Cisco Secure Access and Cisco Trustsec Release 5.0 System Bulletin
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cisco Path Trace Application for APIC-EM Supported Platforms, Release 1.6.0.X
Cisco Path Trace Application for APIC-EM Supported Platforms, Release 1.6.0.x First Published: 2017-10-23 Supported Platforms for Cisco Path Trace Supported Platforms for Cisco Path Trace, Release 1.6.0.x This document describes the supported platforms for the Cisco Path Trace, Release 1.6.0.x. Supported Platforms and Software Requirements The following tables list the supported devices and modules, with their software requirements, for this release. Note For information about the supported platforms and software requirements for the other Cisco APIC-EM applications, see the following documents: • Cisco EasyQoS Application for APIC-EM Supported Platforms • Cisco Network Visibility Application for APIC-EM Supported Platforms • Cisco Path Trace Application for APIC-EM Supported Platforms • Cisco Active Advisor for APIC-EM Release Notes • Cisco Integrity Verification Application for APIC-EM Release Notes • Cisco Remote Troubleshooter for APIC-EM Release Notes • Cisco Wide Area Bonjour Application for APIC-EM Release Notes • Release Notes for Cisco Intelligent Wide Area Network Application (Cisco IWAN App) • Release Notes for Cisco Network Plug and Play Supported Cisco Switches The following table lists the supported Cisco switches for this Cisco Path Trace release. For Path Trace, be sure to use the recommended software version. Cisco Path Trace Application for APIC-EM Supported Platforms, Release 1.6.0.x 1 Supported Platforms for Cisco Path Trace Supported Cisco Switches Table 1: Supported Cisco Switches Supported Switches Recommended Path -

Open Call for Tenders for the Provision of Maintenance Services, Networking Technical Support Services, and the Supply of Networ
Annex K - List of products for H/W and S/W supply CFT/EUI/ICTS/2015/002 Open Call for Tenders for the provision of Maintenance Services, Networking Technical Support Services, and the supply of Network Equipment and Materials for the European University Institute SWITCHES, WIRELESS SECURITY AND SYSTEMS MANAGEMENT VOICE AND UNIFIED COMMUNICATIONS INTERFACES, MODULES AND ROUTERS SWITCHES ROUTERS WIRELESS SYSTEMS MANAGEMENT VOICE AND UNIFIED COMMUNICATIONS Blade Switches Branch Routers Access Point Collaboration and Unified Communications Management Call Control Cisco Blade Switches for Dell Cisco 1100 Series Routers Cisco 800 and 1900 Series ISR Integrated Access Points Cisco Prime Collaboration Cisco Intercompany Media Engine Cisco Blade Switches for FSC Cisco 1800 Series Integrated Services Routers Cisco Aironet 1040 Series Cisco Prime License Manager Cisco Unified Communications Manager (CallManager) Cisco Blade Switches for HP Cisco 1900 Series Integrated Services Routers Cisco Aironet 1130 AG Series Cisco Unified Communications Manager Session Management Edition Cisco Switch Modules for IBM Cisco 2800 Series Integrated Services Routers Cisco Aironet 1140 Series Cisco Unified Mobility Cisco 2900 Series Integrated Services Routers Cisco Aironet 1200 Series Cisco Unified Communications Management Cisco Service Node Cisco 3800 Series Integrated Services Routers Cisco Aironet 1600 Series Cisco Signaling Controllers SFS Solutions for Blade Switches Cisco 3900 Series Integrated Services Routers Cisco Aironet 2600 Series Cisco Unified Operations -

