CSIC 2014( December )
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Driving the Change from Computers to Computerisation
Driving the Change from Computers to Computerisation Excerpts from the book Icons of Indian IT By by Anand Parthasarathy & S Sadagopan 2018 / 148 pages / Hardcover / Rs. 1995 ISBN: 978-8183284851 / Wisdom Tree Prof Mahabala never saw himself as just an academic, so while he helped to set up the first mainframe computers in India’s leading engineering institutions, he also assisted in opening them up for research and industrial use. At the Indian Institutes of Technology (IIT) at Kanpur and Madras (now Chennai) and at the Computer Society of India (CSI), he kick- started the computer revolution and ensured it permeated every facet of societal change in India. Fresh from Canada, where he had obtained his doctorate in Electrical Engineering, Mahabala together with V Rajaraman and HK Kesavan, played a pioneering role in shaping IIT Kanpur into a crucible of Computer Science. When Mahabala finished his doctorate in electrical engineering in 1964 at the University of Saskatchewan, Canada, he took a few days off to visit the IBM plant in Don Mills, Ontario. ‘I saw an IBM 1620 being tested prior to shipping. It carried a placard “CAWNPORE”. I was told that it was being sent to IIT Kanpur, and was, in fact, the first computer to be installed in an educational institution in India,’ he recounts. By one of those happy coincidences, Mahabala ended up in the same institution. He got a telegram from IIT Kanpur— ‘Come and join as an assistant professor’. He later found out this was the work of Prof HK Kesavan of the electrical engineering department, with whom he had interacted briefly on a previous short visit. -

General Awareness
GENERAL AWARENESS January 2021 Vol. 9, Issue 05 A PUBLICATION OF GYANM EDUCATION & TRAINING INSTITUTE PVT. LTD. SCO 13-14-15, 2ND FLOOR, SEC 34-A, CHANDIGARH Contents NATIONAL NEWS CURRENT AFFAIRS NOVEMBER 03-39 October to November 2020 BULLET NEWS VIRTUAL SUMMIT HELD WITH LUXEMBOURG PM 40-66 June 2020 to Sept 2020 LATEST 100 GK MCQs 67-74 SBI PO PRELIMS 75-86 MODEL TEST PAPER Current GK Bytes 87-110 FIGURES TO REMEMBER REPO RATE 4.00% REVERSE REPO RATE 3.35% MARGINAL STANDING 4.25% FACILITY RATE BANK RATE 4.25% Prime Minister Narendra Modi and his Luxembourg counterpart Xavier Bettel STATUTORY LIQUIDITY RATIO 18.00% held a virtual summit on Nov 19. This was the first stand-alone Summit CASH RESERVE RATIO 3.00% meeting between India and Luxembourg in the past two decades. The two BASE RATE(s) 8.15 to leaders discussed the entire spectrum of bilateral relationship, including (of various banks) 9.40% strengthening of India-Luxembourg cooperation in the post-COVID world. Luxembourg is a small European country, surrounded by Belgium, Germany INDIA’s RANK IN and France. Global Hunger Index 2020 94th PM MODI ATTENDS 12TH BRICS SUMMIT th Teacher Status Index (GTSI) 6 Prime Minister Narendra Modi attended the 12th BRICS Summit on November Asia Power Index 2020 4th 17 in virtual mode. The summit was hosted by Russia, under the theme Global Global Economic Freedom Index 105th Stability, Shared Security and Innovative Growth. India will be taking over the Chairship of the BRICS for the year 2021 and will host the 13th BRICS Summit Human Capital Index 116th next year. -

Annual Report 2007 | Reports & Filings | Investors
Once upon a time, the world was spiky. Opportunities were unequal across countries, information was often walled and new economies were unheard of. But around the mid 990s, things started changing. Wealth began to spread, opening up fresh markets. A baby-boomer generation aged in developed countries while a Gen-Y exploded in emerging ones, rebalancing the workforce and propelling new economies. Technology became ubiquitous, connecting people and information. Together, these disruptive forces rearranged and leveled the global business-scape. Braving the waves of complex regulations and changing customer expectations, a new breed of entrepreneurs arrived to claim the unexplored land. They found a flat world. We live in exciting times. Infosys Annual Report 2006-07 | Winning in the Flat World Nandan M. Nilekani, CEO and Managing Director, Infosys Technologies Ltd., in conversation with Brianna Yvonne Dieter, Executive – Academic Relations, Infosys Technologies Ltd. Recently you have been talking about the world becoming companies should beat them by making their operations more flat. Could you elaborate further? cost-competitive and globally efficient. We believe that four major trends are changing the business Create customer loyalty through faster innovation: Customers stay landscape. They are: with companies which have the most innovative and useful products and services. Therefore, companies must be able to innovate rapidly The emergence of developing economies creating new markets l to offer products and services that customers value. In many cases, and accessible talent pools, this may require co-creating these offerings with customers or l A global shift in demographics, driving companies to tap young partners. and skilled talent pools outside of industrialized countries, Make money from information: Despite years of investment in l The ongoing adoption of technology which is changing how systems, few companies are truly able to leverage information to consumers and companies use technology, and improve their operational or financial performance. -

