Cisco Subscriber Edge Services Manager Application Management Guide, Release
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Java Management Extension Didier DONSEZ
http://www-adele.imag.fr/users/Didier.Donsez/cours JMX Java Management eXtension Didier DONSEZ Université Joseph Fourier –Grenoble 1 PolyTech’Grenoble LIG/ADELE [email protected], [email protected] 19/02/2008 Outline Motivation Architecture MBeans Standard, Dynamic Monitor Notification Utilities Remote Management Connector & Adaptor API Tools JSR Bibliography (c)Donsez,JMX Didier 2003-2008, 2 19/02/2008 Under Translation Motivations fr->en Service d’administration d’applications Ressources matérielles accessibles depuis une JVM Ressources logiciels s’exécutant sur une JVM S’inspire de SNMP Instrumentations des ressources au moyen de composants appelés MBean (Manageable Bean) Adopté initialement par J2EE et maintenant J2SE 1.5 (c)Donsez,JMX Didier 2003-2008, 3 19/02/2008 Usage Get and set applications configuration (Pull) Collect statistics (Pull) Performance Ressources usage Problems Notify events (Push) Faults State changes (c)Donsez,JMX Didier 2003-2008, 4 19/02/2008 JMX 3-Level Architecture JMX Web SNMP Specific Browser Console Console Console JConsole HTML/HTTP SNMP Remote RMI HTTP/SOAP Management Level C C’ A A’ Agent MBeanServer Level Probe MBean1 MBean2 MXBean3 (c)Donsez,JMX Didier 2003-2008, Level 5 19/02/2008 JMX 3-Level Architecture JMX Web SNMP Specific Browser Console Console Console JConsole HTML/HTTP SNMP Remote RMI HTTP/SOAP Management Level Connector Connector’ Adaptor Adaptor’ Agent MBeanServer Level Standard Dynamic Probe MXBean3 (c)Donsez,JMX Didier 2003-2008, Level MBean1 MBean2 For Wikipedia 6 19/02/2008 JMX 3-Level Architecture Probe level JMX Web SNMP Specific Browser Console Console Console Resources,JConsole such as applications, devices, or services, are instrumentedHTML/HTTP using JavaSNMP objects called Managed Beans (MBeans). -
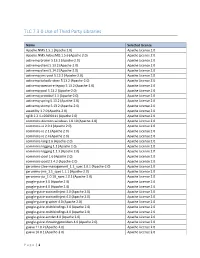
TLC 7.3.0 Use of Third Party Libraries
TLC 7.3.0 Use of Third Party Libraries Name Selected License Apache.NMS 1.5.1 (Apache 2.0) Apache License 2.0 Apache.NMS.ActiveMQ 1.5.6 (Apache 2.0) Apache License 2.0 activemq-broker 5.13.2 (Apache-2.0) Apache License 2.0 activemq-client 5.13.2 (Apache-2.0) Apache License 2.0 activemq-client 5.14.2 (Apache-2.0) Apache License 2.0 activemq-jms-pool 5.13.2 (Apache-2.0) Apache License 2.0 activemq-kahadb-store 5.13.2 (Apache-2.0) Apache License 2.0 activemq-openwire-legacy 5.13.2 (Apache-2.0) Apache License 2.0 activemq-pool 5.13.2 (Apache-2.0) Apache License 2.0 activemq-protobuf 1.1 (Apache-2.0) Apache License 2.0 activemq-spring 5.13.2 (Apache-2.0) Apache License 2.0 activemq-stomp 5.13.2 (Apache-2.0) Apache License 2.0 awaitility 1.7.0 (Apache-2.0) Apache License 2.0 cglib 2.2.1-v20090111 (Apache 2.0) Apache License 2.0 commons-daemon-windows 1.0.10 (Apache-2.0) Apache License 2.0 commons-io 2.0.1 (Apache 2.0) Apache License 2.0 commons-io 2.1 (Apache 2.0) Apache License 2.0 commons-io 2.4 (Apache 2.0) Apache License 2.0 commons-lang 2.6 (Apache-2.0) Apache License 2.0 commons-logging 1.1 (Apache 2.0) Apache License 2.0 commons-logging 1.1.3 (Apache 2.0) Apache License 2.0 commons-pool 1.6 (Apache 2.0) Apache License 2.0 commons-pool2 2.4.2 (Apache-2.0) Apache License 2.0 geronimo-j2ee-management_1.1_spec 1.0.1 (Apache-2.0) Apache License 2.0 geronimo-jms_1.1_spec 1.1.1 (Apache-2.0) Apache License 2.0 geronimo-jta_1.0.1B_spec 1.0.1 (Apache-2.0) Apache License 2.0 google-guice 3.0 (Apache 2.0) Apache License 2.0 google-guice 4.0 (Apache -