Cisco Enterprise Networks Catalog Volume 5: Europe, Middle East, Africa and Russia #Networkintuitive 02 Switches Wireless Routing
Constantly learning, constantly adapting, constantly protecting Built on Cisco DNA Cisco Enterprise Networks Catalog Volume 5: www.cisco.com/go/DNA Europe, Middle East, Africa and Russia #networkintuitive 02 Switches Wireless Routing Cisco Catalog - EMEAR Switches No SDA/SDA Switches P20 Vol.5 Cisco Catalyst 2960-CX Series P26 Cisco Catalyst 3560-CX Series P26 Security Cisco Catalyst 2960-L Series Switches P27 Cisco Catalyst 2960-X Series P28 Cisco Catalyst 3650 Series P28 Cisco Catalyst 3850 Series P31 Index Cisco Catalyst 4500E Series P33 Cisco Catalyst 4500-X Series P35 Cisco Catalyst 6800 Series P36 Cisco Nexus 7700 Switches P37 Cisco Meraki Cisco Catalyst 9300 Series Switches P40 Cisco Catalyst 9400 Series Switches P41 Cisco Catalyst 9500 Series Switches P42 Modules & Accessories P45 What's New Subscription-based software P46 Wireless Switches Cisco Virtual Beacon P54 DNA-Center Revolutionary Cisco Aironet Access Points P57 ■ Indoor Access Points P57 Catalyst 9000 Series ■ Outdoor Access Points P59 P16 ■ Cisco Aironet Antennas and Accessories P60 Cisco Wireless Controllers P62 Subscription-based software P64 Cisco DNA for Access Routing Wireless and Switching Subscription Cisco ISR 800 Series P69 Introducing New Software Cisco ISR 1000 Series P70 Subscription Licensing Cisco ISR 4000 Series P71 SMB Modules & Accessories P17 P72 Cisco Enterprise Network Functions Virtualization (ENVF) P74 Cisco 5000 Series Enterprise Network Compute System P75 Cisco SD WAN Wireless P76 Cisco Wide Area Application Services (WAAS) P78 Cisco® Aironet® -

The Game-Changing Technology Allows Your Networks to Evolve Beyond 1 G P06
Accelerating Innovation with Fast IT Switches Cisco Wireless Cisco Catalog Volume 1: Europe, Middle East, Africa and Russia Routers Feature Cisco Catalyst Multigigabit Technology (mGig) The Game-changing Technology Small Business Small Cisco’s First Allows Your Networks to Evolve 11ac Wave 2 Access Point!! Beyond 1 G Aironet 1850 Services Give Power to Your Business Surge Ahead of the Pack ENJOY FAST MOBILITY WITH CISCO MGIG! ✚ No complex deployment ✚ No new cabling required ✚ No expensive investment The rising number of wireless devices and evolving wireless standards brings challenges to your network. Equipped with NBASE-T Multigigabit (mGig) Ethernet technology, the new generation of Cisco® Catalyst® Multigigabit Ethernet switches enables intermediate data rates of 2.5 and 5 Gbps over your existing cabling infrastructure to ease the jump between traditional rates of 1 Gbps and 10 Gbps. This provides you the scale and capacity you need today, while protecting your network investments for the next ve years. Cisco mGig: Easy to deploy. Budget friendly. Lower total operational costs. Typical Setup WIFI >1G Cat 5e Cables Speed: Up to 1G Access Point Regular Access Regular Core (802.11ac wave 2) Switch Switch With Cisco mGig Switch WIFI >1G Cat 5e Cables Speed: Increase from Access Point mGig Access 1G to 2.5-5G mGig Core (802.11ac wave 2) Switch Switch ■ Cisco Catalyst Multigigabit Technology (mGig): Speeds and Cables Cable Type 1 Gbps 2.5 Gbps 5 Gbps 10 Gbps Coupled with the Cisco Mobility Bundle, you get to enjoy: Cat 5e ✔ ✔ ✔ - • Reduced complexity Cat 6 ✔ ✔ ✔ ✔ (55m) • Increased security Cat 6a ✔ ✔ ✔ ✔ • Improved user experience Cisco Catalyst Multigigabit Ethernet Switches Cisco Mobility Express Bundle 4500E/3850/3560-CX 1700/2700/3700 STAR HOT BUY! BUY! Key Benets Key Benets • Increase network bandwidth and speed without running • Includes two 802.11ac access multiple cables between switches and access points. -

Readme for Cisco ANA 3.7.2 Device Package 3.0
Readme for Cisco ANA 3.7.2 Device Package 3.0 Date: May 10, 2011 OL-24561-03 Table of Contents 1 Contents of Cisco ANA 3.7.2 Device Package 3.0 ................................................................................. 2 1.1 New Software/Feature for Cisco Network Elements .................................................................... 2 1.2 New Support for Device Package Mechanism .............................................................................. 3 1.3 New Reduced Polling (EVNE) Support .......................................................................................... 4 1.4 New Support for Cisco ANA Configuration and Image Management ........................................... 4 2 Installing Cisco ANA 3.7.2 Device Package 3.0 ...................................................................................... 4 3 List of Latest Driver Files ....................................................................................................................... 5 4 Resolved Bugs ....................................................................................................................................... 6 4.1 Bug Resolutions That Require ANA Patches ................................................................................. 7 5 Open Bugs ............................................................................................................................................. 8 5.1 Device-Specific Open Bugs ........................................................................................................... -