Annual Report 2019 - 2020
Year of 2 Million Surgeries PINNACLE OF EYE CARE ANNUAL REPORT 2019 - 2020 Registered Office Address: SANKARA EYE HOSPITAL 16A, Sankara Eye Hospital Street, Sathy Road, Sivanandapuram, Coimbatore - 641 035. Ph: 0422-2666450, 4236789. Email: [email protected] Www.sankaraeye.com It is the Divine Sankalpa of the Acharyas which has shaped our Institution over the past 43 years. Gurur Brahma Gurur Vishnu Gurur Devo Maheshwaraha: Gurur Saakshaat Parabrahma Tasmai Shri Guruvey Namaha: Our obeisance at the lotus feet of the Sankaracharyas of Kanchi 2 3 SANKARA EYE FOUNDATION INDIA SRI KANCHI KAMAKOTI MEDICAL TRUST Not-for-Profit healthcare organisation. One of the largest community eye care networks globally, with a Pan-India presence. Served over 10 million Rural patients so far Performed over 2 Million free eye surgeries 750 free eye surgeries every day VISION To work towards freedom from preventable and curable blindness. MISSION To provide unmatched eye care through a strong service oriented team. 4 5 SRI KANCHI KAMAKOTI SRI KANCHI KAMAKOTI MEDICAL TRUST MEDICAL TRUST STEERING COUNCIL MEMBERS BOARD OF TRUSTEES Mr. P. Jayendra Mr. S.G. Murali Mr. C.N. Srivatsan Mr. Sundar Radhakrishnan Dr. S. V. Balasubramaniam Dr. R. V. Ramani Dr. P. G. Viswanathan Chairman Founder & Managing Trustee Dr. P. Janakiraman Mr. Arun Madhavan Mr. Bhaskar Bhat SENIOR LEADERSHIP Dr. S. R. Rao Dr. S. Balasubramaniam Sri J. M. Chanrai Dr. Radha Ramani Dr. Jagadeesh Kumar Dr. P. Mahesh Co-Founder Reddy Shanmugam Group Head - Cataract & Group Head - Vitreo Retina Cornea Sri. Murali Krishnamurthy Sri. M. N. Padmanabhan Mrs. Seetha Chandrasekar Dr. Kaushik Murali Mr. -

Top 65 Mcqs for IBPS RRB Clerk Mains
Top 65 MCQs for IBPS RRB Clerk Mains Question. Budget 2021-22 proposals to rest on six pillars. Which of the following is not among them? a) Health & well being b) Minimum Government, Maximum Governance c) Innovation and R&D d) Inclusive Development for Aspirational India e) Agricultural Development Question. Budget 2021-22 proposals to rest on six pillars. Which of the following is not among them? a) Health & well being b) Minimum Government, Maximum Governance c) Innovation and R&D d) Inclusive Development for Aspirational India e) Agricultural Development ➢ Main pillars of Budget 2021 1. Health & well-being 2. Physical & financial capital & infrastructure 3. Inclusive development for aspirational India 4. Reinvigorating human capital 5. Innovation & R&D 6. Minimum Govt & Maximum Governance Question. The forthcoming census would be the first digital census in the history of India. How much amount is allocated for this in 2021-22? a) 2,654 crore b) 4,973 crore c) 2,872 crore d) 3,768 crore e) 4,675 crore Question. The forthcoming census would be the first digital census in the history of India. How much amount is allocated for this in 2021-22? a) 2,654 crore b) 4,973 crore c) 2,872 crore d) 3,768 crore e) 4,675 crore Question. How much amount was paid to farmers for wheat procurement in 2020-21? a) 60,000 crore b) 85,000 crore c) 70,000 crore d) 75,000 crore e) 80,000 crore Question. How much amount was paid to farmers for wheat procurement in 2020-21? a) 60,000 crore b) 85,000 crore c) 70,000 crore d) 75,000 crore e) 80,000 crore Question. -

