Correcting Fake News: a Survey Ex- Periment"
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Automated Meme Magic: an Exploration Into the Implementations and Imaginings of Bots on Reddit”
1 “Automated Meme Magic: An Exploration into the Implementations and Imaginings of Bots on Reddit” Jonathan Murthy | [email protected] | 2018 2 Table of Contents Acknowledgments......................................................................................................................................3 Abstract......................................................................................................................................................4 1.2 Research Questions.........................................................................................................................6 1.2.1 Why Reddit..............................................................................................................................7 1.2.2 Bots..........................................................................................................................................9 1.3 Outline...........................................................................................................................................10 2 Bot Research.........................................................................................................................................11 2.1. Functional Bots.............................................................................................................................13 2.2 Harmful Bots.................................................................................................................................14 2.2.1 The Rise of Socialbots...........................................................................................................16 -

A Tool for Automated Knowledge Base Construction
KELVIN: a tool for automated knowledge base construction Paul McNamee, James Mayfield Tim Finin, Tim Oates Johns Hopkins University University of Maryland Human Language Technology Center of Excellence Baltimore County Dawn Lawrie Tan Xu, Douglas W. Oard Loyola University Maryland University of Maryland College Park Abstract X:Person has-job-title title • X:Organization headquartered-in Y:Location We present KELVIN, an automated system for • processing a large text corpus and distilling a Multiple layers of NLP software are required for knowledge base about persons, organizations, this undertaking, including at the least: detection of and locations. We have tested the KELVIN named-entities, intra-document co-reference resolu- system on several corpora, including: (a) the tion, relation extraction, and entity disambiguation. TAC KBP 2012 Cold Start corpus which con- To help prevent a bias towards learning about sists of public Web pages from the University of Pennsylvania, and (b) a subset of 26k news prominent entities at the expense of generality, articles taken from English Gigaword 5th edi- KELVIN refrains from mining facts from sources tion. such as documents obtained through Web search, 2 3 Our NAACL HLT 2013 demonstration per- Wikipedia , or DBpedia. Only facts that are as- mits a user to interact with a set of search- serted in and gleaned from the source documents are able HTML pages, which are automatically posited. generated from the knowledge base. Each Other systems that create large-scale knowledge page contains information analogous to the bases from general text include the Never-Ending semi-structured details about an entity that are Language Learning (NELL) system at Carnegie present in Wikipedia Infoboxes, along with Mellon University (Carlson et al., 2010), and the hyperlink citations to supporting text. -

Corruption in the Defense Sector: Identifying Key Risks to U.S
Corruption in the Defense Sector: Identifying Key Risks to U.S. Counterterrorism Aid Colby Goodman and Christina Arabia October 2018 About Center for International Policy The Center for International Policy promotes cooperation, transparency, and accountability in U.S.global relations. Through research and advocacy, our programs address the most urgent threats to our planet: war, corruption, inequality, and climate change. CIP’s scholars, journal- ists, activists and former government ofcials provide a unique mixture of access to high-level ofcials, issue-area expertise, media savvy and strategic vision. We work to inform the public and decision makers in the United States and in international organizations on policies to make the world more just, peaceful, and sustainable. About Foriegn Influence Transparency Inititative While investigations into Russian infuence in the 2016 election regularly garner front-page head- lines, there is a half-billion-dollar foreign infuence industry working to shape U.S. foreign policy every single day that remains largely unknown to the public. The Foreign Infuence Transparency Initiative is working to change that anonymity through transparency promotion, investigative research, and public education. Acknowledgments This report would not have been possible without the hard work and support of a number of people. First and foremost, Hannah Poteete, who tirelessly coded nearly all of the data mentioned here. Her attention to detail and dedication to the task were extraordinary. The report also could not have been completed without the exemplary work of Avery Beam, Thomas Low, and George Savas who assisted with writing, data analysis, fact-checking, formatting, and editing. Salih Booker and William Hartung of the Center for International Policy consistently supported this project, all the way from idea inception through editing and completion of this report. -

