Media Access Control Spoofing Techniques and Its Counter Measures Mrs
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Final Report
Augment Spoofer Project to Improve Remediation Efforts (ASPIRE) Final Report Dr. Kimberly Claffy and Dr. Matthew Luckie September 21, 2020 Table of Contents A Executive Summary 2 B Problem: Long-standing vulnerability that threatens U.S. critical infrastructure 3 C Technical Approach 3 D Development Deliverables 6 D.1 Extend visibility capabilities to infrastructure behindNATs............. 6 D.2 SupportforAS-levelopt-innotificationsystem . ............ 7 D.3 Automated monthly reports to regional operator mailing lists............ 7 D.4 Maintainspooferoperations . ...... 8 E Analysis of Remediation Efforts 10 E.1 Impactofprivatenotificationsonremediation . ............ 10 E.2 Impact of public (“name-and-shame”) notifications . ............. 10 F Technology Transition and Commercialization 12 F.1 Commercializationopportunities . ......... 12 F.2 Expansiontoothermeasurementplatforms . ......... 12 G Overcoming misaligned incentives to deploy SAV 12 G.1 Impactofexogenousinterventions . ........ 13 G.2 Liability,insurance,andindustrystandards . ............. 13 G.3 Regulatingtransparency . ..... 14 G.4 Regulatinggovernmentprocurement . ........ 14 G.5 Stickydefaults: vendorSAVresponsibility . ............ 15 H Deliverables 17 A Executive Summary 1. Performer: University of California, San Diego (UCSD) & University of Waikato, NZ 2. Award: DHS S&T contract 140D7018C0010. 3. Period of Performance: 1 Sept 2018 - 19 Sept 2020. Despite source IP address spoofing being a known vulnerability – arguably the greatest archi- tectural vulnerability in the TCP/IP protocol suite as designed – for close to 30 years, and despite many efforts to shed light on the problem, spoofing remains a viable attack method for redirection, amplification, and anonymity. While some application-layer patches can mitigate these attacks, attackers continuously search for new vectors. To defeat DDoS attacks requires operators to en- sure their networks filter packets with spoofed source IP addresses, a best current practice (BCP) known as source address validation (SAV). -

Introduction to Spanning Tree Protocol by George Thomas, Contemporary Controls
Volume6•Issue5 SEPTEMBER–OCTOBER 2005 © 2005 Contemporary Control Systems, Inc. Introduction to Spanning Tree Protocol By George Thomas, Contemporary Controls Introduction powered and its memory cleared (Bridge 2 will be added later). In an industrial automation application that relies heavily Station 1 sends a message to on the health of the Ethernet network that attaches all the station 11 followed by Station 2 controllers and computers together, a concern exists about sending a message to Station 11. what would happen if the network fails? Since cable failure is These messages will traverse the the most likely mishap, cable redundancy is suggested by bridge from one LAN to the configuring the network in either a ring or by carrying parallel other. This process is called branches. If one of the segments is lost, then communication “relaying” or “forwarding.” The will continue down a parallel path or around the unbroken database in the bridge will note portion of the ring. The problem with these approaches is the source addresses of Stations that Ethernet supports neither of these topologies without 1 and 2 as arriving on Port A. This special equipment. However, this issue is addressed in an process is called “learning.” When IEEE standard numbered 802.1D that covers bridges, and in Station 11 responds to either this standard the concept of the Spanning Tree Protocol Station 1 or 2, the database will (STP) is introduced. note that Station 11 is on Port B. IEEE 802.1D If Station 1 sends a message to Figure 1. The addition of Station 2, the bridge will do ANSI/IEEE Std 802.1D, 1998 edition addresses the Bridge 2 creates a loop. -
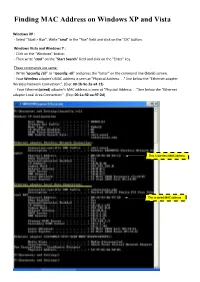
Finding MAC Address on Windows XP and Vista
Finding MAC Address on Windows XP and Vista Windows XP : - Select "Start > Run". Write "cmd" in the "Run" field and click on the "OK" button. Windows Vista and Windows 7 : - Click on the "Windows" button. - Then write "cmd" on the "Start Search" field and click on the "Enter" key. These commands are same: - Write "ipconfig /all" or "ipconfig -all" and press the "Enter" on the command line (blank) screen. - Your Wireless adapter’s MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Wireless Network Connection:”. (Exp: 00-1b-9e-2a-a4-13) - Your Ethernet(wired) adapter's MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Local Area Connection:”. (Exp: 00-1a-92-aa-97-2d) This is wireless MAC address This is wired MAC address Finding MAC Address on Linux root@test:/ > ifconfig –a eth0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:85 <----- This is wired MAC address inet addr:10.92.52.10 Bcast:10.92.255.255 Mask:255.255.248.0 inet6 addr: fe80::1:2ae:9a85/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a85/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 wlan0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:95 <----- This is wireless MAC address inet addr:10.80.2.94 Bcast:10.80.255.255 Mask:255.255.252.0 inet6 addr: fe80::1:2ae:9a95/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a95/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 Finding MAC Address on Macintosh OS 10.1 - 10.4 Please note: Wired and Wireless MAC addresses are different. -

