551 Symbols A
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Run-Commands-Windows-10.Pdf
Run Commands Windows 10 by Bettertechtips.com Command Action Command Action documents Open Documents Folder devicepairingwizard Device Pairing Wizard videos Open Videos Folder msdt Diagnostics Troubleshooting Wizard downloads Open Downloads Folder tabcal Digitizer Calibration Tool favorites Open Favorites Folder dxdiag DirectX Diagnostic Tool recent Open Recent Folder cleanmgr Disk Cleanup pictures Open Pictures Folder dfrgui Optimie Drive devicepairingwizard Add a new Device diskmgmt.msc Disk Management winver About Windows dialog dpiscaling Display Setting hdwwiz Add Hardware Wizard dccw Display Color Calibration netplwiz User Accounts verifier Driver Verifier Manager azman.msc Authorization Manager utilman Ease of Access Center sdclt Backup and Restore rekeywiz Encryption File System Wizard fsquirt fsquirt eventvwr.msc Event Viewer calc Calculator fxscover Fax Cover Page Editor certmgr.msc Certificates sigverif File Signature Verification systempropertiesperformance Performance Options joy.cpl Game Controllers printui Printer User Interface iexpress IExpress Wizard charmap Character Map iexplore Internet Explorer cttune ClearType text Tuner inetcpl.cpl Internet Properties colorcpl Color Management iscsicpl iSCSI Initiator Configuration Tool cmd Command Prompt lpksetup Language Pack Installer comexp.msc Component Services gpedit.msc Local Group Policy Editor compmgmt.msc Computer Management secpol.msc Local Security Policy: displayswitch Connect to a Projector lusrmgr.msc Local Users and Groups control Control Panel magnify Magnifier -
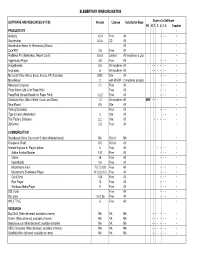
Elementary Windows Matrix
ELEMENTARY WINDOWS MATRIX SOFTWARE AND RESOURCES 8/17/05 Version License Installation Base Access to Software PK K 1 2 3 4 5 Teacher PRODUCTIVITY • Audacity 1.2.4 Free All • • • • Boardmaker 5.3.6 CD All • Boardmaker Addon for Elementary Schools All • Cute PDF 2.6 Free All • FileMaker Pro (Networked, Report Cards) 5.0v3 Limited AV machines & Lab • Hyperstudio Player 4.5 Free All • • • • ImageBlender 2.5 All machines All • • • • • • • • Inspiration 8 All machines All • • • • • • • Microsoft Office (Word, Excel, Access, PP, Publisher) 2000 Site All • • • • MovieMaker 2 with WinXP 2 machines on carts • Netscape Composer 7.1 Free All • • • • Photo Album add-in for PowerPoint Free All • • • • PowerTalk (Screen Reader for Power Point) 1.2.2 Free All • • • • Scholastic Keys (Max's Write, Count, and Show) 1.2 All machines All MW • • • • SmartBoard 9.5 Site All • Talking Calculator Free All • • • • Type to Learn (Networked) 3 Site All • • • Tool Factory Database 2.2 Site All • • • • • • ZipCentral 2.6 Free All • COMMUNICATION Blackboard Online Classroom Builder (Web-delivered) NA District NA • Groupwise Client 6.5 District All • Internet Explorer w. Plugins below: 6 Free All • • • • • Adobe Acrobat Reader 7.07 Free All • • • • Chime v6 Free All • • • • HyperStudio 4.5 Free All Macromedia Flash 7 (7.0.19.0) Free All • • • • Macromedia Shockwave Player 10 (0.0.21.0) Free All • • • • QuickTime 7.04 Free All • • • • Real Player 10 Free All • • • • Windows Media Player 9 Free All • • • • SOL Fonts Free All • • • • Sun Java 1.5.0_06 Free All • • • • -

