470-Historical-Cryptography.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Historical Ciphers • A
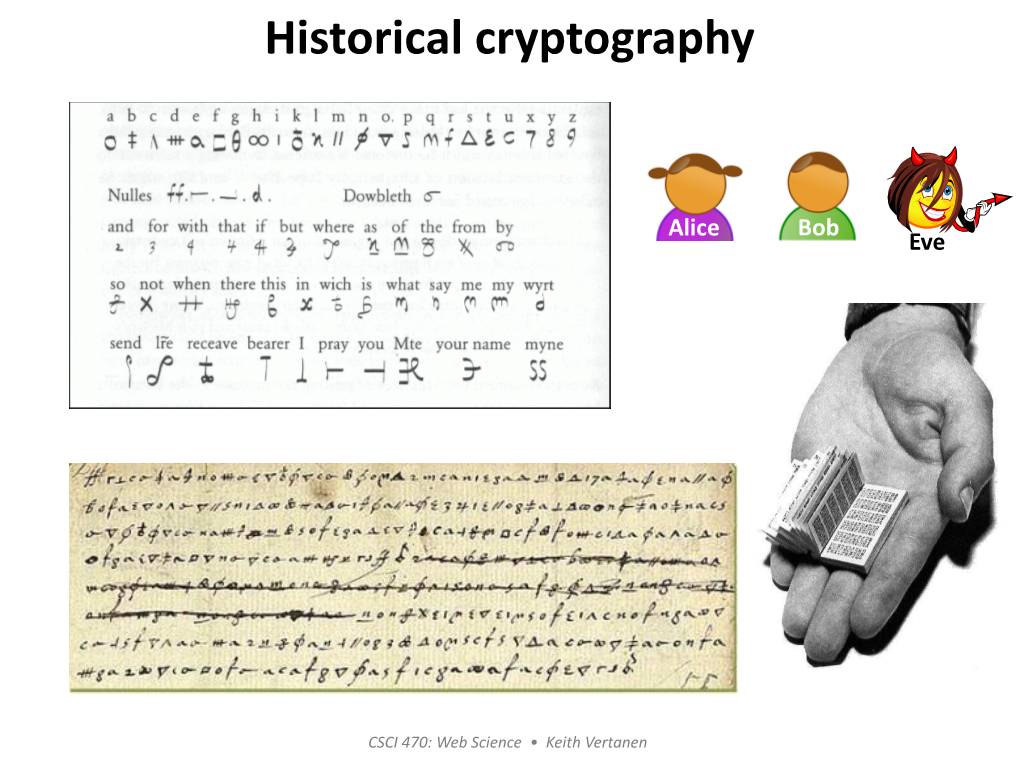
ECE 646 - Lecture 6 Required Reading • W. Stallings, Cryptography and Network Security, Chapter 2, Classical Encryption Techniques Historical Ciphers • A. Menezes et al., Handbook of Applied Cryptography, Chapter 7.3 Classical ciphers and historical development Why (not) to study historical ciphers? Secret Writing AGAINST FOR Steganography Cryptography (hidden messages) (encrypted messages) Not similar to Basic components became modern ciphers a part of modern ciphers Under special circumstances modern ciphers can be Substitution Transposition Long abandoned Ciphers reduced to historical ciphers Transformations (change the order Influence on world events of letters) Codes Substitution The only ciphers you Ciphers can break! (replace words) (replace letters) Selected world events affected by cryptology Mary, Queen of Scots 1586 - trial of Mary Queen of Scots - substitution cipher • Scottish Queen, a cousin of Elisabeth I of England • Forced to flee Scotland by uprising against 1917 - Zimmermann telegram, America enters World War I her and her husband • Treated as a candidate to the throne of England by many British Catholics unhappy about 1939-1945 Battle of England, Battle of Atlantic, D-day - a reign of Elisabeth I, a Protestant ENIGMA machine cipher • Imprisoned by Elisabeth for 19 years • Involved in several plots to assassinate Elisabeth 1944 – world’s first computer, Colossus - • Put on trial for treason by a court of about German Lorenz machine cipher 40 noblemen, including Catholics, after being implicated in the Babington Plot by her own 1950s – operation Venona – breaking ciphers of soviet spies letters sent from prison to her co-conspirators stealing secrets of the U.S. atomic bomb in the encrypted form – one-time pad 1 Mary, Queen of Scots – cont. -

