THE THIRD Blogging Linux Feeds an Ogre | Pixel | Selinux
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

MODUL PELATIHAN MIGRASI OPEN SOURCE SOFTWARE “Level Pengguna”
MODUL PELATIHAN MIGRASI OPEN SOURCE SOFTWARE “Level Pengguna” Update : Juli 2010 Oleh : Hasan B. Usman L Kelompok TIK Open Source Software Keterampilan √ Tingkat Pemula Tingkat Menengah Tingkat Mahir Jenis Buku √ Referensi √ Tutorial Latihan Pendukung √ CD/DVD OSS Linux √ Video Tutorial OSS √ Modul lain yg relevan URL http://www.igos.web.id, http://www.igos.or.id Email : [email protected] KATA PENGANTAR KATA PENGANTAR Adopsi terhadap perangkat lunak open source juga bisa diartikan sebagai bagian dari proses migrasi yang tidak secara kasat mata merupakan perpindahan, karena pada dasarnya migrasi bertujuan untuk menguatkan penggunaan software legal oleh pengguna perangkat lunak. Migrasi adalah pekerjaan dengan tingkat kerumitan yang sangat beragam, bisa mudah dan bahkan bisa menjadi sulit. Bila tidak ahli di bidangnya, proses migrasi akan menjadi lebih sulit. Untuk memudahkan anda dalam melakukan proses migrasi, buku panduan ini disusun sebagai salah satu referensi dan diperuntukkan bagi pengguna (end user) dan mudah-mudahan dengan adanya referensi ini dapat membantu anda. Salam Hangat Hasan B. Usman Ketua Tim Migrasi ([email protected] ) Modul Pelatihan Migrasi OSS Untuk Level Pengguna, update Juli 2010 http://www.igos.or.id, email : [email protected] i RINGKASAN RINGKASAN Materi pelatihan teknologi informasi menggunakan open source software ini adalah salah satu referensi untuk mendukung proses migrasi untuk level pengguna. Topik pembahasan pada materi ini adalah mengenai pengantar oss, Instalasi linux, desktop linux, aplikasi perkantoran openoffice, aplikasi internet, aplikasi multimedia dan grafis sampai dengan cara akses file melewati jaringan Modul Pelatihan Migrasi OSS Untuk Level Pengguna, update Juli 2010 http://www.igos.or.id, email : [email protected] ii COURSE OBJECTIVE COURSE OBJECTIVE 1.1. -

Linux Journal | August 2014 | Issue
™ SPONSORED BY Since 1994: The Original Magazine of the Linux Community AUGUST 2014 | ISSUE 244 | www.linuxjournal.com PROGRAMMING HOW-TO: + OpenGL Build, Develop Programming and Validate Creation of RPMs USE VAGRANT Sysadmin Cloud for an Easier Troubleshooting Development with dhclient Workflow Tips for PROMISE Becoming a THEORY Web Developer An In-Depth A Rundown Look of Linux for Recreation V WATCH: ISSUE OVERVIEW LJ244-Aug2014.indd 1 7/23/14 6:56 PM Get the automation platform that makes it easy to: Build Infrastructure Deploy Applications Manage In your data center or in the cloud. getchef.com LJ244-Aug2014.indd 2 7/23/14 11:41 AM Are you tiredtiered of of dealing dealing with with proprietary proprietary storage? storage? ® 9%2Ä4MHÆDCÄ2SNQ@FD ZFS Unified Storage zStax StorCore from Silicon - From modest data storage needs to a multi-tiered production storage environment, zStax StorCore zStax StorCore 64 zStax StorCore 104 The zStax StorCore 64 utilizes the latest in The zStax StorCore 104 is the flagship of the dual-processor Intel® Xeon® platforms and fast zStax product line. With its highly available SAS SSDs for caching. The zStax StorCore 64 