Android Exploits Commanding Higher Price Than Ever Before
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

BUGS in the SYSTEM a Primer on the Software Vulnerability Ecosystem and Its Policy Implications
ANDI WILSON, ROSS SCHULMAN, KEVIN BANKSTON, AND TREY HERR BUGS IN THE SYSTEM A Primer on the Software Vulnerability Ecosystem and its Policy Implications JULY 2016 About the Authors About New America New America is committed to renewing American politics, Andi Wilson is a policy analyst at New America’s Open prosperity, and purpose in the Digital Age. We generate big Technology Institute, where she researches and writes ideas, bridge the gap between technology and policy, and about the relationship between technology and policy. curate broad public conversation. We combine the best of With a specific focus on cybersecurity, Andi is currently a policy research institute, technology laboratory, public working on issues including encryption, vulnerabilities forum, media platform, and a venture capital fund for equities, surveillance, and internet freedom. ideas. We are a distinctive community of thinkers, writers, researchers, technologists, and community activists who Ross Schulman is a co-director of the Cybersecurity believe deeply in the possibility of American renewal. Initiative and senior policy counsel at New America’s Open Find out more at newamerica.org/our-story. Technology Institute, where he focuses on cybersecurity, encryption, surveillance, and Internet governance. Prior to joining OTI, Ross worked for Google in Mountain About the Cybersecurity Initiative View, California. Ross has also worked at the Computer The Internet has connected us. Yet the policies and and Communications Industry Association, the Center debates that surround the security of our networks are for Democracy and Technology, and on Capitol Hill for too often disconnected, disjointed, and stuck in an Senators Wyden and Feingold. unsuccessful status quo. -

The Million Dollar Dissident: NSO Group's Iphone Zero-Days Used Against a UAE Human Rights Defender
Research Teaching News Lab Projects GLA2010 In the News About Publications Newsletter People Archives Events Opportunities Contact The Million Dollar Dissident: NSO Group’s iPhone Zero-Days used against a UAE Human Rights Defender August 24, 2016 Categories: Bill Marczak, John Scott-Railton, Reports and Briefings Authors: Bill Marczak and John Scott-Railton, Senior Researchers at the Citizen Lab, with the assistance of the research team at Lookout Security. Media coverage: The New York Times, Motherboard, Gizmodo, Wired, Washington Post, ZDNet. This report describes how a government targeted an internationally recognized human rights defender, Ahmed Mansoor, with the Trident, a chain of zero-day exploits designed to infect his iPhone with sophisticated commercial spyware. 1. Executive Summary Ahmed Mansoor is an internationally recognized human rights defender, based in the United Arab Emirates (UAE), and recipient of the Martin Ennals Award (sometimes referred to as a “Nobel Prize for human rights”). On August 10 and 11, 2016, Mansoor received SMS text messages on his iPhone promising “new secrets” about detainees tortured in UAE jails if he clicked on an included link. Instead of clicking, Mansoor sent the messages to Citizen Lab researchers. We recognized the links as belonging to an exploit infrastructure connected to NSO Group, an Israel-based “cyber war” company that sells Pegasus, a government- exclusive “lawful intercept” spyware product. NSO Group is reportedly owned by an American venture capital firm, Francisco Partners Management. The ensuing investigation, a collaboration between researchers from Citizen Lab and from Lookout Security, determined that the links led to a chain of zero-day exploits (“zero-days”) that would have remotely jailbroken Mansoor’s stock iPhone 6 and installed sophisticated spyware. -

