Boolean Ring Cryptographic Equation Solving
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Boolean Like Semirings
Int. J. Contemp. Math. Sciences, Vol. 6, 2011, no. 13, 619 - 635 Boolean Like Semirings K. Venkateswarlu Department of Mathematics, P.O. Box. 1176 Addis Ababa University, Addis Ababa, Ethiopia [email protected] B. V. N. Murthy Department of Mathematics Simhadri Educational Society group of institutions Sabbavaram Mandal, Visakhapatnam, AP, India [email protected] N. Amarnath Department of Mathematics Praveenya Institute of Marine Engineering and Maritime Studies Modavalasa, Vizianagaram, AP, India [email protected] Abstract In this paper we introduce the concept of Boolean like semiring and study some of its properties. Also we prove that the set of all nilpotent elements of a Boolean like semiring forms an ideal. Further we prove that Nil radical is equal to Jacobson radical in a Boolean like semi ring with right unity. Mathematics Subject Classification: 16Y30,16Y60 Keywords: Boolean like semi rings, Boolean near rings, prime ideal , Jacobson radical, Nil radical 1 Introduction Many ring theoretic generalizations of Boolean rings namely , regular rings of von- neumann[13], p- rings of N.H,Macoy and D.Montgomery [6 ] ,Assoicate rings of I.Sussman k [9], p -rings of Mc-coy and A.L.Foster [1 ] , p1, p2 – rings and Boolean semi rings of N.V.Subrahmanyam[7] have come into light. Among these, Boolean like rings of A.L.Foster [1] arise naturally from general ring dulity considerations and preserve many of the formal 620 K. Venkateswarlu et al properties of Boolean ring. A Boolean like ring is a commutative ring with unity and is of characteristic 2 with ab (1+a) (1+b) = 0. -

Solving Equations; Patterns, Functions, and Algebra; 8.15A
Mathematics Enhanced Scope and Sequence – Grade 8 Solving Equations Reporting Category Patterns, Functions, and Algebra Topic Solving equations in one variable Primary SOL 8.15a The student will solve multistep linear equations in one variable with the variable on one and two sides of the equation. Materials • Sets of algebra tiles • Equation-Solving Balance Mat (attached) • Equation-Solving Ordering Cards (attached) • Be the Teacher: Solving Equations activity sheet (attached) • Student whiteboards and markers Vocabulary equation, variable, coefficient, constant (earlier grades) Student/Teacher Actions (what students and teachers should be doing to facilitate learning) 1. Give each student a set of algebra tiles and a copy of the Equation-Solving Balance Mat. Lead students through the steps for using the tiles to model the solutions to the following equations. As you are working through the solution of each equation with the students, point out that you are undoing each operation and keeping the equation balanced by doing the same thing to both sides. Explain why you do this. When students are comfortable with modeling equation solutions with algebra tiles, transition to writing out the solution steps algebraically while still using the tiles. Eventually, progress to only writing out the steps algebraically without using the tiles. • x + 3 = 6 • x − 2 = 5 • 3x = 9 • 2x + 1 = 9 • −x + 4 = 7 • −2x − 1 = 7 • 3(x + 1) = 9 • 2x = x − 5 Continue to allow students to use the tiles whenever they wish as they work to solve equations. 2. Give each student a whiteboard and marker. Provide students with a problem to solve, and as they write each step, have them hold up their whiteboards so you can ensure that they are completing each step correctly and understanding the process. -