Coremedia Operations Basics Coremedia Operations Basics |
CoreMedia 6 //Version 5.3.27 CoreMedia Operations Basics CoreMedia Operations Basics | CoreMedia Operations Basics Copyright CoreMedia AG © 2012 CoreMedia AG Ludwig-Erhard-Straße 18 20459 Hamburg International All rights reserved. No part of this manual or the corresponding program may be reproduced or copied in any form (print, photocopy or other process) without the written permission of CoreMedia AG. Germany Alle Rechte vorbehalten. CoreMedia und weitere im Text erwähnte CoreMedia Produkte sowie die entsprechenden Logos sind Marken oder eingetragene Marken der CoreMedia AG in Deutschland. Alle anderen Namen von Produkten sind Marken der jeweiligen Firmen. Das Handbuch bzw. Teile hiervon sowie die dazugehörigen Programme dürfen in keiner Weise (Druck, Fotokopie oder sonstige Verfahren) ohne schriftliche Genehmigung der CoreMedia AG reproduziert oder vervielfältigt werden. Unberührt hiervon bleiben die gesetzlich erlaubten Nutzungsarten nach dem UrhG. Licenses and Trademarks All trademarks acknowledged. 12.Feb 2013 CoreMedia Operations Basics 2 CoreMedia Operations Basics | 1. Introduction ...................................................................... 1 1.1. Audience ................................................................ 2 1.2. Typographic Conventions ........................................... 3 1.3. Change Chapter ....................................................... 4 2. System Requirements .......................................................... 5 2.1. Hardware Requirements ........................................... -

Open Source Acknowledgements
This document acknowledges certain third‐parties whose software is used in Esri products. GENERAL ACKNOWLEDGEMENTS Portions of this work are: Copyright ©2007‐2011 Geodata International Ltd. All rights reserved. Copyright ©1998‐2008 Leica Geospatial Imaging, LLC. All rights reserved. Copyright ©1995‐2003 LizardTech Inc. All rights reserved. MrSID is protected by the U.S. Patent No. 5,710,835. Foreign Patents Pending. Copyright ©1996‐2011 Microsoft Corporation. All rights reserved. Based in part on the work of the Independent JPEG Group. OPEN SOURCE ACKNOWLEDGEMENTS 7‐Zip 7‐Zip © 1999‐2010 Igor Pavlov. Licenses for files are: 1) 7z.dll: GNU LGPL + unRAR restriction 2) All other files: GNU LGPL The GNU LGPL + unRAR restriction means that you must follow both GNU LGPL rules and unRAR restriction rules. Note: You can use 7‐Zip on any computer, including a computer in a commercial organization. You don't need to register or pay for 7‐Zip. GNU LGPL information ‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐ This library is free software; you can redistribute it and/or modify it under the terms of the GNU Lesser General Public License as published by the Free Software Foundation; either version 2.1 of the License, or (at your option) any later version. This library is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU Lesser General Public License for more details. You can receive a copy of the GNU Lesser General Public License from http://www.gnu.org/ See Common Open Source Licenses below for copy of LGPL 2.1 License. -