configurations and scalable architecture, the platform is perfect for: zStax StorCore 104 platform is ideal for: VPDOOPHGLXPRIILFHILOHVHUYHUV EDFNHQGVWRUDJHIRUYLUWXDOL]HGHQYLURQPHQWV VWUHDPLQJYLGHRKRVWV PLVVLRQFULWLFDOGDWDEDVHDSSOLFDWLRQV VPDOOGDWDDUFKLYHV DOZD\VDYDLODEOHDFWLYHDUFKLYHV TalkTalk with with an anexpert expert today: today: 866-352-1173 866-352-1173 - http://www.siliconmechanics.com/zstax LJ244-Aug2014.indd 3 7/23/14 11:41 AM AUGUST 2014 CONTENTS ISSUE 244 PROGRAMMING FEATURES 64 Vagrant 74 An Introduction to How to use Vagrant to create a OpenGL Programming much easier development workflow. -

Withlinux Linux
LINUX JOURNAL MISTERHOUSE | F-SPOT | AJAX | KAFFEINE | ROBOTS | VIDEO CODING An Excerpt from Apress’ Beginning DIGITAL LIFESTYLE DIGITAL Ubuntu Linux: From Novice to Professional ™ Since 1994: The Original Magazine of the Linux Community OCTOBER 2006 | ISSUE 150 | www.linuxjournal.com MisterHouse | AL F-Spot DIGIT | Ajax | Kaffeine LIFESTYLE | ux Robots with LinuxLin | Video Coding Video >> F-Spot Tips >> Working with Digital Images >> H.264 Video Encoding for Low-Bitrate Video | Ubuntu >> Linux-Based Do-It-Yourself Robots >> Share Music with Kaffiene, Amarok, Last.fm and more >> Digital Convenience at Home with Open-Source Technology O >> Maddog’s Travel Gadgets C T O B E >> Using MisterHouse for Home Automation R 2006 AN I S S PUBLICATION U E USA $5.00 150 + Doc Searls Breaks the Marketing Matrix CAN $6.50 U|xaHBEIGy03102ozXv,:! Today, Carlo restored a failed router in Miami, rebooted a Linux server in Tokyo, and remembered someone’s very special day. With Avocent centralized management solutions, the world can finally revolve around you. Avocent puts secure access and control right at your fingertips – from multi-platform servers to network routers, your local data center to branch offices. Our “agentless” out-of-band solution manages your physical and virtual connections (KVM, serial, integrated power, embedded service processors, IPMI and SoL) from a single console. You have guaranteed access to your critical hardware even when in-band methods fail. Let others roll crash carts to troubleshoot – with Avocent, trouble becomes a thing of the past, so you can focus on the present. Visit www.avocent.com/special to download Data Center Control: Guidelines to Achieve Centralized Management white paper. -

Engineering Law and Ethics
ENSC 406 Software, Computer and Internet Ethics Bob Gill, P.Eng., FEC, smIEEE May 15th 2017 1 Topics Covered What is Open Source Software? A One-Slide History of Open Source Software The Open Source Development Model Why Companies Use (and Don’t Use) Open Source Software Open Source Licensing Strategies Open Source Licenses and “Copyleft” Open Source Issues in Corporate Transactions Relevant Cases and Disputes Open source vs. Freeware vs. Shareware Site Licensing Software Maintenance Computer and Internet Ethics 2 What is Open Source Software? Open Source software is software licensed under an agreement that conforms to the Open Source Definition Access to Source Code Freedom to Redistribute Freedom to Modify Non-Discriminatory Licensing (licensee/product) Integrity of Authorship Redistribution in accordance with