Future Directions in Technology-Enabled Crime: 2007–09
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Case 3:07-Cr-00057-MRK Document 6 Filed 03/21/2007 Page 1 of 9
Case 3:07-cr-00057-MRK Document 6 Filed 03/21/2007 Page 1 of 9 UNITED STATES DISTRICT COURT DISTRICT OF CONNECTICUT UNITED STATES OF AMERICA : Case No: : : VIOLATIONS: : : 18 U.S.C. § 2339A (Providing Material v. : Support to Terrorists) : : 18 U.S.C. § 793(d) (Communicating : National Defense Information to Persons not : Entitled to Receive it) HASSAN ABUJIHAAD, : a/k/a PAUL R. HALL : 18 U.S.C. § 2 I N D I C T M E N T The Grand Jury charges that: INTRODUCTION 1. From on or about December 20, 1997, through on or about January 25, 2002, HASSAN ABUJIHAAD, a/k/a PAUL R. HALL (“ABUJIHAAD”), was an enlisted member of the United States Navy. From on or about July 1, 1998, through on or about January 10, 2002, ABUJIHAAD was assigned to a United States Navy destroyer named the U.S.S. Benfold, where his primary position was Signalman. In March and April 2001, the U.S.S. Benfold was part of a United States Navy Battle Group directed to transit from California to the Persian Gulf region. 2. On January 6, 1998, in connection with his duties in the United States Navy, ABUJIHAAD was approved by the Department of the Navy Central Adjudication Facility (“DONCAF”) for access to information classified at the “Secret” level pursuant to Executive Order 12,958, as amended by Executive Order 13,292. Case 3:07-cr-00057-MRK Document 6 Filed 03/21/2007 Page 2 of 9 3. Pursuant to Executive Order 12,958, as amended by Executive Order 13,292, national security information may be classified as, among other things, “Secret.” The designation “Secret” applies to information, the unauthorized disclosure of which reasonably could be expected to cause serious damage to the national security. -

Adware-Searchsuite
McAfee Labs Threat Advisory Adware-SearchSuite June 22, 2018 McAfee Labs periodically publishes Threat Advisories to provide customers with a detailed analysis of prevalent malware. This Threat Advisory contains behavioral information, characteristics and symptoms that may be used to mitigate or discover this threat, and suggestions for mitigation in addition to the coverage provided by the DATs. To receive a notification when a Threat Advisory is published by McAfee Labs, select to receive “Malware and Threat Reports” at the following URL: https://www.mcafee.com/enterprise/en-us/sns/preferences/sns-form.html Summary Detailed information about the threat, its propagation, characteristics and mitigation are in the following sections: Infection and Propagation Vectors Mitigation Characteristics and Symptoms Restart Mechanism McAfee Foundstone Services The Threat Intelligence Library contains the date that the above signatures were most recently updated. Please review the above mentioned Threat Library for the most up to date coverage information. Infection and Propagation Vectors Adware-SearchSuite is a "potentially unwanted program" (PUP). PUPs are any piece of software that a reasonably security- or privacy-minded computer user may want to be informed of and, in some cases, remove. PUPs are often made by a legitimate corporate entity for some beneficial purpose, but they alter the security state of the computer on which they are installed, or the privacy posture of the user of the system, such that most users will want to be aware of them. Mitigation Mitigating the threat at multiple levels like file, registry and URL could be achieved at various layers of McAfee products. Browse the product guidelines available here (click Knowledge Center, and select Product Documentation from the Support Content list) to mitigate the threats based on the behavior described in the Characteristics and symptoms section. -