Apache Geronimo Uncovered a View Through the Eyes of a Websphere Application Server Expert
Apache Geronimo uncovered A view through the eyes of a WebSphere Application Server expert Skill Level: Intermediate Adam Neat ([email protected]) Author Freelance 16 Aug 2005 Discover the Apache Geronimo application server through the eyes of someone who's used IBM WebSphere® Application Server for many years (along with other commercial J2EE application servers). This tutorial explores the ins and outs of Geronimo, comparing its features and capabilities to those of WebSphere Application Server, and provides insight into how to conceptually architect sharing an application between WebSphere Application Server and Geronimo. Section 1. Before you start This tutorial is for you if you: • Use WebSphere Application Server daily and are interested in understanding more about Geronimo. • Want to gain a comparative groundwork understanding of Geronimo and WebSphere Application Server. • Are considering sharing applications between WebSphere Application Server and Geronimo. • Simply want to learn and understand what other technologies are out there (which I often do). Prerequisites Apache Geronimo uncovered © Copyright IBM Corporation 1994, 2008. All rights reserved. Page 1 of 23 developerWorks® ibm.com/developerWorks To get the most out of this tutorial, you should have a basic familiarity with the IBM WebSphere Application Server product family. You should also posses a general understanding of J2EE terminology and technologies and how they apply to the WebSphere Application Server technology stack. System requirements If you'd like to implement the two technologies included in this tutorial, you'll need the following software and components: • IBM WebSphere Application Server. The version I'm using as a base comparison is IBM WebSphere Application Server, Version 6.0. -

Meaningful Method Names
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by NORA - Norwegian Open Research Archives Meaningful Method Names Doctoral dissertation by Einar W. Høst Submitted to the Faculty of Mathematics and Natural Sciences at the University of Oslo in partial fulfillment of the requirements for the degree Philosophiae Doctor in Computer Science November 2010 © Einar W. Høst, 2011 Series of dissertations submitted to the Faculty of Mathematics and Natural Sciences, University of Oslo No. 1044 ISSN 1501-7710 All rights reserved. No part of this publication may be reproduced or transmitted, in any form or by any means, without permission. Cover: Inger Sandved Anfinsen. Printed in Norway: AIT Oslo AS. Produced in co-operation with Unipub. The thesis is produced by Unipub merely in connection with the thesis defence. Kindly direct all inquiries regarding the thesis to the copyright holder or the unit which grants the doctorate. Abstract We build computer programs by creating named abstractions, aggregations of be- haviour that can be invoked by referring to the name alone. Abstractions can be nested, meaning we can construct new, more powerful abstractions that use more primitive abstractions. Thus we can start from tiny blocks of behaviour and build ar- bitrarily complex systems. For this to work, however, the abstractions must be sound — in other words, the names must suit the behaviour they represent. Otherwise our tower of abstractions will collapse. Hence we see the crucial importance of naming in programming. Despite this importance, programmers almost completely lack tools to assist them. The computer treats names as arbitrary, allowing for sloppy and inconsistent naming. -

Third-Party Software Usage and Licenses Version 11.1 • July 2014
Oracle Commerce Guided Search Third-Party Software Usage and Licenses Version 11.1 • July 2014 Contents Copyright and disclaimer..........................................................................................................5 About this guide.........................................................................................................................7 Who should use this guide.........................................................................................................................................7 Conventions used in this guide..................................................................................................................................7 Contacting Oracle Support.........................................................................................................................................7 Chapter 1: Third-Party Software Usage and Licenses.....................................9 Commercial Packages and Terms.............................................................................................................................9 Open Source Packages and Terms.........................................................................................................................10 Libraries....................................................................................................................................................................25 Other Third-party Dependencies..............................................................................................................................28 -

