Winter 2021 Course Catalog
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Senior Data Engineer Cala Health, Inc
875 Mahler Road, Ste. 168 Burlingame, CA, 94010 +1 415-890-3961 www.calahealth.com Job Description: Senior Data Engineer Cala Health, Inc. About Cala Health Cala Health is a bioelectronic medicine company transforming the standard of care for chronic disease. The company's wearable neuromodulation therapies merge innovations in neuroscience and technology to deliver individualized peripheral nerve stimulation. Cala Health’s lead product, Cala Trio™, is the only non-invasive prescription therapy for essential tremor and is now available through a unique digital business model of direct- to-patient solutions. New therapies are under development in neurology, cardiology, and psychiatry. The company is headquartered in the San Francisco Bay Area and backed by leading investors in both healthcare and technology. For more information, visit CalaHealth.com. The Opportunity We are looking for a Senior Data Engineer to expedite our Data Platform Stack to support our growth and also enable new product development in a dynamic, fast-paced startup environment. Specific Responsibilities also include ● Key stakeholder in influencing the roadmap of Cala’s Digital Therapeutics Data Platform. ● Build, operate and maintain highly scalable and reliable data pipelines to enable data collection from Cala wearables, partner systems, EMR systems and 3rd party clinical sources. ● Enable analysis and generation of insights from structured and unstructured data. ● Build Datawarehouse solutions that provide end-to-end management and traceability of patient longitudinal data, enable and optimize internal processes and product features. ● Implement processes and systems to monitor data quality, ensuring production data is always accurate and available for key stakeholders and business processes that depend on it. -

Software Assurance
Information Assurance State-of-the-Art Report Technology Analysis Center (IATAC) SOAR (SOAR) July 31, 2007 Data and Analysis Center for Software (DACS) Joint endeavor by IATAC with DACS Software Security Assurance Distribution Statement A E X C E E C L I L V E R N E Approved for public release; C S E I N N I IO DoD Data & Analysis Center for Software NF OR MAT distribution is unlimited. Information Assurance Technology Analysis Center (IATAC) Data and Analysis Center for Software (DACS) Joint endeavor by IATAC with DACS Software Security Assurance State-of-the-Art Report (SOAR) July 31, 2007 IATAC Authors: Karen Mercedes Goertzel Theodore Winograd Holly Lynne McKinley Lyndon Oh Michael Colon DACS Authors: Thomas McGibbon Elaine Fedchak Robert Vienneau Coordinating Editor: Karen Mercedes Goertzel Copy Editors: Margo Goldman Linda Billard Carolyn Quinn Creative Directors: Christina P. McNemar K. Ahnie Jenkins Art Director, Cover, and Book Design: Don Rowe Production: Brad Whitford Illustrations: Dustin Hurt Brad Whitford About the Authors Karen Mercedes Goertzel Information Assurance Technology Analysis Center (IATAC) Karen Mercedes Goertzel is a subject matter expert in software security assurance and information assurance, particularly multilevel secure systems and cross-domain information sharing. She supports the Department of Homeland Security Software Assurance Program and the National Security Agency’s Center for Assured Software, and was lead technologist for 3 years on the Defense Information Systems Agency (DISA) Application Security Program. Ms. Goertzel is currently lead author of a report on the state-of-the-art in software security assurance, and has also led in the creation of state-of-the-art reports for the Department of Defense (DoD) on information assurance and computer network defense technologies and research. -
Global SCRUM GATHERING® Berlin 2014
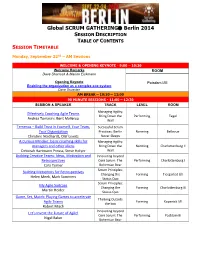
Global SCRUM GATHERING Berlin 2014 SESSION DESCRIPTION TABLE OF CONTENTS SESSION TIMETABLE Monday, September 22nd – AM Sessions WELCOME & OPENING KEYNOTE - 9:00 – 10:30 Welcome Remarks ROOM Dave Sharrock & Marion Eickmann Opening Keynote Potsdam I/III Enabling the organization as a complex eco-system Dave Snowden AM BREAK – 10:30 – 11:00 90 MINUTE SESSIONS - 11:00 – 12:30 SESSION & SPEAKER TRACK LEVEL ROOM Managing Agility: Effectively Coaching Agile Teams Bring Down the Performing Tegel Andrea Tomasini, Bent Myllerup Wall Temenos – Build Trust in Yourself, Your Team, Successful Scrum Your Organization Practices: Berlin Norming Bellevue Christine Neidhardt, Olaf Lewitz Never Sleeps A Curious Mindset: basic coaching skills for Managing Agility: managers and other aliens Bring Down the Norming Charlottenburg II Deborah Hartmann Preuss, Steve Holyer Wall Building Creative Teams: Ideas, Motivation and Innovating beyond Retrospectives Core Scrum: The Performing Charlottenburg I Cara Turner Bohemian Bear Scrum Principles: Building Metaphors for Retrospectives Changing the Forming Tiergarted I/II Helen Meek, Mark Summers Status Quo Scrum Principles: My Agile Suitcase Changing the Forming Charlottenburg III Martin Heider Status Quo Game, Set, Match: Playing Games to accelerate Thinking Outside Agile Teams Forming Kopenick I/II the box Robert Misch Innovating beyond Let's Invent the Future of Agile! Core Scrum: The Performing Postdam III Nigel Baker Bohemian Bear Monday, September 22nd – PM Sessions LUNCH – 12:30 – 13:30 90 MINUTE SESSIONS - 13:30 -