Shift Cipher
Transposition Ciphers - ANSWERS Caesar Shift Cipher Assignment 1 CONTINUE TO ENCIPHER THIS MESSAGE YOU NEED TO REPLACE FRQWLQXH WR HQFLSKHU WKLV PHVVDJH BRX QHHG WR UHSODFH EACH LETTER USING THE CIPHER GRID HDFK OHWWHU XVLQJ WKH FLSKHU JULG A B C D E F G H I J K L M N O P Q R S T U V W X Y Z D E F G H I J K L M N O P Q R S T U V W X Y Z A B C Using the same grid decipher the following – remember to decipher from the lower grid to the upper. Assignment 2 JHQLXV LV RQH SHU FHQW LQVSLUDWLRQ DQG QLQHWB QLQH SHU FHQW SHUVSLUDWLRQ TXRWH IURP WKRPDV HGLVRQ ‘Genius is one per cent inspiration and ninety nine per cent perspiration’ quote from Thomas Edison Shift Cipher Similar to the example above, can you crack the cipher? How much does it shift? To find the Caesar Shift on the computer click on the question mark on the homepage Then select Caesar Shift - Copy the text into the right hand side box and decipher – Try different shift values until the message makes sense. 1 Assignment 3 RCTQCA KIMAIZ AMVB BPM NQZAB SVWEV MVKQXPMZML UMAAIOMA NWZ UQTQBIZG XCZXWAMA PM LQL QB QV I AGABMUIBQK EIG JG APQNBQVO BPM ITXPIJMB NWZEIZL BPZMM XTIKMA BPQA XZWDML ZMTIBQDMTG MIAG BW LMKQXPMZ ZMXTIKQVO MIKP TMBBMZ EQBP WVM BPZMM XTIKMA JIKSEIZLA LQNNMZMVB KIMAIZ APQNBA KQXPMZA MFQAB JG UWDQVO I LQNNMZMVB VCUJMZ WN XTIKMA QN GWCZ MVMUG QVBMZKMXBML GWCZ UMAAIOM QB EIA VWB BWW LQNNQKCTB NWZ BPMU BW LMKQXPMZ A B C D E F G H I J K L M N O P Q R S T U V W X Y Z I J K L M N O P Q R S T U V W X Y Z A B C D E F G H Julius Caesar sent the first known enciphered messages, for military purposes. -

The True Executor of the Execution of Mary, Queen of Scots," Constructing the Past: Vol
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Digital Commons @ Illinois Wesleyan University Constructing the Past Volume 6 | Issue 1 Article 4 2005 The rT ue Executor of the Execution of Mary, Queen of Scots Melissa Koeppen Illinois Wesleyan University Recommended Citation Koeppen, Melissa (2005) "The True Executor of the Execution of Mary, Queen of Scots," Constructing the Past: Vol. 6: Iss. 1, Article 4. Available at: http://digitalcommons.iwu.edu/constructing/vol6/iss1/4 This Article is brought to you for free and open access by the History Department at Digital Commons @ IWU. It has been accepted for inclusion in Constructing the Past by an authorized administrator of Digital Commons @ IWU. For more information, please contact [email protected]. ©Copyright is owned by the author of this document. The rT ue Executor of the Execution of Mary, Queen of Scots Abstract This paper examines the culpability of Elizabeth and her Councillors in the execution of Mary, Queen of Scots, the woman who threatened to take Elizabeth's throne and life away from her. This article is available in Constructing the Past: http://digitalcommons.iwu.edu/constructing/vol6/iss1/4 Constrocting the Post Constrocting the Post The True Executor of the Execution ofMary, Queen of Scots oath signed by thousands of Englishmen.5 It was primarily the work ofWalsingham and By Melissa Koeppen Burghley.6 Both these men saw Mary as the clear cause of Elizabeth's problems.? The Councillors went so far as to condemn Mary and to pledge to refuse to "accept or favor any such This paper examines the culpability ofElizabeth and her Councillors in the execution ofMary, pretended successor, by whom or for whom any such detestable act shall be attempted or Queen ofScots, the woman who threatened to take Elizabeth's throne and life away from her. -