Red Hat Application Server Jonas User Guide
Red Hat Application Server JOnAS User Guide Red Hat Application Server: JOnAS User Guide Copyright © 1999-2004 by ObjectWeb Consortium ObjectWeb Consortium INRIA - ZIRST, 655 avenue de l'Europe Montbonnot 38334 SAINT-ISMIER Cedex FRANCE Additional information copyright © Red Hat, Inc., 2003-2004. 1801 Varsity Drive Raleigh NC 27606-2072 USA Phone: +1 919 754 3700 Phone: 888 733 4281 Fax: +1 919 754 3701 PO Box 13588 Research Triangle Park NC 27709 USA Manual identifier: • PDF: rhel-jonas-EN-3-PDF-RHI (2003-09-24T01:08) • HTML: rhel-jonas-EN-3-HTML-RHI (2003-09-24T01:08) Red Hat is a registered trademark and the Red Hat Shadow Man logo, RPM, and the RPM logo are trademarks of Red Hat, Inc. JOnAS is copyright © ObjectWeb Consortium. The JOnAS logo is copyright © Bruno Bellamy. Tomcat is copyright © The Apache Software Foundation (ASF). IntelTM, PentiumTM, ItaniumTM, and CeleronTM are registered trademarks of Intel Corporation. EJBTM, J2EETM, JCATM, JCEETM, JDBCTM, JDOTM, JMSTM, RMITM, and SunTM, and Sun Microsystems® are registered trademarks of Sun Microsystems, Inc. Linux is a registered trademark of Linus Torvalds. All other trademarks and copyrights referred to are the property of their respective owners. The GPG fingerprint of the [email protected] key is: CA 20 86 86 2B D6 9D FC 65 F6 EC C4 21 91 80 CD DB 42 A6 0E Table of Contents I. Introductory JOnAS Documentation ..........................................................................................vii 1. Java Open Application Server (JOnAS): a J2EE Platform ................................................... 1 1.1. Introduction to Red Hat Application Server .......................................................... 1 1.2. JOnAS Features ..................................................................................................... 2 1.3. JOnAS Architecture.............................................................................................. -

Open Source: Open for Business Open Source: Open for Business for Open Source: Open LEF09/3Cover.Qxd 9/3/04 1:18 PM Page 2
LEF09/3cover.qxd 9/3/04 1:18 PM Page 1 THE LEADING PRESENTS: FORUM EDGE THE LEADING EDGE FORUM PRESENTS: Open Source: Open for Business Open Source: Open for Business LEF09/3cover.qxd 9/3/04 1:18 PM Page 2 CSC’s Leading Edge Forum is a global thought leadership program that examines the technology trends and issues affecting us today and those that will impact us in the future. As part of the CSC Office of Innovation, the LEF explores emerging technologies through sponsored inno- vation and grants programs, applied research, awards for the most innovative client solutions, and alliances with research labs. The LEF examines technology marketplace ABOUT THE LEF DIRECTORS trends and best practices, and stimulates innovation and collaboration among CSC, our clients and our alliance partners. In this ongoing series of reports about technology directions, the LEF looks at the role of innovation in the marketplace both now and in the years to come. By studying technology’s current realities and anticipating its future shape, these reports provide organizations with the necessary balance between tactical decision making and strategic planning. PAUL GUSTAFSON WILLIAM KOFF Director, Leading Edge Forum, and Senior Partner, Vice President, Leading Edge Forum CSC Consulting Group Paul Gustafson is an accomplished technologist and Bill Koff is a leader in CSC’s technology community. proven leader in emerging technologies, applied He chairs the Leading Edge Forum executive committee, research and strategy. As director of the Leading Edge whose members are the chief technologists from each Forum, Paul brings vision and leadership to a portfolio of CSC’s business units. -