Child Pornography Is Sex Trafficking
Child Pornography is Sex Trafficking January 31, 2017 By Human Trafficking Collaborative Network (HTCN) 1 On December 30, 2011, Former President Obama declared January to be National Slavery and Human Trafficking Prevention Month. The general public’s awareness of human trafficking has improved considerably over the past years. At the time of this writing, the last day of the 2017 Human Trafficking Awareness Month, we are grateful that many community activities have been held in St. Louis and surrounding areas. Some activists participated in a series of anti- human trafficking campaigns at the Missouri Capital; some held a vigil for survivors and victims who lost their lives; some held resource dissemination events to better inform service providers, concerned citizens and students. In light of a very recent high-profile indictment of a St. Louis County child pornography case, we are compelled to providing regional information on child pornography in the context of human trafficking. As defined by the Victims of Trafficking and Violence Protection Act of 2000 (TPVA, 2000), [i] human trafficking includes recruitment, harboring, provision, receipt, transportation and/or obtaining of individuals by using force or threats, coercion, fraud and/or using systems of indebtedness or debt bondage for purposes of sexual or other forms of economic exploitation. Coercion includes threats of physical or psychological harm to the 1. The Human Trafficking Collaborative Network (HTCN) core members include: Rumi Kato Price (WU School of Medicine); Andrea Nichols (WU Brown School of Social Work & Women Gender and Sexuality Studies; St. Louis Community College Forest Park); Kathleen Thimsen (Goldfarb School of Nursing at BJC); Tonya Edmond (WU Brown School of Social Work); Richelle Clark & Matthew Brown (IPH Center for Community Health Partnership & Research; Sundari Balan (WU School of Medicine); Natalie Palmer (Goldfarb School of Nursing at BJC); and Porpong (Paul) Boonmak (McDonnell International Scholars Academy, Master of Population Health Sciences; WU School of Medicine). -