BUGS in the SYSTEM a Primer on the Software Vulnerability Ecosystem and Its Policy Implications
ANDI WILSON, ROSS SCHULMAN, KEVIN BANKSTON, AND TREY HERR BUGS IN THE SYSTEM A Primer on the Software Vulnerability Ecosystem and its Policy Implications JULY 2016 About the Authors About New America New America is committed to renewing American politics, Andi Wilson is a policy analyst at New America’s Open prosperity, and purpose in the Digital Age. We generate big Technology Institute, where she researches and writes ideas, bridge the gap between technology and policy, and about the relationship between technology and policy. curate broad public conversation. We combine the best of With a specific focus on cybersecurity, Andi is currently a policy research institute, technology laboratory, public working on issues including encryption, vulnerabilities forum, media platform, and a venture capital fund for equities, surveillance, and internet freedom. ideas. We are a distinctive community of thinkers, writers, researchers, technologists, and community activists who Ross Schulman is a co-director of the Cybersecurity believe deeply in the possibility of American renewal. Initiative and senior policy counsel at New America’s Open Find out more at newamerica.org/our-story. Technology Institute, where he focuses on cybersecurity, encryption, surveillance, and Internet governance. Prior to joining OTI, Ross worked for Google in Mountain About the Cybersecurity Initiative View, California. Ross has also worked at the Computer The Internet has connected us. Yet the policies and and Communications Industry Association, the Center debates that surround the security of our networks are for Democracy and Technology, and on Capitol Hill for too often disconnected, disjointed, and stuck in an Senators Wyden and Feingold. unsuccessful status quo. -

Malware Trends
NCCIC National Cybersecurity and Communications Integration Center Malware Trends Industrial Control Systems Emergency Response Team (ICS-CERT) Advanced Analytical Laboratory (AAL) October 2016 This product is provided subject only to the Notification Section as indicated here:http://www.us-cert.gov/privacy/ SUMMARY This white paper will explore the changes in malware throughout the past several years, with a focus on what the security industry is most likely to see today, how asset owners can harden existing networks against these attacks, and the expected direction of developments and targets in the com- ing years. ii CONTENTS SUMMARY .................................................................................................................................................ii ACRONYMS .............................................................................................................................................. iv 1.INTRODUCTION .................................................................................................................................... 1 1.1 State of the Battlefield ..................................................................................................................... 1 2.ATTACKER TACTIC CHANGES ........................................................................................................... 2 2.1 Malware as a Service ...................................................................................................................... 2 2.2 Destructive Malware ...................................................................................................................... -

Threatpost | the First Stop for Security News
Threatpost | The first stop for security news Categories Category List Cloud Security Critical Infrastructure Cryptography Government Category List Hacks Malware Mobile Security Privacy Category List SAS Vulnerabilities Web Security Authors Michael Mimoso Christopher Brook Additional Categories Slideshows The Kaspersky Lab News Service Featured Authors Michael Mimoso Christopher Brook The Kaspersky Lab News Service Featured Posts All Wireless ‘BlueBorne’ Attacks Target Billions of… Apache Foundation Refutes Involvement in Equifax… Popular D-Link Router Riddled with Vulnerabilities Many Questions, Few Answers For Equifax… Equifax Says Breach Affects 143 Million… New Dridex Phishing Campaign Delivers Fake… Podcasts Latest Podcasts All Threatpost News Wrap, September 1, 2017 Threatpost News Wrap, August 25, 2017 Threatpost News Wrap, August 18, 2017 Threatpost News Wrap, August 11, 2017 Threatpost News Wrap, August 4, 2017 Black Hat USA 2017 Preview Recommended The Kaspersky Lab Security News Service Videos Latest Videos All Mark Dowd on Exploit Mitigation Development iOS 10 Passcode Bypass Can Access… BASHLITE Family Of Malware Infects 1… How to Leak Data From Air-Gapped… Bruce Schneier on the Integration of… Chris Valasek Talks Car Hacking, IoT,… Recommended The Kaspersky Lab Security News Service Search Twitter Facebook Google LinkedIn YouTube RSS Welcome > Blog Home>Vulnerabilities > Zerodium Offering $1M for Tor Browser Zero Days 0 0 22 0 Zerodium Offering $1M for Tor Browser Zero Days by Chris Brook September 13, 2017 , 12:54 pm The exploit acquisition vendor Zerodium is doubling down again. Weeks after the company said it would pay $500,000 for zero days in private messaging apps such as Signal and WhatsApp, Zerodium said Wednesday it will pay twice that for a zero day in Tor Browser. -

