A Surveillant Platform Study of Microsoft's Xbox
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Smart Home Automation with Linux Smart
CYAN YELLOW MAGENTA BLACK PANTONE 123 C BOOKS FOR PROFESSIONALS BY PROFESSIONALS® THE EXPERT’S VOICE® IN LINUX Companion eBook Available Smart Home Automation with Linux Smart Dear Reader, With this book you will turn your house into a smart and automated home. You will learn how to put together all the hardware and software needed for Automation Home home automation, to control appliances such as your teakettle, CCTV, light switches, and TV. You’ll be taught about the devices you can build, adapt, or Steven Goodwin, Author of hack yourself from existing technology to accomplish these goals. Cross-Platform Game In Smart Home Automation with Linux, you’ll discover the scope and possi- Programming bilities involved in creating a practical digital lifestyle. In the realm of media and Game Developer’s Open media control, for instance, you’ll learn how you can read TV schedules digitally Source Handbook and use them to program video remotely through e-mail, SMS, or a web page. You’ll also learn the techniques for streaming music and video from one machine to another, how to give your home its own Twitter and e-mail accounts for sending automatic status reports, and the ability to remotely control the home Smart Home lights or heating system. Also, Smart Home Automation with Linux describes how you can use speech synthesis and voice recognition systems as a means to converse with your household devices in new, futuristic, ways. Additionally, I’ll also show you how to implement computer-controlled alarm clocks that can speak your daily calendar, news reports, train delays, and local with weather forecasts. -
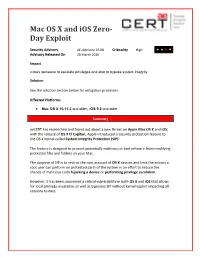
Mac OS X and Ios Zero- Day Exploit
Mac OS X and iOS Zero- Day Exploit Security Advisory AE-Advisory 16-08 Criticality High Advisory Released On 28 March 2016 Impact Allows someone to escalate privileges and also to bypass system integrity Solution See the solution section below for mitigation processes. Affected Platforms Mac OS X 10.11.3 and older, iOS 9.2 and older Summary aeCERT has researched and found out about a new threat on Apple Mac OS X and iOS; with the release of OS X El Capitan, Apple introduced a security protection feature to the OS X kernel called System Integrity Protection (SIP). The feature is designed to prevent potentially malicious or bad software from modifying protected files and folders on your Mac. The purpose of SIP is to restrict the root account of OS X devices and limit the actions a root user can perform on protected parts of the system in an effort to reduce the chance of malicious code hijacking a device or performing privilege escalation. However, it has been uncovered a critical vulnerability in both OS X and iOS that allows for local privilege escalation as well as bypasses SIP without karnel exploit impacting all versions to date. Threat Details The zero day vulnerability is a Non-Memory Corruption bug that allows hackers to execute arbitrary code on any targeted machine, perform remote code execution (RCE) or sandbox escapes. The attacker then escalates the malware's privileges to bypass System Integrity Protection SIP, alter system files, and then stay on the infected system. By default, System Integrity Protection or SIP protects these folders: /System. -
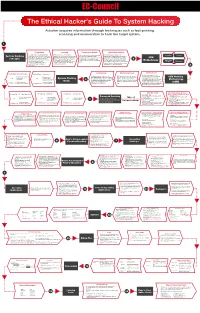
Download the Ethical Hacker's Guide to System Hacking
The Ethical Hacker's Guide To System Hacking Attacker acquires information through techniques such as foot printing, scanning and enumeration to hack the target system. 1 Footprinting Scanning Enumeration Module Vulnerability Analysis It is the process of accumulating data Vulnerability Assessment is an This is a procedure for identifying This is a method of intrusive probing, Footprinting Scanning System Hacking regarding a specific network environment. active hosts, open ports, and unnecessary through which attackers gather examination of the ability of a system or In this phase, the attacker creates a profile services enabled on ports. Attackers use information such as network user lists, application, including current security CEH concepts of the target organization, obtaining different types of scanning, such as port routing tables, security flaws, and procedures, and controls to with stand 2 information such as its IP address range, scanning network scanning, and simple network protocol data (SNMP) assault. Attackers perform this analysis Methodology Vulnerability namespace and employees. Enumeration vulnerability, scanning of target networks data. to identify security loopholes, in the target Analysis Footprinting eases the process of or systems which help in identifying organization’s network, communication system hacking by revealing its possible vulnerabilities. infrastructure, and end systems. vulnerabilities 3 Clearing Logs Maintaining Access Gaining Access Hacking Stage Escalating Privileges Hacking Stage Gaining Access It involves gaining access to To maintain future system access, After gaining access to the target low-privileged user accounts by To acquire the rights of To bypass access CEH Hacking attackers attempt to avoid recognition system, attackers work to maintain cracking passwords through Goal another user or Goal controls to gain System Hacking by legitimate system users. -