Annual Report 2017 - 18
Annual Report 2017 - 18 India@75: Inclusive. Ahead. Responsible Annual Report 2017 - 18 India@75: Inclusive. Ahead. Responsible 2 The CII theme for the year ‘India@75: Inclusive. Ahead. Responsible’ received high attention through the year. Employment, education and healthcare emerged as key pillars for the inclusive growth agenda. In particular, women parity was an issue we actioned strongly. CII opened its fourth Model Career Center, held many job fairs to bring new opportunities for youth and expanded engagement in skills and training. I am happy that CII reaches out to a million youth every year through its various educational and training activities. A competitive Indian industry requires a facilitative investment climate. We celebrated India’s jump in the World Bank ‘Doing Business’ rankings by as many as 30 places in a single year. CII worked closely with Central and State Governments through the year on ease of MS SHOBANA KAMINENI doing business. The reduction in corporate tax rate to President, CII 25% for enterprises with turnover below INR 250 crore was a great step in line with our submissions. Taking India Ahead means adapting to the new technology changes that are gathering momentum. CII has built a strong focus on Start-ups and entrepreneurship, aiming to partner with young people through the Startupreneurs Forum and other initiatives. This year, we also set up the Society of Indian Defence President’s Manufacturers to converge policy and action on this Review sunrise sector. We had the chance to work with the Government on some of its major initiatives. Textiles India and World Looking Back Food India had the participation of Prime Minister. -

Vol. 14 :: No. 3 :: Jul – Sep 2019 Message from the Chairman
Vol. 14 :: No. 3 :: Jul – Sep 2019 Message from the Chairman Dear IEEE Indian Members, I am happy to see that third issue of 2019 of India Council (IC) newsletter is being released. The newsletter is having information of India Council, Sections, Chapters, Affinity Groups etc., interesting articles on diverse fields of interest to our members along with few regular informative columns. I congratulate and thank the efforts taken by Mr. H.R. Mohan, Newsletter Editor. I would also like to put on record and thank the Section leaders who have extended their cooperation in providing the inputs to the newsletter. The flagship technical conference of India Council, INDICON-2019, will be held in Marwadi University, Rajkot, Gujarat in collaboration with IEEE Gujarat Section during December 13-15, 2019. Paper submission deadline is over, however, paper submission for focused session and M V Chouhan Paper contest is open till September 25, 2019. All India Student, Women in Engineering and Young Professional Congress (AISWYC) is to be held in Hyderabad during September 28-30, 2019. I am happy to share that Github, IEEE ComSoc, IEEE MTT-S, IEEE TEMS, and IEEE SPAA have sponsored AISYWC and more than 400 delegates have registered for the same. This year Life Member track is added to the Congress. During this third quarter of 2019, IC EGM and EXCOM was held on 27th July in WTC Brigade Gateway, Bangalore and IEEE India Office, Bangalore respectively. IC Bylaws amendments proposed by IC EXCOM were ratified during the EGM. Adoption of amendments to Article II, IV, V, VI and VIII of IC Bylaws in respect of objective, management, nomination and election of officers, eligibility criterion and finances were ratified by the general assembly. -

