Bih Fei Jong Thesis
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Digital Video Quality Handbook (May 2013
Digital Video Quality Handbook May 2013 This page intentionally left blank. Executive Summary Under the direction of the Department of Homeland Security (DHS) Science and Technology Directorate (S&T), First Responders Group (FRG), Office for Interoperability and Compatibility (OIC), the Johns Hopkins University Applied Physics Laboratory (JHU/APL), worked with the Security Industry Association (including Steve Surfaro) and members of the Video Quality in Public Safety (VQiPS) Working Group to develop the May 2013 Video Quality Handbook. This document provides voluntary guidance for providing levels of video quality in public safety applications for network video surveillance. Several video surveillance use cases are presented to help illustrate how to relate video component and system performance to the intended application of video surveillance, while meeting the basic requirements of federal, state, tribal and local government authorities. Characteristics of video surveillance equipment are described in terms of how they may influence the design of video surveillance systems. In order for the video surveillance system to meet the needs of the user, the technology provider must consider the following factors that impact video quality: 1) Device categories; 2) Component and system performance level; 3) Verification of intended use; 4) Component and system performance specification; and 5) Best fit and link to use case(s). An appendix is also provided that presents content related to topics not covered in the original document (especially information related to video standards) and to update the material as needed to reflect innovation and changes in the video environment. The emphasis is on the implications of digital video data being exchanged across networks with large numbers of components or participants. -

2020 Spring Product Guide Final-Min
2020 SPRING INTEGRATOR PRODUCT GUIDE COME SWIM WITH THE BIG FISH November 9 – 11, 2020 | Cleveland, OH | Huntington Convention Center Take control of your business success. Gain insights from the integration industry elite this November at Total Tech Summit. This uniquely powerful by invitation-only event drives extraordinary progress in the integration industry. Total Tech Summit is where the industry elite gather. Total Tech Summit helps to grow and improve your company through: › Educational, deep-dive sessions from the industry elite › 1-on-1 and boardroom meetings with new vendors that can take your offerings from better to best › Networking at every turn. Connect with both integrators in your industry and beyond to help give you fresh ideas and business strategies › Complimentary flights, hotel, “Gathering of professionals that registration, and meals to help you are non-competition to collaborate focus on what matters most on ideas to grow business in profits, procurement, strategies, staffing and general business practices is a wealth of knowledge at the cost of a couple days’ time and to also have the added benefit of meeting one on one with manufacturers that you may not have reached out to.” — John Rudolph, Vice President, PCD To learn more and to apply to join the best in the industry, please visit www.totaltechsummit.com Table of Contents Page 6 Audio ▶ Page 23 Control/Networking/Energy Management ▶ Page 36 Home Enhancements (central vacuum, wire and cable, tools, testers, furniture) ▶ Page 48 Security ▶ Page 53 Video ▶ Page -

Digital Video Quality Handbook
Digital Video Quality Handbook May 2013 This page intentionally left blank. CONTENTS Contents ......................................................................................................................................... 3 1. Introduction ................................................................................................................................. 5 2. Acknowledgements ..................................................................................................................... 5 3. Scope ........................................................................................................................................... 5 4. Compliance and Best Practices ................................................................................................... 5 4.1 Purpose .......................................................................................................................... 6 4.2 Application .................................................................................................................... 7 5. Use Cases ..................................................................................................................................... 7 5.1 Video Surveillance Use Cases ....................................................................................... 7 5.2 Other Use Case Considerations ..................................................................................... 8 6. Equipment ................................................................................................................................... -

Infocommshow.Org
SHOW GUIDE infocommshow.org Wow! What a Week! Welcome to the InfoComm 2015 experience! By now, you’ve heard InfoComm talking about “the exceptional experience.” For us, this means that AV Table of Contents service providers work to ensure their clients’ goals Executive Director’s Welcome � � � � � � � � � � � � �1 are achieved and expectations exceeded. And once General Show Information� � � � � � � � � � � � � � � � �2 your clients have experienced how good AV can be, Schedule at a Glance � � � � � � � � � � � � � � � � � � 4-5 they’ll want more of it! Shuttle Information � � � � � � � � � � � � � � � � � � � � � �6 At InfoComm 2015, with the show theme of “Wow!”, our InfoComm 2015 Sponsors/Partners � � � � � � 8-10 job is to help you achieve your goals and exceed your InfoComm 2015 Opening Keynote� � � � � � � � � �12 expectations. If you don’t leave InfoComm 2015 saying “Wow!”, then we haven’t done our job. InfoComm 2015 Opening Reception � � � � � � � �12 Special Events � � � � � � � � � � � � � � � � � � � � � � � �14 We have new exhibitors, new technology categories InfoComm by Interest/Pavilion � � � � � � � � � � 16-18 represented, and more than 10,000 new products to see. I can’t wait to welcome you as you explore the Who’s Who at InfoComm International � � � � 20-21 latest technology, connect with your friends and learn InfoComm 2015 Speakers � � � � � � � � � � � � 22-23 through InfoComm’s industry education and product-specific Manufacturers’ Training. InfoComm International Awards � � � � � � � � � 24-27 More than half of our educational sessions are new, and I’m sure will give you the Display Summit � � � � � � � � � � � � � � � � � � � � � � �28 answers and spark the innovation you need to succeed in your business. AV Tech Tours � � � � � � � � � � � � � � � � � � � � � � � �29 When you attend InfoComm you are attending many shows at once. We have more floor InfoComm University’s Three-Day Courses � � �30 space devoted to digital signage solutions or conferencing than any other show in the InfoComm University’s world. -