Ethical Hacking
Ethical Hacking Alana Maurushat University of Ottawa Press ETHICAL HACKING ETHICAL HACKING Alana Maurushat University of Ottawa Press 2019 The University of Ottawa Press (UOP) is proud to be the oldest of the francophone university presses in Canada and the only bilingual university publisher in North America. Since 1936, UOP has been “enriching intellectual and cultural discourse” by producing peer-reviewed and award-winning books in the humanities and social sciences, in French or in English. Library and Archives Canada Cataloguing in Publication Title: Ethical hacking / Alana Maurushat. Names: Maurushat, Alana, author. Description: Includes bibliographical references. Identifiers: Canadiana (print) 20190087447 | Canadiana (ebook) 2019008748X | ISBN 9780776627915 (softcover) | ISBN 9780776627922 (PDF) | ISBN 9780776627939 (EPUB) | ISBN 9780776627946 (Kindle) Subjects: LCSH: Hacking—Moral and ethical aspects—Case studies. | LCGFT: Case studies. Classification: LCC HV6773 .M38 2019 | DDC 364.16/8—dc23 Legal Deposit: First Quarter 2019 Library and Archives Canada © Alana Maurushat, 2019, under Creative Commons License Attribution— NonCommercial-ShareAlike 4.0 International (CC BY-NC-SA 4.0) https://creativecommons.org/licenses/by-nc-sa/4.0/ Printed and bound in Canada by Gauvin Press Copy editing Robbie McCaw Proofreading Robert Ferguson Typesetting CS Cover design Édiscript enr. and Elizabeth Schwaiger Cover image Fragmented Memory by Phillip David Stearns, n.d., Personal Data, Software, Jacquard Woven Cotton. Image © Phillip David Stearns, reproduced with kind permission from the artist. The University of Ottawa Press gratefully acknowledges the support extended to its publishing list by Canadian Heritage through the Canada Book Fund, by the Canada Council for the Arts, by the Ontario Arts Council, by the Federation for the Humanities and Social Sciences through the Awards to Scholarly Publications Program, and by the University of Ottawa. -
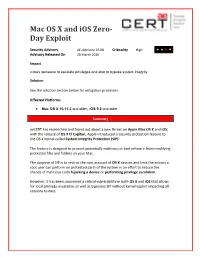
Mac OS X and Ios Zero- Day Exploit
Mac OS X and iOS Zero- Day Exploit Security Advisory AE-Advisory 16-08 Criticality High Advisory Released On 28 March 2016 Impact Allows someone to escalate privileges and also to bypass system integrity Solution See the solution section below for mitigation processes. Affected Platforms Mac OS X 10.11.3 and older, iOS 9.2 and older Summary aeCERT has researched and found out about a new threat on Apple Mac OS X and iOS; with the release of OS X El Capitan, Apple introduced a security protection feature to the OS X kernel called System Integrity Protection (SIP). The feature is designed to prevent potentially malicious or bad software from modifying protected files and folders on your Mac. The purpose of SIP is to restrict the root account of OS X devices and limit the actions a root user can perform on protected parts of the system in an effort to reduce the chance of malicious code hijacking a device or performing privilege escalation. However, it has been uncovered a critical vulnerability in both OS X and iOS that allows for local privilege escalation as well as bypasses SIP without karnel exploit impacting all versions to date. Threat Details The zero day vulnerability is a Non-Memory Corruption bug that allows hackers to execute arbitrary code on any targeted machine, perform remote code execution (RCE) or sandbox escapes. The attacker then escalates the malware's privileges to bypass System Integrity Protection SIP, alter system files, and then stay on the infected system. By default, System Integrity Protection or SIP protects these folders: /System. -