the Open Source License Agreement 3 What is Open Source Software? Any developer/licensor can draft an agreement that conforms to the OSD, though most licensors use existing agreements GNU Public License (“GPL”) Lesser/Library GNU Public License (“LGPL”) Mozilla Public License Berkeley Software Distribution license (“BSD”) Apache Software License MIT – X11 License See complete list at www.opensource.org/licenses 4 Examples of Open Source Software Linux (operating system kernel – substitutes for proprietary UNIX) Apache Web Server (web server for UNIX systems) MySQL(Structured Query Language – competes with Oracle) Cloudscape, Eclipse (IBM contributions) OpenOffice(Microsoft Office Alternate) SciLab, -

LINUX JOURNAL (ISSN 1075-3583) Is Published Monthly by Belltown Media, Inc., 2121 Sage Road, Ste
EPUB, Kindle,SUBSCRIBERS Android, iPhone & iPad editions SQLAlchemy | ConVirt | Fabric | Azure | RaspberryFREE PiTO ™ Make Your Android Device Play with Your Linux Box A Look at SQLAlchemy’s Since 1994: The Original Magazine of the Linux Community Features SYSTEM FEBRUARY 2013 | ISSUE 226 | www.linuxjournal.com ADMINISTRATION Manage Your HOW TO: Virtual Handling Deployment R Packages with ConVirt Spin up Linux VMs on Azure Use Fabric for Sysadmin Tasks on Remote Machines PLUS: Use a Raspberry Pi as a Colocated Server Cover226-Final-banner.indd 1 1/24/13 11:08 AM LJ226-Feb013-bu.indd 2 1/23/13 1:06 PM visit us at www.siliconmechanics.com or call us toll free at 888-352-1173 RACKMOUNT SERVERS STORAGE SOLUTIONS HIGH-PERFORMANCE COMPUTING ““ Just Just becausebecause it’sit’s badass,badass, doesn’tdoesn’t meanmean it’sit’s aa game.”game.” Pierre, our new Operations Manager, is always looking for the right tools to get more work done in less time. That’s why he respects NVIDIA ® Tesla ® GPUs: he sees customers return again and again for more server products featuring hybrid CPU / GPU computing, like the Silicon Mechanics Hyperform HPCg R2504.v3. When you partner with We start with your choice of two state-of- Silicon Mechanics, you the-art processors, for fast, reliable, energy- get more than stellar efficient processing.T hen we add four NVIDIA ® technology - you get an Tesla® GPUs, to dramatically accelerate parallel Expert like Pierre. processing for applications like ray tracing and finite element analysis. Load it up with DDR3 memory, and you have herculean capabilities and an 80 PLUS Platinum Certified power supply, all in the space of a 4U server. -

LINUX JOURNAL CROSS-PLATFORM DEVELOPMENT Shoulda | Openfire | Lazarus | Apparmor | Tircd | Titanium | Qt SEPTEMBER 2009 ISSUE+ 185
Shoulda | Openfire | Lazarus | AppArmor | tircd | Titanium | Qt LINUX JOURNAL ™ LAZARUS a Powerful IDE for Cross- Platform Development CROSS-PLATFORM DEVELOPMENT CROSS-PLATFORM Qt Making Apps Right on All Platforms Build Rich Desktop Apps Since 1994: The Original Magazine of the Linux Community with TITANIUM SEPTEMBER 2009 | ISSUE 185 | www.linuxjournal.com GOOGLE CHROME Open-Source DEVELOPERS Compliance Shoulda | Openfire | Lazarus | AppArmor | tircd | Titanium | Qt | Titanium | AppArmor tircd | Lazarus Shoulda | Openfire Supercharging Best Practices the Web Looking at with V8 AppArmor in Ubuntu Use tircd to Connect to Twitter over IRC SEPTEMBER 2009 ISSUE 185 $5.99US $5.99CAN 09 SHOULDA MAKES +TESTING EASIER FOR RAILS DEVELOPERS 0 09281 03102 4 Temperatures are rising – prices have dropped! 