Proof of Assets in the Diem Blockchain
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Virtual Currencies and Terrorist Financing : Assessing the Risks And
DIRECTORATE GENERAL FOR INTERNAL POLICIES POLICY DEPARTMENT FOR CITIZENS' RIGHTS AND CONSTITUTIONAL AFFAIRS COUNTER-TERRORISM Virtual currencies and terrorist financing: assessing the risks and evaluating responses STUDY Abstract This study, commissioned by the European Parliament’s Policy Department for Citizens’ Rights and Constitutional Affairs at the request of the TERR Committee, explores the terrorist financing (TF) risks of virtual currencies (VCs), including cryptocurrencies such as Bitcoin. It describes the features of VCs that present TF risks, and reviews the open source literature on terrorist use of virtual currencies to understand the current state and likely future manifestation of the risk. It then reviews the regulatory and law enforcement response in the EU and beyond, assessing the effectiveness of measures taken to date. Finally, it provides recommendations for EU policymakers and other relevant stakeholders for ensuring the TF risks of VCs are adequately mitigated. PE 604.970 EN ABOUT THE PUBLICATION This research paper was requested by the European Parliament's Special Committee on Terrorism and was commissioned, overseen and published by the Policy Department for Citizens’ Rights and Constitutional Affairs. Policy Departments provide independent expertise, both in-house and externally, to support European Parliament committees and other parliamentary bodies in shaping legislation and exercising democratic scrutiny over EU external and internal policies. To contact the Policy Department for Citizens’ Rights and Constitutional Affairs or to subscribe to its newsletter please write to: [email protected] RESPONSIBLE RESEARCH ADMINISTRATOR Kristiina MILT Policy Department for Citizens' Rights and Constitutional Affairs European Parliament B-1047 Brussels E-mail: [email protected] AUTHORS Tom KEATINGE, Director of the Centre for Financial Crime and Security Studies, Royal United Services Institute (coordinator) David CARLISLE, Centre for Financial Crime and Security Studies, Royal United Services Institute, etc. -

On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models
mathematics Article On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models Jong-Min Kim 1 , Seong-Tae Kim 2 and Sangjin Kim 3,* 1 Statistics Discipline, University of Minnesota at Morris, Morris, MN 56267, USA; [email protected] 2 Department of Mathematics, North Carolina A&T State University, Greensboro, NC 27411, USA; [email protected] 3 Department of Management and Information Systems, Dong-A University, Busan 49236, Korea * Correspondence: [email protected] Received: 15 September 2020; Accepted: 20 October 2020; Published: 23 October 2020 Abstract: This paper examines the relationship of the leading financial assets, Bitcoin, Gold, and S&P 500 with GARCH-Dynamic Conditional Correlation (DCC), Nonlinear Asymmetric GARCH DCC (NA-DCC), Gaussian copula-based GARCH-DCC (GC-DCC), and Gaussian copula-based Nonlinear Asymmetric-DCC (GCNA-DCC). Under the high volatility financial situation such as the COVID-19 pandemic occurrence, there exist a computation difficulty to use the traditional DCC method to the selected cryptocurrencies. To solve this limitation, GC-DCC and GCNA-DCC are applied to investigate the time-varying relationship among Bitcoin, Gold, and S&P 500. In terms of log-likelihood, we show that GC-DCC and GCNA-DCC are better models than DCC and NA-DCC to show relationship of Bitcoin with Gold and S&P 500. We also consider the relationships among time-varying conditional correlation with Bitcoin volatility, and S&P 500 volatility by a Gaussian Copula Marginal Regression (GCMR) model. The empirical findings show that S&P 500 and Gold price are statistically significant to Bitcoin in terms of log-return and volatility. -

Banking on Bitcoin: BTC As Collateral
Banking on Bitcoin: BTC as Collateral Arcane Research Bitstamp Arcane Research is a part of Arcane Crypto, Bitstamp is the world’s longest-running bringing data-driven analysis and research cryptocurrency exchange, supporting to the cryptocurrency space. After launch in investors, traders and leading financial August 2019, Arcane Research has become institutions since 2011. With a proven track a trusted brand, helping clients strengthen record, cutting-edge market infrastructure their credibility and visibility through and dedication to personal service with a research reports and analysis. In addition, human touch, Bitstamp’s secure and reliable we regularly publish reports, weekly market trading venue is trusted by over four million updates and articles to educate and share customers worldwide. Whether it’s through insights. their intuitive web platform and mobile app or industry-leading APIs, Bitstamp is where crypto enters the world of finance. For more information, visit www.bitstamp.net 2 Banking on Bitcoin: BTC as Collateral Banking on bitcoin The case for bitcoin as collateral The value of the global market for collateral is estimated to be close to $20 trillion in assets. Government bonds and cash-based securities alike are currently the most important parts of a well- functioning collateral market. However, in that, there is a growing weakness as rehypothecation creates a systemic risk in the financial system as a whole. The increasing reuse of collateral makes these assets far from risk-free and shows the potential instability of the financial markets and that it is more fragile than many would like to admit. Bitcoin could become an important part of the solution and challenge the dominating collateral assets in the future. -