A Crawler-Based Study of Spyware on the Web
A Crawler-based Study of Spyware on the Web Alexander Moshchuk, Tanya Bragin, Steven D. Gribble, and Henry M. Levy Department of Computer Science & Engineering University of Washington {anm, tbragin, gribble, levy}@cs.washington.edu Abstract servers [16]. The AOL scan mentioned above has provided simple summary statistics by directly examining desktop in- Malicious spyware poses a significant threat to desktop fections [2], while a recent set of papers have considered security and integrity. This paper examines that threat from user knowledge of spyware and its behavior [6, 29]. an Internet perspective. Using a crawler, we performed a In this paper we change perspective, examining the na- large-scale, longitudinal study of the Web, sampling both ture of the spyware threat not on the desktop but from an executables and conventional Web pages for malicious ob- Internet point of view. To do this, we conduct a large-scale jects. Our results show the extent of spyware content. For outward-looking study by crawling the Web, downloading example, in a May 2005 crawl of 18 million URLs, we found content from a large number of sites, and then analyzing it spyware in 13.4% of the 21,200 executables we identified. to determine whether it is malicious. In this way, we can At the same time, we found scripted “drive-by download” answer several important questions. For example: attacks in 5.9% of the Web pages we processed. Our analy- sis quantifies the density of spyware, the types of of threats, • How much spyware is on the Internet? and the most dangerous Web zones in which spyware is • Where is that spyware located (e.g., game sites, chil- likely to be encountered. -

High Court Judgment Template
Case No: CO/5160/2014 Neutral Citation Number: [2015] EWHC 2354 (Admin) IN THE HIGH COURT OF JUSTICE QUEEN'S BENCH DIVISION ADMINISTRATIVE COURT Royal Courts of Justice Strand, London, WC2A 2LL Date: 07/08/2015 Before: THE HONOURABLE MR JUSTICE CRANSTON - - - - - - - - - - - - - - - - - - - - - Between: THE COMMISSIONER OF THE POLICE OF THE Claimant METROPOLIS - and - SYED TALHA AHSAN Defendant - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Mr Tom Little (instructed by the Metropolitan Police Legal Service) for the Claimant Mr Daniel Squires (instructed by Birnberg Peirce & Partners) for the Defendant Hearing dates: 24/07/2015 - - - - - - - - - - - - - - - - - - - - - Judgmen tMr Justice Cranston: Introduction: 1. This is an application by the Commissioner of Police of the Metropolis (“the Commissioner”) for an order to impose notification requirements for a period of 15 years on Syed Talha Ahsan (“Mr Ahsan”) under the Counter-Terrorism Act 2008 (“the 2008 Act”). In 2013, he was convicted in the United States of conspiracy to provide material assistance for terrorism through his involvement in a website. He has now returned to the United Kingdom. The notification order will require him for that period to attend police stations to provide, and update, information about his living arrangements and to provide details about his travel plans, for which permission can be refused. Breach of the requirements is punishable with imprisonment of up to 5 years. 2. Notification requirements have been imposed in many cases when persons have been convicted in the UK of terrorist-related offences. This is the first case in which a notification order has been contested in respect of a person convicted outside the UK of a corresponding foreign offence. -