Document Preparation in Classical Languages
4.2. Operating System Support: Windows tional language is not the same as anging the language of the user interface. If you want all your menus and so forth in German, that is an additional step. Additional Keyboard Resources Tom Gewee has created keyboards for many languages in addition to those provided by OS X. ey can be found at http://homepage. mac.com/thgewecke/tckbs.html. He also has a general “Multilin- gual Mac” page at http://homepage.mac.com/thgewecke/mlingos9. html and a blog at http://m10lmac.blogspot.com/, both of whi are excellent sources of information about using the Mac OS when writ- ing in languages other than English. ird-party Utilities You can use third-party utilities su as the well known PopChar to e out and enter aracters; see http://www.macility.com/ products/popcharx/), where a demo version is available. e Unicode Cheer utility from earthlingso does a few things that Character Palee doesn’t, su as convert Unicode values to HTML entities or help with normalization issues. In some ways it is more convenient than the Character Palee. See http://earthlingsoft. net/UnicodeChecker/index.html. See also the discussion of GreekKeys in §7.3, page 131. Warning for Mac Users! Be careful not to log out while using a keyboard that does not allow you to enter your password in order to get ba in — for example, logging out when a Hebrew or Greek keyboard is in effect if your password requires Latin aracters. SAMPLE4.2 Operating System Support: Windows -key Methods Windows, by contrast, provides two system-wide methods for access- ing non-English aracters, both of them clumsy. -

Copyrighted Material
18_579274 bindex.qxd 2/22/05 7:41 PM Page 312 Index A C accounts call waiting, dial-up account setup, 196 computer administrator, 157 cascade windows, 35 create, 156–157 CD Writing Wizard, 143 delete, 166–167 CDs Internet connection, manual setup, 194–197 backups to, 289 limited user, 157 burn music to, 124–125 name changes, 160–161 copy files to, 140–143 name restrictions, 161 music, Media Player and, 112–115, 120–123 passwords, 162–163 program installation, 18 picture change, 164–165 rip with Media Player, 120–121 sharing and, 155 view files, 135 switch between, 158–159 Character Map, special symbols, 62–63 User Accounts window, 154–155 check boxes, dialog boxes, 26 Welcome screen, 4 circles (Paint), 91 Activate Windows screen, 12–13 click mouse, 8–9 activate Windows XP, 12–13 close button, 23 Add or Remove Programs close windows, 33 installation and, 19 color uninstall programs, 40–41 background, 253 address bar (Internet Explorer), 206 custom, 256–257 Address Book (Outlook Express), 226–227 color box (Paint) addresses, Web, 204, 208–209 color selection, 99 airbrush freehand drawing (Paint), 96 eraser, 101 All Programs menu, 22 introduction, 86 Appearances and Themes, Display Properties and, 250–251 replace color, 101 attachments to e-mail (Outlook Express), 230-231, 240–241 color fills (Paint), 97 audio, play in Media Player, 110 combo boxes automatic updates, 280–281 dialog boxes, 26 item selection, 29 command buttons, dialog boxes, 27 B compressed folders, extract files, 150–151 Background, 252–253 computer administrator account, 157 Backup or Restore Wizard, 286–289 configuration, startup and, 4 Backup program, 286–287 connections, Internet. -
| Independent Consultant Logo
| INDEPENDENT CONSULTANT LOGO PRIMARY LOGO PRIMARY TWO-TONE HEXAGON LOGO The Scentsy Independent Consultant logo can be used by Consultants on their personal printed materials and websites to promote their business. The space between the elements within the logo should not be modified. The logo should always appear upright, with clearance on either side and clearance on the top and bottom equal to the height of the lower case “S” character as it’s used in the sized logo (see example). SPECIAL NOTE: If you need a two colour option for this logo, use Pantone 522 to replace the 80% screen. Pantone 519 Pantone 519 — 80% C 60 M 100 Y 0 K 40 C 45 M 57 Y 23 K 6 #5c305e #8f7290 7/22/15 SCENTSY CONSULTANT STYLE GUIDE 1 | FONT - INDEPENDENT CONSULTANT LOGO TYPE The logo displays the company name in the Scentsy Spirit font, and the accompanying type in Knockout-HTF34-Junior Sumo. No other fonts should be used to alter Scentsy Spirit the look of the Scentsy Independent Consultant logo. 1234567890!@#$%^&*()_=+ ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz Knockout-HTF34-JuniorSumo 1234567890!@#$%^&*()_=+ ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz 7/22/15 SCENTSY CONSULTANT STYLE GUIDE 2 | INDEPENDENT CONSULTANT LOGO SECONDARY LOGO OPTIONS ONE-COLOUR HEXAGON LOGO ONE-COLOUR LOGO + STAR TRIO The following secondary logos may be used on specific Scentsy Family Store materials and by Scentsy Consultants to promote their personal business. The space between the elements within the secondary logos should not be modified. The logos should always appear upright, with clearance on either side and clearance on the top and bottom equal to the height of the lower case “S” character as it’s used in the sized logo. -

