Hacking for Dummies‰ 4TH EDITION
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Easy Slackware
1 Создание легкой системы на базе Slackware I - Введение Slackware пользуется заслуженной популярностью как классический linux дистрибутив, и поговорка "кто знает Red Hat тот знает только Red Hat, кто знает Slackware тот знает linux" несмотря на явный снобизм поклонников "бога Патре га" все же имеет под собой основания. Одним из преимуществ Slackware является возможность простого создания на ее основе практически любой системы, в том числе быстрой и легкой десктопной, о чем далее и пойдет речь. Есть дис трибутивы, клоны Slackware, созданные именно с этой целью, типа Аbsolute, но все же лучше создавать систему под себя, с максимальным учетом именно своих потребностей, и Slackware пожалуй как никакой другой дистрибутив подходит именно для этой цели. Легкость и быстрота системы определяется выбором WM (DM) , набором программ и оптимизацией программ и системы в целом. Первое исключает KDE, Gnome, даже новые версии XFCЕ, остается разве что LXDE, но набор программ в нем совершенно не устраивает. Оптимизация наиболее часто используемых про грамм и нескольких базовых системных пакетов осуществляется их сборкой из сорцов компилятором, оптимизированным именно под Ваш комп, причем каж дая программа конфигурируется исходя из Ваших потребностей к ее возможно стям. Оптимизация системы в целом осуществляется ее настройкой согласно спе цифическим требованиям к десктопу. Такой подход был выбран по банальной причине, возиться с gentoo нет ни какого желания, комп все таки создан для того чтобы им пользоваться, а не для компиляции программ, в тоже время у каждого есть минимальный набор из не большого количества наиболее часто используемых программ, на которые стоит потратить некоторое, не такое уж большое, время, чтобы довести их до ума. Кро ме того, такой подход позволяет иметь самые свежие версии наиболее часто ис пользуемых программ. -

Further Reading and What's Next
APPENDIX Further Reading and What’s Next I hope you have gotten an idea of how, as a penetration tester, you could test a web application and find its security flaws by hunting bugs. In this concluding chapter, we will see how we can extend our knowledge of what we have learned so far. In the previous chapter, we saw how SQL injection has been done; however, we have not seen the automated part of SQL injection, which can be done by other tools alongside Burp Suite. We will use sqlmap, a very useful tool, for this purpose. Tools that Can Be Used Alongside Burp Suite We have seen earlier that the best alternative to Burp Suite is OWASP ZAP. Where Burp Community edition has some limitations, ZAP can help you overcome them. Moreover, ZAP is an open source free tool; it is community-based, so you don’t have to pay for it for using any kind of advanced technique. We have also seen how ZAP works. Here, we will therefore concentrate on sqlmap only, another very useful tool we need for bug hunting. The sqlmap is command line based. It comes with Kali Linux by default. You can just open your terminal and start scanning by using sqlmap. However, as always, be careful about using it against any live © Sanjib Sinha 2019 197 S. Sinha, Bug Bounty Hunting for Web Security, https://doi.org/10.1007/978-1-4842-5391-5 APPENDIX FuRtHeR Reading and What’s Next system; don’t use it without permission. If your client’s web application has vulnerabilities, you can use sqlmap to detect the database, table names, columns, and even read the contents inside. -
Downloading Private Apps on Google Play Answers to Common Questions About Play App Signing
