Technology and Engineering International Journal of Recent
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
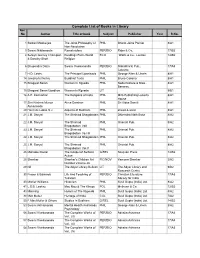
Complete List of Books in Library Acc No Author Title of Book Subject Publisher Year R.No
Complete List of Books in Library Acc No Author Title of book Subject Publisher Year R.No. 1 Satkari Mookerjee The Jaina Philosophy of PHIL Bharat Jaina Parisat 8/A1 Non-Absolutism 3 Swami Nikilananda Ramakrishna PER/BIO Rider & Co. 17/B2 4 Selwyn Gurney Champion Readings From World ECO `Watts & Co., London 14/B2 & Dorothy Short Religion 6 Bhupendra Datta Swami Vivekananda PER/BIO Nababharat Pub., 17/A3 Calcutta 7 H.D. Lewis The Principal Upanisads PHIL George Allen & Unwin 8/A1 14 Jawaherlal Nehru Buddhist Texts PHIL Bruno Cassirer 8/A1 15 Bhagwat Saran Women In Rgveda PHIL Nada Kishore & Bros., 8/A1 Benares. 15 Bhagwat Saran Upadhya Women in Rgveda LIT 9/B1 16 A.P. Karmarkar The Religions of India PHIL Mira Publishing Lonavla 8/A1 House 17 Shri Krishna Menon Atma-Darshan PHIL Sri Vidya Samiti 8/A1 Atmananda 20 Henri de Lubac S.J. Aspects of Budhism PHIL sheed & ward 8/A1 21 J.M. Sanyal The Shrimad Bhagabatam PHIL Dhirendra Nath Bose 8/A2 22 J.M. Sanyal The Shrimad PHIL Oriental Pub. 8/A2 Bhagabatam VolI 23 J.M. Sanyal The Shrimad PHIL Oriental Pub. 8/A2 Bhagabatam Vo.l III 24 J.M. Sanyal The Shrimad Bhagabatam PHIL Oriental Pub. 8/A2 25 J.M. Sanyal The Shrimad PHIL Oriental Pub. 8/A2 Bhagabatam Vol.V 26 Mahadev Desai The Gospel of Selfless G/REL Navijvan Press 14/B2 Action 28 Shankar Shankar's Children Art FIC/NOV Yamuna Shankar 2/A2 Number Volume 28 29 Nil The Adyar Library Bulletin LIT The Adyar Library and 9/B2 Research Centre 30 Fraser & Edwards Life And Teaching of PER/BIO Christian Literature 17/A3 Tukaram Society for India 40 Monier Williams Hinduism PHIL Susil Gupta (India) Ltd. -

JUGGLING His Way Into Adland
March 16-31, 2012 Volume 3, Issue 6 `100 29 DEFINING MOMENTS Shripad Kulkarni Statistical highlights about Allied Media’s CEO. 34 GUJARAT Regional Touch Gujarat Tourism brands a train in Delhi. 37 26 TELEVISION PROFILE Soumitra Karnik The copywriter who fought JUGGLING his way into adland. AXIS BANK Partner in Progress 18 SCHEDULES MIRINDA A good scheduler has to be an even better juggler. A New Mob 20 Slotting the right programme at the right time could be the IRS Q4 2011 difference between success and obscurity. Report Card 30 SAHARA ONE Spot Selling 32 EDITORIAL This fortnight... Volume 3, Issue 6 EDITOR Sreekant Khandekar n the early days of Doordarshan, the television viewer would adjust his day’s plan in accordance PUBLISHER Iwith television programmes. So, an ideal family would wait to finish dinner post the Hindi news Prasanna Singh bulletin at 9 pm or take a tea-break during the interval of the Sunday evening movie. EXECUTIVE EDITOR Prajjal Saha However, today’s television viewers are an evolved species. Today, a channel has SENIOR LAYOUT ARTIST to plan the timing of its shows depending on – hopefully - when the viewer would Vinay Dominic March 16-31, 2012 Volume 3, Issue 6 100 like to watch it. Good content armed with equally aggressive marketing strategies LOGISTICS ` 29 could be a waste if it’s wrongly placed against a show or aired in a wrong time slot. Rajesh Kanwal ADVERTISING ENQUIRIES Channel executives today rack their brains for hours to decide whether to put a Neha Arora, (0120) 4077866, 4077837 DEFINING MOMENTS Shripad Kulkarni Statistical highlights about Noida Allied Media’s CEO. -