A Peek Under the Hood of Apache Geronimo
Colorado Software Summit: October 24 – 29, 2004 © Copyright 2004, Jailey Solutions, LLC Apache Geronimo: A Peek Under the Hood Bruce Snyder Jailey Solutions, LLC Bruce Snyder — Apache Geronimo: A Peek Under the Hood Page 1 Colorado Software Summit: October 24 – 29, 2004 © Copyright 2004, Jailey Solutions, LLC What Is Apache Geronimo? It is Not… It is… Yet another lightweight Designed for long container running servers Yet another web Designed to tolerate framework partial component Yet another AOP failures framework System oriented An MVC framework services Bruce Snyder — Apache Geronimo: A Peek Under the Hood Page 2 Colorado Software Summit: October 24 – 29, 2004 © Copyright 2004, Jailey Solutions, LLC From the Ground on Down Open Source Enterprise Infrastructure Highly modular architecture Initial manifestation as a J2EE Server Other possible configurations ¾Native Spring Integration ¾Bi-directional PicoContainer Integration ¾Native Portlet Integration ¾Native Web Services Integration ¾Deployment Chaining ¾and many more … Bruce Snyder — Apache Geronimo: A Peek Under the Hood Page 3 Colorado Software Summit: October 24 – 29, 2004 © Copyright 2004, Jailey Solutions, LLC Geronimo Kernel Fundamental Core ¾Small memory consumption ~150KB code ¾Component Configuration ¾Component Registration ¾Integrated Repository ¾Lifecycle Control ¾Dependency Manager Components are called GBeans ¾Simple object, plus some metadata Bruce Snyder — Apache Geronimo: A Peek Under the Hood Page 4 Colorado Software Summit: October 24 – 29, 2004 © Copyright -

Esri Third-Party Software Acknowledgements
Esri Third-party Software Acknowledgements This document acknowledges certain third‐parties whose software may be used in Esri products. GENERAL ACKNOWLEDGEMENTS Portions of this work are: Copyright ©2007-2011 Geodata International Ltd. All rights reserved. Copyright ©1998-2008 Leica Geospatial Imaging, LLC. All rights reserved. Copyright ©1995-2003 LizardTech Inc. All rights reserved. MrSID is protected by the U.S. Patent No. 5,710,835. Foreign Patents Pending. Copyright ©1996-2011 Microsoft Corporation. All rights reserved. Based in part on the work of the Independent JPEG Group. Based in part on Dr. Cynthia A. Brewer’s research on color schemes and ColorBrewer work at The Pennsylvania State University. Copyright © 2013 e-on software. Plants by e-on software Plant Factory - www.e-onsoftware.com OPEN SOURCE ACKNOWLEDGEMENTS 7‐Zip 7-Zip © 1999-2010 Igor Pavlov. Licenses for files are: 1) 7z.dll: GNU LGPL + unRAR restriction 2) All other files: GNU LGPL The GNU LGPL + unRAR restriction means that you must follow both GNU LGPL rules and unRAR restriction rules. Note: You can use 7-Zip on any computer, including a computer in a commercial organization. You don't need to register or pay for 7-Zip. GNU LGPL information -------------------- This library is free software; you can redistribute it and/or modify it under the terms of the GNU Lesser General Public License as published by the Free Software Foundation; either version 2.1 of the License, or (at your option) any later version. This library is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. -

Jonas 4.9 EE Configuration Guide
JOnAS 4.9 EE Configuration guide Guide for configuring one or a group of servers JOnAS Team (Philippe Coq, Adriana Danes, Sava# Ali Tokmen) - January 2008 - Copyright © ObjectWeb 2007 Table of Contents 1. Introduction ............................................................................................................. 1 1.1. configuring JOnAS ......................................................................................... 1 1.2. Terminology .................................................................................................. 1 1.2.1. Server or JOnAS instance ......................................................................1 1.2.2. Service ............................................................................................... 1 1.2.3. Container ............................................................................................1 1.2.4. Domain .............................................................................................. 1 1.2.5. Master server ...................................................................................... 2 1.2.6. Cluster ............................................................................................... 2 2. Configuring a JOnAS instance .................................................................................... 3 2.1. Configuring JOnAS Environment : JONAS_BASE ............................................... 3 2.1.1. JONAS_BASE structure ........................................................................3 2.1.2. JONAS_BASE