Smart Electronic Design, Satee 2014
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Сапр Altium Designer 6
СКВОЗНОЕ ПРОЕКТИРОВАНИЕ ФУНКЦИОНАЛЬНЫХ УЗЛОВ РЭС НА ПЕЧАТНЫХ ПЛАТАХ В САПР ALTIUM DESIGNER 6 Санкт-Петербург 2008 Федеральное агентство по образованию Санкт-Петербургский государственный электротехнический университет “ЛЭТИ” ___________________________________________________ В. Ю. СУХОДОЛЬСКИЙ СКВОЗНОЕ ПРОЕКТИРОВАНИЕФУНКЦИОНАЛЬНЫХ УЗЛОВ РЭС НА ПЕЧАТНЫХ ПЛАТАХ В САПР ALTIUM DESIGNER 6 Учебное пособие Часть 1 Санкт-Петербург 2008 УДК 621.____ ББК С Суходольский В.Ю. С___ Сквозное проектирование функциональных узлов РЭС на печат- ных платах в САПР Altium Designer 6. Часть 1.: Учебное пособие. СПб.: Изд-во СПбГЭТУ “ЛЭТИ”, 2008. 148 с. ISBN __________. Дается обзор основных возможностей интегрированной САПР функциональных узлов РЭС на печатных платах Altium Designer 6 и рассматриваются практические приемы работы в процессе выполнения этапов сквозного конструкторского проектирования функциональных узлов РЭС на печатных платах. Предназначено для студентов направ- лений 210200 “Радиотехника” и 210201 “Проектирование и технология электронных средств”, а также может быть полезно инженерам и кон- структорам НИИ и КБ радиоэлектронного профиля. УДК 621.__________________ ББК ______________ Рецензенты: кафедра ТиМ СПбГУТ им. проф. М. А. Бонч-Бруевича; д-р техн. наук, проф. П. П. Бескид (Российский государственный гидроме- теорологический университет). Утверждено редакционно-издательским советом университета в качестве учебного пособия ISBN ВВЕДЕНИЕ Программные продукты САПР австралийской фирмы Protel Technolo- gies, предназначенные для проведения сквозного проектирования функцио- нальных узлов РЭС известны с 90-х гг. На рынок последовательно выходили версии Tango PRO, Protel 99 SE (1999 г.), Protel DXP (2002-2004 гг.). Права на продукты Protel в 2005 г. перешли к фирме Altium Ltd., и в настоящее время версия Protel DXP [1], получившая определенное развитие, вышла на рынок под именем Altium Designer 6. Это современная мощная “сквозная” САПР, превосходящая многие другие по эффективности. -

Integration of a Digital Modulator and a Class-D Amplifier”
Universidad de Málaga Escuela Técnica Superior de Ingeniería de Telecomunicación Programa de Doctorado en Ingeniería de Telecomunicación TESIS DOCTORAL Cost-Effective and Energy-Efficient Techniques for Underwater Acoustic Communication Modems Autor: Muhammad Yousuf Irfan Zia Directores: Pablo Otero Roth Miguel Ángel Luque Nieto Málaga 2020 AUTOR: Muhammad Yousuf Irfan Zia https://orcid.org/0000-0003-4181-5997 EDITA: Publicaciones y Divulgación Científica. Universidad de Málaga Esta obra está bajo una licencia de Creative Commons Reconocimiento-NoComercial- SinObraDerivada 4.0 Internacional: http://creativecommons.org/licenses/by-nc-nd/4.0/legalcode Cualquier parte de esta obra se puede reproducir sin autorización pero con el reconocimiento y atribución de los autores. No se puede hacer uso comercial de la obra y no se puede alterar, transformar o hacer obras derivadas. Esta Tesis Doctoral está depositada en el Repositorio Institucional de la Universidad de Málaga (RIUMA): riuma.uma.es Escuela de Doctorado DECLARACIÓN DE AUTORÍA Y ORIGINALIDAD DE LA TESIS PRESENTADA PARA OBTENER EL TÍTULO DE DOCTOR D./Dña MUHAMMAD YOUSUF IRFAN ZIA Estudiante del programa de doctorado INGENIERÍA DE TELECOMUNICACIÓN de la Universidad de Málaga, autor/a de la tesis, presentada para la obtención del título de doctor por la Universidad de Málaga, titulada: COST-EFFECTIVE AND ENERGY-EFFICIENT TECHNIQUES FOR UNDERWATER ACOUSTIC COMMUNICATION MODEMS Realizada bajo la tutorización de PABLO OTERO ROTH y dirección de PABLO OTERO ROTH y MIGUEL ÁNGEL LUQUE NIETO, DECLARO QUE: La tesis presentada es una obra original que no infringe los derechos de propiedad intelectual ni los derechos de propiedad industrial u otros, conforme al ordenamiento jurídico vigente (Real Decreto Legislativo 1/1996, de 12 de abril, por el que se aprueba el texto refundido de la Ley de Propiedad Intelectual, regularizando, aclarando y armonizando las disposiciones legales vigentes sobre la materia), modificado por la Ley 2/2019, de 1 de marzo. -
Best Free Pcb Cad