Ipv6 Addresses
56982_CH04II 12/12/97 3:34 PM Page 57 CHAPTER 44 IPv6 Addresses As we already saw in Chapter 1 (Section 1.2.1), the main innovation of IPv6 addresses lies in their size: 128 bits! With 128 bits, 2128 addresses are available, which is ap- proximately 1038 addresses or, more exactly, 340.282.366.920.938.463.463.374.607.431.768.211.456 addresses1. If we estimate that the earth’s surface is 511.263.971.197.990 square meters, the result is that 655.570.793.348.866.943.898.599 IPv6 addresses will be available for each square meter of earth’s surface—a number that would be sufficient considering future colo- nization of other celestial bodies! On this subject, we suggest that people seeking good hu- mor read RFC 1607, “A View From The 21st Century,” 2 which presents a “retrospective” analysis written between 2020 and 2023 on choices made by the IPv6 protocol de- signers. 56982_CH04II 12/12/97 3:34 PM Page 58 58 Chapter Four 4.1 The Addressing Space IPv6 designers decided to subdivide the IPv6 addressing space on the ba- sis of the value assumed by leading bits in the address; the variable-length field comprising these leading bits is called the Format Prefix (FP)3. The allocation scheme adopted is shown in Table 4-1. Table 4-1 Allocation Prefix (binary) Fraction of Address Space Allocation of the Reserved 0000 0000 1/256 IPv6 addressing space Unassigned 0000 0001 1/256 Reserved for NSAP 0000 001 1/128 addresses Reserved for IPX 0000 010 1/128 addresses Unassigned 0000 011 1/128 Unassigned 0000 1 1/32 Unassigned 0001 1/16 Aggregatable global 001 -

Attacking the Spanning Tree Protocol
C H A P T E R 3 Attacking the Spanning Tree Protocol Radia Perlman, a distinguished engineer at Sun Microsystems, named as one of the 20 most influential people in the industry in the 25th anniversary issue of Data Communications magazine and the original inventor of the 802.1D spanning-tree specification recently had a few words to say about the protocol: “It’s time to redo (one of the Internet’s most widely used technologies) in a way that is more robust and gives more efficient paths.”1 Introducing Spanning Tree Protocol Chapter 2, “Defeating a Learning Bridge’s Forwarding Process,” explained how Ethernet switches build their forwarding tables by learning source MAC addresses from data traffic. When an Ethernet frame arrives on a switch port in VLAN X with a destination MAC address for which there is no entry in the forwarding table, the switch floods the frame. That is, it sends a copy of the frame to every single port in VLAN X (except the port that originally received the frame). Although this is perfectly fine in a single-switch environment, interesting side effects are observed in multiswitch topologies, as Figure 3-1 shows. The figure represents a simple network composed of two LAN switches interconnected by two Ethernet links. 44 Chapter 3: Attacking the Spanning Tree Protocol Figure 3-1 Basic Network Setup MAC-address 0000.0000.000A 0/1 A B All Interfaces Are Switch 1 in VLAN 5 Link Y Link X Switch 2 0/2 MAC-address 0000.0000.000B In the next steps, MAC addresses are conveniently shortened to a single-letter format for clarity. -

