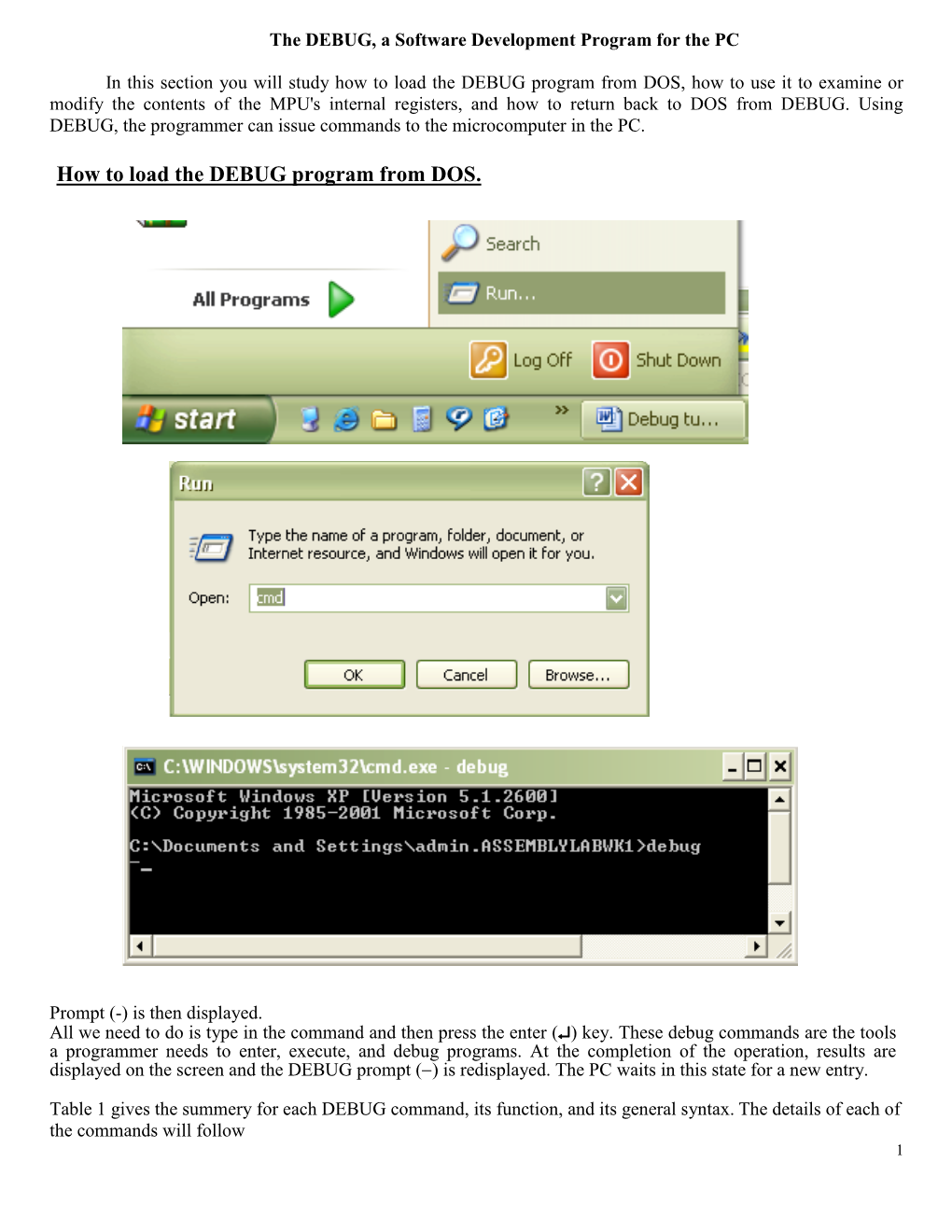
How to Load the DEBUG Program from DOS
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tutorial for VCS
Tutorial for VCS STEP 1: login to the Linux system on Linuxlab server. Start a terminal (the shell prompt). Click here to open a shell window Fig. 1 The screen when you login to the Linuxlab through equeue STEP 2: In the terminal, execute the following command: module add ese461 You could perform “module avail” in the terminal to find the available modules on Linuxlab. Make sure ese461 is presented when you execute this command. 1.Find the available modules 2.Make sure ese461 is presented 3.This command will set up the work environment for class ESE461 Fig. 2 Build work environment for class ESE461 using module 1 STEP 3: Getting started with Verilog • Creating a new folder (better if you have all the files for a project in a specific folder). • Enter into this new folder and start writing your Verilog script in a new file (.v file). Example code for modeling an counter is here • In addition to model code, Test Bench script has to be given in order to verify the functionality of your model (.v file). Example code of test bench for counter is here. Use gedit to edit the .v files (gedit is a commonly used GUI editor on Linux ) Fig. 3 Open gedit through teminal STEP 4: Compiling and simulating your code • In the terminal, change the directory to where your model and test bench files (Counter.v and Counter_tb.v) are present by using this command: cd <path> For example: cd ~/ESE461/VcsTutorial/ (Remark: ‘~’ means home directory on Linux) • Compile the files by typing in the terminal: vcs <file>.v <file_tb>.v In the above example, it should be: vcs Counter.v Counter_tb.v There should be no error presented in the terminal. -

