 0 0 5178 0 27 1825 21496 6903 35 8 57 1 2 0 931M 784M 909 0 0 0 146 0 12 955 9157 3570 8 4 88 blocked plenty of RAM, idle processes no swapping CPUs A disk-bound FreeBSD machine. b = blocked for resources fr = pages freed/sec cs = context switches avm = active virtual pages in = interrupts flt = memory page faults sy = system calls per interval vmstat (RHEL5) # vmstat -S M 5 25 procs ---------memory-------- --swap- ---io--- --system- -----cpu------ r b swpd free buff cache si so bi bo in cs us sy id wa st 1 0 0 1301 194 5531 0 0 0 29 1454 2256 24 20 56 0 0 3 0 0 1257 194 5531 0 0 0 40 2087 2336 34 27 39 0 0 2 0 0 1183 194 5531 0 0 0 53 1658 2763 33 28 39 0 0 0 0 0 1344 194 5531 0 0 0 34 1807 2125 29 19 52 0 0 no blocked busy but not processes overloaded CPU in = interrupts/sec cs = context switches/sec wa = time waiting for I/O Solving disk bottlenecks • Separate spindles (logs and databases) • Get rid of atime updates! • Minimize writes • Move temp writes to /dev/shm Overview of what weʼre about to dive into. -

Awk, Perl, Etc
CNAM, spécialité Informatique NSY116- Multimédia & interaction humain-machine (2008-9) Le texte P. Cubaud <[email protected]> 1. Codes, structures (2. Transport, compression, cryptage) 3. Analyse (4. Synthèse) 5. Présentation Bibliographie B. Habert, C. Fabre, F. Isaac De l’écrit au numérique InterEditions, 1998 I.H. Witten, A. Moffat, T.C. Bell Managing gygabytes. Compressing and indexing documents and images Van Nostrand, 1994 Techniques de l’ingénieur série H. section Document numérique (en ligne au CNAM) R. Laufer, D. Scavetta Texte, hypertexte, hypermédia Que-sais-je n°2629 (v2 1995) 1. Codes - Structures Codage des caractères Trois problèmes : • caractère ≠ glyphe • coder ≠ classer • norme ≠ standard Aussi vieux que le télégraphe… et toujours non résolus. 7 bits : American Standard Code for Information Interchange (ASCII, 1967 - puis ISO646 en 1983) 8 bits : ISO-Latin-XXX (ISO 8859-n) Au delà : Unicode (1990, v3 en 2000) et ISO 10646 = Site web unicode: www.unicode.org Une table à garder en attendant… et un outil : iconv MACCROATIAN [numer:~] pcubaud% iconv -l MACROMANIA ANSI_X3.4-1968 ANSI_X3.4-1986 ASCII CP367 IBM367 ISO-IR-6 ISO646-US ISO_646.IRV:1991 US US-ASCII CSASCII MACCYRILLIC UTF-8 MACUKRAINE ISO-10646-UCS-2 UCS-2 CSUNICODE MACGREEK UCS-2BE UNICODE-1-1 UNICODEBIG CSUNICODE11 MACTURKISH UCS-2LE UNICODELITTLE MACHEBREW ISO-10646-UCS-4 UCS-4 CSUCS4 MACARABIC UCS-4BE MACTHAI UCS-4LE HP-ROMAN8 R8 ROMAN8 CSHPROMAN8 UTF-16 NEXTSTEP UTF-16BE ARMSCII-8 UTF-16LE GEORGIAN-ACADEMY UTF-32 GEORGIAN-PS UTF-32BE KOI8-T UTF-32LE MULELAO-1 -