Firewalls and Vpns
Firewalls and VPNs Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 [email protected] Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse571-17/ Washington University in St. Louis http://www.cse.wustl.edu/~jain/cse571-17/ ©2017 Raj Jain 23-1 Overview 1. What is a Firewall? 2. Types of Firewalls 3. Proxy Servers 4. Firewall Location and Configuration 5. Virtual Private Networks These slides are based on Lawrie Brown’s slides supplied with William Stalling’s th book “Cryptography and Network Security: Principles and Practice,” 7 Ed, 2017. Washington University in St. Louis http://www.cse.wustl.edu/~jain/cse571-17/ ©2017 Raj Jain 23-2 What is a Firewall? Interconnects networks with differing trust Only authorized traffic is allowed Auditing and controlling access Can implement alarms for abnormal behavior Provides network address translation (NAT) and usage monitoring Implements VPNs Washington University in St. Louis http://www.cse.wustl.edu/~jain/cse571-17/ ©2017 Raj Jain 23-3 Firewall Limitations Cannot protect from attacks bypassing it E.g., sneaker net, utility modems, trusted organisations, trusted services (e.g., SSL/SSH) Cannot protect against internal threats E.g., disgruntled or colluding employees Cannot protect against access via Wireless LAN If improperly secured against external use, e.g., personal hot spots Cannot protect against malware imported via laptops, PDAs, and storage infected outside Washington University in St. Louis http://www.cse.wustl.edu/~jain/cse571-17/ ©2017 Raj Jain 23-4 Firewalls – Packet Filters Examine each IP packet (no context) and permit or deny according to rules Washington University in St. -
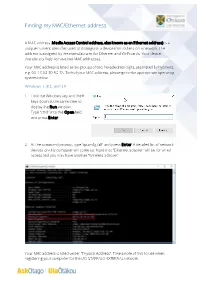
Finding My MAC/Ethernet Address
Finding my MAC/Ethernet address A MAC address (Media Access Control address, also known as an Ethernet address) is a unique numeric identifier used to distinguish a device from others on a network. The address is assigned by the manufacturer for Ethernet and Wi-Fi cards. Your device therefore is likely to have two MAC addresses. Your MAC address is listed as six groups of two hexadecimal digits, separated by hyphens, e.g. 00-13-02-80-92-7A. To find your MAC address, please go to the appropriate operating system below. Windows 7, 8.1, and 10 1. Hold the Windows key and the R keys down at the same time to display the Run window. Type "cmd" into the Open field and press Enter. 2. At the command prompt, type "ipconfig /all" and press Enter. A detailed list of network devices on this computer will come up. Note that "Ethernet adapter" will be for wired access and you may have another "Wireless adapter". Your MAC address is listed under "Physical Address". Take a note of this to use when registering your computer for the UO-STAFF/UO-EXTERNAL network. Mac OS X 1. From the Apple drop-down menu open System Preferences and click on Network. 2. If you want to register for wired access, select Ethernet from the list on the left. 3. Click the Advanced… button and select the Hardware tab to see the MAC address for your Ethernet card. 4. If you need to register for wireless access, click Cancel then select Wi-Fi from the list on the left. -

1.2. OSI Model
1.2. OSI Model The OSI model classifies and organizes the tasks that hosts perform to prepare data for transport across the network. You should be familiar with the OSI model because it is the most widely used method for understanding and talking about network communications. However, remember that it is only a theoretical model that defines standards for programmers and network administrators, not a model of actual physical layers. Using the OSI model to discuss networking concepts has the following advantages: Provides a common language or reference point between network professionals Divides networking tasks into logical layers for easier comprehension Allows specialization of features at different levels Aids in troubleshooting Promotes standards interoperability between networks and devices Provides modularity in networking features (developers can change features without changing the entire approach) However, you must remember the following limitations of the OSI model: OSI layers are theoretical and do not actually perform real functions. Industry implementations rarely have a layer‐to‐layer correspondence with the OSI layers. Different protocols within the stack perform different functions that help send or receive the overall message. A particular protocol implementation may not represent every OSI layer (or may spread across multiple layers). To help remember the layer names of the OSI model, try the following mnemonic devices: Mnemonic Mnemonic Layer Name (Bottom to top) (Top to bottom) Layer 7 Application Away All Layer 6 Presentation Pizza People Layer 5 Session Sausage Seem Layer 4 Transport Throw To Layer 3 Network Not Need Layer 2 Data Link Do Data Layer 1 Physical Please Processing Have some fun and come up with your own mnemonic for the OSI model, but stick to just one so you don't get confused. -

Anti Spoofing
Anti-Spoofing What is Spoofing? In simple terms, A technique used to gain unauthorized access to computers, whereby the intruder sends messages to a computer with an IP address indicating that the message is coming from a trusted host. Types Of Spoofing Attacks IP Address ARP DNS Spoofing Spoofing Spoofing IP Address Spoofing Attacks • IP address spoofing is one of the most frequently used spoofing attack methods. • An attacker sends IP packets from a false (or “spoofed”) source address in order to disguise itself. ARP Spoofing Attacks • ARP is short for Address Resolution Protocol, a protocol that is used to resolve IP addresses to MAC (Media Access Control) addresses for transmitting data. • In this attack, a malicious party sends spoofed ARP messages across a local area network in order to link the attacker’s MAC address with the IP address of a legitimate member of the network. • ARP spoofing only works on local area networks that use the Address Resolution Protocol. DNS Server Spoofing Attacks • The Domain Name System (DNS) is a system that associates domain names with IP addresses. • In a DNS server spoofing attack, a malicious party modifies the DNS server in order to reroute a specific domain name to a different IP address. • In such cases, the new IP address will be for a server that is actually controlled by the attacker and contains files infected with malware. • DNS server spoofing attacks are often used to spread computer worms and viruses. Anti-Spoofing Antispoofing is a technique for identifying and dropping packets that have a false source address. -