Programmable Interrupt Controller
Programmable Interrupt Controller Dr. Wajiha Shah Outline • Explain how the x86 executes interrupts by using the interrupt vector table and interrupt routines. • List the differences between interrupts and CALL instructions. • Describe the differences between hardware and software interrupts. • Examine the ISR for any interrupt, given its interrupt number. • Describe the function of each pin of the 8259 programmable interrupt controller (PIC) chip. • Explain the purpose of each of the four control words of the 8259 and demonstrate how they are programmed. • Examine the interrupts in x86 PC1s. 8088/86 INTERRUPTS • An interrupt is an external event that informs the CPU that a device needs its service. – In 8088/86 there are a total of 256 interrupts. • INT 00, INT 01, ..., INT FF (sometimes called TYPEs). • When an interrupt is executed the processor: – Saves the flag register (FR), instruction pointer (IP), and code segment register (CS) on the stack,. – Goes to a fixed memory location. • In x86, always four times the value of the interrupt number. 8088/86 INTERRUPTS interrupt service routine (ISR) 1. When an interrupt is invoked it is asked to run a program to perform a certain service. 2. There must be a program associated with every interrupt . 3. This program is commonly referred to as an interrupt service routine (ISR), and also called the interrupt handler. 4. When an interrupt is invoked, the CPU runs the interrupt service routine. 8088/86 INTERRUPTS interrupt service routine (ISR) – For every interrupt there are allocated four bytes of memory in the interrupt vector table. – Two bytes for the IP. – Two for the CS of the ISR. -

16-Bit MS-DOS Programming (MS-DOS & BIOS-Level Programming )
Microprocessors (0630371) Fall 2010/2011 – Lecture Notes # 20 16-Bit MS-DOS Programming (MS-DOS & BIOS-level Programming ) Objectives Real-Address Mode MS-DOS Memory Organization MS-DOS Memory Map Interrupts Mechanism—Introduction Interrupts Mechanism — Steps Types of Interrupts 8086/8088 Pinout Diagrams Redirecting Input-Output INT Instruction Interrupt Vectoring Process Common Interrupts Real-Address Mode Real-address mode (16-bit mode) programs have the following characteristics: o Max 1 megabyte addressable RAM o Single tasking o No memory boundary protection o Offsets are 16 bits IBM PC-DOS: first Real-address OS for IBM-PC Later renamed to MS-DOS, owned by Microsoft MS-DOS Memory Organization Interrupt Vector Table BIOS & DOS data Software BIOS MS-DOS kernel Resident command processor Transient programs Video graphics & text Reserved (device controllers) ROM BIOS MS-DOS Memory Map Address FFFFF R O M BIO S F0000 Reserved C0000 Video Text & Graphics B8000 V R A M Video Graphics A0000 Transient Command Processor Transient Program Area (available for application programs) Resident Command Processor 640K R A M DOS Kernel, Device Drivers Software BIOS BIOS & DOS Data 00400 Interrupt Vector Table 00000 Interrupt Mechanism—Introduction Devices such as the keyboard, the monitor, hard disks etc. can cause such interrupts, when they require service of some kind, such as to get or receive a byte. For example, when you press a key on the keyboard this causes an interrupt. When the Microprocessor is interrupted, it completes the current instruction, and then pushes onto the stack the flags register plus the address of the next instruction (the return address). -