Profile of Research Work
Profile of Research Work (Upto March, 2017) Dr. Pravinkumar N. Chougule M.A., NET, M.Phil., Ph.D. Assistant Professor, Department of Hindi, Smt.Kasturbai Walchand College (Arts-Science), Sangli. Rajnemi Campus, Wood House Road, Sangli - 416 416. Phone : 0233-2372102, E-mail : [email protected] Highlights of the Research Work Name :- Dr. Pravinkumar N. Chougule Designation :- Assistant Professor, Dept. of Hindi, Smt. Kasturbai Walchand College, Sangli Rajnemi Campus, North Shivaji Nagar, Sangli. Address :- Flat No. 3 & 5, ‘Shivdarshan’ Apartment, North Shivaji Nagar, Sangli. Pin Code – 416 416. Tal:-Miraj Dist:- Sangli. Contact No :- Office :- 0233-2327128 Cell :- 9881814116 E-mail ID :- [email protected] Date of Birth :- 17th May, 1981. Edu. Qualification :- M.A., NET, M. Phil., Ph.D. Subject :- Hindi Teaching Experience :- 09 Years. Minor Research Project :- 1 (Completed), Publications :- 1. International / National / State Level Article - 25 2. Paper Presentation - 36 Radio Programme :- Sangli - 02 Guest Lecture :- 04 Member Body:- 1. Member of Mahatrashtra Hindi Professor Association, Shivaji University Hindi Professor Association & Dakshin Bharat Jain Sabha. A) ACADEMIC QUALIFICATIONS :- Sr. Examination Year Board/University Grade % No. 1. S. S. C. 1997 Kolhapur Board 69.06 % 2. H. S. C. 2000 Kolhapur Board 52.17% 3. B. A. 2003 Shivaji University, Kolhapur 55.72 % 4. M. A. 2005 Shivaji University, Kolhapur 55.63 % 5. NET 2005 UGC – WRO, Pune Pass 5. M. Phil. 2007 Shivaji University, Kolhapur “A” 6. Ph. D. 2014 Shivaji University, Kolhapur ---- Title of Ph.D. Thesis :- “Adhunik Hindi Mahakavyo Me Chitrit Mahatma Gandhi” B) ADDITIONAL :- (Refresher Courses and Training) QUALIFICATION Sr. Year Place Subject Specialization No. -

Literary Criticism and Literary Historiography University Faculty
University Faculty Details Page on DU Web-site (PLEASE FILL THIS IN AND Email it to [email protected] and cc: [email protected]) Title Prof./Dr./Mr./Ms. First Name Ali Last Name Javed Photograph Designation Reader/Associate Professor Department Urdu Address (Campus) Department of Urdu, Faculty of Arts, University of Delhi, Delhi-7 (Residence) C-20, Maurice Nagar, University of Delhi, Delhi-7 Phone No (Campus) 91-011-27666627 (Residence)optional 27662108 Mobile 9868571543 Fax Email [email protected] Web-Page Education Subject Institution Year Details Ph.D. JNU, New Delhi 1983 Thesis topic: British Orientalists and the History of Urdu Literature Topic: Jaafer Zatalli ke Kulliyaat ki M.Phil. JNU, New Delhi 1979 Tadween M.A. JNU, New Delhi 1977 Subjects: Urdu B.A. University of Allahabad 1972 Subjects: English Literature, Economics, Urdu Career Profile Organisation / Institution Designation Duration Role Zakir Husain PG (E) College Lecturer 1983-98 Teaching and research University of Delhi Reader 1998 Teaching and research National Council for Promotion of Director April 2007 to Chief Executive Officer of the Council Urdu Language, HRD, New Delhi December ’08 Research Interests / Specialization Research interests: Literary criticism and literary historiography Teaching Experience ( Subjects/Courses Taught) (a) Post-graduate: 1. History of Urdu Literature 2. Poetry: Ghalib, Josh, Firaq Majaz, Nasir Kazmi 3. Prose: Ratan Nath Sarshar, Mohammed Husain Azad, Sir Syed (b) M. Phil: Literary Criticism Honors & Awards www.du.ac.in Page 1 a. Career Awardee of the UGC (1993). Completed a research project entitled “Impact of Delhi College on the Cultural Life of 19th Century” under the said scheme. -

