NSO Group) Affiliated with the Years in Jail
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Analysys Mason Document
COVID-19: operators in the UAE should prepare for a gradual lift of the ban on VoIP apps after the crisis April 2020 Karim Yaici Telecoms regulators in Oman and the UAE lifted the ban on selected OTT VoIP and video conferencing apps (including Skype for Business and Zoom) in March 2020 to enable people to work and study from home in compliance with the social distancing guidelines brought in to combat the COVID-19 outbreak. However, popular consumer OTT apps such as WhatsApp and Skype were excluded from the list of authorised apps. The exceptional measures taken by the regulators are likely to last for at least a few weeks. The pressure from the public to extend this period and expand the list of permitted applications will increase, especially in the UAE. In this comment, we share results from Analysys Mason’s Connected Consumer Survey regarding the penetration of OTT services in the UAE, and argue that operators in the country should do more to prepare for the possibility of increased competition from OTT players post-crisis. OTT communications apps remain very popular in Oman and the UAE, despite regulators’ attempts to block or disrupt them Telecoms regulators in Oman and the UAE have adopted a strong defensive stance against OTT players by blocking the voice and video calling features of most OTT communications apps. In contrast, regulators in other countries in the Gulf Co-operation Council (Bahrain, Kuwait, Qatar and Saudi Arabia) have gradually allowed more OTT apps to be used, including WhatsApp. Operators in Oman and the UAE have enforced this ban while partnering with third-party OTT service providers, such as BOTIM, to offer app-to-app calling tariffs (in the UAE) and OTT apps for making international calls (such as Ooredoo Talk in Oman). -

Dubai, UAE February 17-18, 2020 #GTRMENA
Dubai, UAE #GTRMENA www.gtreview.com February 17-18, 2020 OVERVIEW Once registered, log-in to GTR Connect to network with fellow delegates, download event Widely recognised as the most comprehensive materials and more. and long-established trade finance gathering for the Middle East, GTR MENA 2020 will return to Dubai on February 17-18, 2020. The event is set to welcome over 800 key figures from the As the world’s leading trade, commodity and export regional and global markets and provide access to hundreds of finance publisher and event organiser,GTR offers companies engaged in international trade, all of whom are keen sponsors and advertisers unrivalled exposure and to discuss their financing priorities and the future of trade in the profiling among their peer and client groups.GTR can Middle East. offer various appealing options that would strategically and effectively help raise the profile of the partner, Agenda themes for consideration will range from geopolitical and offer a highly effective platform with which to tensions to the region’s many infrastructure demands and showcase its capabilities and mission. requirements, the role of new technologies and innovations to creating a thriving environment for conducting trade business, offering an unrivalled platform for growing awareness of market challenges. Sponsorship opportunities Ed Virtue Director, Global Sales [email protected] “Excellent event, great opportunity to promote +44 (0)20 8772 3008 the bank to peers and corporates.” O Thompson, Wyelands Bank Speaking opportunities -

International Academy for Case Studies
Volume 12, Number 2 2005 Allied Academies International Conference Las Vegas, Nevada October 12-15, 2005 International Academy for Case Studies PROCEEDINGS Volume 12, Number 2 2005 page ii Allied Academies International Conference Las Vegas, 2005 Proceedings of the International Academy for Case Studies, Volume 12, Number 2 Allied Academies International Conference page iii Table of Contents A PROPOSED CURRENCY ARRANGEMENT FOR PALESTINE.......................................................1 Vaughn S. Armstrong, Utah Valley State College Cody G. Boyd, University of Illinois Norman D. Gardner, Utah Valley State College THIS PIZZA PARLOR’S FOR SALE .............................................3 Joyce M. Beggs, The University of North Carolina at Charlotte I. E. Jernigan, III, The University of North Carolina at Charlotte Gerald E. Calvasina, Southern Utah University WHAT NEXT FOR KROGER? ..................................................5 Thomas Bertsch, James Madison University ENTERPRISE NATIONAL BANK: A STUDY IN COST CONTROL ...........................................7 James Bexley, Sam Houston State University RYANAIR (2005): SUCCESSFUL LOW COST LEADERSHIP ..................................9 Thomas M. Box, Pittsburg State University Kent Byus, Texas A&M University – Corpus Christi START-UP CULTURE AT TOPS ...............................................15 Steve Brown, Eastern Kentucky University Peggy Brewer, Eastern Kentucky University Kambiz Tabibzadeh, Eastern Kentucky University JEFF GILLUM’S NEW VENTURE..............................................19 -