8259 Programmable Interrupt Controller
edge of each clock pulse. When the counter reaches zero, the OUT goes low and the counter is reloaded with the full count and the whole process is repeated. 3) In this way, if the count is odd, the output will be high for (n+1)/2 counts and low for (n-1)/2 count MODE 4 : Software Triggered Strobe In this mode , the OUT is high; It goes low for one clock period at the end of the count. The count must be loaded subsequently outputs MODE 5 : Hardware triggered strobe (Retriggerable). Initially, the out is low, and when the gate pulse is triggered from low to high, The count begins. At the end of count, the OUT goes low for one clock period. 8259 programmable interrupt controller 8259 is Programmable Interrupt Controller (PIC) It is a tool for managing the interrupt requests. 8259 is a very flexible peripheral controller chip: PIC can deal with up to 64 interrupt inputs interrupts can be masked various priority schemes can also programmed. There are 5 hardware interrupts and 2 hardware interrupts in 8085 and 8086 respectively. But by connecting 8259 with CPU, we can increase the interrupt handling capability. 8259 combines the multi interrupt input sources into a single interrupt output. Interfacing of single PIC provides 8 interrupts inputs from IR0-IR7. For example, Interfacing of 8085 and 8259 increases the interrupt handling capability of 8085 microprocessor from 5 to 8 interrupt levels. Features of 8259 PIC microprocessor – 1. Intel 8259 is designed for Intel 8085 and Intel 8086 microprocessor. 2. -

Computers Shouldn't Be Limitations Advertising & Distribution a Handicap Is a Limitation
.. No. 48 July-August 1989 $3.95 T HE MICRO TECHN I CAL J 0 URN A L Tools For The Physically Impaired What's important to people who have handicaps? We asked them. (Their responses may surprise you.) The Adventure Begins page 8 Dallas Vordahl demonstrates what you can do with a computer, a mouthstick, and a very limited amount of head motion. Writing Software For page 16 The Blind Don' t exclude the blind from your next software package. File Transfer Via The page 20 Parallel Port The LIMBO Project page 28 Build a maze-running robot. And More ... Debugging A Processor page 44 Growing Your Own page 66 Software Business Great SOGs page 83 And Much, Much, More 07 a 7447019388 3 U[J!]£?[jj) J/@[J!]£? !fJ©llfU/5Ju O[jj)(]@ (j] /JJ@r:'.JQ£?fj[J!]O /LfI1@@£?(JJ(]@£?J/ (j][jj)@ @[jj)@]O[jj)QQ£?O[jj)@] (]@@ODDD Introducing ... The PC-LabCard Family Only from HSC Electronic Supply Digital 1/0 and Prototype Development IBM PC/XT/AT and it's Counter Card compatible models are moving into Card Industrial/Laboratory applications at • 32 Digital Input Channels • Large breadboard area (3290 holes) - TTL compatible an increasing rate. The reasons for • Independent memory and I/O address - Low loading: 0.2 rnA at O.4V input this include their price/performance decoders built-in • 32 Digital Output Channels ratio and short user learning curve. • Memory and I/O ports are jumper - TTL compatible PC-based data acquisition boards selectable - Driving capacity: Sink 24 rnA, are now taking the place of the • All bus signals are buffered, marked, source 15 rnA and ready for use • Intel 8253 Timer/Counter traditional data loggers or recorders - 3 channels of timer/counter which cost several times more. -