Curriculum Vitae
DJAN PHANG 6338 Sunset Cove Lane, Katy, TX 77494 281.693.0645 (home), 281.968.1619 (Cell) [email protected] SKILLS/TOOLS: Operating Systems: Cisco NOS, Cisco IOS, Cisco FTD, Cisco ASA 8.4.7 – 9.x, Cisco CATOS, RiOS, Windows XP/2000, Windows 2016,Windows 2012, Windows 2008, Windows Server 2003, Linux: RedHat, CentOS F5 TMOS version 11.6 – 12.1.2, F5 LTM, F5 ASM, F5 APM. Network Hardware: Cisco ISE 1.1 – 2.7, WebSense 7.8.4 Cisco Nexus, 7000, 6000, 5500, 2200 series Cisco routers, 7200, 4300, 3900, 3800, 3700, 2800, 1800, 2600, 1700, 2500 series Cisco switches 6500, 4500, 4000, 4948, 3800, 3750X, 3500XL, 2900XL, 1900 series Cisco Aeronet 340, 350, 1100, 3700 series Cisco ASA 5520, ASA 5540, and Cisco ASA 5512X, ASA5525X CUCM 8.6.4 – 12.5, IPhone 8800, IPhone 9700, IPhone 7200,jabber, sparks, softphone, Nortel Meridian PBX, Lucent Merlin Magic PBX Cisco Content Switching Module/ACE Cisco TACACS, and Riverbed Cascade Checkpoint (CrossBeam & UTM 3070), Juniper Firewall SSG2000 F5-BigIP, Riverbed 5050 ADVA (DWDM switches) Software: PeopleSoft, Maximo, ACCPAC CQG, TransEnergy, Streamline, Quicktrade, Reuters, Gas Nomination Software, OASIS/TradeWave Microsoft SQL 6.5, Microsoft Project, Microsoft 2016-2003 office Cacti (Windows, Linux), Apache, PHP SolarWinds, Tcpdump, Wireshark Network Connections: DWDM, DecaMAN, GigaMAN, DS3, ELANE, MPLS, Lease line T1, FrameRelay, VSAT, Satellite, Microwave, ISDN, VPN, Wireless Network Protocols VTP, Spanning-Tree, Trunking, VLAN, VPC, HSRP, GLBP, GRE tunnel, IPSEC, DMVPN Routing Protocols: EIGRP, RIP, OSPF, -