Diffman: an Object-Oriented MATLAB Toolbox for Solving Differential Equations on Manifolds
Applied Numerical Mathematics 39 (2001) 323–347 www.elsevier.com/locate/apnum DiffMan: An object-oriented MATLAB toolbox for solving differential equations on manifolds Kenth Engø a,∗,1, Arne Marthinsen b,2, Hans Z. Munthe-Kaas a,3 a Department of Informatics, University of Bergen, N-5020 Bergen, Norway b Department of Mathematical Sciences, NTNU, N-7491 Trondheim, Norway Abstract We describe an object-oriented MATLAB toolbox for solving differential equations on manifolds. The software reflects recent development within the area of geometric integration. Through the use of elements from differential geometry, in particular Lie groups and homogeneous spaces, coordinate free formulations of numerical integrators are developed. The strict mathematical definitions and results are well suited for implementation in an object- oriented language, and, due to its simplicity, the authors have chosen MATLAB as the working environment. The basic ideas of DiffMan are presented, along with particular examples that illustrate the working of and the theory behind the software package. 2001 IMACS. Published by Elsevier Science B.V. All rights reserved. Keywords: Geometric integration; Numerical integration of ordinary differential equations on manifolds; Numerical analysis; Lie groups; Lie algebras; Homogeneous spaces; Object-oriented programming; MATLAB; Free Lie algebras 1. Introduction DiffMan is an object-oriented MATLAB [24] toolbox designed to solve differential equations evolving on manifolds. The current version of the toolbox addresses primarily the solution of ordinary differential equations. The solution techniques implemented fall into the category of geometric integrators— a very active area of research during the last few years. The essence of geometric integration is to construct numerical methods that respect underlying constraints, for instance, the configuration space * Corresponding author. -
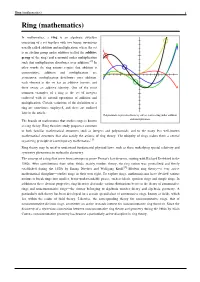
Ring (Mathematics) 1 Ring (Mathematics)
Ring (mathematics) 1 Ring (mathematics) In mathematics, a ring is an algebraic structure consisting of a set together with two binary operations usually called addition and multiplication, where the set is an abelian group under addition (called the additive group of the ring) and a monoid under multiplication such that multiplication distributes over addition.a[›] In other words the ring axioms require that addition is commutative, addition and multiplication are associative, multiplication distributes over addition, each element in the set has an additive inverse, and there exists an additive identity. One of the most common examples of a ring is the set of integers endowed with its natural operations of addition and multiplication. Certain variations of the definition of a ring are sometimes employed, and these are outlined later in the article. Polynomials, represented here by curves, form a ring under addition The branch of mathematics that studies rings is known and multiplication. as ring theory. Ring theorists study properties common to both familiar mathematical structures such as integers and polynomials, and to the many less well-known mathematical structures that also satisfy the axioms of ring theory. The ubiquity of rings makes them a central organizing principle of contemporary mathematics.[1] Ring theory may be used to understand fundamental physical laws, such as those underlying special relativity and symmetry phenomena in molecular chemistry. The concept of a ring first arose from attempts to prove Fermat's last theorem, starting with Richard Dedekind in the 1880s. After contributions from other fields, mainly number theory, the ring notion was generalized and firmly established during the 1920s by Emmy Noether and Wolfgang Krull.[2] Modern ring theory—a very active mathematical discipline—studies rings in their own right. -

Teaching Strategies for Improving Algebra Knowledge in Middle and High School Students
EDUCATOR’S PRACTICE GUIDE A set of recommendations to address challenges in classrooms and schools WHAT WORKS CLEARINGHOUSE™ Teaching Strategies for Improving Algebra Knowledge in Middle and High School Students NCEE 2015-4010 U.S. DEPARTMENT OF EDUCATION About this practice guide The Institute of Education Sciences (IES) publishes practice guides in education to provide edu- cators with the best available evidence and expertise on current challenges in education. The What Works Clearinghouse (WWC) develops practice guides in conjunction with an expert panel, combining the panel’s expertise with the findings of existing rigorous research to produce spe- cific recommendations for addressing these challenges. The WWC and the panel rate the strength of the research evidence supporting each of their recommendations. See Appendix A for a full description of practice guides. The goal of this practice guide is to offer educators specific, evidence-based recommendations that address the challenges of teaching algebra to students in grades 6 through 12. This guide synthesizes the best available research and shares practices that are supported by evidence. It is intended to be practical and easy for teachers to use. The guide includes many examples in each recommendation to demonstrate the concepts discussed. Practice guides published by IES are available on the What Works Clearinghouse website at http://whatworks.ed.gov. How to use this guide This guide provides educators with instructional recommendations that can be implemented in conjunction with existing standards or curricula and does not recommend a particular curriculum. Teachers can use the guide when planning instruction to prepare students for future mathemat- ics and post-secondary success. -