Pietro Deandrea
POETRY AND THE WAR ON TERROR: THE CASE OF SYED TALHA AHSAN Pietro Deandrea In May 2013 public opinion was informed that the British army in Camp Bastion (Afghanistan) held some ninety native prisoners in inhuman conditions, arbitrarily and indefinitely, as a result of a government decision to extend exceptional measures to all detainees. Predictably, the news stirred much shock and debate1, showing another appalling side of the involvement of the UK in the American War on Terror based on exceptional measures. Commenting on President Bush’s 2001 special laws, Giorgio Agamben identified in the state of exception, “state power’s immediate response to the most extreme internal conflicts”, a structural element of continuity between the techniques of government of modern totalitarian states and the “so- called democratic ones […] a threshold of indeterminacy between democracy and absolutism.” Agamben’s juridical and philosophical analysis shows that the state of exception “tends increasingly to appear as the dominant paradigm of government in contemporary politics”2. Unfortunately, in the past decade the exceptional practice whereby people can be detained without evidence and trial has been practised on British soil, too, thanks to a specific Act involving Britain and the US: In 2003 a new Extradition Act was fast-tracked into UK legislation without a formal consultative parliamentary process, scrutiny or debate. […] the UK would be expected to extradite any individual to the US on request, without the need for the US to provide prima facie evidence (only to invoke reasonable suspicion), and thus 1 E. GIORDANA, La Guantanamo di Sua Maestà, “Il manifesto” 30-5-2013, p. -
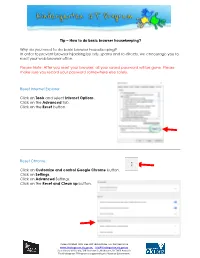
Tip – How to Do Basic Browser Housekeeping?
Tip – How to do basic browser housekeeping? Why do you need to do basic browser housekeeping? In order to prevent browser hijacking by ads, spams and re-directs, we encourage you to reset your web browser often. Please Note: After you reset your browser, all your saved password will be gone. Please make sure you record your password somewhere else safely. _______________________________________________________________________________________ Reset Internet Explorer Click on Tools and select Internet Options . Click on the Advanced tab. Click on the Reset button. _______________________________________________________________________________________ Reset Chrome Click on Customize and control Google Chrome button. Click on Settings . Click on Advanced Settings. Click on the Reset and Clean up button. Phone: (03) 8664 7001 Free Call: 1800 629 835 Fax: (03) 9639 2175 www.kindergarten.vic.gov.au [email protected] State Library of Victoria, 328 Swanston St, Melbourne, VIC 3000 Australia The Kindergarten IT Program is supported by the Victorian Government. Reset Firefox In the address bar of the FireFox type in about:support and hit Enter. Click Refresh Firefox… button. A window will appear showing the details of this action. Click Refresh Firefox button. _______________________________________________________________________________________ Clear website data in Safari Click on Safari tab and select Preferences… Click Privacy tab. Click Manage Website Data… Click on Remove All . Phone: (03) 8664 7001 Free Call: 1800 629 835 Fax: (03) 9639 2175 www.kindergarten.vic.gov.au [email protected] State Library of Victoria, 328 Swanston St, Melbourne, VIC 3000 Australia The Kindergarten IT Program is supported by the Victorian Government. Reset Edge Click on Settings and More button. -

COVID-19 Updates and Resources for Local Governments G Tuesday, March 23, 2021 Welcome Greeting
COVID-19 Updates and Resources for Local Governments g Tuesday, March 23, 2021 Welcome Greeting Kayla Rosen Departmental Analyst, Community Engagement and Finance, Department of Treasury 2 Tools and Resources for Local Governments: 11th Webinar Tuesday, March 23, 2021 – 2 p.m. – 3 p.m. I. Welcome & Introductions Heather Frick, Bureau Director, Bureau of Local Government and School Services, Michigan Department of Treasury I. Treasury Update a. CARES Act Grant b. FDCVT Grant c. Overviews of Recreational Marijuana Payments d. American Rescue Plan Eric Bussis, Chief Economist and Director of the Office of Revenue and Tax Analysis, Michigan Department of Treasury I. Cybersecurity for Local Governments Derek Larson, Acting Deputy Chief Security Officer, Department of Technology, Management and Budget (DTMB) I. Question and Answer II. Closing Remarks Heather Frick, Bureau Director, Bureau of Local Government and School Services, Michigan Department of Treasury 3 Welcome & Introductions Heather Frick Bureau Director, Bureau of Local Government and School Services, Department of Treasury 4 Treasury Local Government Funding Update Eric Bussis Chief Economist and Director Office of Revenue and Tax Analysis Michigan Department of Treasury 5 Treasury Update • CARES Act Grant • FDCVT Grant Agenda • Overviews of Recreational Marijuana Payments • American Rescue Plan 6 First Responder Hazard Pay Premiums Program (FRHPPP) • Payments made to 740 applicants, supporting approximately 37,500 first responders • 97 applications were selected for further federal -