Linux Lunacy V & Perl Whirl
SPEAKERS Linux Lunacy V Nicholas Clark Scott Collins & Perl Whirl ’05 Mark Jason Dominus Andrew Dunstan Running Concurrently brian d foy Jon “maddog” Hall Southwestern Caribbean Andrew Morton OCTOBER 2ND TO 9TH, 2005 Ken Pugh Allison Randal Linux Lunacy V and Perl Whirl ’05 run concurrently. Attendees can mix and match, choosing courses from Randal Schwartz both conferences. Doc Searls Ted Ts’o Larry Wall Michael Warfield DAY PORT ARRIVE DEPART CONFERENCE SESSIONS Sunday, Oct 2 Tampa, Florida — 4:00pm 7:15pm, Bon Voyage Party Monday, Oct 3 Cruising The Caribbean — — 8:30am – 5:00pm Tuesday, Oct 4 Grand Cayman 7:00am 4:00pm 4:00pm – 7:30pm Wednesday, Oct 5 Costa Maya, Mexico 10:00am 6:00pm 6:00pm – 7:30pm Thursday, Oct 6 Cozumel, Mexico 7:00am 6:00pm 6:00pm – 7:30pm Friday, Oct 7 Belize City, Belize 7:30am 4:30pm 4:30pm – 8:00pm Saturday, Oct 8 Cruising The Caribbean — — 8:30am – 5:00pm Sunday, Oct 9 Tampa, Florida 8:00am — Perl Whirl ’05 and Linux Lunacy V Perl Whirl ’05 are running concurrently. Attendees can mix and match, choosing courses Seminars at a Glance from both conferences. You may choose any combination Regular Expression Mastery (half day) Programming with Iterators and Generators of full-, half-, or quarter-day seminars Speaker: Mark Jason Dominus Speaker: Mark Jason Dominus (half day) for a total of two-and-one-half Almost everyone has written a regex that failed Sometimes you’ll write a function that takes too (2.5) days’ worth of sessions. The to match something they wanted it to, or that long to run because it produces too much useful conference fee is $995 and includes matched something they thought it shouldn’t, and information. -

When Geeks Cruise
COMMUNITY Geek Cruise: Linux Lunacy Linux Lunacy, Perl Whirl, MySQL Swell: Open Source technologists on board When Geeks Cruise If you are on one of those huge cruising ships and, instead of middle-aged ladies sipping cocktails, you spot a bunch of T-shirt touting, nerdy looking guys hacking on their notebooks in the lounges, chances are you are witnessing a “Geek Cruise”. BY ULRICH WOLF eil Baumann, of Palo Alto, Cali- and practical tips on application develop- The dedicated Linux track comprised a fornia, has been organizing geek ment – not only for Perl developers but meager spattering of six lectures, and Ncruises since 1999 (http://www. for anyone interested in programming. though there was something to suit geekcruises.com/), Neil always finds everyone’s taste, the whole thing tended enough open source and programming Perl: Present and to lack detail. Ted T’so spent a long time celebrities to hold sessions on Linux, (Distant?) Future talking about the Ext2 and Ext3 file sys- Perl, PHP and other topics dear to geeks. In contrast, Allison Randal’s tutorials on tems, criticizing ReiserFS along the way, Parrot Assembler and Perl6 features were but had very little to say about network Open Source Celebs hardcore. Thank goodness Larry Wall file systems, an increasingly vital topic. on the Med summed up all the major details on Perl6 Developers were treated to a lecture on I was lucky enough to get on board the in a brilliant lecture that was rich with developing shared libraries, and admins first Geek Cruise on the Mediterranean, metaphors and bursting with informa- enjoyed sessions on Samba and hetero- scaring the nerds to death with my tion. -

Linux Performance Tools
Linux Performance Tools Brendan Gregg Senior Performance Architect Performance Engineering Team [email protected] @brendangregg This Tutorial • A tour of many Linux performance tools – To show you what can be done – With guidance for how to do it • This includes objectives, discussion, live demos – See the video of this tutorial Observability Benchmarking Tuning Stac Tuning • Massive AWS EC2 Linux cloud – 10s of thousands of cloud instances • FreeBSD for content delivery – ~33% of US Internet traffic at night • Over 50M subscribers – Recently launched in ANZ • Use Linux server tools as needed – After cloud monitoring (Atlas, etc.) and instance monitoring (Vector) tools Agenda • Methodologies • Tools • Tool Types: – Observability – Benchmarking – Tuning – Static • Profiling • Tracing Methodologies Methodologies • Objectives: – Recognize the Streetlight Anti-Method – Perform the Workload Characterization Method – Perform the USE Method – Learn how to start with the questions, before using tools – Be aware of other methodologies My system is slow… DEMO & DISCUSSION Methodologies • There are dozens of performance tools for Linux – Packages: sysstat, procps, coreutils, … – Commercial products • Methodologies can provide guidance for choosing and using tools effectively • A starting point, a process, and an ending point An#-Methodologies • The lack of a deliberate methodology… Street Light An<-Method 1. Pick observability tools that are: – Familiar – Found on the Internet – Found at random 2. Run tools 3. Look for obvious issues Drunk Man An<-Method • Tune things at random until the problem goes away Blame Someone Else An<-Method 1. Find a system or environment component you are not responsible for 2. Hypothesize that the issue is with that component 3. Redirect the issue to the responsible team 4.