1&1 Summer Specials: 1&1® HOME PACKAGE 2 Domain Names Included (Choose from .com, .net, .org, .biz and .info) N 120 GB Web Space N Credit to start advertising N 1,200 GB Monthly Traffic with major search engines N 1,200 E-mail Accounts like Google™. N Easy-to-use Site Building Tool N 24/7 Customer Support N 1&1 Blog N ... and much more! N 1&1 Photo Gallery 1st year $ .99 per 4 month FREE!* Offer valid through August 31st ! .us Domain Names $2.99 for the first year!* More special offers are available online. For details, visit www.1and1.com Now accepting * Offers valid through August 31, 2009. 24 month minimum contract term and a setup fee of $4.99 apply with the Home Package ® offer. Other terms and conditions may apply. Private domain registration not available with .us domains. -

We've Got Bugs, P
Billix | Rails | Gumstix | Zenoss | Wiimote | BUG | Quantum GIS LINUX JOURNAL ™ REVIEWED: Neuros OSD and COOL PROJECTS Cradlepoint PHS300 Since 1994: The Original Magazine of the Linux Community AUGUST 2008 | ISSUE 172 WE’VE GOT Billix | Rails Gumstix Zenoss Wiimote BUG Quantum GIS MythTV BUGs AND OTHER COOL PROJECTS TOO E-Ink + Gumstix Perfect Billix Match? Kiss Install CDs Goodbye AUGUST How To: 16 Terabytes in One Case www.linuxjournal.com 2008 $5.99US $5.99CAN 08 ISSUE Learn to Fake a Wiimote Linux 172 + UFO Landing Video Interface HOW-TO 0 09281 03102 4 AUGUST 2008 CONTENTS Issue 172 FEATURES 48 THE BUG: A LINUX-BASED HARDWARE MASHUP With the BUG, you get a GPS, camera, motion detector and accelerometer all in one hand-sized unit, and it’s completely programmable. Mike Diehl 52 BILLIX: A SYSADMIN’S SWISS ARMY KNIFE Build a toolbox in your pocket by installing Billix on that spare USB key. Bill Childers 56 FUN WITH E-INK, X AND GUMSTIX Find out how to make standard X11 apps run on an E-Ink display using a Gumstix embedded device. Jaya Kumar 62 ONE BOX. SIXTEEN TRILLION BYTES. Build your own 16 Terabyte file server with hardware RAID. Eric Pearce ON THE COVER • Neuros OSD, p. 44 • Cradlepoint PHS300, p. 42 • We've got BUGs, p. 48 • E-Ink + Gumstix—Perfect Match?, p. 56 • How To: 16 Terabytes in One Case, p. 62 • Billix—Kiss Install CDs Goodbye, p. 52 • Learn to Fake a UFO Landing Video, p. 80 • Wiimote Linux Interface How-To, p. 32 2 | august 2008 www.linuxjournal.com lj026:lj018.qxd 5/14/2008 4:00 PM Page 1 The Straight Talk People -

U | UML | Xen | Wine REVIEWED Vmware 5.5
Jon “maddog” Hall | GPL 3 | GCJ | VMware | QEMU | UML | Xen | Wine REVIEWED VMware 5.5 ™ Since 1994: The Original Magazine of the Linux Community MAY 2006 | www.linuxjournal.com Virtual Linux NEW COLUMN: Jon “maddog” Hall’s Beachhead Tales from the Beach Embedded Java with GCJ Using RTNETLINK AN PUBLICATION USA $5.00 PLUS CAN $6.50 U|xaHBEIGy03102ozXv!:; Is Linux VoIP Ready? MAY 2006 CONTENTS Issue 145 FEATURES ON THE COVER: IMAGE BY AYAAZ RATTANSI 60 RUNNING SOUND APPLICATIONS UNDER WINE 72 XEN You can make Linux sound better with a little Wine. Xen’s unusual approach to virtual