downloading private apps on google play Answers to common questions about Play App Signing. Android apps are cryptographically signed by the developer. This allows the package manager on the user’s device to verify that every app update comes from the same source and that it hasn’t been tampered with. Google Play also enforces this signature check when you upload your APK to the Google Play Console, so that even if someone had your login credentials it would be impossible to send a malicious update without also having access to your private key. Historically, developers were responsible for generating their own private keys and keeping them safe throughout the application’s lifetime. While this offered a lot of flexibility, it was also prone to mistakes: generating weak keys, accidentally checking in your private key to a public repository or even losing it altogether are just a few common ones that happen routinely even to seasoned developers. Nowadays developers have a compelling alternative to managing keys themselves: Play App Signing , in which the upload key (the one you use to upload your artifacts to Google Play) and the app signing key (the one used to sign APKs distributed to devices) can be separate, and the app signing key is stored securely on Google’s infrastructure. Even though many other popular platforms treat distribution keys this way, for many developers it’s a departure from the previous Android signing model, and some developers may feel like they’re giving up too much control over their apps. That’s why, I want to dispel some common misconceptions about Play App Signing, as well as give guidance on specific scenarios that you might encounter. -

Creating Permanent Test Collections of Web Pages for Information Extraction Research*
Creating Permanent Test Collections of Web Pages for Information Extraction Research* Bernhard Pollak and Wolfgang Gatterbauer Database and Artificial Intelligence Group Vienna University of Technology, Austria {pollak, gatter}@dbai.tuwien.ac.at Abstract. In the research area of automatic web information extraction, there is a need for permanent and annotated web page collections enabling objective performance evaluation of different algorithms. Currently, researchers are suffering from the absence of such representative and contemporary test collections, especially on web tables. At the same time, creating your own sharable web page collections is not trivial nowadays because of the dynamic and diverse nature of modern web technologies employed to create often short- lived online content. In this paper, we cover the problem of creating static representations of web pages in order to build sharable ground truth test sets. We explain the principal difficulties of the problem, discuss possible approaches and introduce our solution: WebPageDump, a Firefox extension capable of saving web pages exactly as they are rendered online. Finally, we benchmark our system with current alternatives using an innovative automatic method based on image snapshots. Keywords: saving web pages, web information extraction, test data, Firefox, web table ground truth, performance evaluation 1 Introduction In the visions of a future Semantic Web, agents will crawl the web for information related to a given task. With the current web lacking semantic annotation, researchers are working on automatic information extraction systems that allow transforming heterogonous and semi-structured information into structured databases that can be later queried for data analysis. For testing purposes researchers need representative and annotated ground truth test data sets in order to benchmark different extraction algorithms against each other. -

Digicult.Info Issue 6
.Info Issue 6 A Newsletter on Digital Culture ISSN 1609-3941 December 2003 INTRODUCTION his is a rich issue of DigiCULT.Info covering topics in such Tareas as digitisation, asset management and publication, virtual reality, documentation, digital preservation, and the development of the knowledge society. n October the Italian Presidency of the European Union pro- Imoted, in cooperation with the European Commission and the ERPANET (http://www.erpanet.org) and MINERVA Continued next page (UofGlasgow),© HATII Ross, Seamus 2003 Technology explained and applied ... Challenges, strategic issues, new initiatives ... 6 3D-ArchGIS:Archiving Cultural Heritage 16 New Open-source Software for Content in a 3D Multimedia Space and Repository Management 10 Zope at Duke University: Open Source Content 19 The IRCAM Digital Sound Archive in Context Management in a Higher Education Context 55 Towards a Knowledge Society 16 PLEADE – EAD for the Web 31 Metadata Debate:Two Perspectives on Dublin Core News from DigiCULT´s Regional Correspondents ... 