A Records, 244–245, 279 -A Switch in Nbtstat, 190 in Netstat, 186 AAS Deployment Package, 710 .Aas Extension, 712 Abstract
22_InsideWin_Index 13/3/03 9:50 AM Page 1269 Index A A records, 244–245, 279 ACEs (Access Control Entries) -a switch access masks in, 568–570 in Nbtstat, 190 command-line tools for, 572–576 in Netstat, 186 for cumulative permissions, 577 AAS deployment package, 710 for deny permissions, 578 .aas extension, 712 inheritance in, 579–580, 725–728 Abstract classes, 299–300 object ownership in, 572 Accelerated Graphics Port (AGP) adapters, 164 viewing and modifying, 570–571 Access Control Entries. See ACEs (Access ACKs in DHCP, 101–102 Control Entries) ACL Editor, 570, 723 Access control lists (ACLs) Advanced view in Active Directory security, 732–734 for inheritance, 578, 581 objects in, 339 for ownership, 572 in security descriptors, 559 for special permissions, 723–724 Access Control Settings window, 728 Edit view, 725–726 Access masks for permissions inheritance, 578 in ACEs, 568–570 blocking, 579 in DSOs, 733 settings for, 581 Access requests in Kerberos, 621 viewings, 582 Access rights. See also Permissions ACLs (access control lists) in Active Directory security in Active Directory security, 732–734 delegation, 729–732 objects in, 339 types of, 724–725 in security descriptors, 559 for group policies, 682 ACPI (Advanced Configuration and Power Access tokens Interface) contents of, 560–561 compatibility of, 23–28, 148–149 local, 559 kernel version for, 135 SIDs in, 559, 561, 581 for PnP,17, 147–149 ACCM (Asynchronous-Control- ACPIEnable option, 149 Character-Map), 1124 Activation Account domain upgrades, 496–498 in IA64, 130 BDC, 494–496 in installation, 49–50 PDC, 490–493 unattended setup scripts for, 95 Account lockout policies Active Directory, 238 in domain design, 429 bulk imports and exports in, 353–356 in password security, 593–594 DNS deployment in, 242–243 Account logons, auditing, 647 DNS integration in, 238–239 Account management, auditing, 511, 648 dynamic updates, 244–245 Accounts in domain migration. -