High-Speed Internet Connection Guide Welcome
High-Speed Internet Connection Guide Welcome Welcome to Suddenlink High-Speed Internet Thank you for choosing Suddenlink as your source for quality home entertainment and communications! There is so much to enjoy with Suddenlink High-Speed Internet including: + Easy self-installation + WiFi@Home availability + Easy access to your Email + Free access to Watch ESPN This user guide will help you get up and running in an instant. If you have any other questions about your service please visit help.suddenlink.com or contact our 24/7 technical support. Don’t forget to register online for a Suddenlink account at suddenlink.net for great features and access to email, billing statements, Suddenlink2GO® and more! 1 Table of Contents Connecting Your High Speed Internet Connecting Your High-Speed Internet Your Suddenlink Self-Install Kit includes Suddenlink Self-Install Kit ..................................................................................... 3 Connecting your computer to a Suddenlink modem ....................................... 4 the following items: Connecting a wireless router or traditional router to Suddenlink ................. 5 Getting Started Microsoft Windows XP or Higher ......................................................................... 6 Cable Modem Power Adapter Mac OS X ................................................................................................................. 6 Register Your Account Online ................................................................................7 Suddenlink WiFi@Home -

Cases of IP Address Spoofing and Web Spoofing —
3-3 StudiesonCountermeasuresforThwarting SpoofingAttacks—CasesofIPAddress SpoofingandWebSpoofing— MIYAMOTO Daisuke, HAZEYAMA Hiroaki, and KADOBAYASHI Youki This article intends to give case studies for of thwarting spoofing attack. Spoofing is widely used when attackers attempt to increase the success rate of their cybercrimes. In the context of Denial of Service (DoS) attacks, IP address spoofing is employed to camouflage the attackers’ location. In the context of social engineering, Web spoofing is used to persuade victims into giv- ing away personal information. A Web spoofing attacker creates a convincing but false copy of the legitimate enterprises’ web sites. The forged websites are also known as phishing sites. Our research group developed the algorithms, systems, and practices, all of which analyze cybercrimes that employ spoofing techniques. In order to thwart DoS attacks, we show the deployment scenario for IP traceback systems. IP traceback aims to locate attack source, regardless of the spoofed source IP addresses. Unfortunately, IP traceback requires that its sys- tems are widely deployed across the Internet. We argue the practical deployment scenario within Internets of China, Japan, and South Korea. We also develop a detection method for phishing sites. Currently, one of the most important research agenda to counter phishing is improving the accuracy for detecting phishing sites. Our approach, named HumanBoost, aims at improving the detection accuracy by utilizing Web users’ past trust decisions. Based on our subject experiments, we analyze the average detection accuracy of both HumanBoost and CANTINA. Keywords IP spoofing, Web spoofing, Internet emulation, IP traceback, Machine learning 1 Introduction measures. IP traceback aims to locate attack sources, regardless of the spoofed source IP DoS attacks exhaust the resources of addresses. -

Towards Remediating Ddos Attacks
Towards Remediating DDoS Attacks Arturs Lavrenovs NATO CCDCOE, Tallinn, Estonia [email protected] DOI: 10.34190/IWS.21.046 Abstract: The Internet infrastructure has been struggling with distributed denialofservice (DDoS) attacks for more than two decades. This paper reviews aspects of current remediation strategies for reflected amplified DDoS attacks and identifies elements that are insufficiently researched which might be hindering remediation efforts. It identifies additional actors who should be playing a role in these efforts and reviews their incentives and motivation. The issue has long been whether it is possible to remediate abused protocols faster than the protocols get deprecated while devices using them remain functional until the end of their life. It now appears that it is. The Memcache protocol attack capacity was only 319 Mbps in May 2020 but it was 1.7 Tbps only two years previously. Thus it can be considered fully remediated. The paper examines why this was a successful remediation effort and whether it could be applied to other commonly abused protocols by using the reflector capacity measurement methodology. In contrast, the longterm abused DNS protocol has not seen a significant drop in capacity, which is lingering around 27.5 Tbps. Keywords: DDoS attacks, DDoS attack capacity, DDoS attack remediation, reflectors, amplifiers 1. Introduction The first DDoS network attack was two decades ago and was soon followed by reflected amplified DDoS attacks that have been plaguing the Internet ever since. Although the number of reflectors observed by scanning projects has been steadily decreasing, the attack capacity is evergrowing and is setting new records.