Vulnerability of Blockchain Technologies to Quantum Attacks
Vulnerability of Blockchain Technologies to Quantum Attacks Joseph J. Kearneya, Carlos A. Perez-Delgado a,∗ aSchool of Computing, University of Kent, Canterbury, Kent CT2 7NF United Kingdom Abstract Quantum computation represents a threat to many cryptographic protocols in operation today. It has been estimated that by 2035, there will exist a quantum computer capable of breaking the vital cryptographic scheme RSA2048. Blockchain technologies rely on cryptographic protocols for many of their essential sub- routines. Some of these protocols, but not all, are open to quantum attacks. Here we analyze the major blockchain-based cryptocurrencies deployed today—including Bitcoin, Ethereum, Litecoin and ZCash, and determine their risk exposure to quantum attacks. We finish with a comparative analysis of the studied cryptocurrencies and their underlying blockchain technologies and their relative levels of vulnerability to quantum attacks. Introduction exist to allow the legitimate owner to recover this account. Blockchain systems are unlike other cryptosys- tems in that they are not just meant to protect an By contrast, in a blockchain system, there is no information asset. A blockchain is a ledger, and as central authority to manage users’ access keys. The such it is the asset. owner of a resource is by definition the one hold- A blockchain is secured through the use of cryp- ing the private encryption keys. There are no of- tographic techniques. Notably, asymmetric encryp- fline backups. The blockchain, an always online tion schemes such as RSA or Elliptic Curve (EC) cryptographic system, is considered the resource— cryptography are used to generate private/public or at least the authoritative description of it. -
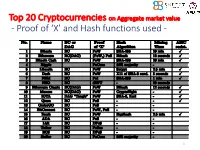
Proof of 'X' and Hash Functions Used
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5. -

Is Bitcoin Rat Poison? Cryptocurrency, Crime, and Counterfeiting (Ccc)
IS BITCOIN RAT POISON? CRYPTOCURRENCY, CRIME, AND COUNTERFEITING (CCC) Eric Engle1 1 JD St. Louis, DEA Paris II, DEA Paris X, LL.M.Eur., Dr.Jur. Bremen, LL.M. Humboldt. Eric.Engle @ yahoo.com, http://mindworks.altervista.org. Dr. Engle beleives James Orlin Grabbe was the author of bitcoin, and is certain that Grabbe issued the first digital currency and is the intellectual wellspring of cryptocurrency. Kalliste! Copyright © 2016 Journal of High Technology Law and Eric Engle. All Rights Re- served. ISSN 1536-7983. 2016] IS BITCOIN RAT POISON? 341 Introduction Distributed cryptographic currency, most famously exempli- fied by bitcoin,2 is anonymous3 on-line currency backed by no state.4 The currency is generated by computation (“mining”), purchase, or trade.5 It is stored and tracked using peer-to-peer technology,6 which 2 See Jonathan B. Turpin, Note, Bitcoin: The Economic Case for A Global, Virtual Currency Operating in an Unexplored Legal Framework, 21 IND. J. GLOBAL LEGAL STUD. 335, 337-38 (2014) (describing how Bitcoin is a virtual currency). Bitcoin is supported by a distributed network of users and relies on advanced cryptography techniques to ensure its stability and reliability. A Bitcoin is simply a chain of digital signatures (i.e., a string of numbers) saved in a “wallet” file. This chain of signa- tures contains the necessary history of the specific Bitcoin so that the system may verify its legitimacy and transfer its ownership from one user to another upon request. A user's wallet consists of the Bitcoins it contains, a public key, and a private key. -