Press Release Future Group Announces Joint Venture with Axiom Telecom LLC Mumbai, July 20, 2007
Press Release Future Group announces Joint Venture with Axiom Telecom LLC Mumbai, July 20, 2007: Future Group today announced that it‟s flagship company Pantaloon Retail (I) Ltd. has signed a 50:50 joint venture agreement with the UAE based, Axiom Telecom LLC, the largest authorized distributor, retailer and after sales support provider of mobile phones, phone accessories, wireless gadgets, memory & storage devices in the Middle East. The new company will focus on developing backend sourcing infrastructure for the Pantaloon Retail‟s existing telecom retailing business, to enable it to expand and scale up, exponentially. Additionally, it will also create a nationwide network of state-of-the-art after sales service centers for mobile handsets in the country. Said Mr. Kishore Biyani, Group CEO, Future Group, “The current explosion of the telecom retail market that we are seeing, is breaking new barriers every day. There is no doubt that mobiles will soon be the single largest electronic products retailed in the country. Future Group, with the knowledge and expertise of Axiom Telecom‟s systems and process in this area, will be best positioned to retail and service the Indian telecom market.” Said, Mr. Faisal Al Bannai, CEO, Axiom Telecom LLC, “We see great business potential in India for distribution & servicing of telecom products, and are delighted to partner with Future Group, the largest retailer in the country. We believe that our expertise in distribution and after sales service operations, and Future Group‟s understanding of the Indian consumer and the marketplace, will create a win-win for us, as well as the Indian consumers.” The joint venture activities would be carried out by a separate company. -

Data Is Dangerous: Comparing the Risks That the United States, Canada and Germany See in Data Troves
Institute for International Economic Policy Working Paper Series Elliott School of International Affairs The George Washington University Data Is Dangerous: Comparing the Risks That the United States, Canada and Germany See in Data Troves IIEP-WP-2020-5 Susan A. Aaronson George Washington University April 2020 Institute for International Economic Policy 1957 E St. NW, Suite 502 Voice: (202) 994-5320 Fax: (202) 994-5477 Email: [email protected] Web: iiep.gwu.edu CIGI Papers No. 241 — April 2020 Data Is Dangerous: Comparing the Risks That the United States, Canada and Germany See in Data Troves Susan Ariel Aaronson CIGI Papers No. 241 — April 2020 Data Is Dangerous: Comparing the Risks That the United States, Canada and Germany See in Data Troves Susan Ariel Aaronson About CIGI Credits The Centre for International Governance Innovation (CIGI) is an independent, non- Director, Global Economy Robert Fay partisan think tank whose peer-reviewed research and trusted analysis influence Program Manager Heather McNorgan policy makers to innovate. Our global network of multidisciplinary researchers and strategic partnerships provide policy solutions for the digital era with one goal: to Publications Editor Susan Bubak improve people’s lives everywhere. Headquartered in Waterloo, Canada, CIGI Senior Publications Editor Jennifer Goyder has received support from the Government of Canada, the Government of Ontario Graphic Designer Brooklynn Schwartz and founder Jim Balsillie. À propos du CIGI Le Centre pour l’innovation dans la gouvernance internationale (CIGI) est un groupe de réflexion indépendant et non partisan dont les recherches evaluées par des pairs et les analyses fiables incitent les décideurs à innover. -
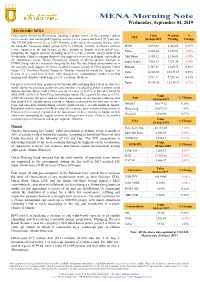
MSM Index: 53
MENA Morning Note Wednesday, September 04, 2019 ECONOMIC NEWS China stocks firmed on Wednesday, bucking a global retreat, as the country’s upbeat Value Previous % GCC service sector data outweighed lingering worries over a protracted Sino-U.S. trade war. 03-Sep-2019 Closing Change The CSI300 index rose 0.1% to 3,859.14 points at the end of the morning session, while the Shanghai Composite Index gained 0.2% to 2,936.68. Activity in China’s services MSM 4,016.62 4,002.66 0.35% sector expanded at the fastest pace in three months in August as new orders rose, Dubai 2,876.44 2,889.81 -0.46% prompting the biggest increase in hiring in over a year, a private survey showed on Wednesday. China’s economy showed clear signs of a recovery in August, especially in Abu Dhabi 5,105.12 5,156.01 -0.99% the employment sector, Zhong Zhengsheng, director of Macroeconomic Analysis at Saudi Arabia 7,924.18 7,971.14 -0.59% CEBM Group, said in a statement alongside the data The data helped offset worries over the year-long trade dispute, which has strained economic growth in China and the United Bahrain 1,543.18 1,540.75 0.16% States. U.S. President Donald Trump on Tuesday warned he would be “tougher” on Qatar 10,300.01 10,274.15 0.25% Beijing in a second term if trade talks dragged on, compounding market fears that ongoing trade disputes could trigger a U.S. recession. (Reuters) Kuwait 5,961.32 5,953.50 0.13% Egypt 14,999.58 15,110.23 -0.73% Oil prices recovered some ground on Wednesday after touching their lowest in close to a month during the previous session on concerns that a weakening global economy could 8,243.32 8,432.41 -2.24% depress demand. -