Designation: Assistant Professor Address (O): Department of Hindi, Assam University, Silchar- 788011, Assam
SHEETANSHU KUMAR (A Brief Profile) Designation: Assistant Professor Address (O): Department of Hindi, Assam University, Silchar- 788011, Assam. Contact: 09435173696 E.mail: [email protected] , [email protected] Specialization: Historiography of Literature, 19th Century Hindi Literature. Criticism, Orientalism. Post-Graduation: M.A (Hindi), M.A. (English). Research Work: M.Phil Dissertation: ‘Fort William College aur Hindi Bhasha’ (J.N.U., New Delhi.) Ph.D. Thesis: ‘British Prachyawad aur Hindi Sahityetihas Lekhan ki Avdharnayien’ (C.U., Kolkata) Publication: Selected Papers 1. Ummed Jo Taqleef Jaisi Hai, Vagarth, Bhartiya Bhasha Parishad, Kolkata, 2009. 2. John Borthwick Gilchrist ki Bhasha Niti, Sankalp, Journal of the Hindi Dept., Calcutta University, Volume 9, 2009. 3. Fort William College ki Bhasha Niti aur Willim Price, Gaveshna, Journal of the Central Hindi Institute (MHRD, Govt. of India.), Volume 95/96, 2010. 4. Hindi Sahitya ki Parampara ki Chinta, Samuchchay, Journal of English and Foreign Languages University, Hyderabad, volume 2, 2011. 5. East India Company ki Bhasha Niti aur Prachyawad, Anusandhan, Journal of the Hindi Department, Allahabad University, Vol 8, year 8, 2012. 6. Edward Said ke Marx aur Ramvilas Sharma, Aroh, Journal of Hindi department, Assam University, 2013. 7. Aparichitikaran ke daur mein Nagarjun, Prasthan, Gorakhpur, 2013. 8. Hindi Urdu ek Bar Fir, Bhasha Vimarsh, Kolkata, 2014. 9. Vaishwikaran aur Dalit Sahitya, E-PG Pathshala, INFLIBNET, UGC, New Delhi, 2014 10. Prachyawad aur Ramvilas Sharma ka Jones Path, Vasudha, Bhopal, 2015 11. Garcin Da Tassy ke Itihas mein: Bhasha ke Tarazu par Dharm ka Pasang, Mantavya, Lucknow, 2015 12. Vaishwikaran aur dalit prashn, Baya, Delhi, 2015 13. -

Of Contemporary India
OF CONTEMPORARY INDIA Catalogue Of The Papers of Prabhakar Machwe Plot # 2, Rajiv Gandhi Education City, P.O. Rai, Sonepat – 131029, Haryana (India) Dr. Prabhakar Machwe (1917-1991) Prolific writer, linguist and an authority on Indian literature, Dr. Prabhakar Machwe was born on 26 December 1917 at Gwalior, Madhya Pradesh, India. He graduated from Vikram University, Ujjain and obtained Masters in Philosophy, 1937, and English Literature, 1945, Agra University; Sahitya Ratna and Ph.D, Agra University, 1957. Dr. Machwe started his career as a lecturer in Madhav College, Ujjain, 1938-48. He worked as Literary Producer, All India Radio, Nagpur, Allahabad and New Delhi, 1948-54. He was closely associated with Sahitya Akademi from its inception in 1954 and served as Assistant Secretary, 1954-70, and Secretary, 1970-75. Dr. Machwe was Visiting Professor in Indian Studies Departments at the University of Wisconsin and the University of California on a Fulbright and Rockefeller grant (1959-1961); and later Officer on Special Duty (Language) in Union Public Service Commission, 1964-66. After retiring from Sahitya Akademi in 1975, Dr. Machwe was a visiting fellow at the Institute of Advanced Studies, Simla, 1976-77, and Director of Bharatiya Bhasha Parishad, Calcutta, 1979-85. He spent the last years of his life in Indore as Chief Editor of a Hindi daily, Choutha Sansar, 1988-91. Dr. Prabhakar Machwe travelled widely for lecture tours to Germany, Russia, Sri Lanka, Mauritius, Japan and Thailand. He organised national and international seminars on the occasion of the birth centenaries of Mahatma Gandhi, Rabindranath Tagore, and Sri Aurobindo between 1961 and 1972. -