Subway Officially Cuts Ties with Jared
adage.com http://adage.com/article/cmo-strategy/subway-officially-cuts-ties-jared/300012/ Subway Officially Cuts Ties With Jared Maureen August 18, Morrison 2015 Subway has appeared to officially sever its ties to longtime spokesman Jared Fogle after news reports surfaced that he was going to plead guilty to possession of child pornography charges on Wednesday. Said the company on Twitter: Earlier on Tuesday, a local Fox affiliate reported that, according to sources, Mr. Fogle was going accept a plea deal on Wednesday, but not much more detail was available. Mr. Fogle initially had his relationship suspended by Subway in early July after federal authorities raided his home. At the time, the federal agents did not specify why they investigated Mr. Fogle's residence, but it came less than two months after Russell Taylor, executive director of the Fogle Foundation, a group that is dedicated to helping teach kids healthy lifestyle habits, was arrested on child pornography charges. Following those charges, Subway and Mr. Fogle said they had severed all ties with Mr. Taylor. ADVERTISING After the federal raid, Subway distanced itself by saying that it had "suspended" its relationship with Jared, but that language left some wiggle room for the brand to reinstate it. The company also removed its Jared references from its website, including what became an unfortunately named game on its kids' site called Jared's Pants Dance. Whether any of this will affect Subway's business of course remains to be seen, but it's possible it won't impact it much. "I don't think it will materially impact Subway -- they already distanced themselves from him," said marketing consultant Denise Lee Yohn in an email. -
![<R2PX] 2^]Rtstb <XRWXVP]](https://docslib.b-cdn.net/cover/2984/r2px-2-rtstb-xrwxvp-492984.webp)
<R2PX] 2^]Rtstb <XRWXVP]
M V 7>DB4>540AC7)Get a chic blueprint with no carbon footprint | 8]bXST A PUBLICATION OF | P L A N Y O U R N I G H T A T W W W. E X P R E S S N I G H T O U T. C O M | OCTOBER 3-5, 2008 | -- 5A44++ Weekend C74A>03F0AA8>AB --;Pbc]XVWc½bSTQPcTT]STSPUcTa C74A43B:8=B4G?42C0C>D675867C8=?78;;Hk ! 4g_aTbb½STPS[X]T5X]SX]ST_cW R^eTaPVTPcfPbWX]Vc^]_^bcR^\ <R2PX] 2^]RTSTb CHRIS O’MEARA/AP Evan Longoria hit two home runs in the Rays’ win. <XRWXVP] APhbA^[[)Longoria powers Losing ground, Republican Tampa to first playoff win | # writes off battleground state F0B78=6C>=k Republican presidential can- ATbRdT4UU^ac) Push to get didate John McCain conceded battleground Michigan to the Democrats on Thursday, GOP bailout passed gains steam | " officials said, a major retreat as he struggles to regain his footing in a campaign increas- 5^bbTcc2[dTb) Wreckage of ingly dominated by economic issues. These officials said McCain was pulling adventurer’s plane found | # staff and advertising out of the economically distressed Midwestern state. With 17 elec- 4=C4AC08=<4=C toral votes, Michigan voted for Democrat John Kerry in 2004, but Republicans had poured money into an effort to try to place it in their column this year. ?[PhX]V=XRT) The decision allows McCain’s resources Michael Cera acts to be sent to Ohio, Wisconsin, Florida and other more competitive states. But it also sweetly awk- means Obama can shift money to other ward .. -
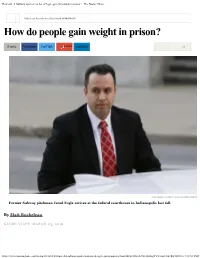
How Did Ex-Subway Spokesman Jared Fogle Gain 30 Pounds in Prison? - the Boston Globe
How did ex-Subway spokesman Jared Fogle gain 30 pounds in prison? - The Boston Globe Help Your Favorite Area Non-Profit With GRANT How do people gain weight in prison? E-MAIL FACEBOOK TWITTER GOOGLE+ LINKEDIN 22 /MICHAEL CONROY/ASSOCIATED PRESS Former Subway pitchman Jared Fogle arrives at the federal courthouse in Indianapolis last fall. By Matt Rocheleau GLOBE STAFF MARCH 03, 2016 https://www.bostonglobe.com/metro/2016/03/03/how-did-subway-spokesman-jared-fogle-gain-pounds-prison/BEiiFJ2K6lvVnLbk0mgPVN/story.html[4/14/2016 7:13:51 PM] How did ex-Subway spokesman Jared Fogle gain 30 pounds in prison? - The Boston Globe Former Subway restaurant spokesman Jared Fogle has reportedly gained 30 pounds in just his first three months in prison. Such dramatic weight gain while locked up is not an unprecedented phenomenon, researchers have found. Fogle is serving a sentence of more than 15 years for child pornography possession and having sex with underage prostitutes. Before that, Fogle spent 15 years as the face of Subway, crediting his regular diet of the chain’s sandwiches with helping him to lose 245 pounds. His weight loss relapse was reported this week by InTouch Weekly magazine. But there have been other prominent cases of prisoners gaining weight. Serial killer Gary Lee Sampson was reported in 2014 to have gained about 150 pounds over the course of roughly 11 years behind bars. Singer Chris Brown reportedly gained 35 pounds after about three and a half months in prison. Experts blame several factors, which can work in combination with each other. -

The Underlying Psychophysiology of Pedophilic Disorder and the Implications for Treatment Approaches
National Louis University Digital Commons@NLU Dissertations 8-2019 The Underlying Psychophysiology of Pedophilic Disorder and the Implications for Treatment Approaches Tonise Florexil Follow this and additional works at: https://digitalcommons.nl.edu/diss Part of the Clinical Psychology Commons, Counseling Psychology Commons, Developmental Psychology Commons, and the Mental and Social Health Commons Recommended Citation Florexil, Tonise, "The Underlying Psychophysiology of Pedophilic Disorder and the Implications for Treatment Approaches" (2019). Dissertations. 554. https://digitalcommons.nl.edu/diss/554 This Dissertation - Public Access is brought to you for free and open access by Digital Commons@NLU. It has been accepted for inclusion in Dissertations by an authorized administrator of Digital Commons@NLU. For more information, please contact [email protected]. The Underlying Psychophysiology of Pedophilic Disorder and the Implications for Treatment Approaches Tonise Florexil Doctor of Psychology Florida School of Professional Psychology Patricia S. Dixon, Psy.D. Chair Dr. Eric L. Rosen, Ph.D. Member A Clinical Research Project submitted to the Faculty of the Florida School of Professional Psychology at National Louis University in partial fulfillment of the requirements for the degree of Doctor of Psychology in Clinical Psychology. Tampa, Florida August 2019 The Doctorate Program in Clinical Psychology Florida School of Professional Psychology at National Louis University CERTIFICATE OF APPROVAL ___________________________ Clinical Research Project ___________________________ This is to certify that the Clinical Research Project of Tonise Florexil has been approved by the CRP Committee on August 9, 2019 as satisfactory for the CRP requirement for the Doctorate of Psychology degree with a major in Clinical Psychology Examining Committee: ___________________________________________ Committee Chair: Patricia S. -