Cisco Path Trace Application for APIC-EM Supported Platforms, Release 1.5.0.X
Cisco Path Trace Application for APIC-EM Supported Platforms, Release 1.5.0.x First Published: 2017-06-23 Supported Platforms for Cisco Path Trace Supported Platforms for Cisco Path Trace, Release 1.5.0.x This document describes the supported platforms for the Cisco Path Trace, Release 1.5.0.x. Supported Platforms and Software Requirements The following tables list the supported devices and modules, with their software requirements, for this release. Note For information about the supported platforms and software requirements for the other Cisco APIC-EM applications, see the following documents: • Cisco Path Trace Application for APIC-EM Supported Platforms • Cisco EasyQoS Application for APIC-EM Supported Platforms • Cisco Active Advisor for APIC-EM Release Notes • Release Notes for Cisco SD-Bonjour • Cisco Integrity Verification Application for APIC-EM Release Notes • Cisco Remote Troubleshooter for APIC-EM Release Notes • Release Notes for Cisco Intelligent Wide Area Network Application (Cisco IWAN App) • Release Notes for Cisco Network Plug and Play Supported Cisco Switches The following table lists the supported Cisco switches for this Cisco Path Trace release. For Path Trace, be sure to use the recommended software version. Cisco Path Trace Application for APIC-EM Supported Platforms, Release 1.5.0.x 1 Supported Platforms for Cisco Path Trace Supported Platforms and Software Requirements Table 1: Supported Cisco Switches Supported Switches Recommended Path Trace Statistics Software Version Interface QoS Device Performance Monitor -
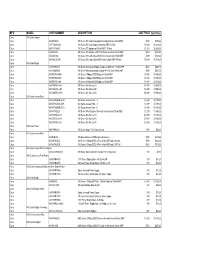
Cisco Price List.Pdf
MFG MODEL PART NUMBER DESCRIPTION LIST PRICE Sell Price Cisco 350 Series Adapter Cisco AIR-PCM352 350 Series PC Card w/Integrated Diversity Antenna,128-bitWEP $199 $159.20 Cisco AIR-PCM352/40 350 Series PC Card Adapter w/128-bit WEP 40 Pack $7,899 $6,319.20 Cisco AIR-PCI352/10 350 Series PCI Adapter w/128-bit WEP 10 Pack $3,199 $2,559.20 Cisco AIR-PCI352 350 Series PCI Adapter w/RP-TNC,Dipole Antenna,128-bit WEP $329 $263.20 Cisco AIR-LMC352 350 Series PC Card w/Dual MMCX Connectors and 128-bit WEP $199 $159.20 Cisco AIR-LMC352/40 350 Series PC Card w/Dual MMCX and 128-bit WEP 40 Pack $7,899 $6,319.20 Cisco 350 Series Bridge Cisco AIR-WGB352C 350 Series Workgroup Bridge w/Captured Antenna / 128-bit WEP $629 $503.20 Cisco AIR-WGB352R 350 Series Workgroup Bridge w/Dual RP-TNC and 128-bit WEP $659 $527.20 Cisco AIR-BR350-A-K9 350 Series 11Mbps, DSSS Bridge w/128-bit WEP $1,999 $1,599.20 Cisco AIR-BR350-E-K9 350 Series 11Mbps, DSSS Bridge w/128-bit WEP $1,999 $1,599.20 Cisco AIR-BR350-J-K9 350 Series 11Mbps, DSSS Bridge w/128-bit WEP $1,999 $1,599.20 Cisco AIR-SSB350-A-K9 350 Series Site Survey Kit $4,499 $3,599.20 Cisco AIR-SSB350-J-K9 350 Series Site Survey Kit $4,499 $3,599.20 Cisco AIR-SSB350-E-K9 350 Series Site Survey Kit $4,499 $3,599.20 Cisco 350 Series Access Point Cisco AIR-AP352E2R-A-K9 350 Series Access Point - A $1,499 $1,199.20 Cisco AIR-AP352E2R-J-K9 350 Series Access Point - J $1,499 $1,199.20 Cisco AIR-AP352E2R-E-K9 350 Series Access Point - E $1,499 $1,199.20 Cisco AIR-AP352E2C 350 Series AP w/Captured Diversity Antennas and 128-bit WEP $1,299 $1,039.20 Cisco AIR-SSI350-A-K9 350 Series Site Survey Kit $3,999 $3,199.20 Cisco AIR-SSI350-E-K9 350 Series Site Survey Kit $3,999 $3,199.20 Cisco AIR-SSI350-J-K9 350 Series Site Survey Kit $3,999 $3,199.20 Cisco 350 Series Power Cisco AIR-PWRINJ= 350 Series Single Port Power Injector $59 $47.20 Cisco 340 Series Access Point Cisco AIR-BSE342 340 Base Station w/ WEP;Captured Antenna $399 $319.20 Cisco AIR-AP342E2C 340 Series 11Mbps DSSS AP w/128-bit WEP and 2 Int. -

Cisco Network Visibility Application for APIC-EM Supported Platforms, Release 1.6.0.X
Cisco Network Visibility Application for APIC-EM Supported Platforms, Release 1.6.0.x First Published: 2017-10-23 Supported Platforms for Cisco Network Visibility for APIC-EM, Release 1.6.0.x This document describes the supported platforms for Cisco Network Visibility for APIC-EM, Release 1.6.0.x Supported Platforms and Software Requirements The following tables list the supported devices and modules, with their software requirements, for this release. Note For information about the supported platforms and software requirements for the other Cisco APIC-EM applications, see the following documents: • Cisco EasyQoS Application for APIC-EM Supported Platforms • Cisco Network Visibility Application for APIC-EM Supported Platforms • Cisco Path Trace Application for APIC-EM Supported Platforms • Cisco Active Advisor for APIC-EM Release Notes • Cisco Integrity Verification Application for APIC-EM Release Notes • Cisco Remote Troubleshooter for APIC-EM Release Notes • Cisco Wide Area Bonjour Application for APIC-EM Release Notes • Release Notes for Cisco Intelligent Wide Area Network Application (Cisco IWAN App) • Release Notes for Cisco Network Plug and Play Supported Cisco Switches The following table lists the supported Cisco switches for this Cisco Network Visibility release. Cisco Network Visibility Application for APIC-EM Supported Platforms, Release 1.6.0.x 1 Supported Platforms for Cisco Network Visibility for APIC-EM, Release 1.6.0.x Supported Cisco Switches Table 1: Supported Cisco Switches Supported Switches Minimum Software Version -