Genre Channel Name Channel No Hindi Entertainment Star Bharat 114 Hindi Entertainment Investigation Discovery HD 136 Hindi Enter
Genre Channel Name Channel No Hindi Entertainment Star Bharat 114 Hindi Entertainment Investigation Discovery HD 136 Hindi Entertainment Big Magic 124 Hindi Entertainment Colors Rishtey 129 Hindi Entertainment STAR UTSAV 131 Hindi Entertainment Sony Pal 132 Hindi Entertainment Epic 138 Hindi Entertainment Zee Anmol 140 Hindi Entertainment DD National 148 Hindi Entertainment DD INDIA 150 Hindi Entertainment DD BHARATI 151 Infotainment DD KISAN 152 Hindi Movies Star Gold HD 206 Hindi Movies Zee Action 216 Hindi Movies Colors Cineplex 219 Hindi Movies Sony Wah 224 Hindi Movies STAR UTSAV MOVIES 225 Hindi Zee Anmol Cinema 228 Sports Star Sports 1 Hindi HD 282 Sports DD SPORTS 298 Hindi News ZEE NEWS 311 Hindi News AAJ TAK HD 314 Hindi News AAJ TAK 313 Hindi News NDTV India 317 Hindi News News18 India 318 Hindi News Zee Hindustan 319 Hindi News Tez 326 Hindi News ZEE BUSINESS 331 Hindi News News18 Rajasthan 335 Hindi News Zee Rajasthan News 336 Hindi News News18 UP UK 337 Hindi News News18 MP Chhattisgarh 341 Hindi News Zee MPCG 343 Hindi News Zee UP UK 351 Hindi News DD UP 400 Hindi News DD NEWS 401 Hindi News DD LOK SABHA 402 Hindi News DD RAJYA SABHA 403 Hindi News DD RAJASTHAN 404 Hindi News DD MP 405 Infotainment Gyan Darshan 442 Kids CARTOON NETWORK 449 Kids Pogo 451 Music MTV Beats 482 Music ETC 487 Music SONY MIX 491 Music Zing 501 Marathi DD SAHYADRI 548 Punjabi ZEE PUNJABI 562 Hindi News News18 Punjab Haryana Himachal 566 Punjabi DD PUNJABI 572 Gujrati DD Girnar 589 Oriya DD ORIYA 617 Urdu Zee Salaam 622 Urdu News18 Urdu 625 Urdu -

MSO Name:- STAR CLUB
MSO Name:- STAR CLUB Sl No Name Broadcaster Genre Language 1 TRAI INFO @STAR CLUB FTA OTHERS BENGALI 2 SAHARA MP FTA REGIONAL Hindi 3 SAHARA UP FTA REGIONAL Hindi 4 SAHARA MUMBAI FTA REGIONAL Hindi 5 SKYSTAR TELEGU FTA REGIONAL Telugu 6 DD RANCHI FTA REGIONAL Hindi 7 DD RAJASTHAN FTA REGIONAL Hindi 8 DD NORTH EAST FTA REGIONAL Hindi 9 DD RAIPUR FTA REGIONAL Hindi 10 DD MP FTA REGIONAL Hindi 11 DD UP FTA REGIONAL Hindi 12 DD DEHRADUN FTA REGIONAL Hindi 13 DD KOHIMA FTA REGIONAL Hindi 14 DD AIZWAL FTA REGIONAL Hindi 15 DD IMPHAL FTA REGIONAL Hindi 16 DD ARUNPRABHA FTA REGIONAL Hindi 17 DD KASHIR FTA REGIONAL Hindi 18 DD GIRNAR FTA REGIONAL Telugu 19 DD CHANDANA FTA REGIONAL Telugu 20 PRATIDIN TIME FTA REGIONAL BENGALI 21 TAZA TV FTA REGIONAL Hindi 22 HARIYANA NEWS FTA REGIONAL Hindi 23 AAHO MUSIC FTA REGIONAL PUNJABI 24 SANDAR CINEMA FTA REGIONAL BHOHPURI 25 ANJAN TV FTA REGIONAL BHOHPURI 26 BHAKTI SAGAR 2 FTA BHAKTI Hindi 27 SUBHA CINEMA FTA BHAKTI Hindi 28 SUBHA TV FTA BHAKTI Hindi 29 SURIYA BHAKTI FTA BHAKTI Hindi 30 SADHANA BHAKTI FTA BHAKTI Hindi 31 VAIDEK FTA BHAKTI Hindi 32 HARE KRISHNA FTA BHAKTI Hindi 33 FOOD FOOD FTA LIFE STYLE Hindi 34 SAHARA NCR FTA HINDI NEWS Hindi 35 SHOW BOX FTA HINDI MUSIC Hindi 36 M TUNE SD FTA HINDI MUSIC Hindi 37 ZINGAAT FTA HINDI MOVIES Hindi 38 MANORANJAN GRAND FTA HINDI MOVIES Hindi 39 MULTIPLEX FTA HINDI MOVIES Hindi 40 HOUSEFULL ACTION FTA HINDI MOVIES Hindi 41 MOVIE PLUS FTA HINDI MOVIES Hindi 42 BFLIX MOVIES FTA HINDI MOVIES Hindi 43 WOW CINEMA FTA HINDI MOVIES Hindi 44 DD INDIA FTA HINDI ENTERTAINMENT -

