Pro Apache Geronimo
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Testing and Deploying IBM Rational HATS® Applications on Apache Geronimo Server
Testing and Deploying IBM Rational HATS® 8.5 Applications on Apache Geronimo Server 3.1 Royal Cyber Inc. Modernized e-business solutions Testing and Deploying IBM Rational HATS® Applications on Apache Geronimo Server Overview This white paper explains how to run, test and deploy IBM Host Access Transformation Service® (HATS) web application on Apache Geronimo Application server. Part 1 - Introduction In the 'Introduction' part the overview of the White Paper is provided. Basic introduction to the IBM Host Access Transformation Service (HATS) and Apache Geronimo Server are provided in this part. Part 2 - Deploying and Installing Apache Geronimo Server In the 'Deploying and Installing Geronimo Server' part, the entire process of deploying the Geronimo Server is explained. Along with that using IBM HATS projects in the Geronimo Server are also explained Part 3 - Benefits In the 'Benefits' part, the overall benefits of the combination IBM HATS-Apache Geronimo Server are discussed. Testing and Deploying IBM Rational HATS® Applications on Apache Geronimo Server PART 1- INTRODUCTION Application server is a very important component in the overall scheme of the web systems as it provides platform for launching or executing applications. It manages all the involved resources like Hardware, OS, Network, etc. It is not just mere hosting of the application, an application server acts as a stage for the deployment and development of Enterprise JavaBeans (EJBs), Web services, etc. In short, Application server interacts between the front end (end users) and system resources at backend. There are various Application servers available in market both paid and unpaid. However, for working with IBM HATS, Apache's Geronimo server is one of the top Application server choices. -

Mobile Server Deployment and Configuration Guide Content
CUSTOMER SAP BusinessObjects Mobile Document Version: 4.2 SP6 – 2017-12-15 Mobile Server Deployment and Configuration Guide Content 1 Document History..............................................................5 2 Target Audience............................................................... 6 3 Introducing the SAP BusinessObjects Mobile Solution.................................. 7 3.1 Solution Overview...............................................................7 SAP BusinessObjects Mobile Client................................................8 SAP BusinessObjects Mobile Server................................................8 SAP BusinessObjects Business Intelligence (BI) Platform.................................9 4 Deploying the SAP BusinessObjects Mobile Server Package.............................10 4.1 Pre-Installation Checklist..........................................................11 4.2 Deploying Server Package using WDeploy..............................................12 4.3 Configuring Your Web application Server.............................................. 13 SAP NetWeaver Web Application Server ............................................13 WebSphere Application Server ...................................................14 WebLogic Web Application Server.................................................14 JBoss Web Application Server................................................... 15 4.4 Auto-Deployment of Mobile Server.................................................. 15 4.5 Deploying SAP Lumira Server on Unsupported -

California State University, Northridge the Design And
CALIFORNIA STATE UNIVERSITY, NORTHRIDGE THE DESIGN AND IMPLEMENTATION OF A SMALL TO MEDIUM RESTAURANT BUSINESS WEB APPLICATION A graduate project submitted in partial fulfillment of the requirements for the degree of Master of Science in Computer Science By Edward Gerhardstein May 2011 The graduate project of Edward Gerhardstein is approved: John Noga , Ph.D. Date Robert McIlhenny , Ph.D. Date Jeff Wiegley , Ph.D., Chair Date California State University, Northridge ii Table of Contents Signature page ii Abstract vi 1 Overview of Pizza Application 1 2 Open Source Licenses Servers 2 2.1 Open Source License Definition . .2 2.2 Ubuntu . .2 2.3 Apache Tomcat . .2 2.4 MySQL . .4 3 Selected Concepts and Terminologies 6 3.1 Model-View-Controller (MVC) . .6 3.2 JavaScript . .7 3.3 Ajax . .7 3.4 XML . .7 3.5 DTD . .7 3.6 XML Schema . .7 3.7 CSS . .8 4 J2EE Concepts 9 4.1 J2EE Overview . .9 4.2 JavaBean . .9 4.3 Enterprise JavaBeans (EJB) . .9 4.4 Other J2EE APIs and Technologies . .9 4.5 Servlets . 10 4.6 JavaServer Pages (JSP) . 11 4.6.1 Scriptlet . 11 5 Apache Struts Framework 13 5.1 Apache Struts Overview . 13 5.2 ActionServlet . 13 5.3 Struts Config . 13 6 Pizza Application Overview 15 6.1 Design Layout . 15 6.2 Workflow . 15 6.3 JSP Page formats - Index.jsp/Templates . 17 6.4 JSP Page Divisions . 18 7 ClockIn/Clockout and Logon Functionality 21 7.1 ClockIn/Clockout Functionality . 21 iii 7.2 Logon Functionality . 21 8 Administrator Functionality 24 8.1 Administrator Functionality Description . -

