Apps Can Quickly Destroy Your Mobile's Flash: Why They Don't
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Appendix Contents
Appendix This appendix contains the textual transcripts of the fifty smartphone advertisements selected for the analysis. The smartphones are arranged in an alphabetical order and numbered in concord with the numbering of the advertisements used in the thesis. Contents Appendix .................................................................................................................................... 1 1 Acer Liquid Z220 commercial ......................................................................................... 4 2 Acer Liquid Z520 commercial ......................................................................................... 4 3 Alcatel Onetouch Idol 2 S commercial ............................................................................ 5 4 ALCATEL ONETOUCH PIXI 3 Family commercial ................................................... 6 5 ARCHOS Helium Plus commercial ................................................................................. 8 6 ASUS ZenFone 2 and ZenFone Zoom commercial ........................................................ 9 7 ASUS ZenFone Max commercial ................................................................................... 10 8 BlackBerry Classic commercial ..................................................................................... 12 9 BlackBerry PRIV commercial ....................................................................................... 13 10 BLU Life Pure Mini commercial ................................................................................ -

ISS 2016 Bootcamp: Intel Omni-Path Architecture
Intel® Scalable System Framework A Configurable Design Philosophy Extensible to a Wide Range of Workloads Small Clusters Through Supercomputers Compute Memory/Storage Compute and Data-Centric Computing Fabric Software Standards-Based Programmability Intel Silicon On-Premise and Cloud-Based Photonics Intel® Xeon® Processors Intel® Solutions for Lustre* Intel® Omni-Path Architecture HPC System Software Stack Intel® Xeon Phi™ Processors Intel® SSDs Intel® True Scale Fabric Intel® Software Tools Intel® Xeon Phi™ Coprocessors Intel® Optane™ Technology Intel® Ethernet Intel® Cluster Ready Program Intel® Server Boards and Platforms 3D XPoint™ Technology Intel® Silicon Photonics Intel® Visualization Toolkit 1 YANG YANGUO May 2016 Intel Confidential Agenda Quick Overview: HPC Fabrics What is Intel® 100Gb Omni-Path Architecture(OPA)? Why is Intel 100Gb OPA Summary Intel® Solutions Summit 2016 Intel Confidential 3 Intel Confidential What is Different Between Networks and Fabrics? Network: Universal interconnect designed to HPC Fabric: Optimized interconnect allows allow any-and-all systems to communicate many nodes to perform as a single system Intel® Omni-Path Architecture or Infiniband Key NETWORK (Ethernet) Attributes: Key FABRIC Attributes: . Flexibility for any application . Targeted for specific applications . Designed for universal communication . Optimized for performance and efficiency . Extensible configuration . Engineered topologies . Multi-vendor components . Single-vendor solutions Intel® Solutions Summit 2016 Intel Confidential 5 Fabric: InfiniBand* and OPA InfiniBand/OPA is a multi-lane, high-speed serial interconnect (Copper or Fiber) . Typically presented as a 4x solution . Speeds: 40Gb/s (M & Intel QDR), 56Gb/s (M FDR), 100Gb/s (EDR & Intel OPA) High bandwidth, low latency HPC interconnect for commodity servers . Ethernet switch latency is typically measured in μs, but InfiniBand/OPA is in nanoseconds . -
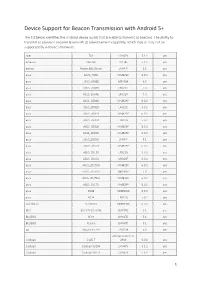
Device Support for Beacon Transmission with Android 5+
Device Support for Beacon Transmission with Android 5+ The list below identifies the Android device builds that are able to transmit as beacons. The ability to transmit as a beacon requires Bluetooth LE advertisement capability, which may or may not be supported by a device’s firmware. Acer T01 LMY47V 5.1.1 yes Amazon KFFOWI LVY48F 5.1.1 yes archos Archos 80d Xenon LMY47I 5.1 yes asus ASUS_T00N MMB29P 6.0.1 yes asus ASUS_X008D MRA58K 6.0 yes asus ASUS_Z008D LRX21V 5.0 yes asus ASUS_Z00AD LRX21V 5.0 yes asus ASUS_Z00AD MMB29P 6.0.1 yes asus ASUS_Z00ED LRX22G 5.0.2 yes asus ASUS_Z00ED MMB29P 6.0.1 yes asus ASUS_Z00LD LRX22G 5.0.2 yes asus ASUS_Z00LD MMB29P 6.0.1 yes asus ASUS_Z00UD MMB29P 6.0.1 yes asus ASUS_Z00VD LMY47I 5.1 yes asus ASUS_Z010D MMB29P 6.0.1 yes asus ASUS_Z011D LRX22G 5.0.2 yes asus ASUS_Z016D MXB48T 6.0.1 yes asus ASUS_Z017DA MMB29P 6.0.1 yes asus ASUS_Z017DA NRD90M 7.0 yes asus ASUS_Z017DB MMB29P 6.0.1 yes asus ASUS_Z017D MMB29P 6.0.1 yes asus P008 MMB29M 6.0.1 yes asus P024 LRX22G 5.0.2 yes blackberry STV100-3 MMB29M 6.0.1 yes BLU BLU STUDIO ONE LMY47D 5.1 yes BLUBOO XFire LMY47D 5.1 yes BLUBOO Xtouch LMY47D 5.1 yes bq Aquaris E5 HD LRX21M 5.0 yes ZBXCNCU5801712 Coolpad C106-7 291S 6.0.1 yes Coolpad Coolpad 3320A LMY47V 5.1.1 yes Coolpad Coolpad 3622A LMY47V 5.1.1 yes 1 CQ CQ-BOX 2.1.0-d158f31 5.1.1 yes CQ CQ-BOX 2.1.0-f9c6a47 5.1.1 yes DANY TECHNOLOGIES HK LTD Genius Talk T460 LMY47I 5.1 yes DOOGEE F5 LMY47D 5.1 yes DOOGEE X5 LMY47I 5.1 yes DOOGEE X5max MRA58K 6.0 yes elephone Elephone P7000 LRX21M 5.0 yes Elephone P8000 -