Indiana State Report on Human Trafficking 1 | P a G E
Indiana State Report on Human Trafficking 1 | P a g e December 1, 2016 Dear Colleagues, Human trafficking, a scourge against humanity, has far reaching impacts nationally, internationally, and in Indiana. I am pleased to provide the first comprehensive report in the State of Indiana on human trafficking. This is a project prepared over the past 18 months by many individuals and organizations who contributed to the work of the Indiana Protection for Abused and Trafficked Humans Task Force (IPATH), the state-wide human trafficking task force, and others who serve victims and who contribute daily, such as members of law enforcement, victim advocates and legislators. In 2009, when I first became co-chair of the task force with the U.S. Attorney for the Southern District of Indiana, little was known about this horrific crime, its victims, the perpetrators, or the trauma inflicted on those who fall prey to it. Through my service as the Chair of the National Association of Attorneys General Special Committee on Human Trafficking, I further realized the scope of this scourge and its impact on victims nationally and across the globe. Today we know far more than we did then, or even as far back as 2005 when the taskforce was first created. While we have made tremendous progress in policy, legislation, and research, we still have a long way to go. I am proud to present a summary and overview of the work done by many people in our state, from victim service providers to law enforcement, to lawmakers and researchers. This report represents a cumulative picture of those efforts, and outlines, most importantly, a path forward with ideas, recommendations and thoughts for the future. -

Creative Brief
SITUATION ANALYSIS ● Subway is the fast food restaurant with the most locations nationwide. ● #3 in sales in the the fast food restaurant category. ● For the past two years, Subway sales have been dropping at a faster rate than any other top 25 fast food chain. ● In recent years, Subway has lost its positioning as a healthier choice to fast food. ● The recent PR scandal involving Jared Fogle has not only affected Subway’s Brand Image, but also ended a successful 15 year partnership. CATEGORY ● Convenient, Customizable & Conscientious: Consumers are drawn to QSRs that allow them to customize their orders and choose healthier options. ● Bring on the Bold: Today’s consumer, particularly the growing multicultural segment and younger generation, is more adventurous when it comes to eating hot spices and exotic flavors. ● Make it Mobile: Mobile platforms offer solutions for ordering, marketing, loyalty programs and payment - mobile payments rose to $9 Billion in 2015 (US). ● Decisions, Decisions: 200,000+ restaurant locations in the U.S. alone. ● Fast Casual vs. QSR: 8% | 0 THE COMPETITION Main competition includes the following QSRs: ● McDonalds: the perfect burger experience for families since it is cheap, offers children- friendly menu options and many branches include a playing area ● Burger King: the perfect burger experience for busy and picky-eating individuals 18+, because it offers customization through “have it your way” initiative and includes more higher quality ingredients than McDonalds- the burger is grilled. ● Wendy’s: the perfect meal solution for young people 18-25 looking for healthier fast food options, saving money and to get as much value as possible as the burgers “don't cut corners” and the menu offers seasonal salads. -