WORLDSPECIAL REPORT the Tech Behind Bitcoin Has Been Released
THE INSATIABLE DO YOU NEED THE BLOCK-CHAINING THE MONEY MINES BITCOIN BEAST A BLOCKCHAIN? OF WALL STREET OF MONGOLIA Cryptocurrency’s Find out in seconds A new platform for How watts coming energy crisis with our handy guide trading in the trillions become bitcoins P. 36 P. 38 P. 40 P. 46 FOR THE TECHNOLOGY INSIDER | 10.17 BLOCK- CHAIN WORLD SPECIAL REPORT The tech behind Bitcoin has been released into the wild. Here’s how it’s going to change the landscape P. 24 SUPERMICRO® BigTwin® The IT Industry’s Highest Performing Twin Multi-Node System 2U Multi-Node System Supporting • A Full Range of Processors Up to the highest performing 205 watt CPUs • Maximum Memory 3TB 24 DIMMs per node • All-Flash NVMe 24 All Flash NVMe or Hybrid NVMe/SAS3 drives • Double the I/O Capacity Three PCI-E 3.0 x16 options per node • Supports Intel® Xeon® Scalable Processors Intel Inside®. Powerful Productivity Outside. Learn more at supermicro.com/GPU © Super Micro Computer, Inc. Specifications subject to change without notice. Intel, the Intel logo, Xeon, and Xeon Inside are trademarks or registered trademarks of Intel Corporation in the U.S. and/or other countries. 10.17 Special Report: BLOCKCHAIN WORLD The Blossoming 26 Blockchains: How They 45 Blockchain Lingo Work and Why They’ll Change Your cheat sheet for all things blockchain. of Blockchain the World 24 Enthusiasts The technology behind Bitcoin could touch every 46 Photo Essay: are sure that transaction you ever make. By Morgen E. Peck The Bitcoin Mines of China This Bitcoin operation in Inner Mongolia uses blockchain 36 Feeding the sophisticated semiconductors to turn cheap, dirty technology is Blockchain Beast energy into digital cash. -

Android Exploits Commanding Higher Price Than Ever Before
Memo 10/09/2019 - TLP:WHITE Android exploits commanding higher price than ever before Reference: Memo [190910-1] – Version: 1.0 Keywords: Android, iOS, exploit, vulnerability Sources: Zerodium, Google, Wired Key Points The price of android exploits exceeds the price of iOS exploits for the first time This is possibly because Android security is improving over iOS The release of Android 10 is also a likely cause for the price hike Summary Zerodium1, a cyber security exploit broker dealing in zero-day vulnerabilities, has published its most recent price list. It indicates that the price of an Android full-chain exploit with persistence can fetch the developer up to 2,500,000 dollars. The going rate for a similar exploit for Apple’s iOS has gone down by 500,000 dollars and is now worth 2,000,000. This is the first confirmed time when Android exploits are valued more than iOS. Zerodium payouts for mobile devices Up to $2,500,000 Android zero click full compromise chain with persistence. Up to $2,000,000 iOS zero click full compromise chain with persistence. Up to $1,500,000 WhatsApp zero click remote code execution with iMessage remote code execution with local local privilege escalation on iOS or Android. privilege escalation. Up to $1,000,000 WhatsApp remote code execution with local privilege SMS/MMS remote code execution with local escalation on iOS or Android. privilege escalation on iOS or Android. Comments Zero-click exploits do not require interaction from the user. This is very difficult to achieve and thus commands the highest prices. -

Paper on Xbox Cluster
Building a large low-cost computer cluster with unmodified Xboxes B.J. Guillot, B. Chapman and J.-F. Pâris Department of Computer Science University of Houston Houston, TX, 77204-3010 [email protected], {chapman, paris}@cs.uh.edu Abstract We propose to build a large low-cost computer cluster in order to study error recovery techniques for today and tomorrow’s large computer clusters. The Xbox game console is an inexpensive computer whose internal architecture is very close to that of a conventional Intel-based personal computer. In addition, it can be rebooted as a Linux computing node through software exploits without having to purchase any additional hardware or even opening the Xbox. We built a four-node cluster consisting of four unmodified Xboxes running Debian Linux and found out that a cluster of Xboxes linked by a Fast Ethernet would constitute a scaled down version of a current generation supercomputer with the same number of nodes. As a result, it would provide a cost-effective testbed for investigating novel distributed error-recovery algorithms and testing how they would scale up. Keywords: computer clusters, game console, Linux, distributed error recovery. 1. Introduction Improvements in technology as well as pricing trends have enabled the construction of clusters with increasingly larger node counts. However, the reliability of the cluster decreases in rough correspondence to the number of configured nodes, greatly reducing the attractiveness of such systems, especially for large or long-running jobs. In general, dealing with faults is a matter for the application developer, who must insert checkpoints into each application and thus periodically save all pertinent data. -