ISDN Configuration Wizard Charmap
Windows Commands and Shortcuts Commands calc - Calculator cfgwiz32 - ISDN Configuration Wizard charmap - Character Map chkdisk - Repair damaged files cleanmgr - Cleans up hard drives clipbrd - Windows Clipboard viewer cmd - Opens a new Command Window (cmd.exe) control - Displays Control Panel dcomcnfg - DCOM user security debug - Assembly language programming tool defrag - Defragmentation tool drwatson - Records programs crash & snapshots dxdiag - DirectX Diagnostic Utility explorer - Windows Explorer fontview - Graphical font viewer ftp - ftp.exe program hostname - Returns Computer's name ipconfig - Displays IP configuration for all network adapters jview - Microsoft Command-line Loader for Java classes MMC - Microsoft Management Console msconfig - Configuration to edit startup files msinfo32 - Microsoft System Information Utility nbtstat - Displays stats and current connections using NetBios over TCP/IP netstat - Displays all active network connections nslookup - Returns your local DNS server odbcad32 - ODBC Data Source Administrator ping - Sends data to a specified host/IP regedit - registry Editor regsvr32 - register/de-register DLL/OCX/ActiveX regwiz - Reistration wizard sfc /scannow - Sytem File Checker sndrec32 - Sound Recorder sndvol32 - Volume control for soundcard sysedit - Edit system startup files (config.sys, autoexec.bat, win.ini, etc.) systeminfo - display various system information in text console taskmgr - Task manager telnet - Telnet program taskkill - kill processes using command line interface tskill - reduced version -

3 the Windows Files
Chapter 3 The Windows Files A question that technical people often ask about Microsoft Windows is: What does this file do? This chapter describes the purpose for each file in the WINDOWS directory and the SYSTEM subdirectory. For information about how to add to the list of files that are installed automatically with Windows, see “Modifying . INF Files for Custom Installations” in Chapter 2, “The Windows Setup Information Files.” Related information ••• Windows Resource Kit: Chapter 2, “The Windows Setup Information Files”; Chapter 4, “The Windows Initialization Files”; Appendix C, “Windows 3.1 Disks and Files” ••• Glossary terms: code page, EMS , XMS , protected mode, virtual device Contents of this chapter About the Windows Files .................................................................................136 WIN.COM ..........................................................................................................136 The Core Files ..................................................................................................137 Drivers, Fonts, and International Support Files................................................137 Driver Files................................................................................................137 Font Files...................................................................................................144 International Support Files ........................................................................147 MS-DOS Support Components of Windows .....................................................148 -

Programs That Come with Windows by Dick Evans
Programs That Come With Windows by Dick Evans, www.rwevans.com We talk a lot about the cloud and the apps that can be both run in the cloud or the ones that are freely downloaded to our computer. But what about the one that are already on our computer, the one that are included within the Windows package? Whether you have XP, Vista, 7,or 8 there are a number of places you may never have gone. Definitions The term cursor is misused by many today. they call anything that blinks a cursor as well as the mouse pointer as they move it around the screen. ● Cursor ○ Rarely used thick blinking underscore that indicates the location of next character to be type. Appears in the command window and other machine level programs. Not seen by most computer users today. ● Insertion Point ○ A blinking vertical line. The next character to be typed will appear to the right of it. ● Mouse Pointer ○ A arrow that moves around the screen as you move the mouse. In some programs it may may appear as an Ibeam. NOTE: Blue indicates programs found in all OS from XP up Some of the Programs included with Windows XP Start > All Programs > Accessories Calculator Notepad Paint WordPad Start > All Programs > Accessories > Utilities Address Book Character Map Disk Cleanup Disk Defrag 1 Scheduled Tasks System Information System Restore Start > All Programs > Accessories > Accessibility Magnifier Narrator On Screen Keyboard Start > All Programs > Accessories > Entertainment Sound Recorder Windows Movie Maker NOTE: In Windows Vista and above, simply start typing the name of the program you wish to access in the Start Search box and the list of programs will appear above. -