Interior Design, Contracting & Project Management
Interior Design, Contracting & Project Management CORAL SUPPLIES & INTERIORS LLC Deira Office Al Qusais Office Al Bakhit Centre Office 505 Al Habtoor Warehouse Complex Unit No 46 PO Box 24538 Dubai United Arab Emirates. PO Box 24538 Dubai United Arab Emirates. T: +971 4 2625261 F: +971 4 2664630 T: +971 4 2588732 F: +971 4 2588723 E: [email protected] W: www.csiuae.com E: [email protected] W: www.csiuae.com Design & Build Solutions INTERIOR PROJECT DESIGN MANAGEMENT TURNKEY TENNANT FITOUT CO-ORDINATION CONTRACTORS CIVIL & MEP SERVICES A wide range of specialist activities and experience including: l Turnkey Fit Out Contractors l Retail Design Consultants l Commercial Interior Design and Space Planning l Project Management l Islamic Design and Decorative Finishes l Tenant Co-ordination for Shopping Centres & Commercial Developments l F&B Design and Fit Out INTRODUCTION CSI is a specialist in Interior Design, Project Management and Fit Out Conntracting, offering a full range of professional services Based in Dubai since 1991, CSI has been involved in projects throughout the GCC region, Asia and Europe. PHILOSOPHY CSI sets a different approach. We firmly believe that good design can save our clients money. The object is to improve the efficiency and profitability of our client’s business. CSI is fully committed to sustainable use of materials and care of the environment. Our fit out work enforce health and safety procedures and fully commited to sustainable use of materials and the care of the environment. RETAIL CSI offer a dedicated service covering all aspects of interior design and fitout for shops and shopping malls. -

E-Commerce in MENA Report
E-commerce in MENA Opportunity beyond the hype Disclaimer This report was published by Google and Bain & Company for information purposes only. To the extent permitted by law, we do not represent or warrant that this report is reliable, accurate, complete. Accordingly, this report is made available for use “as is,” and any use thereof will be undertaken solely at your own risk. We reserve the right, in our sole discretion, to cease publishing this report at any time, and we do not give or enter into any conditions, warranties or other terms with regard to this report. In particular, no condition, warranty or other term is given or entered into to the effect that this report will be of satisfactory quality, noninfringement or that the report will be fit for any particular purpose. This work is based on secondary market research, analysis of financial information available or provided to Bain & Company and a range of interviews with industry participants. Bain & Company has not independently verified any such information provided or available to Bain and makes no representation or warranty, express or implied, that such information is accurate or complete. Projected market and financial information, analyses and conclusions contained herein are based on the information described above and on Bain & Company’s judgment, and should not be construed as definitive forecasts or guarantees of future performance or results. The information and analysis herein do not constitute advice of any kind, are not intended to be used for investment purposes, and neither Bain & Company nor any of its subsidiaries or their respective officers, directors, shareholders, employees or agents accept any responsibility or liability with respect to the use of or reliance on any information or analysis contained in this document. -

Indian Telcos Asked to Enable Social App Blocks Following Attacks
Indian Telcos Asked To Enable Social App Blocks Following Attacks ERROR_GETTING_IMAGES-1 Indian Telcos Asked To Enable Social App Blocks Following Attacks 1 / 4 2 / 4 A GPRS-enabled mobile phone uses packet mode technique to transfer data and ... terrorist attacks across the city of Mumbai, India on 26th November, 2008. ... Government of India's Order dated 7thJuly, 2003 on the subject of Blocking of websites. ... widespread adoption of new telecom 506 Legal Regulation of Cybercafés.. ToTok, an Emirati messaging app that has been downloaded to millions of ... ToTok surged to become one of the most downloaded social apps in the ... The government blocks specific functions of apps like WhatsApp and ... Huawei, the Chinese telecom giant, recently promoted ToTok in advertisements. Delhi Police had requested Airtel/Vodafone/Idea/Jio/MTNL/BSNL to ... Related Article: CAA Protests: Internet Ban Hits Telcos The Hardest ... Vodafone India has also confirmed blocking internet and cellular services in parts of the city. ... in the light of the brutal attacks on students in many parts of the country.. The Telecom Regulatory Authority of India (TRAI) is a statutory body set up by the Government ... conditions for the growth of telecommunications in India to enable the country to ... On 6 June 2017, TRAI launched three new apps and a web portal to ensure ... "SC strikes down 'arbitrary, unconstitutional' call drop penalty".. Social media access in Valley: Telcos race to block VPNs ... A female journalist uses internet on her mobile phone after the ... internet service providers in the Valley to allow access to only white-listed websites, ... Stay up to date on all the latest Nation news with The New Indian Express App. -