Troubles at Home and Abroad
Troubles at home and abroad Key terms: Elizabeth’s posion was always very vulnerable and her instability was Why was Elizabeth’s excommunicaon a CALVINIST ‐ Protestants who followed the closely ed up with religious disagreements. For some, Elizabeth was an turning point? teachings of John Calvin illegimate HERETIC who had no right to be Queen of England. She man‐ Elizabeth was declared a herec. The bull aged to antagonise both Catholics and Protestants at home. Meanwhile, CHAPLAIN—a clergyman aached to the released Elizabeth’s subjects from allegiance dangerous plots constantly revolved around her Catholic cousin, Mary, private chapel of a prominent person to her—they no longer obeyed her. It en‐ Queen of Scots. Eventually, the momentous decision was taken to have couraged Catholic states, such as France and EPISCOPAL—a Church hierarchy struc‐ Mary executed. In 1588, in the aermath of Mary’s dramac death, the Spain to believe they could wage a holy war tured around bishops. Spanish launched their famous Armada, which threatened to destroy Eliza‐ on England. It encouraged further plots HERETIC—a person who did not follow the beth and England forever. Elizabeth’s posion as Queen was therefore against Elizabeth, centred around Mary official religion of the country. always fragile. Queen of Scots. It also led to more severe HUGUENOT—A French Protestant. They treatment of English Catholics. suffered severe persecuon and many fled Why was Mary Queen of Scots arrival in to England. Key individuals: England so important? JESUIT—Roman Catholic missionary Mary, Queen of Scots –Henry VIIs great– granddaughter, Elizabeth’s It led to the following plots: priests second cousin, Catholic and with a strong claim to the throne. -

The Catholic Plots Early Life 1560 1570 1580 1590 1600
Elizabethan England: Part 1 – Elizabeth’s Court and Parliament Family History Who had power in Elizabethan England? Elizabeth’s Court Marriage The Virgin Queen Why did Parliament pressure Elizabeth to marry? Reasons Elizabeth chose Group Responsibilities No. of people: not to marry: Parliament Groups of people in the Royal What did Elizabeth do in response by 1566? Who was Elizabeth’s father and Court: mother? What happened to Peter Wentworth? Council Privy What happened to Elizabeth’s William Cecil mother? Key details: Elizabeth’s Suitors Lieutenants Robert Dudley Francis Duke of Anjou King Philip II of Spain Who was Elizabeth’s brother? Lord (Earl of Leicester) Name: Key details: Key details: Key details: Religion: Francis Walsingham: Key details: Who was Elizabeth’s sister? Justices of Name: Peace Nickname: Religion: Early Life 1560 1570 1580 1590 1600 Childhood 1569 1571 1583 1601 Preparation for life in the Royal The Northern Rebellion The Ridolfi Plot The Throckmorton Plot Essex’s Rebellion Court: Key conspirators: Key conspirators: Key conspirators: Key people: Date of coronation: The plan: The plan: The plan: What happened? Age: Key issues faced by Elizabeth: Key events: Key events: Key events: What did Elizabeth show in her response to Essex? The Catholic Plots Elizabethan England: Part 2 – Life in Elizabethan Times Elizabethan Society God The Elizabethan Theatre The Age of Discovery Key people and groups: New Companies: New Technology: What was the ‘Great Chain of Being’? Key details: Explorers and Privateers Francis Drake John Hawkins Walter Raleigh Peasants Position Income Details Nobility Reasons for opposition to the theatre: Gentry 1577‐1580 1585 1596 1599 Drake Raleigh colonises ‘Virginia’ in Raleigh attacks The Globe Circumnavigation North America. -