“Pi” Fonts ✵ This Font Package Contains Both Opentype and Postscript Type 1 Versions of Symbol Or “Pi” Fonts
A Word About Symbol or “Pi” Fonts ✵ This font package contains both OpenType and PostScript Type 1 versions of symbol or “pi” fonts. This allows you to use either version of the font, according to the terms of the end user license agreement. Adobe has included both versions of these fonts because some of the characters in the OpenType ver- sions of symbol or “pi” fonts may not be accessible to certain applications due to the way these charac- ters are encoded. Although OpenType fonts from Adobe are compatible with virtually all recent applications, operat- ing systems, and output devices, Adobe’s symbol or “pi” fonts in OpenType format use code points in Unicode that are not part of the standard Windows and Mac basic character sets. (Unicode is a plat- form-independent character encoding standard that maps each character in a font to a unique value that is used to access that character.) As a result, the “pi” and symbol characters in OpenType fonts are not accessible in most applications from normal keyboards. For example, when using the Type 1 version of ITC Zapf Dingbats, you would type the letter “A” to access the “victory hand” character. This is because a standard Type 1 font treats symbolic fonts as if they contained regular alphabetic characters. However, OpenType fonts use Unicode encoding, where these characters have their own unique code points, which do not have corresponding keys on any language’s standard keyboard. In Adobe’s Open- Type “ITC Zapf Dingbats Std” font, for example, the “victory hand” is at the Unicode value U+270C, whereas a capital “A” would be U+0041. -

COPYRIGHTED MATERIAL COPYRIGHTED 36214 TOC.F 7/22/04 10:24 AM Page 2
36214 TOC.F 7/22/04 10:24 AM Page 1 COPYRIGHTED MATERIAL COPYRIGHTED 36214 TOC.F 7/22/04 10:24 AM Page 2 TABLE OF CONTENTS GETTING STARTED 1) WINDOWS XP BASICS 3) WORK WITH FILES 1 Introduction to Windows XP ..................................4 Select Files ............................................................52 What's New in Windows XP ..................................6 Open Files ............................................................54 Parts of the Windows XP Screen ............................8 View Pictures ........................................................56 Using the Mouse......................................................9 Move Files ............................................................58 Using the Start Menu ............................................10 Copy Files..............................................................60 Using Run to Start a Program................................12 Copy Files to a CD ................................................62 Maximize or Minimize a Window ........................14 Copy Pictures from a Digital Camera....................66 Move or Size a Window ........................................16 Scan a Document ..................................................70 Switch Between Windows ....................................18 Rename Files ........................................................74 Arrange Windows..................................................20 Delete Files ............................................................76 Getting Help ........................................................22 -

Rocket Universe NLS Guide
Rocket UniVerse NLS Guide Version 11.2 November 2013 UNV-112-NLS-1 Notices Edition Publication date: November 2013 Book number: UNV-112-NLS-1 Product version: Rocket UniVerse V11.2 Copyright © Rocket Software, Inc. or its affiliates 1985-2014. All Rights Reserved. Trademarks Rocket is a registered trademark of Rocket Software, Inc. For a list of Rocket registered trademarks go to: www.rocketsoftware.com/about/legal. All other products or services mentioned in this document may be covered by the trademarks, service marks, or product names of their respective owners. Examples This information might contain examples of data and reports. The examples include the names of individuals, companies, brands, and products. All of these names are fictitious and any similarity to the names and addresses used by an actual business enterprise is entirely coincidental. License agreement This software and the associated documentation are proprietary and confidential to Rocket Software, Inc., are furnished under license, and may be used and copied only in accordance with the terms of such license. Note: This product may contain encryption technology. Many countries prohibit or restrict the use, import, or export of encryption technologies, and current use, import, and export regulations should be followed when exporting this product. Contact information Website: www.rocketsoftware.com Rocket Software, Inc. Headquarters 77 4th Avenue, Suite 100 Waltham, MA 02451-1468 USA Tel: +1 781 577 4321 Fax: +1 617 630 7100 2 Contacting Global Technical Support If you have current support and maintenance agreements with Rocket Software, you can access the Rocket Customer Portal to report and track a problem, to submit an enhancement request or question, or to find answers in the U2 Knowledgebase.