34 Cistercians in Yorkshire: Creating a Virtual Heritage Learning Package 37 Bulgaria 45 SMIL Explained 38 Czech Republic 47 Finding Names with the Autonom Parser 40 France 49 The Object of Learning:Virtual and Physical 41 Greece Cultural Heritage Interactions 42 Italy News, events ... 44 Poland 44 Serbia and Montenegro 23 Delivering The Times Digital Archive 30 NZ Electronic Text Centre 37 Cultural Heritage Events Action in the Preservation of Memory ... 52 New Project Highlights the Growing Use of DOIs 24 PANDORA,Australia’s -
Securecrt 7.3.6 Crack for Mac >>>
Securecrt 7.3.6 Crack For Mac >>> http://shurll.com/77o35 1 / 5 2 / 5 hash,,47850D6A1C717CEC4534B14525ED9BF2292DD905,,... VanDyke,,SecureCRT,,and,,SecureFX,,7 .3.6,,[Mac,,Os,,X],,[MAC599],,DOWNLOAD,,TORRENTSecureCRT,,for,,Mac,,OS,,X,,7.1... VanDyke,,Secu reCRT,,and,,SecureFX,,7.3.6,,[Mac,,Os,,X].torrent,,내부,,파일,,..Turn,,,your,,,computer,,,into,,,a,,,terminal,, ,server,,,using,,,Serial,,,to,,,Ethernet,,,Converter,,,with,,,its,,,amazing,,,capability,,,to,,,share,,,serial,,, devices,,,in,,,... Free,,,Download,,,SecureCRT,,,for,,,Mac,,,8.1.3,,,Build,,,1382,,,-,,,A,,,fully-featured,,,te rminal,,,emulator,,,as,,,well,,,as,,,a,,,SSH,,,and,,,Telnet,,,client,,,with,,,advanced,,,session,,,mana... Do wnload,,,VanDyke,,,SecureCRT,,,and,,,SecureFX,,,7.3.6,,,[Mac,,,Os,,,X],,,[MAC599],,,torrent,,,or,,,any,, ,other,,,torrent,,,from,,,Mac,,,category. SecureCRT®,,,7.3.6.963,,,for,,,MAC,,,|,,,40.7MbUsers,,,with,,,PCs,,,installed,,,with,,,Windows,,,8. Secu reCRT,,,provides,,,rock-solid,,,terminal,,,emulation,,,for,,,computing,,,professionals,,,,raising,,,product ivity,,,with,,,advanced,,,session,,,management,,,and,,,a,,,host,,,of,,,ways,,,to,,,save SecureCRT,,,for,,, Mac,,,,free,,,and,,,safe,,,downloadSecureCRT,,,supports,,,SSH2,,,,SSH1,,,,Telnet,,,,Telnet/SSL,,,,Serial, ,,,and,,,other,,,protocols..It,,,has,,,been,,,designed,,,to,,,be,,,used,,,during,,,the,,,high,,,stress,,,produc tion,,,... Torrentz,,,-,,,Fast,,,and,,,convenient,,,Torrents,,,Search,,,EngineApowersoft,,Screen,,Capture, ,Pro,,1.3.1,,InclTurn,,your,,computer,,into,,a,,terminal,,server,,using,,Serial,,to,,Ethernet,,Converter,, -

Paradise Lost , Book III, Line 18
_Paradise Lost_, book III, line 18 %%%%%%%%%%%%%%%%%%%%%%%% ++++++++++Hacker's Encyclopedia++++++++ ===========by Logik Bomb (FOA)======== <http://www.xmission.com/~ryder/hack.html> ---------------(1997- Revised Second Edition)-------- ##################V2.5################## %%%%%%%%%%%%%%%%%%%%%%%% "[W]atch where you go once you have entered here, and to whom you turn! Do not be misled by that wide and easy passage!" And my Guide [said] to him: "That is not your concern; it is his fate to enter every door. This has been willed where what is willed must be, and is not yours to question. Say no more." -Dante Alighieri _The Inferno_, 1321 Translated by John Ciardi Acknowledgments ---------------------------- Dedicated to all those who disseminate information, forbidden or otherwise. Also, I should note that a few of these entries are taken from "A Complete List of Hacker Slang and Other Things," Version 1C, by Casual, Bloodwing and Crusader; this doc started out as an unofficial update. However, I've updated, altered, expanded, re-written and otherwise torn apart the original document, so I'd be surprised if you could find any vestiges of the original file left. I think the list is very informative; it came out in 1990, though, which makes it somewhat outdated. I also got a lot of information from the works listed in my bibliography, (it's at the end, after all the quotes) as well as many miscellaneous back issues of such e-zines as _Cheap Truth _, _40Hex_, the _LOD/H Technical Journals_ and _Phrack Magazine_; and print magazines such as _Internet Underground_, _Macworld_, _Mondo 2000_, _Newsweek_, _2600: The Hacker Quarterly_, _U.S. News & World Report_, _Time_, and _Wired_; in addition to various people I've consulted. -

Capitol Murder