Extreme Privilege Escalation on Windows 8/UEFI Systems
Extreme Privilege Escalation on Windows 8/UEFI Systems C o r e y K a l l e n b e r g @ c o r e y k a l X e n o K o v a h @ x e n o k o v a h John Butterworth @jwbutterworth3 Sam Cornwell @ssc0rnwell © 2014 The MITRE Corporation. All rights reserved. | 2 | Introduction . Who we are: – Trusted Computing and firmware security researchers at The MITRE Corporation . What MITRE is: – A not-for-profit company that runs six US Government "Federally Funded Research & Development Centers" (FFRDCs) dedicated to working in the public interest – Technical lead for a number of standards and structured data exchange formats such as CVE, CWE, OVAL, CAPEC, STIX, TAXII, etc – The first .org, !(.mil | .gov | .com | .edu | .net), on the ARPANET © 2014 The MITRE Corporation. All rights reserved. | 3 | Attack Model (1 of 2) . We’ve gained administrator access on a victim Windows 8 machine . But we are still constrained by the limits of Ring 3 © 2014 The MITRE Corporation. All rights reserved. | 4 | Attack Model (2 of 2) . As attackers we always want – More Power – More Persistence – More Stealth © 2014 The MITRE Corporation. All rights reserved. | 5 | Typical Post-Exploitation Privilege Escalation . Starting with x64 Windows vista, kernel drivers must be signed and contain an Authenticode certificate . In a typical post-exploitation privilege escalation, attacker wants to bypass the signed driver requirement to install a kernel level rootkit . Various methods to achieve this are possible, including: – Exploit existing kernel drivers – Install a legitimate (signed), but vulnerable, driver and exploit it . -

Towards Taming Privilege-Escalation Attacks on Android
Towards Taming Privilege-Escalation Attacks on Android Sven Bugiel1, Lucas Davi1, Alexandra Dmitrienko3, Thomas Fischer2, Ahmad-Reza Sadeghi1;3, Bhargava Shastry3 1CASED/Technische Universitat¨ Darmstadt, Germany 2Ruhr-Universitat¨ Bochum, Germany fsven.bugiel,lucas.davi,[email protected] thomas.fi[email protected] 3Fraunhofer SIT, Darmstadt, Germany falexandra.dmitrienko,ahmad.sadeghi,[email protected] Abstract 1. Introduction Android’s security framework has been an appealing sub- Google Android [1] has become one of the most popular ject of research in the last few years. Android has been operating systems for various mobile platforms [23, 3, 31] shown to be vulnerable to application-level privilege esca- with a growing market share [21]. Concerning security and lation attacks, such as confused deputy attacks, and more privacy aspects, Android deploys application sandboxing recently, attacks by colluding applications. While most of and a permission framework implemented as a reference the proposed approaches aim at solving confused deputy at- monitor at the middleware layer to control access to system tacks, there is still no solution that simultaneously addresses resources and mediate application communication. collusion attacks. The current Android business and usage model allows developers to upload arbitrary applications to the Android In this paper, we investigate the problem of designing and app market1 and involves the end-user in granting permis- implementing a practical security framework for Android to sions to applications at install-time. This, however, opens protect against confused deputy and collusion attacks. We attack surfaces for malicious applications to be installed on realize that defeating collusion attacks calls for a rather users’ devices (see, for instance, the recent DroidDream system-centric solution as opposed to application-dependent Trojan [6]). -

By Zohaib & Vlad
Follow the slides: goo.gl/bvmYgb Privilege Escalation in Windows OS by Zohaib & Vlad Follow the slides: goo.gl/bvmYgb What is Privilege Escalation? An act of exploiting a bug, design flaw or configuration oversight with the goal to gain elevated access to application resources ● Gives the ability to perform unauthorized actions in software, web apps, operating systems What is Privilege Escalation? Vertical Horizontal Accesses to functions that are Accesses functions that are reserved for higher privilege users accessible by other normal users. or applications. ● gaining administrative privileges ● Accessing accounts on the same user level ● Jailbreaking Devices ● Lock Screen Bypass ● Stealing usernames/passwords Vertical: Cross-zone scripting A web browser exploit that takes advantage of a zone-based vulnerability http://windowsupdate.microsoft.com%2f.example.com/ Windows Permission Structure ● root is “Local System” Account ● Windows UAC (User Account Control) ○ disabled admin account, instead uses UAC ● “sudo” is “runas” to run with privileges Types of Accounts: ● Local User ● Domain User ● The LocalSystem Windows with User Access Control ● All users run as an unprivileged user by default, even when logged on as an Administrator. ● Once running, the privilege of an application cannot be changed. ● Users are prompted to provide explicit consent before using elevated privilege, which then lasts for the life of the process. Windows OS Privilege Escalation ● replacing “screensaver” binary ● scan the registry for ○ logon Information ○ network -