Best free pcb cad click here to download Now, before we get into the five best and free PCB design programs, it is to design schematics, you can do no wrong by going with TinyCAD. Do you need a free PCB design software or tool to put in practice the new electronic PCBWeb is a free CAD application for designing and manufacturing. Free PCB CAD Software. This is a comparison of printed circuit board design software. Our criteria for including a PCB CAD program are: There should be a. CircuitMaker is the best free PCB design software by Altium for Open Source Hardware Designers, Hackers, Makers, Students and Hobbyists.Projects · Components · Blog · Hubs. 10 best free pcb designing software open source software download. TinyCAD helps user to draw circuit diagrams and export it as a PCB. Eagle is a very good piece of software. Specifically, the non-free versions scale up to much bigger targets. Meanwhile, you have all of those What is the best free PCB designing application. I always recomment FreePCB, but it lacks one component you Anyone who thinks its the best more than likely hasn't used anything else. The world of PCB CAD software has been very active in recent years – so much so that it's easy to lose track of all the players and products. PCB design: you need a CAD program for your project, but which is best? There are They range from free or inexpensive to high-end/premium. They come. Free CAD Software. Start by downloading our free CAD software. -

Exhibitor Profiles
National Electronics Week 11 – 12 March 2014, Gallagher Convention Centre, Midrand Exhibitor profiles Allan Mckinnon & Associates Deltronics Stand number: B17 Contact: Vangeli Glyptis Stand number: 4-18 Contact: Rob Sterling Tel: 083 309-9785 | [email protected] | Tel: 021 705-7741 | [email protected] | www.deltronics.co.za www.ama-sa.co.za & www.testerion.co.za Deltronics is an innovative contract electronics design company specialising in the design of custom products, embedded systems and Allan McKinnon and associates have been supplying the South African wireless technologies. We focus on fully understanding all aspects of the electronics industry with equipment, consumables and process clients’ requirements. Deltronics is a distributor of Altium Designer, Tasking assistance for over 30 years. Products, JTAG Technologies, JTAG Studio Live and Topor Auto Router. We’re also a registered Altium, Tasking and JTAG Technologies training Asic Design Services facility with certified trainers experienced from entry level to FPGA and Simulation. Deltronics provides product training and will guide you to Stand number: 4-54 Contact: Steve Santamarina successful designs. Visit our stand for competitions and specials on all Tel: 011 315-8316 | [email protected] | www.asic.co.za products listed above. ASIC Design Services distributes electronic components and electronic design automation software and offers design, consulting and training Dizzy Enterprises services. Our product lines include Microsemi (FPGAs, multi-chip Stand number: 4-38 Contact: Dane du Plooy packages (memories, processors), Mentor Graphics (PCB layout, analysis, HDL simulation, wiring harness software), HALO (magnetics), Holt (avionics Tel: 072 435-0005 | [email protected] | www.dizzy.co.za ICs), DownStream Technologies (CAM software) and XJTAG (PCB test The Proteus Design Suite is a schematic capture and PCB design equipment). -

How Foraging Works: Uncertainty Magnifies Food-Seeking Motivation Cambridge.Org/Bbs
Behavioral and Brain Sciences How foraging works: Uncertainty magnifies food-seeking motivation cambridge.org/bbs Patrick Anselme and Onur Güntürkün Target Article Faculty of Psychology, Department of Biopsychology, University of Bochum, D-44801 Bochum, Germany. [email protected], www.bio.psy.rub.de and Faculty of Psychology, Department of Biopsychology, University Cite this article: Anselme P, Güntürkün O. of Bochum, D-44801 Bochum, Germany. [email protected], www.bio.psy.rub.de (2019) How foraging works: Uncertainty magnifies food-seeking motivation. Behavioral Abstract and Brain Sciences 42, e35, 1–59. doi:10.1017/ S0140525X18000948 Food uncertainty has the effect of invigorating food-related responses. Psychologists have noted that mammals and birds respond more to a conditioned stimulus that unreliably pre- Target Article Accepted: 25 February 2018 dicts food delivery, and ecologists have shown that animals (especially small passerines) con- Target Article Manuscript Online: 8 March 