Security Measures in Openbsd
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Porting Darwin to the MV88F6281 Arming the Snowleopard
Porting Darwin to the MV88F6281 ARMing the SnowLeopard. Tristan Schaap 1269011 Apple Inc. Platform Technologies Group Delft University of Technology Dept. of Computer Science Committee: Ir. B.R. Sodoyer Dr. K. van der Meer Preface! 3 Introduction! 4 Summary! 5 Building a new platform! 6 Booting iBoot! 7 Building the kernelcache! 8 Booting the kernel! 10 THUMBs down! 16 Conclusion! 18 Future Work! 19 Glossary! 20 References! 21 Appendix A! 22 Appendix B! 23 Skills! 23 Process! 26 Reflection! 27 Appendix C! 28 Plan of Approach! 28 2 Preface Due to innovative nature of this project, I have had to limit myself in the detail in which I describe my work. This means that this report will be lacking in such things as product specific- and classified information. I would like to thank a few people who made it possible for me to successfully complete my internship at the Platform Technologies Group at Apple. First off, the people who made this internship possible, John Kelley, Ben Byer and my manager John Wright. Mike Smith, Tom Duffy and Anthony Yvanovich for helping me through the rough patches of this project. And the entirety of Core OS for making my stay an unforgettable experience. 3 Introduction About the Platform Technologies Group As it was described by a manager: “We do the plumbing, if we do our jobs right, you never see it.”. The Platform Technologies Group, a subdivision of the Core OS department, works on the embedded platforms that Apple maintains. Here, platforms are brought up and the embedded kernel and lower level support for the platforms is maintained. -

Linux on the Road
Linux on the Road Linux with Laptops, Notebooks, PDAs, Mobile Phones and Other Portable Devices Werner Heuser <wehe[AT]tuxmobil.org> Linux Mobile Edition Edition Version 3.22 TuxMobil Berlin Copyright © 2000-2011 Werner Heuser 2011-12-12 Revision History Revision 3.22 2011-12-12 Revised by: wh The address of the opensuse-mobile mailing list has been added, a section power management for graphics cards has been added, a short description of Intel's LinuxPowerTop project has been added, all references to Suspend2 have been changed to TuxOnIce, links to OpenSync and Funambol syncronization packages have been added, some notes about SSDs have been added, many URLs have been checked and some minor improvements have been made. Revision 3.21 2005-11-14 Revised by: wh Some more typos have been fixed. Revision 3.20 2005-11-14 Revised by: wh Some typos have been fixed. Revision 3.19 2005-11-14 Revised by: wh A link to keytouch has been added, minor changes have been made. Revision 3.18 2005-10-10 Revised by: wh Some URLs have been updated, spelling has been corrected, minor changes have been made. Revision 3.17.1 2005-09-28 Revised by: sh A technical and a language review have been performed by Sebastian Henschel. Numerous bugs have been fixed and many URLs have been updated. Revision 3.17 2005-08-28 Revised by: wh Some more tools added to external monitor/projector section, link to Zaurus Development with Damn Small Linux added to cross-compile section, some additions about acoustic management for hard disks added, references to X.org added to X11 sections, link to laptop-mode-tools added, some URLs updated, spelling cleaned, minor changes. -

Oracle Solaris 11.4 Security Target, V1.3
Oracle Solaris 11.4 Security Target Version 1.3 February 2021 Document prepared by www.lightshipsec.com Oracle Security Target Document History Version Date Author Description 1.0 09 Nov 2020 G Nickel Update TOE version 1.1 19 Nov 2020 G Nickel Update IDR version 1.2 25 Jan 2021 L Turner Update TLS and SSH. 1.3 8 Feb 2021 L Turner Finalize for certification. Page 2 of 40 Oracle Security Target Table of Contents 1 Introduction ........................................................................................................................... 5 1.1 Overview ........................................................................................................................ 5 1.2 Identification ................................................................................................................... 5 1.3 Conformance Claims ...................................................................................................... 5 1.4 Terminology ................................................................................................................... 6 2 TOE Description .................................................................................................................... 9 2.1 Type ............................................................................................................................... 9 2.2 Usage ............................................................................................................................. 9 2.3 Logical Scope ................................................................................................................ -

Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Android 4.4 home screen Company / developer Google Open Handset Alliance Android Open Source Project (AOSP) Programmed in C (core), C++, Java (UI) OS family Unix-like Working state Current Source model Open source with proprietary components Initial release September 23, 2008 Latest stable release 4.4.2 KitKat / December 9, 2013 Marketing target Smartphones Tablet computers Available language(s) Multi-lingual (46 languages) Package manager Google Play, APK Supported platforms 32-bit ARM, MIPS, x86 Kernel type Monolithic (modified Linux kernel) [1] [2] [3] Userland Bionic libc, shell from NetBSD, native core utilities with a few from NetBSD Default user interface Graphical (Multi-touch) License Apache License 2.0 Linux kernel patches under GNU GPL v2 [4] Official website www.android.com Android is an operating system based on the Linux kernel, and designed primarily for touchscreen mobile devices such as smartphones and tablet computers. Initially developed by Android, Inc., which Google backed financially Android (operating system) 2 and later bought in 2005, Android was unveiled in 2007 along with the founding of the Open Handset Alliance: a consortium of hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices. The first publicly available smartphone running Android, the HTC Dream, was released on October 22, 2008. The user interface of Android is based on direct manipulation, using touch inputs that loosely correspond to real-world actions, like swiping, tapping, pinching and reverse pinching to manipulate on-screen objects. Internal hardware such as accelerometers, gyroscopes and proximity sensors are used by some applications to respond to additional user actions, for example adjusting the screen from portrait to landscape depending on how the device is oriented. -

The Dragonflybsd Operating System
1 The DragonFlyBSD Operating System Jeffrey M. Hsu, Member, FreeBSD and DragonFlyBSD directories with slightly over 8 million lines of code, 2 million Abstract— The DragonFlyBSD operating system is a fork of of which are in the kernel. the highly successful FreeBSD operating system. Its goals are to The project has a number of resources available to the maintain the high quality and performance of the FreeBSD 4 public, including an on-line CVS repository with mirror sites, branch, while exploiting new concepts to further improve accessible through the web as well as the cvsup service, performance and stability. In this paper, we discuss the motivation for a new BSD operating system, new concepts being mailing list forums, and a bug submission system. explored in the BSD context, the software infrastructure put in place to explore these concepts, and their application to the III. MOTIVATION network subsystem in particular. A. Technical Goals Index Terms— Message passing, Multiprocessing, Network The DragonFlyBSD operating system has several long- operating systems, Protocols, System software. range technical goals that it hopes to accomplish within the next few years. The first goal is to add lightweight threads to the BSD kernel. These threads are lightweight in the sense I. INTRODUCTION that, while user processes have an associated thread and a HE DragonFlyBSD operating system is a fork of the process context, kernel processes are pure threads with no T highly successful FreeBSD operating system. Its goals are process context. The threading model makes several to maintain the high quality and performance of the FreeBSD guarantees with respect to scheduling to ensure high 4 branch, while exploring new concepts to further improve performance and simplify reasoning about concurrency. -

Least Privilege and Privilege Separation
CSE 127: Computer Security Least privilege and privilege separation Deian Stefan Slides adopted from John Mitchell, Dan Boneh, and Stefan Savage This week… • How to build secure systems ➤ Least privilege and privilege separation ➤ Sandboxing and isolation • Key is underlying principles not mechanisms ➤ We’re going to look at systems techniques ➤ Other ways to achieve similar goals: language-based Principles of secure design • Principle of least privilege • Privilege separation • Defense in depth ➤ Use more than one security mechanism ➤ Fail securely/closed • Keep it simple Principles of secure design • Principle of least privilege • Privilege separation • Defense in depth ➤ Use more than one security mechanism ➤ Fail securely/closed • Keep it simple Principle of Least Privilege Defn: A system should only have the minimal privileges needed for its intended purposes • What’s a privilege? ➤ Ability to access (e.g., read or write) a resource Principle of Least Privilege Defn: A system should only have the minimal privileges needed for its intended purposes • What’s a privilege? ➤ Ability to access (e.g., read or write) a resource Principle of Least Privilege Defn: A system should only have the minimal privileges needed for its intended purposes • What’s a privilege? ➤ Ability to access (e.g., read or write) a resource What’s the problem with this defn? • Talking about a huge, monolith system is not really useful • Why? Network Network User input User device File system File system Breaking a system into components • Compartmentalization and isolation ➤ Separate the system into isolated compartments ➤ Limit interaction between compartments • Why is this more meaningful? Network Network User input User device File system File system How dow we break things apart? Map compartment to user ids! • Recall: permissions in UNIX granted according to UID ➤ A process may access files, network sockets, …. -