ONVIF Streaming Specification
ONVIF™ – 1 – Streaming – Ver. 21.06 ONVIF™ Streaming Specification Version 21.06 June, 2021 ONVIF™ – 2 – Streaming – Ver. 21.06 Copyright © 2008-2021 ONVIF™ All rights reserved. Recipients of this document may copy, distribute, publish, or display this document so long as this copyright notice, license and disclaimer are retained with all copies of the document. No license is granted to modify this document. THIS DOCUMENT IS PROVIDED "AS IS," AND THE CORPORATION AND ITS MEMBERS AND THEIR AFFILIATES, MAKE NO REPRESENTATIONS OR WARRANTIES, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO, WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, NON-INFRINGEMENT, OR TITLE; THAT THE CONTENTS OF THIS DOCUMENT ARE SUITABLE FOR ANY PURPOSE; OR THAT THE IMPLEMENTATION OF SUCH CONTENTS WILL NOT INFRINGE ANY PATENTS, COPYRIGHTS, TRADEMARKS OR OTHER RIGHTS. IN NO EVENT WILL THE CORPORATION OR ITS MEMBERS OR THEIR AFFILIATES BE LIABLE FOR ANY DIRECT, INDIRECT, SPECIAL, INCIDENTAL, PUNITIVE OR CONSEQUENTIAL DAMAGES, ARISING OUT OF OR RELATING TO ANY USE OR DISTRIBUTION OF THIS DOCUMENT, WHETHER OR NOT (1) THE CORPORATION, MEMBERS OR THEIR AFFILIATES HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES, OR (2) SUCH DAMAGES WERE REASONABLY FORESEEABLE, AND ARISING OUT OF OR RELATING TO ANY USE OR DISTRIBUTION OF THIS DOCUMENT. THE FOREGOING DISCLAIMER AND LIMITATION ON LIABILITY DO NOT APPLY TO, INVALIDATE, OR LIMIT REPRESENTATIONS AND WARRANTIES MADE BY THE MEMBERS AND THEIR RESPECTIVE AFFILIATES TO THE CORPORATION AND OTHER MEMBERS IN CERTAIN WRITTEN POLICIES OF THE CORPORATION. ONVIF™ – 3 – Streaming – Ver. 21.06 CONTENTS 1 Scope 5 2 Normative references 5 3 Terms and Definitions 6 3.1 Definitions ............................................................................................................................... -

ONVIF-Streaming-Spec-V210.Pdf
ONVIF™ – 1 – Streaming Spec. – Ver. 2.10 ONVIF™ Streaming Specification Version 2.1 June, 2011 ONVIF™ – 2 – Streaming Spec. – Ver. 2.10 2008-2011 by ONVIF: Open Network Video Interface Forum Inc.. All rights reserved. Recipients of this document may copy, distribute, publish, or display this document so long as this copyright notice, license and disclaimer are retained with all copies of the document. No license is granted to modify this document. THIS DOCUMENT IS PROVIDED "AS IS," AND THE CORPORATION AND ITS MEMBERS AND THEIR AFFILIATES, MAKE NO REPRESENTATIONS OR WARRANTIES, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO, WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, NON-INFRINGEMENT, OR TITLE; THAT THE CONTENTS OF THIS DOCUMENT ARE SUITABLE FOR ANY PURPOSE; OR THAT THE IMPLEMENTATION OF SUCH CONTENTS WILL NOT INFRINGE ANY PATENTS, COPYRIGHTS, TRADEMARKS OR OTHER RIGHTS. IN NO EVENT WILL THE CORPORATION OR ITS MEMBERS OR THEIR AFFILIATES BE LIABLE FOR ANY DIRECT, INDIRECT, SPECIAL, INCIDENTAL, PUNITIVE OR CONSEQUENTIAL DAMAGES, ARISING OUT OF OR RELATING TO ANY USE OR DISTRIBUTION OF THIS DOCUMENT, WHETHER OR NOT (1) THE CORPORATION, MEMBERS OR THEIR AFFILIATES HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES, OR (2) SUCH DAMAGES WERE REASONABLY FORESEEABLE, AND ARISING OUT OF OR RELATING TO ANY USE OR DISTRIBUTION OF THIS DOCUMENT. THE FOREGOING DISCLAIMER AND LIMITATION ON LIABILITY DO NOT APPLY TO, INVALIDATE, OR LIMIT REPRESENTATIONS AND WARRANTIES MADE BY THE MEMBERS AND THEIR RESPECTIVE AFFILIATES TO THE CORPORATION AND OTHER MEMBERS IN CERTAIN WRITTEN POLICIES OF THE CORPORATION. ONVIF™ – 3 – Streaming Spec. – Ver. -