JAMS 7.X User Guide
User Guide JAMS Scheduler 7.3 Copyright Terms and Conditions Copyright Help/Systems LLC and its group of companies. The content in this document is protected by the Copyright Laws of the United States of America and other countries worldwide. The unauthorized use and/or duplication of this material without express and written permission from HelpSystems is strictly prohibited. Excerpts and links may be used, provided that full and clear credit is given to HelpSystems with appropriate and specific direction to the original content. HelpSystems and its trademarks are properties of the HelpSystems group of companies. All other marks are property of their respective owners. 202108110755 JAMS 7.X User Guide Table of Contents JAMS 7.X Client Features 3 Jobs In JAMS 4 Working with Jobs 5-19 Scheduling Recurring Jobs 20-22 Execution Methods 23-27 Submitting Jobs Manually 28-29 Sequence Jobs 30-34 Managing Sequence Parameters 35-38 Sequence Tasks 39-47 Workflow Jobs 48-51 Workflow Activities 52-59 Migrating JAMS Objects 60-61 File Transfer Features 62-67 Variables 68 Working with Variables 69-71 Elements 72 Documentation Elements 73-74 EventHandler Elements 75-79 Prerequisite Elements 80-83 Result Elements 84-86 Trigger Elements 87-92 Folders 93 Working with Folders 94-104 Dates and Times 105 Date Properties 106-107 Creating Special Date Definitions 108-111 Specifying Dates Using Natural Language 112-114 Named Times in JAMS 115-118 Dashboards and Reports 119 Custom Dashboards 120-129 Creating New Report Templates and Customizing Existing Reports -

How to Cheat at Windows System Administration Using Command Line Scripts
www.dbebooks.com - Free Books & magazines 405_Script_FM.qxd 9/5/06 11:37 AM Page i How to Cheat at Windows System Administration Using Command Line Scripts Pawan K. Bhardwaj 405_Script_FM.qxd 9/5/06 11:37 AM Page ii Syngress Publishing, Inc., the author(s), and any person or firm involved in the writing, editing, or produc- tion (collectively “Makers”) of this book (“the Work”) do not guarantee or warrant the results to be obtained from the Work. There is no guarantee of any kind, expressed or implied, regarding the Work or its contents.The Work is sold AS IS and WITHOUT WARRANTY.You may have other legal rights, which vary from state to state. In no event will Makers be liable to you for damages, including any loss of profits, lost savings, or other incidental or consequential damages arising out from the Work or its contents. Because some states do not allow the exclusion or limitation of liability for consequential or incidental damages, the above limitation may not apply to you. You should always use reasonable care, including backup and other appropriate precautions, when working with computers, networks, data, and files. Syngress Media®, Syngress®,“Career Advancement Through Skill Enhancement®,”“Ask the Author UPDATE®,” and “Hack Proofing®,” are registered trademarks of Syngress Publishing, Inc.“Syngress:The Definition of a Serious Security Library”™,“Mission Critical™,” and “The Only Way to Stop a Hacker is to Think Like One™” are trademarks of Syngress Publishing, Inc. Brands and product names mentioned in this book are trademarks or service marks of their respective companies. -