Paper 2: Early Elizabethan England 1558-88
Paper 2: Early Elizabethan England 1558-88 Number of I need to … Prove it! Marks Write 4 paragraphs. Use the examples given in the bullet points and an example from your own knowledge. Always Q1 The threat of invasion was Elizabeth’s main problem when she became queen explain how each example you write about agrees or disagrees with the statement in the question. End with a in 1558.’ How far do you agree? Explain your answer. You must use the conclusion. following in your answer 20 40%- First paragraph. Describe how the example in the first bullet point agrees/disagrees with the France and Spain (16 for Q statement. Explain how the example proves the statement is correct/incorrect The legitimacy of Elizabeth’s succession You must also use information of your own. [16 marks] + 4 for On the one hand, I agree with the statement that the threat of invasion was Elizabeth’s main threat SPaG) when she became queen in 1558. For example there was the threat of invasion from France and Spain More Q2.The threat from the Northern Earls 1569, was the most problematic revolt specifically, Mary Queen of Scots was married to the French King and there were French soldiers in Scotland who Elizabeth faced 1569-86.’ How far do you agree? Explain your answer. might invade. +Another example was that King Philip of Spain had promised to protect all Europe’s Catholics if You may use the following in your answer: • Babington Elizabeth made England protestant he might invade. This was a threat because France and Spain were both • Ridolfi very powerful countries and an invasion could result I Elizabeth being overthrown and even killed. -

Early Elizabethan England Revision Booklet NAME:______
Early Elizabethan England Revision Booklet NAME:____________ Contents Tick when complete Topic 1 • How did Elizabeth’s Early Life affect her later decisions? p 2-3 What were the • What were the threats to Elizabeth’s succession? P 3-5 early threats to • How did Elizabeth govern? P6 Elizabeth’s reign? • What was the Religious Settlement? 7-10 • How serious was the Puritan Challenge? P 11-12 • Why was Mary Queen of Scots a Threat 1858-1868? p 12-13 • Knowledge and Exam Question Checklist p 14 Topic 2 • What were the causes of the Revolt of the Northern Earls p15-16 What were the Catholic • Which Plot was the greatest threat to Elizabeth? P 17-19 Plots that threatened • Why was Mary Queen of Scots executed in 1587? P20-21 Elizabeth? Why did England go to War with • Why did England go to war with Spain in 1585? p22-24 Spain in 1585? Why was • Why was the Spanish Armada defeated in 1588? p24-26 the Armada defeated in • Knowledge and Exam Question Checklist p 27 1588? Topic 3 • Why did poverty increase in Elizabethan England? p28-29 Elizabethan Society in • Why were Elizabethans so scared of Vagabonds? p30-33 the Age of exploration • Why did Drake and Raleigh go on voyages around the world and what did they discover? p33-36 • Why did the Virginia colonies fail? p37-40 • Was there a Golden Age for all Elizabethans? P41-43 • Knowledge and Exam Question Checklist p 44 Quizzes • Topic 1 p 45-46 • Topic 2 p 47-48 • Topic 3 p 49-50 Learning Ladder • 16 mark p 51 • 12 mark p 52 • 4 mark p 53 1 Topic 1 pages 2-14 How did Elizabeth’s Early Life affect her later decisions? 1. -