Boot’ for Computer Best of Outstanding Technology
Session 2013-2014 ‘Boot’ For Computer Best of Outstanding Technology Department of Computer Science & Engineering Institute of Engineering and Science IPS Academy, Indore 2013-2014 CONTENTS Part A S. List of Titles Page No. No. Programme Education Objectives (PEO)/ Programme 1. I Outcomes (PO) 2. Departmental Information III 3. Vision & Mission of the Department IV 4. Department Faculty Details V 5. Department Event VIII Membership of Professional Societies/ Sports News/ 6. IX Placements 7. Faculty Members Achievements X 8. Students Achievements XII Part B S. No. Topic Page No. 1. Gesture Recognition, Voice Command& Holography 1 Technology 2. First Step To Android Application Development 3 3. Nanotechnology 5 4. Coronal mass ejection 8 5. Big Data Analytics & SAS: An Overview 11 6. Era of Smartphone’s 14 7. Edward Snowden: how the spy story of the age leaked out 18 8. Free Amazon Web Services -and How to Make the Most of 22 them 9. Hacking the Internet - bringing down infrastructure 26 10. Holographic screen 30 11. Review of Energy Awareness in TORA Protocol 32 12. Affective computing and its applications in the apparel retail 33 industry 13. OLED Display Technology 34 14. Continuous Speech Recognition System in Hindi 36 15. OpenStack : Open Source Cloud 37 16. Viruses are Good Thing 40 17. Google Cloud Messaging 42 18. Network Simulater-2 43 19. Intelligent vehicular ad hoc networks (InVANETs) 45 20. Software as a Service (SaaS) 47 21. Infrastructure as a Service (IaaS) 48 22. Advanced Data Recovery 49 Principal Message Technical Education is the most potential instrument for socio-economic change. -

Product Change Notification
Product Change Notification Change Notification #: 116422 - 00 Change Title: For select Intel® SSD DC S4500 Series and Intel® SSD DC S4600 Series SKUs, PCN 116422-00, Product Discontinuance, End of Life Date of Publication: August 31, 2018 Key Characteristics of the Change: Product Discontinuance Forecasted Key Milestones: Last Product Discontinuance Order Date: December 31, 2018 Last Product Discontinuance Shipment Date: April 30, 2019 Description of Change to the Customer: Intel is announcing the End of Life timeline for the Intel® SSD DC S4500 Series and Intel® SSD DC S4600 Series SKUs listed in the products affected table list in the PCN announcement. The Intel® SSD DC S4500 Series and Intel® SSD DC S4600 Series products listed on the "Products Affected/Intel Ordering Codes" table below will be discontinued and unavailable for additional orders after the December 31, 2018. Effective April 30, 2019 Intel will stop shipping Intel® SSD DC S4500 Series and Intel® SSD DC S4600 Series hardware. Customer Impact of Change and Recommended Action: While Intel will make commercially reasonable efforts to support last time order quantities, it is recommended for customers to transition to the next generation of products - Intel® SSD D3-S4510 Series and D3-S4610 Series. Please contact your local Intel Field Sales representative if you have any further questions about this End of Life notice. Page 1 of 3 PCN #116422 - 00 Products Affected / Intel Ordering Codes: Product Name Product Code MM# Intel® SSD DC S4500 Series (240GB, 2.5in SATA 6Gb/s, -