2018 sume and/or hoard more food and can get fatter when access to that resource is unpredictable. Commentaries Accepted: 19 September 2018 Are these phenomena related? We think they are. Psychologists have proposed several mech- Keywords: anistic interpretations, while ecologists have suggested a functional interpretation: The effect animal behavior; causal model; dopamine; fat of unpredictability on fat reserves and hoarding behavior is an evolutionary strategy acting reserves; food seeking; functional model; against the risk of starvation when food is in short supply. Both perspectives are complemen- incentive motivation; reward uncertainty tary, and we argue that the psychology of incentive motivational processes can shed some light on the causal mechanisms leading animals to seek and consume more food under uncertainty What is Open Peer Commentary? What in the wild. -

Проектирование Системы Сбора Данных И Управления На Основе Протокола Lora УДК 004.75 DOI: 10.18698/2541-8009-2019-05-472
Проектирование системы сбора данных и управления на основе протокола LoRa УДК 004.75 DOI: 10.18698/2541-8009-2019-05-472 ПРОЕКТИРОВАНИЕ СИСТЕМЫ СБОРА ДАННЫХ И УПРАВЛЕНИЯ НА ОСНОВЕ ПРОТОКОЛА LoRa Н.А. Башлыков [email protected] SPIN-код: 5204-0628 МГТУ им. Н.Э. Баумана, Москва, Российская Федерация Аннотация Ключевые слова Описан процесс разработки приемопередающего Прием и передача данных, беспро- устройства, работающего на основе протокола LoRa водная связь, интернет вещей, (Long Range), который позволяет осуществлять па- Kicad, TopoR, микроконтроллер, кетную передачу данных на большом расстоянии. STM32, LoRa, SX1276 Представлена последовательность разработки ра- диоэлектронного прибора. Обоснован выбор типа разрабатываемой печатной платы, микрокомпонен- тов, технологии их последующего монтажа. Модели- рование устройства проводилось в симбиозе двух систем автоматизированного проектирования: Kicad и TopoR. Сформулированы требования к устройству с учетом особенностей области применения. Актуаль- ность темы определяется перспективностью кон- цепции интернета вещей, поскольку подобным обра- зом можно создавать любые системы сбора данных. Технология LoRa малоразвита в России, что делает перспективным развитие устройств беспроводной Поступила в редакцию 13.03.2019 передачи данных более широкого радиуса действия. © МГТУ им. Н.Э. Баумана, 2019 Введение. Непрерывное развитие информационных технологий требует посто- янного увеличения эффективности обработки и передачи информации. Проры- вом в области связи стала не только передача информации по беспроводному -

Kicad Russiam Team
РЕДАКТОР ПЕЧАТНЫХ ПЛАТ PCBNEW Программное обеспечение со свободной лицензией © Жан-Пьер Шарра (Франция) и KiCAD-сообщество программистов и пользователей 2010 2 Содержание 1 ПРЕДСТАВЛЕНИЕ PCBNEW....................................................................................................4 1.1 АННОТАЦИЯ..................................................................................................................................4 1.2 ПРИНЦИПЫ ВЕДЕНИЯ РАЗРАБОТКИ В PCBNEW................................................................................4 1.3 ДОПОЛНИТЕЛЬНЫЕ ТРЕБОВАНИЯ.......................................................................................................5 2 ВЫЗОВ РЕДАКТОРА PCBNEW.................................................................................................6 2.1 МОДИФИКАЦИЯ ЗАДАННОЙ КОНФИГУРАЦИИ KICAD...........................................................................6 3 ОСНОВНЫЕ ОПЕРАЦИИ В PCBNEW....................................................................................7 3.1 ДОСТУП К ОПЕРАЦИЯМ...................................................................................................................7 3.2 КОМАНДЫ С ИСПОЛЬЗОВАНИЕМ МЫШКИ............................................................................................7 3.3 ВЫБОР РАЗМЕРА СЕТКИ (GRID)........................................................................................................8 3.4 РЕГУЛИРОВАНИЕ РАЗМЕРОВ ОТОБРАЖЕНИЯ (ZOOM).........................................................................9 -
Table of Contents