Cisco Technical Content Style Guide
Cisco Technical Content Style Guide Last Updated: 2019-10-10 The Style Team updates the Cisco Technical Content Style Guide in real time and republishes the guide after every update. You can access the always-up-to-date style guide online and download the full-book PDF anytime. Cisco Systems, Inc. www.cisco.com Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1721R) © 1992-2019 Cisco Systems, Inc. All rights reserved. 2 New and Changed Information Change Summary Table 1 Significant Changes in the Style Guide Change Chapter Date Added the term “app stack.” A-Z Terms 2019-10-10 Updated guidelines at the Website References Voice, Tone, and Language 2019-10-08 subsection. Added two examples for the serial comma guideline. Core Writing Guidelines 2019-07-23 Added notes for the term “AAA” to indicate use of the A-Z Terms 2019-04-24 correct indefinite article. Added the words “caveat” and “bug” as a A-Z Terms 2019-04-03 comparative word pair. Added the “slide-in pane” entry in the Conventions for Writing About GUIs 2018-12-07 Fields, Titles, and Information Areas table. Deprecated the term “on-premise” and added the A-Z Terms 2018-12-07 alternate term “on-premises.” Cisco Systems, Inc. -

Prime Network 50 Supported Vnes Addendum
Addendum: Additional VNE Driver Support for Cisco Prime Network 5.0 Date: July 30, 2021 This is a companion document to Cisco Prime Network 5.0 Supported VNEs. It contains the following: • Information about new or enhanced Virtual Network Elements (VNE) drivers, new modules, new technologies and new software versions supported after Prime Network 5.0 release. • Device support information for Change and Configuration Management. • Device support information for command scripts (scripts launched by right-clicking an NE in Prime Network Vision and choosing Commands). Table of Contents Obtaining the New and Enhanced Device Drivers ...........................................................................................4 Which Jar File is a Device Using? ....................................................................................................................4 New Support for Cisco Routers.......................................................................................................................6 Cisco ASR 10XX Series Routers — Additional Support ..........................................................................................6 Cisco ASR 901 Routers — Additional Support .....................................................................................................8 Cisco ASR 902 Routers — Additional Support .....................................................................................................8 Cisco ASR 903 Routers — Additional Support .....................................................................................................8 -
Cisco Systems Routing Innovations
Cisco Systems Routing Innovations Innovation in Internet Protocol (IP) routing is one of Cisco Systems’ strongest commitments. The IP router—the heart of the Internet—inspects each packet of data and its corresponding IP address and sends it through the network using sophisticated hardware and software technology. The company has more than 15 years of development and innovation experience, and has built the largest IP networks in the world. Cisco continues to be a market share leader in IP Routing, and according to Synergy Research, the IP Routing market is expected to grow from $7 billion today to $10.5 billion by 2007. Today’s core and edge routing announcements reinforce Cisco’s commitment to enabling service providers to be successful in a very challenging environment. The Cisco routing platform allows service providers to protect their existing infrastructure investments, while providing the foundation for new, revenue-generating services. Cisco’s most recent routing innovation—the Cisco Carrier Routing System (CRS-1)—demonstrates how the company has built a networking router of unprecedented performance and intelligence to run the infrastructure for the Information Age. Below is a timeline of Cisco’s routing innovations from 1986 through the present. For more information on Cisco’s leadership routing technologies, solutions, and services, visit http://newsroom.cisco.com/dlls/innovators/Core_IP/index.html. 1986 • Cisco forever changes networking communications industry and Internet by launching its first innovation, the AGS multi-protocol router. • Cisco introduces and ships the FGS, its first remote access router. 1993 • Cisco introduces the high-end 7000 router. 1994 • Cisco introduces the Cisco 2500 Series: the first compact, full-featured router for small or branch offices.