Computer Security
CS155 Computer Security Course overview Dan Boneh Admin • Course web site: https://cs155.Stanford.edu • Profs: Dan Boneh and Zakir Durumeric • Three programming projects (pairs) and two written homeworks • Project #1 posted on Thu. Please attend section this Friday! • Use EdDiscussions and Gradescope • Automatic 72 hour extension Dan Boneh Live lectures on Zoom Lectures are recorded … posted on canvas ask questions Dan Boneh The computer security problem • Lots of buggy software • Social engineering is very effective • Money can be made from finding and exploiting vulns. 1. MarketpLace for expLoits (gaining a foothoLd) 2. MarketpLace for maLware (post compromise) 3. Strong economic and poLiticaL motivation for using both current state of computer security Dan Boneh Top 10 products by totaL number of “distinct” vuLnerabiLities in 2019 source: https://www.cvedetails.com/top-50-products.php?year=2019 Dan Boneh Vulnerable applications being exploited Java Android Browser Office Source: Kaspersky Security Bulletin 2020 Dan Boneh A global problem Top 10 countries by share of attacked users: Source: Kaspersky Security Bulletin 2020 Dan Boneh Goals for this course • Understand expLoit techniques – Learn to defend and prevent common expLoits • Understand the avaiLabLe security tooLs • Learn to architect secure systems Dan Boneh This course Part 1: basics (architecting for security) • Securing apps, OS, and Legacy code: sandboxing, access controL, and security testing Part 2: Web security (defending against a web attacker) • BuiLding robust web sites, understand the browser security modeL Part 3: network security (defending against a network attacker) • Monitoring and architecting secure networks. Part 4: securing mobile applications Dan Boneh Don’t try this at home ! Dan Boneh Introduction What motivates attackers? … economics Dan Boneh Why compromise end user machines? 1. -
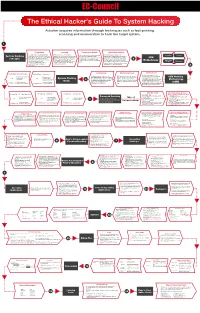
Download the Ethical Hacker's Guide to System Hacking
The Ethical Hacker's Guide To System Hacking Attacker acquires information through techniques such as foot printing, scanning and enumeration to hack the target system. 1 Footprinting Scanning Enumeration Module Vulnerability Analysis It is the process of accumulating data Vulnerability Assessment is an This is a procedure for identifying This is a method of intrusive probing, Footprinting Scanning System Hacking regarding a specific network environment. active hosts, open ports, and unnecessary through which attackers gather examination of the ability of a system or In this phase, the attacker creates a profile services enabled on ports. Attackers use information such as network user lists, application, including current security CEH concepts of the target organization, obtaining different types of scanning, such as port routing tables, security flaws, and procedures, and controls to with stand 2 information such as its IP address range, scanning network scanning, and simple network protocol data (SNMP) assault. Attackers perform this analysis Methodology Vulnerability namespace and employees. Enumeration vulnerability, scanning of target networks data. to identify security loopholes, in the target Analysis Footprinting eases the process of or systems which help in identifying organization’s network, communication system hacking by revealing its possible vulnerabilities. infrastructure, and end systems. vulnerabilities 3 Clearing Logs Maintaining Access Gaining Access Hacking Stage Escalating Privileges Hacking Stage Gaining Access It involves gaining access to To maintain future system access, After gaining access to the target low-privileged user accounts by To acquire the rights of To bypass access CEH Hacking attackers attempt to avoid recognition system, attackers work to maintain cracking passwords through Goal another user or Goal controls to gain System Hacking by legitimate system users. -

Security Now! #705 - 03-12-19 Spoiler
Security Now! #705 - 03-12-19 Spoiler This week on Security Now! This week we look at the 0-day exploit bidding war that's underway, the NSA's release of Ghidra, Firefox's addition of privacy enhancements which were first developed for the Tor version of Firefox, a pair of 0-days that were biting people in the wild, news of a worrisome breach at Citrix, the risk of claiming to be an unhackable aftermarket car alarm, a new and interesting "windows developers chatting with users" idea at Microsoft, a semi-solution to Windows updates crashing systems, detailed news of the Marriott/Starwood breach, a bit of miscellany from Elaine, a SpinRite question answered, and then we finish with SPOILER, the latest research exploiting yet another new and different consequence of speculation on Intel machines. See next page for the picture of the week... Happy 30th Birthday to the World Wide Web! http://info.cern.ch/Proposal.html 1 Security News Zerodium: $500,000 for a Hypervisor 0-Day Last week's topic was "Careers in Bug Hunting." While we were delivering that podcast, and although we were primarily talking about HackerOne, I mentioned Zerodium as a admitted alternative cash-out source if someone found a particularly tasty and important 0-day flaw. As it happens, while we were delivering that podcast Zerodium was upping the ante! They tweeted: We're paying up to $500,000 for #0day exploits targeting VMware ESXi (vSphere) or Microsoft Hyper-V, and allowing Guest-to-Host escapes. The exploits must work with default configs, be reliable, and lead to full access to the host. -