systems can give it a speed edge. Dave Phillips Irfan Habib 64 USER-MODE LINUX ON THE COVER Run Linux on top of Linux? It makes sense. Really. • VMware 5.5, p. 56 Matthew E. Hoskins • Jon "maddog" Hall's Beachhead, p. 46 68 QEMU: A MULTIHOST, MULTITARGET EMULATOR • Embedded Java with GCJ, p. 76 Can a free virtual system offer what you need? • Using RTNETLINK, p. 86 Daniel Bartholomew • Is Linux VoIP Ready? p. 80 2 | may 2006 www.linuxjournal.com MAY 2006 CONTENTS Issue 145 COLUMNS REVIEW 22 REUVEN LERNER’S 56 VMWARE WORKSTATION 5.5 AT THE FORGE FOR LINUX HOSTS Google Web Services Mick Bauer 28 MARCEL GAGNÈ’S COOKING WITH LINUX The Virtual Streets of $HOME INDEPTH 80 IS LINUX VOICE OVER IP READY? 76 EMBEDDED JAVA WITH GCJ 34 DAVE TAYLOR’S GCJ may not be for end-user applications, WORK THE SHELL but it’s the bomb for embedded systems. Counting Cards Gene Sally Next Month 36 MICK BAUER’S 80 IS LINUX VOICE OVER IP READY? PARANOID PENGUIN What are the viable VoIP options for Linux Security Features in Debian 3.1 and how do they compare? Machtelt Garrels STORAGE 42 DEE-ANN LEBLANC’S Next month, we’re going fishing. -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -

Linuxvilag-34.Pdf 5767KB 8 2012-05-28 10:19:04
Beköszöntõ Végre megjelent a har- kedtem (márkás, drága, új, csilli-villi), mincnegyedik számunk, amihez adtak Windows XP-t. Ponto- © Kiskapu Kft. Minden jog fenntartva ami azt is jelenti, hogy sabban elõtelepítették nekem a teljes háromévesek lettünk. lemezre. Ha akartam újratelepíthettem, Ezt a matematikailag s egy csöpp szöveg figyelmeztetett, nehézkesen bizonyítható hogy a telepítõ egyedi, abban az érte- kijelentést úgy is megfo- lemben, hogy elsõ lépésként fûbe vágja galmazhattam volna, hogy az egész merevlemezt, ledarálja az három évvel ezelõtt, no- összes adatot, és feltesz nekem egy gyá- vemberben jelent meg az rilag elõtelepített Windowst. Hiába na, ország méltán legnépsze- angyalok ezek az OEM-rendszerek. rûbb Linuxszal foglalkozó Azért (így utolsóként) a „pénzes” terü- nyomtatott sajtóorgánu- letek is kezdenek alkalmazkodni. Már mának elsõ száma. De ez vannak helyek, ahol még azt a plusz talán egy csöppet felleng- két-háromtízezrest sem kell kifizetnünk, zõsen hangzana. ha esetleg más operációs rendszert Szy György Az elsõ szám még irkafûzéssel, sok akarunk a gépünkhöz. Idõ kérdése, és a Linuxvilág fõszerkesztõje, lelkesedéssel és még több sajtóhibával talán eljutunk a nyugaton (és keleten) a Kiskapu Kiadó vezetõje. látott napvilágot. Azóta sokat változ- immár több éve szokásos módihoz: Mindenki levelét örömmel tunk, például nem irkafûzéssel jele- megkérdezik a kereskedõk, mit szeret- várja a következõ levélcímen: nünk meg. A másik kettõ még megvan. nénk. Mert ugye az elég fontos. Lega- [email protected] Ugyanúgy, ahogy a parázs viták is, lábbis nekünk. A vevõ pedig olyan, amelyeket a fordításokkal kapcsán foly- hogy oda megy, ahol azt kapja, ami kell tatunk, vagy a siránkozások, hogy neki, nem azt, amirõl úgy tudja az nyugaton mennyivel szélesebb körben eladó, hogy kell neki. -
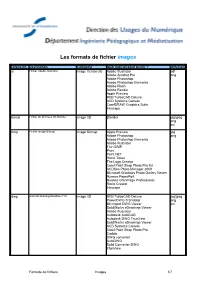
Les Formats De Fichier Images