CAPITOL MURDER A THESIS SUBMITTED TO THE GRADUATE DIVISION OF THE UNIVERSITY OF HAWAI‘I AT MĀNOA IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF ARTS IN ENGLISH DECEMBER 2012 By Sara M. K. Young Thesis Committee: Rodney Morales, Chairperson Cynthia Franklin Gary Pak ACKNOWLEDGMENTS I would like to thank the following people for their assistance with my thesis: Kai Lau, for providing his knowledge of information technology systems; Gary Pak and Cynthia Franklin, for their instruction and participation; Instructor Shawna Yang Ryan and my ENG 613C Fiction Workshop classmates for Spring and Fall 2012, for their commentary and feedback on my workshop drafts; Rodney Morales, for his literary guidance, mentorship, and overall advice; and Marcus Hayden, for his continuous encouragement and support. i TABLE OF CONTENTS ACKNOWLEDGMENTS ................................................................................................... i PROLOGUE ....................................................................................................................... 1 CHAPTER 1 ....................................................................................................................... 6 CHAPTER 2 ..................................................................................................................... 27 CHAPTER 3 ..................................................................................................................... 52 CHAPTER 4 .................................................................................................................... -

Linux Networking Cookbook.Pdf
Linux Networking Cookbook ™ Carla Schroder Beijing • Cambridge • Farnham • Köln • Paris • Sebastopol • Taipei • Tokyo Linux Networking Cookbook™ by Carla Schroder Copyright © 2008 O’Reilly Media, Inc. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (safari.oreilly.com). For more information, contact our corporate/institutional sales department: (800) 998-9938 or [email protected]. Editor: Mike Loukides Indexer: John Bickelhaupt Production Editor: Sumita Mukherji Cover Designer: Karen Montgomery Copyeditor: Derek Di Matteo Interior Designer: David Futato Proofreader: Sumita Mukherji Illustrator: Jessamyn Read Printing History: November 2007: First Edition. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. The Cookbook series designations, Linux Networking Cookbook, the image of a female blacksmith, and related trade dress are trademarks of O’Reilly Media, Inc. Java™ is a trademark of Sun Microsystems, Inc. .NET is a registered trademark of Microsoft Corporation. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. -
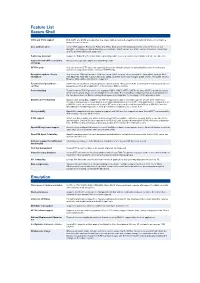
Feature List Secure Shell
Feature List Secure Shell SSH1 and SSH2 support Both SSH1 and SSH2 are supported in a single client, providing the maximum in flexibility when connecting to a range of remote servers. User authentication SecureCRT supports Password, Public Key (RSA, DSA, and X.509 including Smart Cards), Kerberos v5 (via GSSAPI), and Keyboard Interactive when connecting to SSH2 servers. For SSH1 servers, Password, Public Key, and TIS authentications are supported. Public Key Assistant Support for Public Key Assistant makes uploading public keys to an SSH2 server simple and safe for end users. Support for GSSAPI secured key Mechanisms supported depend on GSSAPI provider. exchange SFTP in a tab You can open an SFTP tab to the same SSH2 session without having to re-authenticate to perform file transfer operations using an interactive, text-based SFTP utility. Encryption ciphers: Strong The maximum 2048 bits length of DSA keys under SSH2 provides strong encryption. SecureCRT supports AES- encryption 128, AES-192, AES-256, Twofish, Blowfish, 3DES, and RC4 when connecting to SSH2 servers. For SSH1 servers, Blowfish, DES, 3DES, and RC4 are supported. Password and passphrase SSH2 session passwords and passphrases can be cached, letting SecureCRT and SecureFX share passwords and caching passphrases while either application or the Activator utility is running. Port forwarding Tunnel common TCP/IP protocols (for example, POP3, IMAP4, HTTP, SMTP) via SecureCRT to a remote Secure Shell server using a single, secure, multiplexed connection. Port forwarding configuration has been integrated into the tree-based Session Options dialog allowing easier configuration for securing TCP/IP application data. Dynamic port forwarding Dynamic port forwarding simplifies how TCP/IP application data is routed through the Secure Shell connection. -