Table of Contents Preface................................................................................................................................................xvii Volume I Section 1 Fundamental Concepts and Theories Chapter 1 ConvergenceofNanotechnologyandMicrobiology.............................................................................. 1 Mussrat Fayaz Khanday, Annamalai University, India Chapter 2 ABriefInsightintoNanorobotics......................................................................................................... 23 Sanchita Paul, Birla Institute of Technology, India Chapter 3 NanobiotechnologyandTherapeutics................................................................................................... 75 Vikrant, Avvaiyar Government College for Women, India Chapter 4 TheNeedforGlobalStandardsinBiomedicalEthicsandtheQualitativeMethodology.................. 100 F. Sigmund Topor, Keio University, Japan Section 2 Development and Design Methodologies Chapter 5 TextMiningonBigandComplexBiomedicalLiterature.................................................................. 129 Boya Xie, East Carolina University, USA Qin Ding, East Carolina University, USA Di Wu, Drexel University, USA Chapter 6 NucleicAcids-BasedNanotechnology:EngineeringPrincipalsandApplications............................ 155 Robert Penchovsky, Sofia University “St. Kliment Ohridski”, Bulgaria Chapter 7 Modeling,MathematicalandNumericalStudiesofaNewBiventricularModelforArtificialHeart -
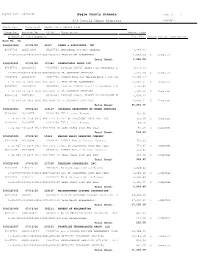
November 2020 Checks
Report Date 12/01/20 Eagle County Schools Page No 1 A/P Detail Check Register FPREG02A Check Key Date Paid Vendor No / Vendor Name Claim No Invoice No PO No Description Amount Paid Account No / Description Acct Amt. Status Status Description Bank No 50 5000325000 07/02/20 44547 LEWAN & ASSOCIATES, INC. 00347589 IN1051034 00105701 DOCUSHARE SUPPORT RENEWAL 1,082.00 1-10-650-00-2840-0432-000-0000-01 TECH MAINT AGREEMENTS 1,082.00 C Computer Total Check: 1,082.00 5000325001 07/02/20 197386 POWERSCHOOL GROUP LLC 00347591 INV220615 00105863 INVOICE 220615 TALENT ED CONTRACTS LI 7,237.20 1-10-640-00-2830-0500-000-0000-70 HR SOFTWARE SERVICES 7,237.20 C Computer 00347592 INV225107 00105702 POWERSCHOOL SIS MAINTENANCE & SIS STA 43,583.54 1-10-650-00-2840-0432-000-0000-01 TECH MAINT AGREEMENTS 43,583.54 C Computer 00347591 INV220615 00105863 INVOICE 220615 TALENT ED RECORDS LICE 7,432.80 1-10-640-00-2830-0500-000-0000-70 HR SOFTWARE SERVICES 7,432.80 C Computer 00347590 INV220617 00105863 INVOICE 220615 TALENT ED APPLICANT TR 6,838.21 1-10-640-00-2830-0500-000-0000-70 HR SOFTWARE SERVICES 6,838.21 C Computer Total Check: 65,091.75 5000325002 07/02/20 129127 COLORADO DEPARTMENT OF HUMAN SERVICES 00347587 ECSD-EVE 00105704 EVE License Renewal 453.90 1-10-627-00-2238-0810-000-3141-01 DIR OF PRESCHOOL DUES AND FEES 453.90 C Computer 00347587 ECSD-EVE 00105704 EVE License Renewal 80.10 1-22-627-00-2238-0810-000-8600-00 HEAD START DUES AND FEES 80.10 C Computer Total Check: 534.00 5000325003 07/02/20 55662 KAPLAN EARLY LEARNING COMPANY 00347588 W4360098 00105742 E-DECA Annual License Renewal 773.45 1-10-627-00-2238-0810-000-3141-01 DIR OF PRESCHOOL DUES AND FEES 773.45 C Computer 00347588 W4360098 00105742 E-DECA Annual License Renewal 136.50 1-22-627-00-2238-0810-000-8600-00 HEAD START DUES AND FEES 136.50 C Computer Total Check: 909.95 5000325004 07/02/20 217336 TEACHING STRATEGIES, INC. -

PCB Supplier of the Best Quality, Lowest Price and Reliable Lead Time
The Best Quality PCB Supplier PCB Supplier of the Best Quality, Lowest Price and Reliable Lead Time • Low Cost Prototype • Standard Prototype & Production • Stencil • PCB Design • • • • • • Visit us: www.qualiecocircuits.co.nz PCB Supplier of the Best Quality, Lowest Price and Reliable Lead Time PCB DESIGN BASICS Hello friends!! Welcome to the world of PCB designing, where you will not only learn but update yourself with various advance technologies and designing tips. First of all, let us see the basic of PCB Designing step by step, which will give you an idea what exactly PCB designing is? First step is schematic capture or schematic entry is done through an EDA (Electronic Design Automation) tool. Card dimensions and template are decided based on required circuitry and case of the PCB. Determine the fixed components and heat sinks if required. Deciding stack layers of the PCB. 4 to 12 layers or more depending on design complexity. Ground plane and Power