Extreme Privilege Escalation on Windows 8/UEFI Systems
Extreme Privilege Escalation on Windows 8/UEFI Systems C o r e y K a l l e n b e r g @ c o r e y k a l X e n o K o v a h @ x e n o k o v a h John Butterworth @jwbutterworth3 Sam Cornwell @ssc0rnwell © 2014 The MITRE Corporation. All rights reserved. | 2 | Introduction . Who we are: – Trusted Computing and firmware security researchers at The MITRE Corporation . What MITRE is: – A not-for-profit company that runs six US Government "Federally Funded Research & Development Centers" (FFRDCs) dedicated to working in the public interest – Technical lead for a number of standards and structured data exchange formats such as CVE, CWE, OVAL, CAPEC, STIX, TAXII, etc – The first .org, !(.mil | .gov | .com | .edu | .net), on the ARPANET © 2014 The MITRE Corporation. All rights reserved. | 3 | Attack Model (1 of 2) . We’ve gained administrator access on a victim Windows 8 machine . But we are still constrained by the limits of Ring 3 © 2014 The MITRE Corporation. All rights reserved. | 4 | Attack Model (2 of 2) . As attackers we always want – More Power – More Persistence – More Stealth © 2014 The MITRE Corporation. All rights reserved. | 5 | Typical Post-Exploitation Privilege Escalation . Starting with x64 Windows vista, kernel drivers must be signed and contain an Authenticode certificate . In a typical post-exploitation privilege escalation, attacker wants to bypass the signed driver requirement to install a kernel level rootkit . Various methods to achieve this are possible, including: – Exploit existing kernel drivers – Install a legitimate (signed), but vulnerable, driver and exploit it . -

Countering the Proliferation of Offensive Cyber Capabilities
COUNTERING THE PROLIFERATION OF OFFENSIVE CYBER CAPABILITIES Mr. Robert Morgus, Cybersecurity Initiative & International Security Program, New America Mr. Max Smeets, Centre for International Security and Cooperation (CISAC), Stanford University Mr. Trey Herr, Harvard Kennedy School MEMO №2 GCSC ISSUE BRIEF 161 TABLE OF CONTENTS SECTION 1: INTRODUCTION 163 SECTION 2: SCOPE OF ANALYSIS 165 SECTION 3: THE PILLARS AND OBJECTIVES OF COUNTERPROLIFERATION 167 SECTION 4: THE TRACE FRAMEWORK 169 SECTION 5: MAKING PROGRESS ON PROLIFERATION: APPLYING THE TRACE MODEL 177 Potential International Agreements 177 Arms Control Agreement 178 Export Control Arrangement 180 Tools for States or Like-minded Actors 181 Enhance Offensive and Defensive Capability 182 Diplomatic Toolbox 183 SECTION 6: RECOMMENDATIONS 184 1. Patience. 184 2. Increase the cost of developing offensive cyber capabilities 185 3. Further explore ways to increase barriers to spreading offensive cyber capability 186 CONCLUSIONS 187 GCSC ISSUE BRIEF 162 SECTION 1: INTRODUCTION The tenor of the cyber stability debate, often moribund and moving more sideways than forward, changed with the 2010 United Nations Governmental Group of Experts (UN GGE) Consensus Report that international law applied to cyberspace.164 It followed a position paper by the Obama administration published in January of that year to bring the various sides closer together. Though it wasn’t a steep trend line which followed, the slow process towards cyber norms was considered to be meaningful and positive.165 Despite this and subsequent progress, however, the events of 2017 have shed doubt on this progressive dynamic. The collapse of the UN GGE process in June sent an alarming message that we are moving away from establishing a meaningful cyber stability regime, rather than towards it.