All Roads Lead to SYSTEM
MWR Labs Whitepaper All Roads Lead to SYSTEM Kostas Lintovois Contents page Contents page............................................................................................ 2 1. Introduction ............................................................................................ 3 1.1 Windows Service Accounts ......................................................................... 4 2. Auditing Windows Services ......................................................................... 5 2.1 Insecure File System Permissions .................................................................. 5 2.2 Insecure Registry Permissions ...................................................................... 8 2.3 Insecure Named Pipe Permissions ................................................................ 10 2.4 Insecure Service Permissions ...................................................................... 12 2.5 Missing DLLs......................................................................................... 15 2.6 Unquoted Service Binary Paths ................................................................... 18 3. Service Exploitation ................................................................................ 21 4. Scripted Assessment ............................................................................... 23 5. Summary .............................................................................................. 24 6. References .......................................................................................... -

A Practitioners Guide to the Forensic Investigation of Xbox 360 Gaming Consoles
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Embry-Riddle Aeronautical University 2011 Annual ADFSL Conference on Digital Forensics, Security and Law Proceedings May 25th, 11:00 AM A Practitioners Guide to the Forensic Investigation of Xbox 360 Gaming Consoles Ashley L. Podhradsky Drexel University Rob D’Ovidio Drexel University Cindy Casey Drexel University Follow this and additional works at: https://commons.erau.edu/adfsl Part of the Computer Engineering Commons, Computer Law Commons, Electrical and Computer Engineering Commons, Forensic Science and Technology Commons, and the Information Security Commons Scholarly Commons Citation Podhradsky, Ashley L.; D’Ovidio, Rob; and Casey, Cindy, "A Practitioners Guide to the Forensic Investigation of Xbox 360 Gaming Consoles" (2011). Annual ADFSL Conference on Digital Forensics, Security and Law. 9. https://commons.erau.edu/adfsl/2011/wednesday/9 This Peer Reviewed Paper is brought to you for free and open access by the Conferences at Scholarly Commons. It has been accepted for inclusion in Annual ADFSL Conference on Digital Forensics, Security and Law by an (c)ADFSL authorized administrator of Scholarly Commons. For more information, please contact [email protected]. ADFSL Conference on Digital Forensics, Security and Law, 2011 A PRACTITIONERS GUIDE TO THE FORENSIC INVESTIGATION OF XBOX 360 GAMING CONSOLES Dr. Ashley L Podhradsky Drexel University Dr. Rob D’Ovidio Drexel University Cindy Casey Drexel University ABSTRACT Given the ubiquitous nature of computing, individuals now have nearly 24-7 access to the internet. People are not just going online through traditional means with a PC anymore, they are now frequently using nontraditional devices such as cell phones, smart phones, and gaming consoles. -

MEADES Phd Thesis
PLAYING AGAINST THE GRAIN RHETORICS OF COUNTERPLAY IN CONSOLE BASED FIRST-PERSON SHOOTER VIDEOGAMES A thesis submitted for the degree of Doctor of Philosophy By Alan Frederick Meades School of Arts, Brunel University February 2013 1 ABSTRACT Counterplay is a way of playing digital games that opposes the encoded algorithms that define their appropriate use and interaction. Counterplay is often manifested within the social arena as practices such as the creation of incendiary user generated content, grief-play, cheating, glitching, modding, and hacking. It is deemed damaging to normative play values, to the experience of play, and detrimental to the viability of videogames as mainstream entertainment products. Counterplay is often framed through the rhetoric of transgression as pathogen, as a hostile, infectious, threatening act. Those found conducting it are subject to a range of punishments ranging from expulsion from videogames to criminal conviction. Despite the steps taken to manage counterplay, it occurs frequently within contemporary videogames causing significant disruption to play and necessitating costly remedy. This thesis argues that counterplay should be understood as a practice with its own pleasures and justifying rhetorics that problematise the rhetoric of pathogen and attenuate the threat of penalty. Despite the social and economic significance of counterplay upon contemporary videogames, relatively little is known of the practices conducted by counterplayers, their motivations, or the rhetorics that they deploy to justify and contextualise their actions. Through the use of ethnographic approaches, including interview and participant observation, alongside the identification and application of five popular rhetorics of transgression, this study aims to expose the meanings and complexities of contemporary counterplay.