plane are decided. Signal planes, where signals are routed, are in top layer as well as internal layers. Line impedance determination using dielectric layer thickness, routing copper thickness and trace-width. Trace separation also taken into account in case of differential signals. Microstrip, stripline or dual stripline can be used to route signals. Placement of the components. Thermal considerations and geometry are taken into account. Vias and lands are marked. Routing the signal trace. For optimal EMI performance high frequency signals are routed in internal layers between power or ground planes as power plane behaves as ground for AC. And the last step Geber File generation for manufacturing. -

Living Well with Chronic Illness: a Call for Public Health Action
THE NATIONAL ACADEMIES PRESS This PDF is available at http://nap.edu/13272 SHARE Living Well with Chronic Illness: A Call for Public Health Action DETAILS 350 pages | 6 x 9 | HARDBACK ISBN 978-0-309-38773-6 | DOI 10.17226/13272 AUTHORS BUY THIS BOOK Committee on Living Well with Chronic Disease: Public Action to Reduce Disability and Improve Functioning and Quality of Life; Institute of Medicine FIND RELATED TITLES Visit the National Academies Press at NAP.edu and login or register to get: – Access to free PDF downloads of thousands of scientific reports – 10% off the price of print titles – Email or social media notifications of new titles related to your interests – Special offers and discounts Distribution, posting, or copying of this PDF is strictly prohibited without written permission of the National Academies Press. (Request Permission) Unless otherwise indicated, all materials in this PDF are copyrighted by the National Academy of Sciences. Copyright © National Academy of Sciences. All rights reserved. Living Well with Chronic Illness: A Call for Public Health Action LIVING WELL WITH CHRONIC ILLNESS A Call for Public Health Action Committee on Living Well with Chronic Disease: Public Health Action to Reduce Disability and Improve Functioning and Quality of Life Board on Population Health and Public Health Practice Copyright National Academy of Sciences. All rights reserved. Living Well with Chronic Illness: A Call for Public Health Action THE NATIONAL ACADEMIES PRESS • 500 Fifth Street, NW • Washington, DC 20001 NOTICE: The project that is the subject of this report was approved by the Governing Board of the National Research Council, whose members are drawn from the councils of the National Academy of Sciences, the National Academy of Engineering, and the Institute of Medicine. -

See Our FY18 Annual Report Here
NAVAL POSTGRADUATE SCHOOL MONTEREY, CALIFORNIA CONSORTIUM FOR ROBOTICS AND UNMANNED SYSTEMS EDUCATION AND RESEARCH (CRUSER) FY18 ANNUAL REPORT Prepared by Lyla Englehorn, Faculty Associate – Research December 2018 Approved for public release: distribution unlimited Prepared for: Dr. Brian Bingham, CRUSER Director and Dr. Raymond R. Buettner Jr., NPS FX Director THIS PAGE INTENTIONALLY LEFT BLANK Form Approved REPORT DOCUMENTATION PAGE OMB No. 0704-0188 Public reporting burden for this collection of information is estimated to average 1 hour per response, including the time for reviewing instructions, searching existing data sources, gathering and maintaining the data needed, and completing and reviewing this collection of information. Send comments regarding this burden estimate or any other aspect of this collection of information, including suggestions for reducing this burden to Department of Defense, Washington Headquarters Services, Directorate for Information Operations and Reports (0704-0188), 1215 Jefferson Davis Highway, Suite 1204, Arlington, VA 22202-4302. Respondents should be aware that notwithstanding any other provision of law, no person shall be subject to any penalty for failing to comply with a collection of information if it does not display a currently valid OMB control number. PLEASE DO NOT RETURN YOUR FORM TO THE ABOVE ADDRESS. 1. REPORT DATE (DD-MM-YYYY) 2. REPORT TYPE 3. DATES COVERED (From-To) 28 December 2018 Technical Report 1 Oct 2017 – 30 Sept 2018 4. TITLE AND SUBTITLE 5a. CONTRACT NUMBER Consortium for Robotics and Unmanned Systems Education and Research (CRUSER) FY18 Annual Report 5b. GRANT NUMBER 5c. PROGRAM ELEMENT NUMBER 6. AUTHOR(S) 5d. PROJECT NUMBER Lyla Englehorn, MPP 5e.