Problems and Comments on Boolean Algebras Rosen, Fifth Edition: Chapter 10; Sixth Edition: Chapter 11 Boolean Functions
Problems and Comments on Boolean Algebras Rosen, Fifth Edition: Chapter 10; Sixth Edition: Chapter 11 Boolean Functions Section 10. 1, Problems: 1, 2, 3, 4, 10, 11, 29, 36, 37 (fifth edition); Section 11.1, Problems: 1, 2, 5, 6, 12, 13, 31, 40, 41 (sixth edition) The notation ""forOR is bad and misleading. Just think that in the context of boolean functions, the author uses instead of ∨.The integers modulo 2, that is ℤ2 0,1, have an addition where 1 1 0 while 1 ∨ 1 1. AsetA is partially ordered by a binary relation ≤, if this relation is reflexive, that is a ≤ a holds for every element a ∈ S,it is transitive, that is if a ≤ b and b ≤ c hold for elements a,b,c ∈ S, then one also has that a ≤ c, and ≤ is anti-symmetric, that is a ≤ b and b ≤ a can hold for elements a,b ∈ S only if a b. The subsets of any set S are partially ordered by set inclusion. that is the power set PS,⊆ is a partially ordered set. A partial ordering on S is a total ordering if for any two elements a,b of S one has that a ≤ b or b ≤ a. The natural numbers ℕ,≤ with their ordinary ordering are totally ordered. A bounded lattice L is a partially ordered set where every finite subset has a least upper bound and a greatest lower bound.The least upper bound of the empty subset is defined as 0, it is the smallest element of L. -

Step-By-Step Solution Possibilities in Different Computer Algebra Systems
Step-by-Step Solution Possibilities in Different Computer Algebra Systems Eno Tõnisson University of Tartu Estonia E-mail: [email protected] Introduction The aim of my research is to compare different computer algebra systems, and specifically to find out how the students could solve problems step-by-step using different computer algebra systems. The present paper provides the preliminary comparison of some aspects related to step-by-step solution in DERIVE, Maple, Mathematica, and MuPAD. The paper begins with examples of one-step solutions of equations. This is followed by a cursory survey of useful commands, entering commands, programming etc. I hope that a more detailed and complete review will be composed quite soon. Suggestions for complementing the comparison are welcome. It is necessary to know which concrete versions are under consideration. In alphabetical order: DERIVE for Windows. Version 4.11 (1996) Maple V Release 5. Student Version 5.00 (1998) Mathematica for Students. Version 3.0 (1996) MuPAD Light. Version 1.4.1 (1998) Only pure systems (without additional packages, etc.) are under consideration. I believe that there may be more (especially interface-sensitive) possibilities in MuPAD Pro than in MuPAD Light. My paper is not the first comparison, of course. I found several previous ones in the Internet. For example, 1. Michael Wester. A review of CAS mathematical capabilities. 1995 There are 131 short problems covering a broad range of symbolic mathematics. http://math.unm.edu/~wester/cas/Paper.ps (One of the profoundest comparisons is probably M. Wester's book Practical Guide to Computer Algebra Systems.) 1 2. -