Google Apps for Education Surpasses Expectations at ICHS Contents
Summer 2013 Working With New Technologies Vol. 11, No. 2 Google Apps for Education Surpasses Expectations at ICHS By Amy B. Popp, Librar- Google Apps for Education ian, Webmaster, PR Coor- (www.google.com/enterprise/ apps/education) has fulfilled all of dinator, and Technology these requirements. Teacher at Immaculate Conception High School I had heard about Gmail being used as an email solution for edu- Immaculate Conception High cational and nonprofit organiza- School (ICHS), a Catholic co- tions. Through research, emails, educational school in Mont- and phone calls with Google, I clair, has been transformed found that our school qualified for by the implementation of the free Google Apps for Educa- Google Apps for Education. tion program. We could retain our When I was hired as Librar- email domain name ian/Webmaster in 2011, one ICHS juniors work in Popp’s (Continued on page 4) of my primary goals was to computer class: Joselyn update the content, media, Espinoza (front), Myrna Nu- functionality, and visibility of arhpa, Garyetta Vanderveer. the school’s website. As I revamped the website, I everyone in the school com- Contents noticed that the school's munity to communicate with email system was outdated, each other effectively. In addi- clunky, and barely used. It Google Apps for Education tion, students needed to col- Surpasses Expectations needed to be replaced by laborate, share, and retrieve something that would enable at ICHS 1 their work more effectively. How iPad Stations Support Early Childhood Learning 1 Message from How iPad Stations Support the President 2 Letter from the Early Childhood Learning Executive Director 3 Note from the Editor 3 By Jennifer Salt, Senior and benefits of creating an Children’s Librarian, early childhood tech station Use TechEx to Share using tablet computers. -

Secure Configuration and Management of Linux Systems
Secure Configuration and Management of Linux Systems using a Network Service Orchestrator Vijay Satti A Thesis in The Department of Concordia Institute for Information Systems Engineering Presented in Partial Fulfillment of the Requirements for the Degree of Master of Applied Science at Concordia University Montréal, Québec, Canada May 2019 c Vijay Satti, 2019 CONCORDIA UNIVERSITY School of Graduate Studies This is to certify that the thesis prepared By: Vijay Satti Entitled: Secure Configuration and Management of Linux Systems using a Network Service Orchestrator and submitted in partial fulfillment of the requirements for the degree of Master of Applied Science complies with the regulations of this University and meets the accepted standards with respect to originality and quality. Signed by the Final Examining Committee: Chair Dr. Walter Lucia Examiner Dr. Anjali Agarwal Examiner Dr. Amr Youssef Supervisor Dr. J. William Atwood Approved by Dr. Chadi Assi, Graduate Program Director Department of Concordia Institute for Information Systems Engineering 2019 Dr. Amir Asif, Dean Faculty of Engineering and Computer Science Abstract Secure Configuration and Management of Linux Systems using a Network Service Orchestrator Vijay Satti Manual management of the configuration of network devices and computing devices (hosts) is an error-prone task. Centralized automation of these tasks can lower the costs of management, but can also introduce unknown or unanticipated security risks. Miscon- figuration (deliberate (by outsiders) or inadvertent (by insiders)) can expose a system to significant risks. Centralized network management has seen significant progress in recent years, result- ing in model-driven approaches that are clearly superior to previous "craft" methods. Host management has seen less development.