ALL INDIA INSTITUTE of MEDICAL SCIENCES Ansari Nagar, New Delhi - 110608
ALL INDIA INSTITUTE OF MEDICAL SCIENCES Ansari Nagar, New Delhi - 110608 ALL INDIA ENTRANCE EXAMINATION FOR ADMISSION TO MD/MS/DIPLOMA AND MDS COURSES - 2011 RESULT NOTIFICATION NO. 14/2011 The following is the list of candidates who have qualified for MD/MS/Diploma and MDS courses for admission to various Medical/Dental Colleges/Institutions in India against 50% seats quota on the basis of All India Entrance Examination held on Sunday, the 9th January, 2011. In pursuance to Directorate General of Health Services (Medical Examination Cell) Letter No. U-12021/29/2010-MEC dated 11th Feb., 2011, the list is category and roll number wise and the respective category rank is given in parenthesis against each roll number. The admission is subject to verification of eligibility criteria & original documents as given in the Prospectus. The Institute is not responsible for any printing error. The allocation of subject and Medical College will be done by the Directorate General of Health Services as per revised counselling schedule available on website of Ministry of Health & Family Welfare namely www.mohfw.nic.in. Individual intimation in this respect is being sent separately. Result is displayed on the notice board of Examination Section, AIIMS, New Delhi and is also available on web sites www.aiims.ac.in, www.aiims.edu and www.aiimsexams.org which include category and over all rank of the candidates. MD/MS/DIPLOMA COURSES Roll No. Name Category Over all Rank Category Rank 1100002 Harsh Jayantkumar Shah UR 1643 1619 1100006 Senthilnathan M UR -
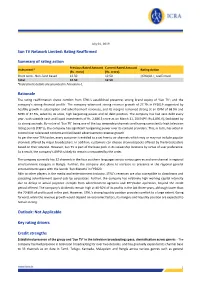
Sun TV Network Limited: Rating Reaffirmed Summary of Rating Action
July 01, 2019 Sun TV Network Limited: Rating Reaffirmed Summary of rating action Previous Rated Amount Current Rated Amount Instrument* Rating Action (Rs. crore) (Rs. crore) Short term - Non-fund based 12.50 12.50 [ICRA]A1+; reaffirmed Total 12.50 12.50 *Instrument details are provided in Annexure-1 Rationale The rating reaffirmation draws comfort from STNL’s established presence; strong brand equity of ‘Sun TV’; and the company’s strong financial profile. The company witnessed strong revenue growth of 27.7% in FY2019 supported by healthy growth in subscription and advertisement revenues, and its margins remained strong at an OPM of 68.9% and NPM of 37.5%, aided by its scale, high bargaining power and nil debt position. The company has had zero debt every year, with sizeable cash and liquid investments of Rs. 2,686.5 crore as on March 31, 2019 (PY: Rs,1,896.9), facilitated by its strong accruals. By virtue of ‘Sun TV’ being one of the top viewership channels and having consistently high television rating points (TRP’s), the company has significant bargaining power over its content providers. This, in turn, has aided in control over telecasted content and facilitated advertisement revenue growth. As per the new TRAI order, every customer is entitled to a set free to air channels which may or may not include popular channels offered by major broadcasters. In addition, customers can choose channels/packs offered by the broadcasters based on their interest. However, Sun TV is part of the base pack in its viewership locations by virtue of user preference. -