New Concept of the Android Keystore Service with Regard to Security and Portability
University of Bremen Department of Mathematics and Computer Science New concept of the Android keystore service with regard to security and portability. Master’s Thesis by Fritjof Bornebusch reviewed by Dr. Karsten Sohr Prof. Dr. Jan Peleska supervised by Dipl. Inf. Florian Junge 2016 Confirmation I hereby confirm that I wrote this master thesis on my own and that I have used only the indicated references, resources, and aids. In German: Hiermit bestätige ich, dass ich die vorliegende Masterthesis selbstständig verfasst, und keine anderen als die angegebenen Quellen und Hilfsmittel verwendet habe. Bremen, 1/13/2016 Fritjof Bornebusch “Any fool can write code that a computer can understand. Good programmers write code that humans can understand.” – Martin Fowler – Bornebusch, Fritjof New concept of the Android keystore service with regard to security and portability. Master’s thesis, Department 3 - Mathematics / Computer Science University of Bremen, 2015 This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License (CC BY-NC-SA 4.0). To view a copy of this license, send an email to [email protected], visit http://creativecommons.org/licenses/by-nc-sa/4.0/ or send a letter to Creative Commons, PO Box 1866, Mountain View, California, 94042, USA. Table of Contents Acknowledgements 7 List of Figures 9 List of Listings 10 Acronyms 13 Glossary 15 1 Introduction 19 2 Background 24 2.1 Android System Architecture . 24 2.1.1 Security-Enhanced Linux . 28 2.1.2 Capabilities . 31 2.2 Memory Vulnerabilities . 32 2.2.1 Buffer Overflow Protection . 33 2.2.2 Dead Store Elimination . -

Integration of Security Measures and Techniques in an Operating System (Considering Openbsd As an Example)
Motivation Security Solutions and Techniques Summary Integration of Security Measures and Techniques in an Operating System (considering OpenBSD as an example) Igor Boehm Institute for Information Processing and Microprocessor Technology Johannes Kepler University Linz, Austria Igor Boehm Integration of Security Measures and Techniques in an OS Motivation Security Solutions and Techniques Summary Outline 1 Motivation The Basic Problem Being Studied Preliminary Solution Ideas and Goals 2 Security Solutions and Techniques Secure Software Design Techniques Memory Protection Techniques Relevance of Random Numbers for Security Igor Boehm Integration of Security Measures and Techniques in an OS Motivation The Basic Problem Being Studied Security Solutions and Techniques Preliminary Solution Ideas and Goals Summary Outline 1 Motivation The Basic Problem Being Studied Preliminary Solution Ideas and Goals 2 Security Solutions and Techniques Secure Software Design Techniques Memory Protection Techniques Relevance of Random Numbers for Security Igor Boehm Integration of Security Measures and Techniques in an OS Motivation The Basic Problem Being Studied Security Solutions and Techniques Preliminary Solution Ideas and Goals Summary The Basic Problem Being Studied The Clever Attacker: . finds a bug . knows how to craft an exploit . the exploit grants the attacker an advantage . the exploit is likely to work on many systems because of the strict regularity of the system environment Is there a way to solve this problem? Igor Boehm Integration of Security -

Z/OS Openssh User's Guide
z/OS Version 2 Release 4 z/OS OpenSSH User's Guide IBM SC27-6806-40 Note Before using this information and the product it supports, read the information in “Notices” on page 503. This edition applies to Version 2 Release 4 of z/OS (5650-ZOS) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2020-11-16 © Copyright International Business Machines Corporation 2015, 2019. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures................................................................................................................. ix Tables.................................................................................................................. xi About this document...........................................................................................xiii Who should use this document?............................................................................................................... xiii z/OS information........................................................................................................................................xiii Discussion list...................................................................................................................................... xiii How to send your comments to IBM......................................................................xv If you have a technical problem.................................................................................................................xv -