Talend Open Studio for Big Data Release Notes
Talend Open Studio for Big Data Release Notes 6.0.0 Talend Open Studio for Big Data Adapted for v6.0.0. Supersedes previous releases. Publication date July 2, 2015 Copyleft This documentation is provided under the terms of the Creative Commons Public License (CCPL). For more information about what you can and cannot do with this documentation in accordance with the CCPL, please read: http://creativecommons.org/licenses/by-nc-sa/2.0/ Notices Talend is a trademark of Talend, Inc. All brands, product names, company names, trademarks and service marks are the properties of their respective owners. License Agreement The software described in this documentation is licensed under the Apache License, Version 2.0 (the "License"); you may not use this software except in compliance with the License. You may obtain a copy of the License at http://www.apache.org/licenses/LICENSE-2.0.html. Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. This product includes software developed at AOP Alliance (Java/J2EE AOP standards), ASM, Amazon, AntlR, Apache ActiveMQ, Apache Ant, Apache Avro, Apache Axiom, Apache Axis, Apache Axis 2, Apache Batik, Apache CXF, Apache Cassandra, Apache Chemistry, Apache Common Http Client, Apache Common Http Core, Apache Commons, Apache Commons Bcel, Apache Commons JxPath, Apache -

Apache Harmony Project Tim Ellison Geir Magnusson Jr
The Apache Harmony Project Tim Ellison Geir Magnusson Jr. Apache Harmony Project http://harmony.apache.org TS-7820 2007 JavaOneSM Conference | Session TS-7820 | Goal of This Talk In the next 45 minutes you will... Learn about the motivations, current status, and future plans of the Apache Harmony project 2007 JavaOneSM Conference | Session TS-7820 | 2 Agenda Project History Development Model Modularity VM Interface How Are We Doing? Relevance in the Age of OpenJDK Summary 2007 JavaOneSM Conference | Session TS-7820 | 3 Agenda Project History Development Model Modularity VM Interface How Are We Doing? Relevance in the Age of OpenJDK Summary 2007 JavaOneSM Conference | Session TS-7820 | 4 Apache Harmony In the Beginning May 2005—founded in the Apache Incubator Primary Goals 1. Compatible, independent implementation of Java™ Platform, Standard Edition (Java SE platform) under the Apache License 2. Community-developed, modular architecture allowing sharing and independent innovation 3. Protect IP rights of ecosystem 2007 JavaOneSM Conference | Session TS-7820 | 5 Apache Harmony Early history: 2005 Broad community discussion • Technical issues • Legal and IP issues • Project governance issues Goal: Consolidation and Consensus 2007 JavaOneSM Conference | Session TS-7820 | 6 Early History Early history: 2005/2006 Initial Code Contributions • Three Virtual machines ● JCHEVM, BootVM, DRLVM • Class Libraries ● Core classes, VM interface, test cases ● Security, beans, regex, Swing, AWT ● RMI and math 2007 JavaOneSM Conference | Session TS-7820 | -