The Programmable Interrupt Controller
The Programmable Interrupt Controller SYSC-3006 Interrupt Controller • Before : The 8086 processor has two hardware interrupt signals • We’ve seen at least 2 interrupt sources. 8086 Timer Keyboard NMI INTR (INT 8) (INT 9) bus • “Decides from which vector table location to load ISR address” SYSC-3006 Interrupt Vectors: Deciding which ISR to run • Auto-vectored interrupts: vector predefined as part of CPU design – For each HW signal, CPU goes to a particular interrupt-type in vector table. – 8086 Example: NMI (auto-vectored -> Interrupt-type 2) • NMI asserted, 8086 executes INT type 2 interrupt behaviour: – save processor state – obtain ISR address from vector 2 (memory address 0:8) – execute type 2 ISR • More than one device shares the NMI signal? (e.g. RAM and power supply) – NMI ISR must check (poll) each device (which one caused the interrupt?) SYSC-3006 Interrupt Vectors: Deciding which ISR to run • Vectored interrupts: vector determined during systems design. – CPU performs “interrupt-acknowledge” cycle -> reads interrupt-type from data bus • Interrupting device can provide interrupt-type • 8086: interrupt controller (IC) External hardware – Vectored interrupts: robust method for multiple devices connected to single interrupt line (no polling!) • Interrupt-type: mapping to unique ISR for each device • Interrupt controller acts as a multiplexer – 8086 Example: INTR is a vectored interrupt SYSC-3006 Interrupt Controller • Interrupt controller acts as a funnel for multiple device interrupts – Allows many devices to share the 8086’s single -

And PC 750 (Type 6887)
Technical Information Manual PC 730 (Type 6877) and PC 750 (Type 6887) Technical Information Manual IBM PC 730 (Type 6877) and PC 750 (Type 6887) Note Before using this information and the product it supports, be sure to read the general information under Appendix B, “Notices and Trademarks” on page 65. First Edition (June 1996) The following paragraph does not apply to the United Kingdom or any country where such provisions are inconsistent with local law: INTERNATIONAL BUSINESS MACHINES CORPORATION PROVIDES THIS PUBLICATION “AS IS” WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. Some states do not allow disclaimer of express or implied warranties in certain transactions, therefore, this statement may not apply to you. This publication could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be incorporated in new editions of the publication. IBM may make improvements and/or changes in the product(s) and/or the program(s) described in this publication at any time. It is possible that this publication may contain reference to, or information about, IBM products (machines and programs), programming, or services that are not announced in your country. Such references or information must not be construed to mean that IBM intends to announce such IBM products, programming, or services in your country. Requests for technical information about IBM products should be made to your IBM reseller or IBM marketing representative. IBM may have patents or pending patent applications covering subject matter in this document. -

Toolkit Feature Interactive Debug Facility User's Guide
High Level Assembler for z/OS & z/VM & z/VSE IBM Toolkit Feature Interactive Debug Facility User's Guide Version 1 Release 6 GC26-8709-09 High Level Assembler for z/OS & z/VM & z/VSE IBM Toolkit Feature Interactive Debug Facility User's Guide Version 1 Release 6 GC26-8709-09 Note Before using this information and the product it supports, be sure to read the general information under “Notices” on page 311. This edition applies to IBM High Level Assembler for z/OS & z/VM & z/VSE Toolkit Feature, Release 6, Program Number 5696-234 and to any subsequent releases until otherwise indicated in new editions. Make sure that you are using the correct edition for the level of the product. Order publications through your IBM representative or the IBM branch office serving your locality. IBM welcomes your comments. For information on how to send comments, see “How to send your comments to IBM” on page xv. © Copyright IBM Corporation 1992, 2017. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures ............... ix Building a module on z/OS ........ 17 Building a module on CMS ........ 17 About this book ........... xi Building a phase on z/VSE ........ 17 Running ASMLANGX ........... 18 Syntax notation ............. xi Extraction file allocation on z/OS ...... 18 Online language extraction on TSO ..... 19 How to send your comments to IBM .. xv Batch language extraction on z/OS ..... 19 If you have a technical problem ....... xv Online language extraction on CMS ..... 20 Batch language extraction on z/VSE .... -