Nominations for Padma Awards 2011
c Nominations fof'P AWARDs 2011 ADMA ~ . - - , ' ",::i Sl. Name';' Field State No ShriIshwarappa,GurapJla Angadi Art Karnataka " Art-'Cinema-Costume Smt. Bhanu Rajopadhye Atharya Maharashtra 2. Designing " Art - Hindustani 3. Dr; (Smt.).Prabha Atre Maharashtra , " Classical Vocal Music 4. Shri Bhikari.Charan Bal Art - Vocal Music 0, nssa·' 5. Shri SamikBandyopadhyay Art - Theatre West Bengal " 6: Ms. Uttara Baokar ',' Art - Theatre , Maharashtra , 7. Smt. UshaBarle Art Chhattisgarh 8. Smt. Dipali Barthakur Art " Assam Shri Jahnu Barua Art - Cinema Assam 9. , ' , 10. Shri Neel PawanBaruah Art Assam Art- Cinema Ii. Ms. Mubarak Begum Rajasthan i", Playback Singing , , , 12. ShriBenoy Krishen Behl Art- Photography Delhi " ,'C 13. Ms. Ritu Beri , Art FashionDesigner Delhi 14. Shri.Madhur Bhandarkar Art - Cinema Maharashtra Art - Classical Dancer IS. Smt. Mangala Bhatt Andhra Pradesh Kathak Art - Classical Dancer 16. ShriRaghav Raj Bhatt Andhra Pradesh Kathak : Art - Indian Folk I 17., Smt. Basanti Bisht Uttarakhand Music Art - Painting and 18. Shri Sobha Brahma Assam Sculpture , Art - Instrumental 19. ShriV.S..K. Chakrapani Delhi, , Music- Violin , PanditDevabrata Chaudhuri alias Debu ' Art - Instrumental 20. , Delhi Chaudhri ,Music - Sitar 21. Ms. Priyanka Chopra Art _Cinema' Maharashtra 22. Ms. Neelam Mansingh Chowdhry Art_ Theatre Chandigarh , ' ,I 23. Shri Jogen Chowdhury Art- Painting \VesfBengal 24.' Smt. Prafulla Dahanukar Art ~ Painting Maharashtra ' . 25. Ms. Yashodhara Dalmia Art - Art History Delhi Art - ChhauDance 26. Shri Makar Dhwaj Darogha Jharkhand Seraikella style 27. Shri Jatin Das Art - Painting Delhi, 28. Shri ManoharDas " Art Chhattisgarh ' 29. , ShriRamesh Deo Art -'Cinema ,Maharashtra Art 'C Hindustani 30. Dr. Ashwini Raja Bhide Deshpande Maharashtra " classical vocalist " , 31. ShriDeva Art - Music Tamil Nadu Art- Manipuri Dance 32. -

NAAC Re-Accreditation Self Study Report
UNIVERSITY COLLEGE THIRUVANANTHAPURAM - 695 034 SELF STUDY REPORT SUBMITTED FOR REACCREDITATION TO NATIONAL ASSESSMENT AND ACCREDITATION COUNCIL BANGALORE - 560 072 2 NAAC Re-Accreditation Committee University College, Thiruvananthapuram Dr. B. S. Mohanachandran (Principal) Patron (Ex-officio) Dr. R. Anilkumar (Dept. of Geography) General Convenor Dr. K. P. Jaikiran (Dept. of Geology) Co-ordinator, IQAC Members Dr.S. Unnikrishnan Nair - (Vice-Principal) Sri. G. Rajeev - (Dept. of Chemistry) Sri. K. Gopalakrishnan - (Dept. of English) Dr. Thomas Kuruvilla - (Dept. of English) Dr. Francis Sunny - (Dept. of Zoology) Dr. Philip Samuel - (Dept. of Statistics) Sri. M.B. Salim - (Dept. of Geography) Sri. P. Surendran - (Dept. of Physical Education) 3 Contents Page No. PREFACE Part I - INSTITUTIONAL DATA 01 - 44 Profile of the Institution Criterion wise input Profiles of the departments Part II - EVALUATIVE REPORT 45 – 400 Stand out facts Executive summary Criterion wise evaluative report Evaluative report of Departments Declaration by the Principal 4 PREFACE University College, Thiruvananthapuram (estd.1866) occupies a position of eminence among the colleges in the state of Kerala and that of a hallowed alma mater among the millions of students, including luminaries like the late Dr K R Narayanan, the former President of India and Dr. G Madhavan Nair, former Director, Indian Space Research Organisation. The college, situated in the heart of Trivandrum, the capital city of Kerala is unique in more than one respect: more than sixty per cent of its teachers are research degree holders; the college has fourteen research departments offering M.Phil. and PhD; and its student strength of 3200* includes enrolment from all social classes. -