Les formats de fichier images Extension Description Catégorie Quel logiciel pour ouvrir ? diffusion ai Fichier Adobe Illustrator Image Vectorielle Adobe Illustrator pdf Adobe Acrobat Pro png Adobe Photoshop Adobe Photoshop Elements Adobe Flash Adobe Reader Apple Preview IMSI TurboCAD Deluxe ACD Systems Canvas CorelDRAW Graphics Suite Inkscape blend Fichier de données 3D Blender Image 3D Blender jpg/jpeg png avi bmp Fichier Image Bitmap Image Bitmap Apple Preview jpg Adobe Photoshop png Adobe Photoshop Elements Adobe Illustrator The GIMP Paint Paint.NET Roxio Toast The Logo Creator Corel Paint Shop Photo Pro X3 ACDSee Photo Manager 2009 Microsoft Windows Photo Gallery Viewer Nuance PaperPort Nuance OmniPage Professional Roxio Creator Inkscape dwg AtoCAD Drawing Database File Image 3D IMSI TurboCAD Deluxe jpg/jpeg PowerDWG Translator png Microspot DWG Viewer avi SolidWorks eDrawings Viewer Adobe Illustrator Autodesk AutoCAD Autodesk DWG TrueView SolidWorks eDrawings Viewer ACD Systems Canvas Corel Paint Shop Photo Pro Caddie DWG converter AutoDWG Solid Converter DWG IrfanView Formats de fichiers Images 1/7 Les formats de fichier images Extension Description Catégorie Quel logiciel pour ouvrir ? diffusion dxf Drawing Exchange Format File Image 3D TurboCAD Deluxe 16 jpg/jpeg PowerCADD PowerDWG translator png Microspot DWG Viewer avi NeoOffice Draw DataViz MacLink Plus Autodesk AutoCAD IMSI TurboCAD Deluxe SolidWorks eDrawings Viewer Corel Paint Shop Photo Pro ACD Systems Canvas DWG converter DWG2Image Converter OpenOffice.org Draw Adobe Illustrator -

Puppy Linux (Notes) 07/28/15 17:32
07/28/15 17:30 Welcome (Notes) Intro to Linux Welcome A Basic Introduction to Linux stan reichardt [email protected] 1 07/28/15 17:32 Introduction (Notes) Introduction stan reichardt GNU/Linux for Beginners Brought to you by the Hazelwood Linux Users Group http://hzwlug.sluug.org/ A Special Interest Group of the St. Louis Unix Users Group (SLUUG) http://www.sluug.org/ 2 2 07/28/15 17:32 Linux Basics (Notes) Linux Basics An Introduction 4 Section I The name of the operating system is usually pronounced “Lin-” as in “Fin”, and “-ux” as in “Trucks”, with the emphasis on the first syllable. Linux is a Unix-like and mostly standards compliant (POSIX) computer operating system assembled under the model of free and open-source software development and distribution. The defining component of Linux is the Linux kernel, an operating system kernel first released on 5 October 1991 by Finnish software developer Linus Torvalds. Linux was originally developed as a free operating system for Intel x86–based personal computers, but has since been ported to more computer hardware platforms than any other operating system. Linux is the leading operating system on servers and other big iron systems such as mainframe computers and supercomputers, but is used on only around 1% of desktop computers. Linux also runs on embedded systems, which are devices whose operating system is typically built into the firmware and is highly tailored to the system; this includes mobile phones, tablet computers, network routers, facility automation controls, televisions and video game consoles. Android, 4 Preview (Notes) 07/28/15 17:32 Preview • Like DOS, MS Windows, or Mac OS-X, Linux is an Operating System.