Mathematics 721 Fall 2016 on Dynkin Systems Definition. a Dynkin
Mathematics 721 Fall 2016 On Dynkin systems Definition. A Dynkin-system D on X is a collection of subsets of X which has the following properties. (i) X 2 D. (ii) If A 2 D then its complement Ac := X n A belong to D. 1 (iii) If An is a sequence of mutually disjoint sets in D then [n=1An 2 D. Observe that every σ-algebra is a Dynkin system. A1. In the literature one can also find a definition with alternative axioms (i), (ii)*, (iii)* where again (i) X 2 D, and (ii)* If A; B are in D and A ⊂ B then B n A 2 D. 1 (iii)* If An 2 D, An ⊂ An+1 for all n = 1; 2; 3;::: then also [n=1An 2 D. Prove that the definition with (i), (ii), (iii) is equivalent with the definition with (i), (ii)*, (iii)*. A2. Verify: If E is any collection of subsets of X then the intersection of all Dynkin-systems containing E is a Dynkin system containing E. It is the smallest Dynkin system containing E. We call it the Dynkin-system generated by E, and denote it by D(E). Definition: A collection A of subsets of X is \-stable if for A 2 A and B 2 A we also have A \ B 2 A. Observe that a \-stable system is stable under finite intersections. A3. (i) Show that if D is a \-stable Dynkin system, then the union of two sets in D is again in D. (ii) Prove: A Dynkin-system is a σ-algebra if and only if it is \-stable. -

The Evolution of Equation-Solving: Linear, Quadratic, and Cubic
California State University, San Bernardino CSUSB ScholarWorks Theses Digitization Project John M. Pfau Library 2006 The evolution of equation-solving: Linear, quadratic, and cubic Annabelle Louise Porter Follow this and additional works at: https://scholarworks.lib.csusb.edu/etd-project Part of the Mathematics Commons Recommended Citation Porter, Annabelle Louise, "The evolution of equation-solving: Linear, quadratic, and cubic" (2006). Theses Digitization Project. 3069. https://scholarworks.lib.csusb.edu/etd-project/3069 This Thesis is brought to you for free and open access by the John M. Pfau Library at CSUSB ScholarWorks. It has been accepted for inclusion in Theses Digitization Project by an authorized administrator of CSUSB ScholarWorks. For more information, please contact [email protected]. THE EVOLUTION OF EQUATION-SOLVING LINEAR, QUADRATIC, AND CUBIC A Project Presented to the Faculty of California State University, San Bernardino In Partial Fulfillment of the Requirements for the Degre Master of Arts in Teaching: Mathematics by Annabelle Louise Porter June 2006 THE EVOLUTION OF EQUATION-SOLVING: LINEAR, QUADRATIC, AND CUBIC A Project Presented to the Faculty of California State University, San Bernardino by Annabelle Louise Porter June 2006 Approved by: Shawnee McMurran, Committee Chair Date Laura Wallace, Committee Member , (Committee Member Peter Williams, Chair Davida Fischman Department of Mathematics MAT Coordinator Department of Mathematics ABSTRACT Algebra and algebraic thinking have been cornerstones of problem solving in many different cultures over time. Since ancient times, algebra has been used and developed in cultures around the world, and has undergone quite a bit of transformation. This paper is intended as a professional developmental tool to help secondary algebra teachers understand the concepts underlying the algorithms we use, how these algorithms developed, and why they work. -

Proto-Boolean Rings
An. S¸t. Univ. Ovidius Constant¸a Vol. 19(3), 2011, 175{194 Proto-Boolean rings Sergiu Rudeanu Abstract We introduce the family of R-based proto-Boolean rings associated with an arbitrary commutative ring R. They generalize the proto- Boolean algebra devised by Brown [4] as a tool for expressing in modern language Boole's research in The Laws of Thought. In fact the algebraic results from [4] are recaptured within the framework of proto-Boolean rings, along with other theorems. The free Boolean algebras with a fi- nite or countable set of free generators, and the ring of pseudo-Boolean functions, used in operations research for problems of 0{1 optimization, are also particular cases of proto-Boolean rings. The deductive system in Boole's Laws of Thought [3] involves both an alge- braic calculus and a \general method in Logic" making use of this calculus. Of course, Boole's treatises do not conform to contemporary standards of rigour; for instance, the modern concept of Boolean algebra was in fact introduced by Whitehead [12] in 1898; see e.g. [9]. Several authors have addressed the problem of presenting Boole's creation in modern terms. Thus Beth [1], Section 25 summarizes the approach of Hoff- Hansen and Skolem, who describe the algebra devised by Boole as the quotient of an algebra of polynomial functions by the ideal generated by x2 − x; y2 − y; z2 − z; : : : . Undoubtedly the most comprehensive analysis of the Laws of Thought is that offered by Hailperin [5] in terms of multisets. Quite recently, Brown [4], taking for granted the existence of formal entities described as polynomials with integer coefficients, subject to the usual computation rules 2 except that the indeterminates are idempotent (xi = xi), analyses Chapters V-X of [3] within this elementary framework, which he calls proto-Boolean algebra. -