Open Source Software Licenses, Notices, and Information
Intergraph InPursuit® WebRMS 03.06.1909 Open Source Software Licenses, Notices, and Information This information is provided for Intergraph InPursuit® WebRMS, a software program of Intergraph® Corporation D/B/A Hexagon Safety & Infrastructure® (“Hexagon”). Source Code Access Intergraph InPursuit WebRMS may include components licensed pursuant to open source software licenses with an obligation to offer the recipient source code. Please see below the list of such components and the information needed to access the source code repository for each. In the event the source code is inaccessible using the information below, please email [email protected]. Component, version Link to download repository Hibernate ORM https://github.com/hibernate/hibernate-orm/releases/tag/3.6.10.Final 3.6.10.Final javassist 3.12.0.GA https://github.com/jboss-javassist/javassist/releases/tag/rel_3_12_0_ga wsdl4j 1.6.1 https://sourceforge.net/projects/wsdl4j/files/WSDL4J/1.6.1/ aspectj 1.8.4 http://git.eclipse.org/c/aspectj/org.aspectj.git/tag/?h=V1_8_4 displaytag 1.2.9 https://github.com/hexagonSI-RMS/displaytag-hexagon Open Source Software Components Intergraph InPursuit WebRMS may include the open source software components identified below. This document provides the notices and information regarding any such open source software for informational purposes only. Please see the product license agreement for Intergraph InPursuit WebRMS to determine the terms and conditions that apply to the open source software. Hexagon reserves all other rights. Component, version URL Copyright License link ActiveMQ KahaDB, version http://activemq.apache.org/kahadb.html © 2005-2012 Apache Software Foundation License 1 5.5.1 ActiveMQ, version 5.5.1 http://activemq.apache.org/ © 2005-2012 Apache Software Foundation License 1 Activiti, version 5.14.0 https://www.activiti.org/ © 2010-2016 Alfresco Software, Ltd. -

Getting Started with Apache Struts 2 , with Netbeans 6.1
Getting started with Apache Struts 2 , with Netbeans 6.1 There are plenty of guides that tell you how to start with struts 2, but most of them are incomplete or don’t work. This guide even makes sure you have IDE JavaDoc support for struts 2 libraries. (Press Ctrl- Space to get details about methods and classes in struts 2 libraries) Download Struts 2 here : http://struts.apache.org/download.cgi Download the Full Distro, so that we get all libraries and docs. (docs are important if u want to have IDE support help and tooltips and syntax) • Full Distribution: o struts-2.0.11.2-all.zip (91mb) [ PGP ] [ MD5 ] As of this writing , this is the latest version of Struts. Download Netbeans 6.1 here : http://www.netbeans.org/downloads/ or here : http://dlc.sun.com.edgesuite.net/netbeans/6.1/final/ Download the full bundle (under the All column) size about 220 MB Choose a folder for all your JAVA material that has NO SPACES in its path. Like C:\Java “C:\Program Files” has a space, so it has some issues with the Sun Application Platform, which you might need after development. Other downloads : [These are not necessary now, but just download them while working on this guide] Eclipse for JavaEE Dev : http://www.eclipse.org/downloads/ Eclipse IDE for Java EE Developers (163 MB) Java Application Platform : http://java.sun.com/javaee/downloads/index.jsp App Platform + JDK† Java Standard Edition [SE] : http://java.sun.com/javase/downloads/index.jsp JDK 6 Update 7 Install as follows : This is how a pro I knew advised to set a comp up for Java EE Dev. -