Short Selling Attack: a Self-Destructive but Profitable 51% Attack on Pos Blockchains
Short Selling Attack: A Self-Destructive But Profitable 51% Attack On PoS Blockchains Suhyeon Lee and Seungjoo Kim CIST (Center for Information Security Technologies), Korea University, Korea Abstract—There have been several 51% attacks on Proof-of- With a PoS, the attacker needs to obtain 51% of the Work (PoW) blockchains recently, including Verge and Game- cryptocurrency to carry out a 51% attack. But unlike PoW, Credits, but the most noteworthy has been the attack that saw attacker in a PoS system is highly discouraged from launching hackers make off with up to $18 million after a successful double spend was executed on the Bitcoin Gold network. For this reason, 51% attack because he would have to risk of depreciation the Proof-of-Stake (PoS) algorithm, which already has advantages of his entire stake amount to do so. In comparison, bad of energy efficiency and throughput, is attracting attention as an actor in a PoW system will not lose their expensive alternative to the PoW algorithm. With a PoS, the attacker needs mining equipment if he launch a 51% attack. Moreover, to obtain 51% of the cryptocurrency to carry out a 51% attack. even if a 51% attack succeeds, the value of PoS-based But unlike PoW, attacker in a PoS system is highly discouraged from launching 51% attack because he would have to risk losing cryptocurrency will fall, and the attacker with the most stake his entire stake amount to do so. Moreover, even if a 51% attack will eventually lose the most. For these reasons, those who succeeds, the value of PoS-based cryptocurrency will fall, and attempt to attack 51% of the PoS blockchain will not be the attacker with the most stake will eventually lose the most. -

Introducing Uni, Yfi and Snx at Bitstamp with Zero Fees Until the End of July!
2021. 4. 27. News and updates – Bitstamp NEW RESEARCH: The state of Bitcoin as collateral. - Read more × News INTRODUCING UNI, YFI AND SNX AT BITSTAMP WITH ZERO FEES UNTIL THE END OF JULY! 26 APR 2021 We are further expanding our support for the growing DeFi space with another trio of new listings. The new assets each cover a unique use case and should be an exciting addition to the portfolios of both DeFi enthusiasts as well as rst-time entrants to the space. We are listing the following cryptocurrencies: ● Uniswap (UNI) – an automated trading and liquidity protocol that enables decentralized trading of tokens through the Uniswap DEX ● Yearn.nance (YFI) – a DeFi service created to help non-technical users maximize returns from yield farming ● Synthetix (SNX) – a DeFi protocol for creating on-chain derivatives (called synths) based on both crypto and non-crypto assets All of these cryptocurrencies will trade with zero fees until the end of July! Please note that for the time being, these assets will not be available to our US customers. Listing schedule: 1. Transfer-only mode: Deposits and withdrawals open but trading is not enabled yet. UNI, YFI, SNX: Monday, 3 May 2. Post-only mode: You will be able to place and cancel limit orders, but they will not be matched. Therefore, no orders will actually be completed during this stage. https://www.bitstamp.net/news/ 1/19 2021. 4. 27. News and updates – Bitstamp UNI: Tuesday, 4 May, at 8:00 AM UTC YFI: Wednesday, 5 May, at 8:00 AM UTC SNX: Thursday, 6 May,NEW at 8:00RESEARCH: AM UTC The state of Bitcoin as collateral. -

Blockchain & Cryptocurrency Regulation
Blockchain & Cryptocurrency Regulation Third Edition Contributing Editor: Josias N. Dewey Global Legal Insights Blockchain & Cryptocurrency Regulation 2021, Third Edition Contributing Editor: Josias N. Dewey Published by Global Legal Group GLOBAL LEGAL INSIGHTS – BLOCKCHAIN & CRYPTOCURRENCY REGULATION 2021, THIRD EDITION Contributing Editor Josias N. Dewey, Holland & Knight LLP Head of Production Suzie Levy Senior Editor Sam Friend Sub Editor Megan Hylton Consulting Group Publisher Rory Smith Chief Media Officer Fraser Allan We are extremely grateful for all contributions to this edition. Special thanks are reserved for Josias N. Dewey of Holland & Knight LLP for all of his assistance. Published by Global Legal Group Ltd. 59 Tanner Street, London SE1 3PL, United Kingdom Tel: +44 207 367 0720 / URL: www.glgroup.co.uk Copyright © 2020 Global Legal Group Ltd. All rights reserved No photocopying ISBN 978-1-83918-077-4 ISSN 2631-2999 This publication is for general information purposes only. It does not purport to provide comprehensive full legal or other advice. Global Legal Group Ltd. and the contributors accept no responsibility for losses that may arise from reliance upon information contained in this publication. This publication is intended to give an indication of legal issues upon which you may need advice. Full legal advice should be taken from a qualified professional when dealing with specific situations. The information contained herein is accurate as of the date of publication. Printed and bound by TJ International, Trecerus Industrial Estate, Padstow, Cornwall, PL28 8RW October 2020 PREFACE nother year has passed and virtual currency and other blockchain-based digital assets continue to attract the attention of policymakers across the globe. -