Constructing a Computer Algebra System Capable of Generating Pedagogical Step-By-Step Solutions
DEGREE PROJECT IN COMPUTER SCIENCE AND ENGINEERING, SECOND CYCLE, 30 CREDITS STOCKHOLM, SWEDEN 2016 Constructing a Computer Algebra System Capable of Generating Pedagogical Step-by-Step Solutions DMITRIJ LIOUBARTSEV KTH ROYAL INSTITUTE OF TECHNOLOGY SCHOOL OF COMPUTER SCIENCE AND COMMUNICATION Constructing a Computer Algebra System Capable of Generating Pedagogical Step-by-Step Solutions DMITRIJ LIOUBARTSEV Examenrapport vid NADA Handledare: Mårten Björkman Examinator: Olof Bälter Abstract For the problem of producing pedagogical step-by-step so- lutions to mathematical problems in education, standard methods and algorithms used in construction of computer algebra systems are often not suitable. A method of us- ing rules to manipulate mathematical expressions in small steps is suggested and implemented. The problem of creat- ing a step-by-step solution by choosing which rule to apply and when to do it is redefined as a graph search problem and variations of the A* algorithm are used to solve it. It is all put together into one prototype solver that was evalu- ated in a study. The study was a questionnaire distributed among high school students. The results showed that while the solutions were not as good as human-made ones, they were competent. Further improvements of the method are suggested that would probably lead to better solutions. Referat Konstruktion av ett datoralgebrasystem kapabelt att generera pedagogiska steg-för-steg-lösningar För problemet att producera pedagogiska steg-för-steg lös- ningar till matematiska problem inom utbildning, är vanli- ga metoder och algoritmer som används i konstruktion av datoralgebrasystem ofta inte lämpliga. En metod som an- vänder regler för att manipulera matematiska uttryck i små steg föreslås och implementeras. -

Analytic Geometry
CHAPTER 2 Analytic Geometry Euclid talks about geometry in Elements as if there is only one geometry. Today, some people think of there being several, and others think of there being infinitely many. Hopefully, after you get through this course, you will be in the second group. The people in the first group generally think of geometry as running from Euclid to Hilbert and then branching into Euclidean geometry, hyperbolic geometry and elliptic geometry. People in the second group understand that perfectly well, but include another, earlier brach starting with Rene Descartes (usually pronounced like “day KART”). This branch continues through people like Gauss and Riemann, and even people like Albert Einstein. In my mind, two of the major advances in the understanding of geometry were known to Descartes. One of these, was only known to Descartes, but Gauss, it seems, figured it out on his own, and we all followed him. The other you know very well, but you probably don’t know much about where it came from. This was the development of analytic geometry, geometry using coordinates. The other is not known very well at all, but Descartes noticed something that tells us that geometry should be built upon a general concept of curvature. What is generally called Modern geometry begins with Euclid and ends with Hilbert. The alternate path, the truly contemporary geometry, begins with Descartes and blossoms with Riemann. Note that, as is typical, modern usually means a long time ago. We’ll look at analytic geometry first, and Descartes’ other piece of insight will come later.