Java Management Extension Didier DONSEZ
http://www-adele.imag.fr/users/Didier.Donsez/cours JMX Java Management eXtension Didier DONSEZ Université Joseph Fourier –Grenoble 1 PolyTech’Grenoble LIG/ADELE [email protected], [email protected] 19/02/2008 Outline Motivation Architecture MBeans Standard, Dynamic Monitor Notification Utilities Remote Management Connector & Adaptor API Tools JSR Bibliography (c)Donsez,JMX Didier 2003-2008, 2 19/02/2008 Under Translation Motivations fr->en Service d’administration d’applications Ressources matérielles accessibles depuis une JVM Ressources logiciels s’exécutant sur une JVM S’inspire de SNMP Instrumentations des ressources au moyen de composants appelés MBean (Manageable Bean) Adopté initialement par J2EE et maintenant J2SE 1.5 (c)Donsez,JMX Didier 2003-2008, 3 19/02/2008 Usage Get and set applications configuration (Pull) Collect statistics (Pull) Performance Ressources usage Problems Notify events (Push) Faults State changes (c)Donsez,JMX Didier 2003-2008, 4 19/02/2008 JMX 3-Level Architecture JMX Web SNMP Specific Browser Console Console Console JConsole HTML/HTTP SNMP Remote RMI HTTP/SOAP Management Level C C’ A A’ Agent MBeanServer Level Probe MBean1 MBean2 MXBean3 (c)Donsez,JMX Didier 2003-2008, Level 5 19/02/2008 JMX 3-Level Architecture JMX Web SNMP Specific Browser Console Console Console JConsole HTML/HTTP SNMP Remote RMI HTTP/SOAP Management Level Connector Connector’ Adaptor Adaptor’ Agent MBeanServer Level Standard Dynamic Probe MXBean3 (c)Donsez,JMX Didier 2003-2008, Level MBean1 MBean2 For Wikipedia 6 19/02/2008 JMX 3-Level Architecture Probe level JMX Web SNMP Specific Browser Console Console Console Resources,JConsole such as applications, devices, or services, are instrumentedHTML/HTTP using JavaSNMP objects called Managed Beans (MBeans). -

IBM Websphere Application Server Community Edition V3.0 Helps Streamline the Creation of Osgi and Java Enterprise Edition 6 Applications
IBM United States Software Announcement 211-083, dated September 27, 2011 IBM WebSphere Application Server Community Edition V3.0 helps streamline the creation of OSGi and Java Enterprise Edition 6 applications Table of contents 1 Overview 6 Technical information 2 Key prerequisites 8 Ordering information 2 Planned availability date 9 Services 3 Description 9 Order now 6 Product positioning At a glance With WebSphere® Application Server Community Edition V3.0: • Developers can select just the components they need for optimum productivity (using OSGi and a component assembly model). • Developers can get JavaTM Enterprise Edition (Java EE) 6 applications started quickly for no charge. • System administrators are given more deployment and management options. • Organizations can take advantage of world-class, IBM® support options under a socket-based pricing model that can help reduce the cost burden in larger configurations. • You have access to a comprehensive and proven portfolio of middleware products from the WebSphere family. Overview WebSphere Application Server Community Edition V3.0 is the IBM open source- based application server that provides: • Java Enterprise Edition (Java EE) 6 support • An enterprise OSGi application programming model • Java Standard Edition (Java SE) 6 support Version 3 is built on Apache Geronimo and integrated with best-of-breed, open- source technology such as Apache Tomcat, Eclipse Equinox OSGi Framework, Apache Aries, Apache OpenEJB, Apache OpenJPA, Apache OpenWebBeans, and Apache MyFaces. Eclipse-based -
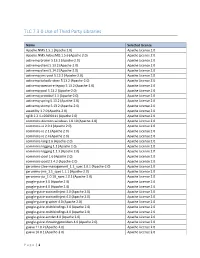
TLC 7.3.0 Use of Third Party Libraries
TLC 7.3.0 Use of Third Party Libraries Name Selected License Apache.NMS 1.5.1 (Apache 2.0) Apache License 2.0 Apache.NMS.ActiveMQ 1.5.6 (Apache 2.0) Apache License 2.0 activemq-broker 5.13.2 (Apache-2.0) Apache License 2.0 activemq-client 5.13.2 (Apache-2.0) Apache License 2.0 activemq-client 5.14.2 (Apache-2.0) Apache License 2.0 activemq-jms-pool 5.13.2 (Apache-2.0) Apache License 2.0 activemq-kahadb-store 5.13.2 (Apache-2.0) Apache License 2.0 activemq-openwire-legacy 5.13.2 (Apache-2.0) Apache License 2.0 activemq-pool 5.13.2 (Apache-2.0) Apache License 2.0 activemq-protobuf 1.1 (Apache-2.0) Apache License 2.0 activemq-spring 5.13.2 (Apache-2.0) Apache License 2.0 activemq-stomp 5.13.2 (Apache-2.0) Apache License 2.0 awaitility 1.7.0 (Apache-2.0) Apache License 2.0 cglib 2.2.1-v20090111 (Apache 2.0) Apache License 2.0 commons-daemon-windows 1.0.10 (Apache-2.0) Apache License 2.0 commons-io 2.0.1 (Apache 2.0) Apache License 2.0 commons-io 2.1 (Apache 2.0) Apache License 2.0 commons-io 2.4 (Apache 2.0) Apache License 2.0 commons-lang 2.6 (Apache-2.0) Apache License 2.0 commons-logging 1.1 (Apache 2.0) Apache License 2.0 commons-logging 1.1.3 (Apache 2.0) Apache License 2.0 commons-pool 1.6 (Apache 2.0) Apache License 2.0 commons-pool2 2.4.2 (Apache-2.0) Apache License 2.0 geronimo-j2ee-management_1.1_spec 1.0.1 (Apache-2.0) Apache License 2.0 geronimo-jms_1.1_spec 1.1.1 (Apache-2.0) Apache License 2.0 geronimo-jta_1.0.1B_spec 1.0.1 (Apache-2.0) Apache License 2.0 google-guice 3.0 (Apache 2.0) Apache License 2.0 google-guice 4.0 (Apache -