ONVIF Core Specification
Open Network Video Interface Forum – 1 – ONVIF Core Spec. – Ver. 1.02 Open Network Video Interface Forum Core Specification Version 1.02 June, 2010 Open Network Video Interface Forum – 2 – ONVIF Core Spec. – Ver. 1.02 2008-2010 by ONVIF: Open Network Video Interface Forum. All rights reserved. Recipients of this document may copy, distribute, publish, or display this document so long as this copyright notice, license and disclaimer are retained with all copies of the document. No license is granted to modify this document. THIS DOCUMENT IS PROVIDED "AS IS," AND THE CORPORATION AND ITS MEMBERS AND THEIR AFFILIATES, MAKE NO REPRESENTATIONS OR WARRANTIES, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO, WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, NON-INFRINGEMENT, OR TITLE; THAT THE CONTENTS OF THIS DOCUMENT ARE SUITABLE FOR ANY PURPOSE; OR THAT THE IMPLEMENTATION OF SUCH CONTENTS WILL NOT INFRINGE ANY PATENTS, COPYRIGHTS, TRADEMARKS OR OTHER RIGHTS. IN NO EVENT WILL THE CORPORATION OR ITS MEMBERS OR THEIR AFFILIATES BE LIABLE FOR ANY DIRECT, INDIRECT, SPECIAL, INCIDENTAL, PUNITIVE OR CONSEQUENTIAL DAMAGES, ARISING OUT OF OR RELATING TO ANY USE OR DISTRIBUTION OF THIS DOCUMENT, WHETHER OR NOT (1) THE CORPORATION, MEMBERS OR THEIR AFFILIATES HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES, OR (2) SUCH DAMAGES WERE REASONABLY FORESEEABLE, AND ARISING OUT OF OR RELATING TO ANY USE OR DISTRIBUTION OF THIS DOCUMENT. THE FOREGOING DISCLAIMER AND LIMITATION ON LIABILITY DO NOT APPLY TO, INVALIDATE, OR LIMIT REPRESENTATIONS AND WARRANTIES MADE BY THE MEMBERS AND THEIR RESPECTIVE AFFILIATES TO THE CORPORATION AND OTHER MEMBERS IN CERTAIN WRITTEN POLICIES OF THE CORPORATION. -
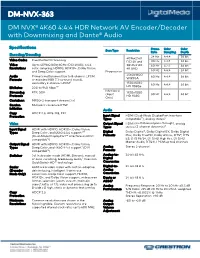
DM-NVX-363 DM NVX® 4K60 4:4:4 HDR Network AV Encoder/Decoder with Downmixing and Dante® Audio
DM-NVX-363 DM NVX® 4K60 4:4:4 HDR Network AV Encoder/Decoder with Downmixing and Dante® Audio Specifications Frame Color Color Scan Type Resolution Rate Sampling Depth Encoding/Decoding 24 Hz 4:4:4 36 bit 4096x2160 Video Codec Pixel Perfect Processing DCI 4K and 30 Hz 4:4:4 36 bit Video Up to 4096x2160@60Hz (DCI 4K60); 4:4:4 3840x2160 60 Hz 4:2:2 36 bit Resolutions color sampling; HDR10, HDR10+, Dolby Vision, 4K UHD and Deep Color support Progressive 60 Hz 4:4:4 24 bit 2560x1600 Audio Primary multichannel (up to 8-channel LPCM 60 Hz 4:4:4 36 bit WQXGA Formats or encoded HBR 7.1 surround sound), 9 1920x1080 secondary 2-channel LPCM 60 Hz 4:4:4 36 bit HD 1080p Bit Rates 200 to 950 Mbps10 Interlaced Streaming RTP, SDP 1920x1080 (Input 30 Hz 4:4:4 36 bit Protocols HD 1080i Only) Container: MPEG-2 transport stream (.ts) Session Multicast via secure RTSP Initiation Audio Copy HDCP 2.3, AES-128, PKI Protection Input Signal HDMI (Dual-Mode DisplayPort interface Types compatible12), analog stereo5 Video Output Signal HDMI (multichannel pass-through), analog Types stereo (2-channel downmix)5 Input Signal HDMI with HDR10, HDR10+, Dolby Vision, Types Deep Color, and 4K60 4:4:4 support1, 11 Digital Dolby Digital®, Dolby Digital EX, Dolby Digital (Dual-Mode DisplayPort™ interface and DVI Formats Plus, Dolby TrueHD, Dolby Atmos, DTS®, DTS compatible12) ES, DTS 96/24, DTS HD High Res, DTS HD Master Audio, DTS:X, LPCM up to 8 channels Output Signal HDMI with HDR10, HDR10+, Dolby Vision, Types Deep Color, and 4K60 4:4:4 support1 (DVI Analog Stereo 2-channel