Release Notes UFED Ultimate, UFED Infield, UFED Physical Analyzer
Release Notes UFED Ultimate, UFED InField, UFED Physical Analyzer, UFED Logical Analyzer & Cellebrite Reader February 2019 Now supporting: 27,785 device profiles App versions: 7,596 Forensic methods v. 7.15 Total Logical extraction 135 11,088 Physical extraction* 140 6,757 File system extraction 137 6,709 Extract/disable user lock 232 3,231 Total 644 27,785 *Including GPS devices The number of unique mobile devices with passcode capabilities is 5,216 HIGHLIGHTS App support • Now supporting deleted data from the WeChat application for Android devices. • 149 updated application versions for iOS and Android devices. Release Notes | UFED Ultimate, UFED InField, UFED Physical Analyzer, UFED Logical Analyzer & Cellebrite Reader | February 2019 | www.cellebrite.com Release Notes Industry first: Samsung Exynos physical bypass solution As Cellebrite continues to pioneer the world of mobile device extractions, we are the first vendor in the industry to provide a generic solution to access Samsung devices with the Exynos processor. This new decrypting bootloader capability enables unlock, full file system and physical extractions from a vast range of Samsung devices, popular around the world. Together with the support for Samsung Qualcomm devices, Cellebrite is the only vendor to provide a holistic solution to unlock and extract data from Samsung devices. Supported devices include: SM-G930F Galaxy S7, SM-G935F Galaxy S7 Edge, SM- A520F Galaxy A5 2017 and SM-J730F Galaxy J7 Pro. Get to evidence faster with Selective Extraction When time is of the essence, and decisions need to be made quickly, examiners can use the new Selective Extraction capability to perform fast and focused extractions. -

Google Cloud Messaging (GCM) I
International Journal of Innovative and Emerging Research in Engineering Volume 3, Issue 2, 2016 Available online at www.ijiere.com International Journal of Innovative and Emerging Research in Engineering e-ISSN: 2394 – 3343 p-ISSN: 2394 – 5494 Google Cloud Messaging (GCM) I. Miss. Sana Ismail Khan, II.Prof. Y. S. Patil I. Third Year of Engineering, Student, II. Asstt. Professor. I, II Department of Computer Science & Engineering, Hindi Seva Mandal’s, Shri Sant Gadge Baba College of Engineering & Technology, Bhusawal - 425203, Dist. – Jalgaon, Maharashtra, India ABSTRACT: Today Android is widely used operating system for smart phones; it is used as personal computer also. It contains a touch screen user interface, camera and network monitoring. The entire feature provides ability to cell phone to become a Smartphone. Basically, most of chat application allow user to send instant messages and provide a way to sharing image files also. The main purpose of this paper is to proposed a methodology to provide instant messaging over Google Cloud Messaging (GCM) and also we presents a survey on timing performance of GCM, our findings that the message delivery is uncertain , it does not guarantee to timely message arrival. Therefore is not applicable for time sensitive, but it may be good for application scenarios where random multicasting is sufficient. Keywords: Instant messaging, GCM, Timing performance of GCM I. INTRODUCTION A. Instant messaging: The instant messaging application allows users to register to the system in order to use the application. After users has log in into the system, then the user can add another registered users to be their friends. -