The Greater Manchester Fringe
\\\\\\\ THE GREATER MANCHESTER FRINGE \\\\\\\ \\\\\\\24TH JUNE - 31ST JULY 2016 www.greatermanchesterfringe.co.uk \\\\\\\ \\\\\\\ Welcome to the 5th ever Greater Manchester Fringe! The programme this summer is bigger and more eclectic than ever. We hope there’s a little something for everyone. A big THANK YOU to all our participants for getting involved in this truly grass roots Fringe. Lets hope the rain stays off and here’s to an excellent summer of Fringe fun! x Lisa, Iain, Zena, Vicky, Debbie, Lola, Violet Chadderton and Shay xxx Chortle The Dancehouse Fast Fringe 24 June: 8pm So many comedians, so little time! More top comedy and variety acts than you thought possible on one bill perform ridiculously short sets in one furiously fast-paced £15.00 (concs £12.00) showcase. It’s a hugely entertaining way to sample the best of what’s coming up at the comedy Greater Manchester Fringe, all held together by compere Justin Moorhouse. ‘A brilliant concept... for variety and value for money‚- a no-brainer’ BroadwayBaby.com THE GREATER MANCHESTER FRINGE 2 www.greatermanchesterfringe.co.uk Inkbrew Productions Bandit Mugger & Thief Die Diana 29, 30 June Die Diana is a dark comedy exploring the afterlife of Princess Diana, the People’s 3, 4, 5, 6 July: 7.30pm Princess. On the 20th anniversary of her death, three people step out of the shadows and lay claim to her title. Each one has a story to tell about what really happened to £10.00 (concs £8.00) her then and since. But who do you believe, if any? And why? play ’Die Diana’ is hilarious, unnerving and utterly compelling, part homage, part horror show, a play like no other. -
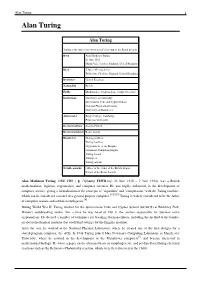
Alan Turing 1 Alan Turing
Alan Turing 1 Alan Turing Alan Turing Turing at the time of his election to Fellowship of the Royal Society. Born Alan Mathison Turing 23 June 1912 Maida Vale, London, England, United Kingdom Died 7 June 1954 (aged 41) Wilmslow, Cheshire, England, United Kingdom Residence United Kingdom Nationality British Fields Mathematics, Cryptanalysis, Computer science Institutions University of Cambridge Government Code and Cypher School National Physical Laboratory University of Manchester Alma mater King's College, Cambridge Princeton University Doctoral advisor Alonzo Church Doctoral students Robin Gandy Known for Halting problem Turing machine Cryptanalysis of the Enigma Automatic Computing Engine Turing Award Turing test Turing patterns Notable awards Officer of the Order of the British Empire Fellow of the Royal Society Alan Mathison Turing, OBE, FRS ( /ˈtjʊərɪŋ/ TEWR-ing; 23 June 1912 – 7 June 1954), was a British mathematician, logician, cryptanalyst, and computer scientist. He was highly influential in the development of computer science, giving a formalisation of the concepts of "algorithm" and "computation" with the Turing machine, which can be considered a model of a general purpose computer.[1][2][3] Turing is widely considered to be the father of computer science and artificial intelligence.[4] During World War II, Turing worked for the Government Code and Cypher School (GC&CS) at Bletchley Park, Britain's codebreaking centre. For a time he was head of Hut 8, the section responsible for German naval cryptanalysis. He devised a number of techniques for breaking German ciphers, including the method of the bombe, an electromechanical machine that could find settings for the Enigma machine. -

Manchester-Visitor-Info-V.01.19.Pdf
Manchester Visitor Information What to see and do in Manchester Manchester is a city waiting to be discovered There is more to Manchester than meets the eye; it’s a city just waiting to be discovered. From superb shopping areas and exciting nightlife to a vibrant history and contrasting vistas, Manchester really has everything. It is a modern city that is Throw into the mix an dynamic, welcoming and impressive range of galleries energetic with stunning and museums (the majority architecture, fascinating of which offer free entry) and museums, award winning visitors are guaranteed to be attractions and a burgeoning stimulated and invigorated. restaurant and bar scene. Manchester has a compact Manchester is a hot-bed of and accessible city centre. cultural activity. From the All areas are within walking thriving and dominant music distance, but if you want scene which gave birth to to save energy, hop onto sons as diverse as Oasis and the Metrolink tram or jump the Halle Orchestra; to one of aboard the free Mettroshuttle the many world class festivals bus. and the rich sporting heritage. We hope you have a wonderful visit. Manchester History Manchester has a unique history and heritage from its early beginnings as the Roman Fort of ‘Mamucium’ [meaning breast-shape hill], to today’s reinvented vibrant and cosmopolitan city. Known as ‘King Cotton’ or ‘Cottonopolis’ during the 19th century, Manchester played a unique part in changing the world for future generations. The cotton and textile industry turned Manchester into the powerhouse of the Industrial Revolution. Leaders of commerce, science and technology, like John Dalton and Richard Arkwright, helped create a vibrant and thriving economy.