The Emergence of Exploit-As-A-Service
Manufacturing Compromise: The Emergence of Exploit-as-a-Service Chris Grier† Lucas Ballard2 Juan Caballerox Neha Chachra∗ Christian J. Dietrichq Kirill Levchenko∗ Panayiotis Mavrommatis2 Damon McCoyz Antonio Nappax Andreas Pitsillidis∗ Niels Provos2 M. Zubair Rafiquex Moheeb Abu Rajab2 Christian Rossowq Kurt Thomasy Vern Paxson† Stefan Savage∗ Geoffrey M. Voelker∗ y University of California, Berkeley ∗ University of California, San Diego 2 Google International Computer Science Institute x IMDEA Software Institute q University of Applied Sciences Gelsenkirchen z George Mason University ABSTRACT 1. INTRODUCTION We investigate the emergence of the exploit-as-a-service model for In this work we investigate the emergence of a new paradigm: the driveby browser compromise. In this regime, attackers pay for an exploit-as-a-service economy that surrounds browser compromise. exploit kit or service to do the “dirty work” of exploiting a vic- This model follows in the footsteps of a dramatic evolution in the tim’s browser, decoupling the complexities of browser and plugin world of for-profit malware over the last five years, where host com- vulnerabilities from the challenges of generating traffic to a web- promise is now decoupled from host monetization. Specifically, the site under the attacker’s control. Upon a successful exploit, these means by which a host initially falls under an attacker’s control are kits load and execute a binary provided by the attacker, effectively now independent of the means by which an(other) attacker abuses transferring control of a victim’s machine to the attacker. the host in order to realize a profit. This shift in behavior is exem- In order to understand the impact of the exploit-as-a-service plified by the pay-per-install model of malware distribution, where paradigm on the malware ecosystem, we perform a detailed anal- miscreants pay for compromised hosts via the underground econ- ysis of the prevalence of exploit kits, the families of malware in- omy [4, 41]. -

Piracy Landscape Study
Piracy Landscape Study: Analysis of Existing and Emerging Research Relevant to Intellectual Property Rights (IPR) Enforcement of Commercial-Scale Piracy Prepared for the U.S. Patent and Trademark Office Solicitation Number: 1333BJ19Q00142004 Brett Danaher Michael D. Smith Rahul Telang Chapman University Carnegie Mellon University Carnegie Mellon University This Version: March 20, 2020 Table of Contents Executive Summary ...................................................................................................................... 3 1. The Piracy Ecosystem........................................................................................................... 4 1.1 Piracy of Physical Goods................................................................................................ 6 1.1.1 Manufacturing......................................................................................................... 7 1.1.2 Discovery ................................................................................................................ 7 1.1.3 Distribution ............................................................................................................. 8 1.1.4 Communication, Payment Processing and Fulfillment ......................................... 11 1.2 Piracy of Digital Goods ................................................................................................ 11 1.2.1 Sources.................................................................................................................. 12 1.2.2 -

Spyware & Adware Products
AdwareAdware/Spyware/Spyware ProductsProducts && RecommendationsRecommendations UCLAUCLA OfficeOffice ofof InstructionalInstructional DevelopmentDevelopment MikeMike TakahashiTakahashi AgendaAgenda WhatWhat isis AdwareAdware/Spyware/Spyware KnownKnown AdwareAdware/Spyware/Spyware ProductsProducts AntiAnti AdwareAdware/Spyware/Spyware RemovalRemoval ProductProduct ComparisonsComparisons TipsTips && RecommendationsRecommendations AdwareAdware AdwareAdware cancan bebe softwaresoftware thatthat generatesgenerates advertisementsadvertisements suchsuch asas poppop--upup windowswindows oror hotlinkshotlinks onon webweb pages.pages. ItIt maymay addadd linkslinks toto youryour favoritesfavorites andand youryour desktop.desktop. ItIt cancan changechange youryour homehome pagepage andand youryour searchsearch engineengine toto sitessites thatthat earnearn incomeincome fromfrom variousvarious advertisers.advertisers. Source http://www.microsoft.com/windows/ie/community/columns/adware.mspx AdwareAdware ExamplesExamples What?!What?! MyMy computercomputer isis infected!infected! OrOr isis it?it? AdwareAdware ExamplesExamples WellWell--knownknown AdwareAdware ProgramsPrograms toto AvoidAvoid HotbarHotbar (Add(Add--ons)ons) Adds graphical skins to Browser and Email clients Adds toolbars and search button BlockCheckerBlockChecker ClipGenieClipGenie CometComet CursorCursor GatorGator WinFixerWinFixer StumbleUponStumbleUpon WeatherBugWeatherBug SpywareSpyware SpywareSpyware isis computercomputer softwaresoftware thatthat collectscollects -