Fake News and Misinformation Policy Lab Practicum (Spring 2017)
ST ANFORD Fake News & Misinformation Policy Practicum 2017 PRACTICUM RESEARCFacebookH TEAM: Research Team Jacob Finkel, JD ’19, Steven Jiang,Mufan BS ’17, Luo, PhD ‘22 Mufan Luo, PhD ’22, Rebecca Mears, JD/MPP ’19, Danaë Metaxa-Kakavouli, PhD ’20Camille, Peeples, JD ‘18 Camille Peeples, JD ’18, BrendanArjun Sasso, Shenoy,JD ’19, JD ‘19 Arjun Shenoy, JD ’19, Vincent Sheu, JD/MS ’18 , Nicolás Torres-Echeverry, JSM ’17 Google Research Team INSTRUCTOR AND PROJECTDanaë LEAD MetaxaS: -Kakavouli, PhD ‘20 Nicolás Torres-Echeverry, JSM ‘17 SENATOR RUSS FEINGOLD Edwin A. Heafey, Jr., Visiting Professor of Law Luciana Herman, Ph.D. Twitter Research Team Lecturer in Law Program Director, Law and Policy LabJacob Finkel, JD ‘19 Steven Jiang, BS ‘17 Ashwin Aravind, JD ‘18 Teaching Assistant Rebecca Mears, JD/MPP ‘19 Katie Joseff, MA ‘19 Research Assistant Reddit Research Team October POLICY CLIENT: Brendan Sasso, JD ‘19 Hewlett Foundation MadisonVincent Initiative Sheu, JD/MS ’18 2017 1 Acknowledgements This report reflects the research and analysis of an inter-disciplinary law and graduate student team enrolled in the Stanford Law School Fake News and Misinformation Policy Lab Practicum (Spring 2017). Under the guidance of instructor Senator Russ Feingold, the Edwin A. Heafey Visiting Professor of Law, the practicum surveyed the roles of four major online platforms in the spread of fake news beginning with the 2016 U.S. election. Assisting Senator Feingold in the practicum were Policy Lab Program Director and Lecturer Luciana Herman, Ph.D., and Teaching Assistant Ashwin Aravind, J.D. ’18. Brendan Sasso, J.D. ’19, served as the exceptional lead student editor for the report. -

Fake News: Potential Solutions to the Online Epidemic Lee K
NORTH CAROLINA LAW REVIEW Volume 96 | Number 1 Article 7 12-1-2017 Fake News: Potential Solutions to the Online Epidemic Lee K. Royster Follow this and additional works at: http://scholarship.law.unc.edu/nclr Part of the Law Commons Recommended Citation Lee K. Royster, Fake News: Potential Solutions to the Online Epidemic, 96 N.C. L. Rev. 270 (2017). Available at: http://scholarship.law.unc.edu/nclr/vol96/iss1/7 This Recent Developments is brought to you for free and open access by Carolina Law Scholarship Repository. It has been accepted for inclusion in North Carolina Law Review by an authorized editor of Carolina Law Scholarship Repository. For more information, please contact [email protected]. 96 N.C. L. REV 270 (2017) FAKE NEWS: POTENTIAL SOLUTIONS TO THE ONLINE EPIDEMIC* On December 4, 2016, police arrested Edgar Maddison Welch for assault with a dangerous weapon at Comet Ping Pong pizzeria in Washington, D.C.1 At some point before that day, Welch came across a story, transmitted online through 4chan, Reddit, and Twitter, along with other websites,2 stating that Hillary and Bill Clinton used Comet Ping Pong as a “front for a pedophile sex ring; the back room was supposedly used for kidnapping and trafficking children.”3 Welch accepted this story as true and decided he had to put a stop to it.4 He grabbed his assault rifle and drove 360 miles from his home in Salisbury, North Carolina to Comet Ping Pong in Washington, D.C,5 operated by the Clinton’s “co-conspirators,” to end the supposed scheme himself.6 He entered the store with family patrons present, walked up to the counter, and pointed his assault rifle directly at the cashier’s face.7 No one was injured, and Welch was apprehended and arrested by Washington police outside the restaurant soon after the incident.8 This “Pizzagate” conspiracy started when James Alefantis, Comet Ping Pong’s owner, was mentioned in an email sent from Hillary Clinton’s campaign manager because he was considering organizing a fundraiser for Clinton’s presidential campaign.9 * © 2017 Lee K.