Product Change Notification
Product Change Notification Change Notification #: 116497 - 00 Change Title: Select Intel® SSD 760p Series, Intel® SSD DC P4101 Series, Intel® SSD E 6100P Series, PCN 116497-00, Label, Label Update Date of Publication: September 25, 2018 Key Characteristics of the Change: Label Forecasted Key Milestones: Date Customer Must be Ready to Receive Post-Conversion Material: December 24, 2018 Description of Change to the Customer: The Intel® SSD 760p Series, Intel® SSD DC P4101 and Intel® SSD E 6100P Series SKUs listed in the Products Affected Table below will have the following label changes: 1. Outer Box: • Add extra information ("Model") and linear barcode on the label with no change to current box label format and location. Page 1 of 3 PCN #116497 - 00 2. White/Brown Box Label: • Add extra information and linear barcode on the label. Customer Impact of Change and Recommended Action: The change in labeling only affects the label. There is no form, fit, function or visible change to the products listed in the Products Affected/Intel Order Codes table. Please contact your local Intel Field Sales Representative if you have any further questions about these changes. Products Affected / Intel Ordering Codes: Marketing Name Product Code MM# Intel® SSD E 6100p Series (128GB, M.2 80mm PCIe 3.0 x4, 3D2, TLC) SSDPEKKR128G801 963756 Generic Single Pack Intel® SSD E 6100p Series (256GB, M.2 80mm PCIe 3.0 x4, 3D2, TLC) SSDPEKKR256G801 963758 Generic Single Pack Intel® SSD E 6100p Series (128GB, M.2 80mm PCIe 3.0 x4, 3D2, TLC) SSDPEKKR128G810 963759 Generic -
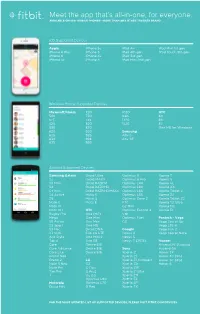
Meet the App That's All-In-One, for Everyone
Meet the app that’s all-in-one, for everyone. AVAILABLE ON 120+ MOBILE PHONES—MORE THAN ANY OTHER TRACKER BRAND iOS Supported Devices Apple iPhone 5c iPad Air iPad Mini 1st gen iPhone 6 Plus iPhone 5 iPad 4th gen iPod Touch 5th gen iPhone 6 iPhone 4s iPad 3rd gen iPhone 5s iPhone 4 iPad Mini 2nd gen Windows Phone Supported Devices Microsoft/Nokia 720 1020 HTC 520 730 Icon 8X 521 735 1320 8XT 525 820 1520 8S 530 830 One M8 for Windows 620 920 Samsung 625 925 Ativ S 630 928 Ativ SE 635 930 Android Supported Devices Samsung Galaxy Droid Ultra Optimus G Xperia T S3 Droid MAXX Optimus G Pro Xperia V S3 Mini Optimus L40 Xperia VL S4 Optimus L80 Xperia AX S4 mini Optimus L65 Xperia Tablet Z S4 Active Moto X Optimus L35 Xperia Z2 S5 Moto G Optimus Zone 2 Xperia Tablet Z2 Note II Moto E F70 Xperia T2 Ultra Note III G2 Mini Xperia M2 Note 10.1 HTC Optimus Exceed 2 Xperia E1 Rugby Pro One (m7) Volt Mega One Mini Optimus Fuel Pantech - Vega S5 Active One Max G3 V ega Secret Up S5 Sport One M8 Vega LTE-A S3 Neo Droid DNA Google Vega Iron 2 S3 Slim Evo 4G LTE Nexus 4 Vega Secret Note Ace Style One Mini 2 Nexus 5 Tab 4 One E8 Nexus 7 (2013) Huawei Core Desire 610 Ascend P7 (Sophia) Core Advance Desire 816 Sony Ascend G6 Core Lite Desire 516 Xperia Z Honor 3X Grand Neo Xperia Z1 Honor 3C (3G) Grand 2 LG Xperia Z1 Compact Honor 3C (4G) Note 3 Neo G2 Xperia Z1s Honor 6 Note Pro G Flex Xperia Z1F Tab Pro G Pro2 Xperia Z Ultra J Vu 3.0 Xperia ZR Optimus L90 Xperia ZL Motorola Optimus L70 Xperia SP Droid Mini G Pad Xperia TX FOR THE MOST UPDATED LIST OF SUPPORTED DEVICES, PLEASE VISIT FITBIT.COM/DEVICES. -