Enabling Devops on Premise Or Cloud with Jenkins
Enabling DevOps on Premise or Cloud with Jenkins Sam Rostam [email protected] Cloud & Enterprise Integration Consultant/Trainer Certified SOA & Cloud Architect Certified Big Data Professional MSc @SFU & PhD Studies – Partial @UBC Topics The Context - Digital Transformation An Agile IT Framework What DevOps bring to Teams? - Disrupting Software Development - Improved Quality, shorten cycles - highly responsive for the business needs What is CI /CD ? Simple Scenario with Jenkins Advanced Jenkins : Plug-ins , APIs & Pipelines Toolchain concept Q/A Digital Transformation – Modernization As stated by a As established enterprises in all industries begin to evolve themselves into the successful Digital Organizations of the future they need to begin with the realization that the road to becoming a Digital Business goes through their IT functions. However, many of these incumbents are saddled with IT that has organizational structures, management models, operational processes, workforces and systems that were built to solve “turn of the century” problems of the past. Many analysts and industry experts have recognized the need for a new model to manage IT in their Businesses and have proposed approaches to understand and manage a hybrid IT environment that includes slower legacy applications and infrastructure in combination with today’s rapidly evolving Digital-first, mobile- first and analytics-enabled applications. http://www.ntti3.com/wp-content/uploads/Agile-IT-v1.3.pdf Digital Transformation requires building an ecosystem • Digital transformation is a strategic approach to IT that treats IT infrastructure and data as a potential product for customers. • Digital transformation requires shifting perspectives and by looking at new ways to use data and data sources and looking at new ways to engage with customers. -

Integrating the GNU Debugger with Cycle Accurate Models a Case Study Using a Verilator Systemc Model of the Openrisc 1000
Integrating the GNU Debugger with Cycle Accurate Models A Case Study using a Verilator SystemC Model of the OpenRISC 1000 Jeremy Bennett Embecosm Application Note 7. Issue 1 Published March 2009 Legal Notice This work is licensed under the Creative Commons Attribution 2.0 UK: England & Wales License. To view a copy of this license, visit http://creativecommons.org/licenses/by/2.0/uk/ or send a letter to Creative Commons, 171 Second Street, Suite 300, San Francisco, California, 94105, USA. This license means you are free: • to copy, distribute, display, and perform the work • to make derivative works under the following conditions: • Attribution. You must give the original author, Jeremy Bennett of Embecosm (www.embecosm.com), credit; • For any reuse or distribution, you must make clear to others the license terms of this work; • Any of these conditions can be waived if you get permission from the copyright holder, Embecosm; and • Nothing in this license impairs or restricts the author's moral rights. The software for the SystemC cycle accurate model written by Embecosm and used in this document is licensed under the GNU General Public License (GNU General Public License). For detailed licensing information see the file COPYING in the source code. Embecosm is the business name of Embecosm Limited, a private limited company registered in England and Wales. Registration number 6577021. ii Copyright © 2009 Embecosm Limited Table of Contents 1. Introduction ................................................................................................................ 1 1.1. Why Use Cycle Accurate Modeling .................................................................... 1 1.2. Target Audience ................................................................................................ 1 1.3. Open Source ..................................................................................................... 2 1.4. Further Sources of Information ......................................................................... 2 1.4.1. -