VULNERABLE by DESIGN: MITIGATING DESIGN FLAWS in HARDWARE and SOFTWARE Konoth, R.K
VU Research Portal VULNERABLE BY DESIGN: MITIGATING DESIGN FLAWS IN HARDWARE AND SOFTWARE Konoth, R.K. 2020 document version Publisher's PDF, also known as Version of record Link to publication in VU Research Portal citation for published version (APA) Konoth, R. K. (2020). VULNERABLE BY DESIGN: MITIGATING DESIGN FLAWS IN HARDWARE AND SOFTWARE. General rights Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. • Users may download and print one copy of any publication from the public portal for the purpose of private study or research. • You may not further distribute the material or use it for any profit-making activity or commercial gain • You may freely distribute the URL identifying the publication in the public portal ? Take down policy If you believe that this document breaches copyright please contact us providing details, and we will remove access to the work immediately and investigate your claim. E-mail address: [email protected] Download date: 07. Oct. 2021 VULNERABLE BY DESIGN: MITIGATING DESIGN FLAWS IN HARDWARE AND SOFTWARE PH.D. THESIS RADHESH KRISHNAN KONOTH VRIJE UNIVERSITEIT AMSTERDAM, 2020 Faculty of Science The research reported in this dissertation was conducted at the Faculty of Science — at the Department of Computer Science — of the Vrije Universiteit Amsterdam This work was supported by the MALPAY consortium, consisting of the Dutch national police, ING, ABN AMRO, Rabobank, Fox-IT, and TNO. -
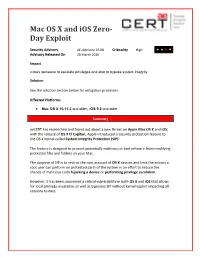
Mac OS X and Ios Zero- Day Exploit
Mac OS X and iOS Zero- Day Exploit Security Advisory AE-Advisory 16-08 Criticality High Advisory Released On 28 March 2016 Impact Allows someone to escalate privileges and also to bypass system integrity Solution See the solution section below for mitigation processes. Affected Platforms Mac OS X 10.11.3 and older, iOS 9.2 and older Summary aeCERT has researched and found out about a new threat on Apple Mac OS X and iOS; with the release of OS X El Capitan, Apple introduced a security protection feature to the OS X kernel called System Integrity Protection (SIP). The feature is designed to prevent potentially malicious or bad software from modifying protected files and folders on your Mac. The purpose of SIP is to restrict the root account of OS X devices and limit the actions a root user can perform on protected parts of the system in an effort to reduce the chance of malicious code hijacking a device or performing privilege escalation. However, it has been uncovered a critical vulnerability in both OS X and iOS that allows for local privilege escalation as well as bypasses SIP without karnel exploit impacting all versions to date. Threat Details The zero day vulnerability is a Non-Memory Corruption bug that allows hackers to execute arbitrary code on any targeted machine, perform remote code execution (RCE) or sandbox escapes. The attacker then escalates the malware's privileges to bypass System Integrity Protection SIP, alter system files, and then stay on the infected system. By default, System Integrity Protection or SIP protects these folders: /System. -
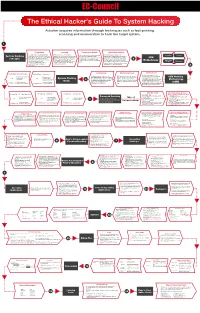
Download the Ethical Hacker's Guide to System Hacking
The Ethical Hacker's Guide To System Hacking Attacker acquires information through techniques such as foot printing, scanning and enumeration to hack the target system. 1 Footprinting Scanning Enumeration Module Vulnerability Analysis It is the process of accumulating data Vulnerability Assessment is an This is a procedure for identifying This is a method of intrusive probing, Footprinting Scanning System Hacking regarding a specific network environment. active hosts, open ports, and unnecessary through which attackers gather examination of the ability of a system or In this phase, the attacker creates a profile services enabled on ports. Attackers use information such as network user lists, application, including current security CEH concepts of the target organization, obtaining different types of scanning, such as port routing tables, security flaws, and procedures, and controls to with stand 2 information such as its IP address range, scanning network scanning, and simple network protocol data (SNMP) assault. Attackers perform this analysis Methodology Vulnerability namespace and employees. Enumeration vulnerability, scanning of target networks data. to identify security loopholes, in the target Analysis Footprinting eases the process of or systems which help in identifying organization’s network, communication system hacking by revealing its possible vulnerabilities. infrastructure, and end systems. vulnerabilities 3 Clearing Logs Maintaining Access Gaining Access Hacking Stage Escalating Privileges Hacking Stage Gaining Access It involves gaining access to To maintain future system access, After gaining access to the target low-privileged user accounts by To acquire the rights of To bypass access CEH Hacking attackers attempt to avoid recognition system, attackers work to maintain cracking passwords through Goal another user or Goal controls to gain System Hacking by legitimate system users.