Coremedia Operations Basics Coremedia Operations Basics |
CoreMedia 6 //Version 5.3.27 CoreMedia Operations Basics CoreMedia Operations Basics | CoreMedia Operations Basics Copyright CoreMedia AG © 2012 CoreMedia AG Ludwig-Erhard-Straße 18 20459 Hamburg International All rights reserved. No part of this manual or the corresponding program may be reproduced or copied in any form (print, photocopy or other process) without the written permission of CoreMedia AG. Germany Alle Rechte vorbehalten. CoreMedia und weitere im Text erwähnte CoreMedia Produkte sowie die entsprechenden Logos sind Marken oder eingetragene Marken der CoreMedia AG in Deutschland. Alle anderen Namen von Produkten sind Marken der jeweiligen Firmen. Das Handbuch bzw. Teile hiervon sowie die dazugehörigen Programme dürfen in keiner Weise (Druck, Fotokopie oder sonstige Verfahren) ohne schriftliche Genehmigung der CoreMedia AG reproduziert oder vervielfältigt werden. Unberührt hiervon bleiben die gesetzlich erlaubten Nutzungsarten nach dem UrhG. Licenses and Trademarks All trademarks acknowledged. 12.Feb 2013 CoreMedia Operations Basics 2 CoreMedia Operations Basics | 1. Introduction ...................................................................... 1 1.1. Audience ................................................................ 2 1.2. Typographic Conventions ........................................... 3 1.3. Change Chapter ....................................................... 4 2. System Requirements .......................................................... 5 2.1. Hardware Requirements ........................................... -

HDP 3.1.4 Release Notes Date of Publish: 2019-08-26
Release Notes 3 HDP 3.1.4 Release Notes Date of Publish: 2019-08-26 https://docs.hortonworks.com Release Notes | Contents | ii Contents HDP 3.1.4 Release Notes..........................................................................................4 Component Versions.................................................................................................4 Descriptions of New Features..................................................................................5 Deprecation Notices.................................................................................................. 6 Terminology.......................................................................................................................................................... 6 Removed Components and Product Capabilities.................................................................................................6 Testing Unsupported Features................................................................................ 6 Descriptions of the Latest Technical Preview Features.......................................................................................7 Upgrading to HDP 3.1.4...........................................................................................7 Behavioral Changes.................................................................................................. 7 Apache Patch Information.....................................................................................11 Accumulo...........................................................................................................................................................