Code Profilers Choosing a Tool for Analyzing Performance
Code Profilers Choosing a Tool for Analyzing Performance Freescale Semiconductor Author, Rick Grehan Document Number: CODEPROFILERWP Rev. 0 11/2005 A profiler is a development tool that lets you look inside your application to see how each component—each routine, each block, sometimes each line and even each instruction—performs. You can find and correct your application’s bottlenecks. How do they work this magic? CONTENTS 1. Passive Profilers ...............................................3 6. Comparing Passive and Active 1.1 How It Is Done—PC Sampling ................4 Profilers .................................................................9 1.2 It Is Statistical ................................................4 6.1 Passive Profilers—Advantages ...............9 6.2 Passive Profilers—Disadvantages .........9 2. Active Profilers ...................................................4 6.3 Active Profilers—Advantages ................10 2.1 Methods of Instrumentation .....................5 6.4 Active Profilers—Disadvantages ..........11 3. Source Code Instrumentation ...................5 7. Conclusion .........................................................12 3.1 Instrumenting by Hand ..............................5 8. Addendum: Recursion and 4. Object Code Instrumentation ....................5 Hierarchies ........................................................12 4.1 Direct Modification .......................................6 4.2 Indirect Modification ...................................7 5. Object Instrumentation vs. Source Instrumentation -

Debugging and Profiling with Arm Tools
Debugging and Profiling with Arm Tools [email protected] • Ryan Hulguin © 2018 Arm Limited • 4/21/2018 Agenda • Introduction to Arm Tools • Remote Client Setup • Debugging with Arm DDT • Other Debugging Tools • Break • Examples with DDT • Lunch • Profiling with Arm MAP • Examples with MAP • Obtaining Support 2 © 2018 Arm Limited Introduction to Arm HPC Tools © 2018 Arm Limited Arm Forge An interoperable toolkit for debugging and profiling • The de-facto standard for HPC development • Available on the vast majority of the Top500 machines in the world • Fully supported by Arm on x86, IBM Power, Nvidia GPUs and Arm v8-A. Commercially supported by Arm • State-of-the art debugging and profiling capabilities • Powerful and in-depth error detection mechanisms (including memory debugging) • Sampling-based profiler to identify and understand bottlenecks Fully Scalable • Available at any scale (from serial to petaflopic applications) Easy to use by everyone • Unique capabilities to simplify remote interactive sessions • Innovative approach to present quintessential information to users Very user-friendly 4 © 2018 Arm Limited Arm Performance Reports Characterize and understand the performance of HPC application runs Gathers a rich set of data • Analyses metrics around CPU, memory, IO, hardware counters, etc. • Possibility for users to add their own metrics Commercially supported by Arm • Build a culture of application performance & efficiency awareness Accurate and astute • Analyses data and reports the information that matters to users insight • Provides simple guidance to help improve workloads’ efficiency • Adds value to typical users’ workflows • Define application behaviour and performance expectations Relevant advice • Integrate outputs to various systems for validation (e.g. -

Mdcg 2019-16
Medical Device Medical Device Coordination Group Document MDCG 2019-16 MDCG 2019-16 Guidance on Cybersecurity for medical devices December 2019 This document has been endorsed by the Medical Device Coordination Group (MDCG) established by Article 103 of Regulation (EU) 2017/745. The MDCG is composed of representatives of all Member States and it is chaired by a representative of the European Commission.The document is not a European Commission document and it cannot be regarded as reflecting the official position of the European Commission. Any views expressed in this document are not legally binding and only the Court of Justice of the European Union can give binding interpretations of Union law. Page 1 of 46 Medical Device Medical Device Coordination Group Document MDCG 2019-16 Table of Contents 1. Introduction ........................................................................................................................................ 4 1.1. Background ............................................................................................................................. 4 1.2. Objectives ............................................................................................................................... 4 1.3. Cybersecurity Requirements included in Annex I of the Medical Devices Regulations ........ 4 1.4. Other Cybersecurity Requirements ......................................................................................... 6 1.5. Abbreviations ......................................................................................................................... -

BSI Medical Devices: Webinar Q&A
ISO 14971:2019 Risk Management for Medical Devices: Webinar Q&A November 2019 BSI Medical Devices: Webinar Q&A ISO 14971:2019 Risk Management for Medical Devices 13 November 2019 Page 1 of 10 ISO 14971:2019 Risk Management for Medical Devices: Webinar Q&A November 2019 Q&A Q. Should EN ISO 14971:2012 be used to demonstrate continued compliance to the ERs or GSPRs or use the 2019 revision of the standard? A. A manufacturer must demonstrate compliance to the applicable legislation. Harmonization of a standard allows for a presumption of conformity to the applicable legislation where the standard is applied and the manufacturer considers the Qualifying remarks/Notes in Annex Z. Additional clarification has been made available from the European Commission, whereby it is now considered that the recent editions of standards published by standardizers reflect the state of the art, regardless of its referencing in the OJEU and therefore the ISO 14971:2019 version represents the state of the art for the Medical Device Directives and Regulation. This update is welcomed as it provides clarity for industry and ensures manufacturers need only to comply with a single version of a standard. It is anticipated the 2019 revision will be harmonized to the Regulations. Q. From the Date of Application of the MDR and IVDR will the technical documentation for existing Directive certificates be required to be updated to the 2019 revision of the standard, considering the transitional provisions of MDR Article 120 and IVDR Article 110? A. A manufacturer must demonstrate compliance to the applicable legislation. -