Case Number 3:04CR301(JCH) : V
Case 3:04-cr-00301-JCH Document 181 Filed 06/16/14 Page 1 of 30 UNITED STATES DISTRICT COURT DISTRICT OF CONNECTICUT UNITED STATES OF AMERICA : Case Number 3:04CR301(JCH) : v. : : BABAR AHMAD a/k/a “Abu Ammar”, : a/k/a “Abu Khubaib/Kubayb Al-Pakistani” : a/k/a “Salah” / “Salahuddin”, a/k/a : “Dr. Karim”, a/k/a “D. Karim”, a/k/a : “Maria Alcala”, a/k/a “Lara Palselmo” : a/k/a “Mr. B” : JUNE 16, 2014 GOVERNMENT’S SENTENCING MEMORANDUM On July 16, 2014, the Court will sentence the defendant, Babar Ahmad (“Ahmad”), for conspiring to provide and providing material support to terrorists, knowing and intending that such support would be used in preparation for and in carrying out: (1) a conspiracy to kill, kidnap, maim or injure persons or damage property; or (2) the murder of U.S. nationals abroad. Ahmad’s conduct, summarized in part below, warrants the maximum sentence of twenty-five (25) years. From at least 1997 through his arrest in August 2004, Babar Ahmad – through the use of numerous kunyas and aliases – surreptitiously led a sophisticated, highly organized, technically savvy and operationally covert support cell in London with global reach, through which he supported the Chechen mujahideen, the Taliban and Al-Qaida. Ahmad’s material support operation was robust, far-reaching and virtually unprecedented in its scope – indeed, Ahmad and his cell provided almost every single category of support set forth in the material support statute. Ahmad supplied funds, military equipment, communication equipment, lodging, training, expert advice and assistance and personnel – all of which were designed to raise funds, recruit for and provide equipment to the Chechen mujahideen, the Taliban and Al-Qaida, and to otherwise 1 Case 3:04-cr-00301-JCH Document 181 Filed 06/16/14 Page 2 of 30 support violent jihad in Afghanistan and Chechnya. -

Syed Talha Ahsan : June 16, 2014
Case 3:06-cr-00194-JCH Document 179 Filed 06/16/14 Page 1 of 52 UNITED STATES DISTRICT COURT DISTRICT OF CONNECTICUT UNITED STATES OF AMERICA : NO. 3:06CR194(JCH) v. : SYED TALHA AHSAN : JUNE 16, 2014 SYED TALHA AHSAN’S MEMORANDUM IN AID OF SENTENCING I. Introduction Syed Talha Ahsan has now served over eight (8) years in prisons in England and the United States, for his peripheral involvement in a case not susceptible to easy explanation or categorization. He is a highly intelligent, sensitive, inquisitive, creative man, who does not subscribe to violence as a means to solving problems. He is a threat to no one. The odds of his committing any kind of new offense are so low as to be virtually negligible. The parsimony clause of the Sentencing Reform Act would be fully satisfied by a sentence of less than the time which he has already served. Under all the circumstances here, a sentence of credit for time served is appropriate. All of Talha Ahsan’s conduct in this case occurred prior to September 11, 2001 (“9/11"). There is no allegation here that Mr. Ahsan committed or attempted to commit any act of violence. This case is not about al Qaeda. It is a case about a citizen of the United Kingdom, who before his extradition had never set foot in the United States, and the marginal assistance he provided to a website when he was twenty years old. The website reported on the plight of Muslim populations around the world. It provided information on the concept of defensive jihad, i.e., the religious obligation to protect Muslims at risk of genocide and violent persecution.