How Secure Is Textsecure?
How Secure is TextSecure? Tilman Frosch∗y, Christian Mainkay, Christoph Badery, Florian Bergsmay,Jorg¨ Schwenky, Thorsten Holzy ∗G DATA Advanced Analytics GmbH firstname.lastname @gdata.de f g yHorst Gortz¨ Institute for IT-Security Ruhr University Bochum firstname.lastname @rub.de f g Abstract—Instant Messaging has gained popularity by users without providing any kind of authentication. Today, many for both private and business communication as low-cost clients implement only client-to-server encryption via TLS, short message replacement on mobile devices. However, until although security mechanisms like Off the Record (OTR) recently, most mobile messaging apps did not protect confi- communication [3] or SCIMP [4] providing end-to-end con- dentiality or integrity of the messages. fidentiality and integrity are available. Press releases about mass surveillance performed by intelli- With the advent of smartphones, low-cost short-message gence services such as NSA and GCHQ motivated many people alternatives that use the data channel to communicate, to use alternative messaging solutions to preserve the security gained popularity. However, in the context of mobile ap- and privacy of their communication on the Internet. Initially plications, the assumption of classical instant messaging, fueled by Facebook’s acquisition of the hugely popular mobile for instance, that both parties are online at the time the messaging app WHATSAPP, alternatives claiming to provide conversation takes place, is no longer necessarily valid. secure communication experienced a significant increase of new Instead, the mobile context requires solutions that allow for users. asynchronous communication, where a party may be offline A messaging app that claims to provide secure instant for a prolonged time. -

EB GUIDE: and Engineering Services All-In-One Automotive HMI UI and Application Development Services Development Toolchain, Voice Assistants (E.G
How can software suppliers create future car user experiences? Elektrobit, the visionary supplier of embedded software products and services is your answer. Deliver stunning, next-generation automotive user interfaces Disruption is affecting every industry. In the automotive At EB, we believe that an optimal interaction between hu- industry, this is most visible in the transformation of the man and machine is characterized by three aspects: classic vehicle into a software-driven Internet of Things (IoT) device. Personalization, connectivity, and mobility-as- a-service are becoming increasingly important for drivers EXCELLENT and passengers. USABILITY HIGH saving you In order to stand out in a marketplace that is growing more EFFICIENCY operator time saving both time competitive by the day, automotive manufacturers are seizing and money the opportunity to showcase their distinct advantages in pro- viding their drivers and passengers user interfaces that are sleek, intuitive, and above all, seamlessly integrated. MAXIMUM Elektrobit has created a big move from simple driver infor- PRODUCTIVITY ultimately giving your mation centers, to in-vehicle infotainment systems, to con- company a competitive nected cockpits that integrate with multiple technologies advantage simultaneously. 2 The secret to our success is simple. We're passionate about Our mission is to deliver HMIs optimized for your target promoting the interactions between humans and machines platform - HMIs that meet your expectations for high qua- through exceptionally designed software tools and solutions lity, that perfectly integrate multimodal input and output and our skilled engineering teams. devices, and that can be easily maintained over multiple variants and even multiple life cycles of your product. -

System Design for Telecommunication Gateways
P1: OTE/OTE/SPH P2: OTE FM BLBK307-Bachmutsky August 30, 2010 15:13 Printer Name: Yet to Come SYSTEM DESIGN FOR TELECOMMUNICATION GATEWAYS Alexander Bachmutsky Nokia Siemens Networks, USA A John Wiley and Sons, Ltd., Publication P1: OTE/OTE/SPH P2: OTE FM BLBK307-Bachmutsky August 30, 2010 15:13 Printer Name: Yet to Come P1: OTE/OTE/SPH P2: OTE FM BLBK307-Bachmutsky August 30, 2010 15:13 Printer Name: Yet to Come SYSTEM DESIGN FOR TELECOMMUNICATION GATEWAYS P1: OTE/OTE/SPH P2: OTE FM BLBK307-Bachmutsky August 30, 2010 15:13 Printer Name: Yet to Come P1: OTE/OTE/SPH P2: OTE FM BLBK307-Bachmutsky August 30, 2010 15:13 Printer Name: Yet to Come SYSTEM DESIGN FOR TELECOMMUNICATION GATEWAYS Alexander Bachmutsky Nokia Siemens Networks, USA A John Wiley and Sons, Ltd., Publication P1: OTE/OTE/SPH P2: OTE FM BLBK307-Bachmutsky August 30, 2010 15:13 Printer Name: Yet to Come This edition first published 2011 C 2011 John Wiley & Sons, Ltd Registered office John Wiley & Sons Ltd, The Atrium, Southern Gate, Chichester, West Sussex, PO19 8SQ, United Kingdom For details of our global editorial offices, for customer services and for information about how to apply for permission to reuse the copyright material in this book please see our website at www.wiley.com. The right of the author to be identified as the author of this work has been asserted in accordance with the Copyright, Designs and Patents Act 1988. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, except as permitted by the UK Copyright, Designs and Patents Act 1988, without the prior permission of the publisher.