A Reference Architecture for Secure Medical Devices Steven Harp, Todd Carpenter, and John Hatcliff
FEATURE © Copyright AAMI 2018. Single user license only. Copying, networking, and distribution prohibited. A Reference Architecture for Secure Medical Devices Steven Harp, Todd Carpenter, and John Hatcliff Abstract and users cannot assume that medical Steven Harp, is a distinguished We propose a reference architecture aimed at devices will operate in a benign security engineer at Adventium Labs in supporting the safety and security of medical environment. Any device that is capable of Minneapolis, MN. Email: steven. devices. The ISOSCELES (Intrinsically connecting to a network or physically [email protected] Secure, Open, and Safe Cyber-Physically exposes any sort of data port is potentially at Enabled, Life-Critical Essential Services) risk. How should we think about and Todd Carpenter, is chief engineer architecture is justified by a collection of design manage risk in this context? at Adventium Labs in Minneapolis, principles that leverage recent advances in This question has been explored exten- MN. Email: todd.carpenter@ software component isolation based on sively.3,4 Special publications from the adventiumlabs.com hypervisor and other separation technologies. National Institute of Standards and Technol- The instantiation of the architecture for ogy (e.g., 800-39) provide a conceptual risk John Hatcliff, PhD, is a particular medical devices is supported by a management framework.5,6 AAMI TIR577 distinguished professor at Kansas development process based on Architecture describes how security risk management State University in Manhattan, KS. Analysis and Design Language. The architec- can be integrated with safety risk manage- Email: [email protected] ture models support safety and security ment (e.g., as addressed in ISO 14971 and analysis as part of a broader risk management specifically for medical devices in IEC framework. -

FI-STAR Deliverable D1.1 Has Already Discussed Legal Requirements Related to Data Security Breach Notifications
Ref. Ares(2014)706091 - 13/03/2014 Deliverable D2.1 Standardisation and Certification requirements Editor: Franck Le Gall, easy global markets Deliverable nature: Report (R) Dissemination level: Public (PU) (Confidentiality) Contractual delivery Dec. 2013 date: Actual delivery date: Jan. 2014 Suggested readers: Version: 1.1 Total number of 74 pages: Keywords: Standardisation, certification Abstract This document details the technical requirements resulting from existing standards and prepares future certification process. FI-STAR FP7-ICT-604691 D1.2 Standardisation and Certification requirements Disclaimer This document contains material, which is the copyright of certain FI-STAR consortium parties, and may not be reproduced or copied without permission. All FI-STAR consortium parties have agreed to full publication of this document. The commercial use of any information contained in this document may require a license from the proprietor of that information. Neither the FI-STAR consortium as a whole, nor a certain part of the FI-STAR consortium, warrant that the information contained in this document is capable of use, nor that use of the information is free from risk, accepting no liability for loss or damage suffered by any person using this information. This project has received funding from the European Union’s Seventh Framework Programme for research, technological development and demonstration under grant agreement no 604691. Impressum [Full project title] Future Internet Social and Technological Alignment Research [Short project -

Ready to Innovate?
ReadyThe Visual COBOL 5.0to Azure innovate? DevOps and Serverless Computing Walkthrough June 2019 The Visual COBOL 5.0 Azure DevOps and Serverless Computing Walkthrough 2 Visual COBOL 5.0— blue sky thinking Ready to build your Cloud story? This is primarily a how-to technical guide that enables COBOL and non- COBOL developers to modernize legacy applications using the Cloud— it’s all about bridging the old with the new. New to Visual COBOL? This is your guided tour of everything it can do towards modernizing core COBOL applications. Already on board? This is the update that explains how to take your applications beyond the next level and on to the Cloud. What will you learn? Much of this Guide focuses on the technical, practical aspect of creating next-gen apps from COBOL code. Among other new skills, you will discover how to… • Bring a COBOL application into Visual Studio or Eclipse • Edit, compile and debug COBOL applications using the IDE • Modernize COBOL apps using .NET and C# • Create and deploy a COBOL microservice as a Serverless application in the Cloud • Build, test and publish your application via a DevOps pipeline • Understand the latest native Cloud technologies The Visual COBOL 5.0 Azure DevOps and Serverless Computing Walkthrough 3 What’s new in Visual COBOL 5.0? This latest update of our unrivalled development experience significantly extends Visual COBOL’s capabilities. It brings the Cloud closer, enabling access to DevOps and Serverless computing for COBOL systems. For Micro Focus, Visual COBOL 5.0 is where meet our customers’ need for application modernization using the Cloud.