Befehlsverzeichnis Zu MS-DOS 3.3 Ansi.Sys Assign Attrib Autoexec.Bat
117 Befehlsverzeichnis zu MS-DOS 3.3 Beschreibung der Befehle (bis Version 3.3 einschlieBlich.) in drei Punkten: J) Be/ehlswort: Befehlszweck, Befehlsart (interner oder externer Befehl). 2) Allgemeilles Format: Klammerangaben wahlfrei, ( .. ) fOr beliebig wiederholbaren Begriff, / fOr entweder-oder, d: fOr Laufwerksangabe. 3) Beispiele: mit Befehlsaufrufen zu typischen Anwendungen. append (ab DOS 3.3) Auf Dateien zugreifen (extern) append d:Pfad (;( d:)Pfad ... ) append (/ x)( I e) ansi.sys Tastatur-Treiber (fur device) device=ansi.sys assign Zugriff umleiten (extern) assign (x( = )y( .. )) attrib Dateianderungsattribut (extern) attrib (+r / -r)(+a/ -a) (d:)(Pfad)(Dateiname(.erw) (/ s) autoexec.bat Spezielle Stapeldatei backup Daten von Platte sichern (extern) backup d:(Pfad)(Dateiname(.erw)) d:(s)( / m)( / a)( / d:u.mm.jj) break Abbruch Strg-C prufen (intern) break (on/ off) buffers Pufferanzahl (fur config.sys) buffers=x cd Verzeichnis wechseln (intern) cd (d:)(Pfad) chcp (ab DOS 3.3) Zeichensatztabelle (intern) chcp (nnn) Gewahlte Zeichen8at~tabelle nnn. 118 chdir Wie cd: (intern) chkdsk Speicherstatusbericht (extern) chkdsk(d:)(Pfad)(Dateiname(.erw))( If)( Iv) f=Fehler. v=Anzeigen cis Bildschirm IOschen (intern) command Befehlsprozessor rufen (extern) command (d:)(Pfad)(/p)(/c Zeichenfolge) (/e:xxxxx) comp Dateiinhalt vergleichen (extern) comp (d:)(Pfad)(Dateiname(.erw)) (d:)(Pfad)( Dateiname(.erw)) copy Dateil Datei2 Dateien kopieren (intern) copy (d:)(Pfad)Dateiname(.erw) (d:)(Dateiname(.erw))( Iv) copy Dateil + Datei2 ... Datei Dateien zusammenfiigen (intern) copy (d:)(Pfad)Dateiname(.erw) (+( d:)(Pfad)Dateiname(.erw) ... ) (d: )(Plad)(Dateiname( .erw) )(/v) copy Eingabeeinheit Datei Eingabe von Einheit aus (intern). copy Datei Ausgabeeinheit Datei drucken (intern) country Linderanpassung (fiir config.sys) country=xxx mit xxx=049 fur Deutschland. -

IBM Tivoli Directory Server – Oracle Enterprise Gateway Integration Guide
Oracle Enterprise Gateway An Oracle White Paper June 2011 IBM Tivoli Directory Server – Oracle Enterprise Gateway Integration Guide 1 / 28 Oracle Enterprise Gateway Disclaimer The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, and timing of any features or functionality described for Oracle’s products remains at the sole discretion of Oracle. 2 / 28 Oracle Enterprise Gateway 1. Introduction ....................................................................................... 4 1.1. Purpose ...................................................................................... 4 1.2. LDAP Architecture ..................................................................... 5 1.3. Setup Used for this Guide: ......................................................... 5 2. Directory Details ................................................................................ 5 2.1. Directory Structure ..................................................................... 5 2.2. Connection Details ..................................................................... 5 3. Authenticate User with HTTP Basic HTTP Filter .............................. 6 3.1. Create a policy to authenticate a user in the LDAP directory .... 6 3.2. Create a new relative path for the Policy ..................................