Blockchain and Cryptocurrency in Africa a Comparative Summary of the Reception and Regulation of Blockchain and Cryptocurrency in Africa
Blockchain and Cryptocurrency in Africa A comparative summary of the reception and regulation of Blockchain and Cryptocurrency in Africa 2018 Baker McKenzie, Johannesburg IMPORTANT DISCLAIMER: The material in this report is of the nature of general comment only. It is not offered as legal advice on any specific issue or matter and should not be taken as such. Readers should refrain from acting on the basis of any discussion contained in this report without obtaining specific legal advice on the particular facts and circumstances at issue. While the authors have made every effort to provide accurate and up-to-date information on laws and policy, these matters are continuously subject to change. Furthermore, the application of these laws depends on the particular facts and circumstances of each situation, and therefore readers should consult their lawyer before taking any action. Information contained herein is as at November 2018. CONTENTS PREFACE ............................................................................................................................................1 GEOGRAPHICAL OVERVIEW ....................................................................................................... 2 COUNTRY PROFILES ..................................................................................................................... 3 1. Botswana ................................................................................................................................................................... 3 2. Ghana .........................................................................................................................................................................4 -

The Bitcoin Trading Ecosystem
ArcaneReport(PrintReady).qxp 21/07/2021 14:43 Page 1 THE INSTITUTIONAL CRYPTO CURRENCY EXCHANGE INSIDE FRONT COVER: BLANK ArcaneReport(PrintReady).qxp 21/07/2021 14:43 Page 3 The Bitcoin Trading Ecosystem Arcane Research LMAX Digital Arcane Research is a part of Arcane Crypto, bringing LMAX Digital is the leading institutional spot data-driven analysis and research to the cryptocurrency exchange, run by the LMAX Group, cryptocurrency space. After launch in August 2019, which also operates several leading FCA regulated Arcane Research has become a trusted brand, trading venues for FX, metals and indices. Based on helping clients strengthen their credibility and proven, proprietary technology from LMAX Group, visibility through research reports and analysis. In LMAX Digital allows global institutions to acquire, addition, we regularly publish reports, weekly market trade and hold the most liquid digital assets, Bitcoin, updates and articles to educate and share insights. Ethereum, Litecoin, Bitcoin Cash and XRP, safely and securely. Arcane Crypto develops and invests in projects, focusing on bitcoin and digital assets. Arcane Trading with all the largest institutions globally, operates a portfolio of businesses, spanning the LMAX Digital is a primary price discovery venue, value chain for digital nance. As a group, Arcane streaming real-time market data to the industry’s deliver services targeting payments, investment, and leading indices and analytics platforms, enhancing trading, in addition to a media and research leg. the quality of market information available to investors and enabling a credible overview of the Arcane has the ambition to become a leading player spot crypto currency market. in the digital assets space by growing the existing businesses, invest in cutting edge projects, and LMAX Digital is regulated by the Gibraltar Financial through acquisitions and consolidation. -

How to Not Get Caught When You Launder Money on Blockchain?
How to Not Get Caught When You Launder Money on Blockchain? Cuneyt G. Akcora1, Sudhanva Purusotham2, Yulia R. Gel2 Mitchell Krawiec-Thayer3, Murat Kantarcioglu2 1University of Manitoba, 2 UT Dallas, 3 Monero Research Lab 65 Chancellor Circle Winnipeg, MB, Canada R3T 2N2 [email protected], fSudhanva.Purushotham, ygl, [email protected], [email protected] Abstract transactions and circumvent existing AI-based money laun- dering techniques. Our insights, however, are intended not to The number of blockchain users has tremendously grown in assist criminals to obfuscate their malicious activities but to recent years. As an unintended consequence, e-crime trans- motivate the AI community for further research in this area actions on blockchains has been on the rise. Consequently, public blockchains have become a hotbed of research for de- of critical societal importance and, as a result, to advance veloping AI tools to detect and trace users and transactions the state of art methodology in the AI-based cryptocurrency that are related to e-crime. money laundering detection. We argue that following a few select strategies can make In the remainder of this paper, we first identify tech- money laundering on blockchain virtually undetectable with niques that can be used by criminals to launder money on most of the currently existing tools and algorithms. As a re- blockchain and then empirically show why these techniques sult, the effective combating of e-crime activities involving would be effective in hiding patterns used by potential AI cryptocurrencies requires the development of novel analytic models. methodology in AI. 2 Related Work 1 Introduction The success of Bitcoin (Nakamoto 2008) has encouraged Cryptocurrencies have emerged as an important rapidly hundreds of similar digital coins (Tschorsch and Scheuer- evolving financial tool that allows for cross-border transac- mann 2016).