Aed 2,599 Aed 549 Aed 2,899 Aed 2,599
SAVE سامسونج غالكسي إس ٧ إيدج SAVE آي فون ٧ iPhone 7 32GB AED Samsung Galaxy S7 Edge 32GB AED 499 1,995 + FERRARI WATCH + + Samsung Level U Headphones & Samsung Gear VR UAE Flag Edition Ferrari Watch 128GB Memory Card & Bluetooth speaker Worth AED 799 Worth AED 599 Worth AED 698 Worth AED 698 AED 3,398 4.7” A10 12 MP TOUCH ID 5.5” 4 GB 12 MP DUAL SCREEN CHIP CAMERA SENSOR AED 2,899 SCREEN RAM CAMERA SIM AED 2,599 SAVE إتش تي سي ديزاير ٨٢٠+ هواوي مايت ٩ Huawei Mate 9 64GB JUST HTC Desire 820G+ AED ARRIVED 299 FERRARI + WATCH Bluetooth speaker UAE Flag Edition Worth AED 299 Worth AED 799 AED 3,098 5.9” DUAL LENS 4 GB DUAL 5.5” 13 MP 2 GB DUAL SCREEN CAMERA RAM SIM AED 2,599 SCREEN CAMERA RAM SIM AED 549 December 2016 - V1 Shop online at www.axiomtelecom.com and get it delivered in 2 HOURS only SAVE UP TO AED 1,300 JUST PAY 1,799* & GET Samsung Galaxy S7 Edge 32GB YOUR ONE FREE STOP FREE 18 GB SHOP Data du Bronze 600 Number Flexi min AED 2,599 * 24 months contract AED 1,799 Choose from the following PROTECT WORTH AED 500 ENHANCE PERSONALIZE Choose your Choose your protection plan accessories Choose your style * With du Smart Plan 300. Conditions apply. FREE PHONE WORTH AED 300 WITH Smart plan 150* 300 6GB Flexi Data Minutes Smart plan 300* AED 400 12GB 600 Voucher Data Flexi Minutes FOR AS LOW AS AED 599* With Trade-in and select du plans ONLY AT AXIOM *Based on your old phone’s model and condition. -

Original Research Care, Support and Therapy Service of HIV Patients with the “SATE Krembung” Application
Jurnal Ners Vol. 14, No. 3, Special Issue 2019 This is an Open Access article distributed under the terms of the Creative Commons http://dx.doi.org/10.20473/jn.v14i3(si).17104 Attribution 4.0 International License Original Research Care, Support and Therapy Service of HIV Patients with the “SATE Krembung” Application Totok Indarto1, Arif Rahman Nurdianto2 and Dyah Ayu Febiyanti3 1 Faculty of Nursing, Universitas Airlangga, Surabaya, East Java, Indonesia 2 Primary Health Care of Trosobo, Sidoarjo, East Java, Indonesia 3 General Hospital of Sidoarjo, East Java, Indonesia ABSTRACT ARTICLE HISTORY Introduction: The prevalence and incidence of HIV and AIDS in Sidoarjo is Received: December 26, 2019 still high. Today, the adherence of patients to several ART services in Accepted: December 31, 2019 Sidoarjo is quite low and varied. Therefore the researchers want to find out the effectiveness of registration using “the SATE Krembung” application in KEYWORDS terms of service effectiveness, reducing the Lost Follow Up (LFU) and care; support; HIV; Sate Krembung; increasing patient adherence in Krembung Primary Health Care. Methods: The study was cross-sectional. The use of alternative ART service CONTACT modes was done via “the SATE Krembung” application as an integrated Totok Indarto queue system. The patients who participated in this study were HIV patients [email protected] at Krembung Primary Health Care who accessed ART at Krembung Primary Faculty of Nursing, Universitas Health Care within the age range of 20 - 60 years. The total number of Airlangga, Surabaya, Indonesia samples in this test was 16 patients. Results: Registration using “the SATE Krembung” application can reduce the waiting time for getting access to services for the HIV patients who plan on getting CST services and ART collection.