The Funeral of Mr. Wang Examines Social Change in Urbanizing China Through the Lens of Funerals, the Funerary Industry, and Practices of Memorialization
KIPNIS ANTHROPOLOGY | ASIAN STUDIES In rural China funerals are conducted locally, on village land by village elders. But in urban areas, people have neither land for burials nor elder relatives to conduct funerals. Chinese urbanization, which has increased drastically in recent decades, involves the creation of cemeteries, state-run funeral homes, WANG OF MR. FUNERAL THE and small private funerary businesses. The Funeral of Mr. Wang examines social change in urbanizing China through the lens of funerals, the funerary industry, and practices of memorialization. It analyzes changes in family life, patterns of urban sociality, transformations in economic relations, the politics of memorialization, and the echoes of these changes in beliefs about the dead and ghosts. “This book is highly original and addresses a topic of central importance to understanding Chinese family life and the limits of a party-state’s regulatory THE FUNERAL OF MR. WANG power over the society and individual citizens. Original and systematic field- work is expertly used to illustrate core arguments. To my knowledge there is no competing ethnography.” LIFE, DEATH, AND GHOSTS IN URBANIZING CHINA Deborah Davis, Professor Emerita of Sociology, Yale University ANDREW B. KIPNIS “The Funeral of Mr. Wang is a vivid portrait of how the transition from life to death is negotiated in the midst of a rapidly transforming urban Chinese so- ciety. Showing how death in contemporary China generates interconnected processes of cultural recombination among family members, funeral service providers, bureaucratic regulators, strangers, and ghosts, this book will be crit- ical reading for all students of China and of death in contemporary societies.” David A. -

Hathway Fta Pack
HATHWAY FTA PACK DELHI DELHI FTA Total Channels 142 SD + 0 HD LANG - GENRE CHANNEL_NAME SD/HD Assamese - Gec DD ArunPrabha SD Assamese - Gec DD ASSAM SD Assamese - News PRAG NEWS SD Bengali - Gec AAKASH AATH SD Bengali - Gec DD BANGLA SD Bengali - Gec RUPASI BANGLA SD Bengali - Movie ENTERR10 MOVIES SD Bengali - Music SANGEET BANGLA SD Bengali - News ABP ANANDA SD Bhojpuri - Gec DANGAL SD Bhojpuri - Movie BHOJPURI CINEMA SD Bhojpuri - Movie PITAARA SD Bhojpuri - Movie SURYA BHOJPURI SD Bhojpuri - Music SANGEET BHOJPURI SD English - Devotional PEACE OF MIND SD English - Lifestyle FASHION TV SD English - News REPUBLIC TV SD Gujarati - Gec DD GIRNAR SD Haryanvi - Gec RAGNI SPECIAL SD Haryanvi - Music APNA HARYANA SD Hindi - Devotional AASTHA SD Hindi - Devotional AASTHA BHAJAN SD Hindi - Devotional ARIHANT SD Hindi - Devotional DIVINE SD Hindi - Devotional HARE KRSNA TV SD Hindi - Devotional HINDU DHARMAM SD Hindi - Devotional LORD BUDDHA TV SD Hindi - Devotional PARAS SD Hindi - Devotional SANSKAR SD Hindi - Devotional SATSANG SD Hindi - Devotional SHRADDHA MH ONE SD Hindi - Devotional SHUBHSANDESH SD Hindi - GEC A1TV SD Page 1 of 47 Hindi - Gec ABZY COOL SD Hindi - Gec CCC SD Hindi - Gec DD BIHAR SD Hindi - Gec DD MADHYA PRADESH SD Hindi - Gec DD NATIONAL SD Hindi - Gec DD RAJASTHAN SD Hindi - Gec DD UTTAR PRADESH SD Hindi - GEC DISHUM SD Hindi - Gec ENTERR10 SD Hindi - Gec HATHWAY HARYANVI SD Hindi - GEC KISHORE MANCH SD Hindi - GEC PANINI SD Hindi - GEC SHARDA SD Hindi - GEC SHEMAROO TV SD Hindi - Infotainment DD BHARATI SD Hindi - Infotainment