Elizabethan England 1558-88. (Paper 2) Model Answer Work Booklet
Elizabethan England 1558‐88. (Paper 2) Model Answer work booklet. 1 Question 5a Describe two features of ‐‐‐‐ (4 marks) 5 minutes? Model Answers Example 1... Describe two key features of the plots against Elizabeth from 1571 to 1587. (4 marks) One feature of the Throckmorton plot of 1583 was that it planned for the French Duke of Guise, Mary Queen of Scots’ cousin to invade England. This would lead to the overthrow of Elizabeth and the restoration of the Catholic Church as England’s official religion. Another feature of the Babington Plot of 1586 was that English Catholics would rise up and rebel against Elizabeth. With support from the Pope they would kill Elizabeth and replace her with Mary Queen of Scots who many Catholics saw as a more legitimate monarch. There are clearly two very specific features Each of the features are further developed or identified. explained briefly. Example 2... Describe two features of Mary Queen of Scots’ threat to Elizabeth I. (4 marks) According to many people at the time Mary Queen of Scots had a stronger claim to the English throne than Elizabeth I. Some Catholics especially thought that Elizabeth was illegitimate and should not be Queen of England whereas Mary was a real Queen. There were several Roman Catholic plots to put Mary Queen of Scots on the throne. The Ridolfi plot of 1571 was a real threat to Elizabeth and Catholics tried to use Mary Queen of Scots as a possible replacement to Elizabeth; which made the plots a real threat to her. There are clearly two very specific features Each of the features are further developed or identified. -

Anthony Rivers" and the Appellant Controversy, 1601-2 John M
Notre Dame Law School NDLScholarship Journal Articles Publications 2006 The ecrS et Sharers: "Anthony Rivers" and the Appellant Controversy, 1601-2 John M. Finnis Notre Dame Law School, [email protected] Patrick Martin Follow this and additional works at: https://scholarship.law.nd.edu/law_faculty_scholarship Part of the Legal History Commons Recommended Citation John M. Finnis & Patrick Martin, The Secret Sharers: "Anthony Rivers" and the Appellant Controversy, 1601-2, 69 Huntington Libr. Q. 195 (2006). Available at: https://scholarship.law.nd.edu/law_faculty_scholarship/681 This Article is brought to you for free and open access by the Publications at NDLScholarship. It has been accepted for inclusion in Journal Articles by an authorized administrator of NDLScholarship. For more information, please contact [email protected]. The Secret Sharers: “Anthony Rivers” and the Appellant Controversy, 1601–2 Author(s): Patrick Martin and and John Finnis Source: Huntington Library Quarterly, Vol. 69, No. 2 (June 2006), pp. 195-238 Published by: University of California Press Stable URL: http://www.jstor.org/stable/10.1525/hlq.2006.69.2.195 . Accessed: 14/10/2013 09:19 Your use of the JSTOR archive indicates your acceptance of the Terms & Conditions of Use, available at . http://www.jstor.org/page/info/about/policies/terms.jsp . JSTOR is a not-for-profit service that helps scholars, researchers, and students discover, use, and build upon a wide range of content in a trusted digital archive. We use information technology and tools to increase productivity and facilitate new forms of scholarship. For more information about JSTOR, please contact [email protected]. -

Elizabeth's 'Middle Way' Brought Both Catholic and Protestant Elements
Improve your knowledge – Elizabethan England 1568-1603: Trouble at Home and Abroad. Timeline of key events 1583 The Throckmorton Plot - an attempt by English Roman Catholics to murder Queen Elizabeth I of England and replace her with her first cousin once removed, Mary, Queen of Scots. May 1559 Act of Supremacy was passed. It re-established the break from Rome and an independent Church of England (like Henry VIII in 1534). As a compromise, Elizabeth chose the less controversial title of Supreme 1585 Act Against Jesuits and Seminary Priests. This made becoming a priest treason, and all priested were Governor rather than Supreme Head of the Church (to please the Catholics due to removing papal ordered to leave England within 40 days on pain of death. authority). 1586 Babington Plot and trial of Mary, Queen of Scots, for treason. It was a plan in to assassinate Queen Elizabeth May 1559 Act of Uniformity was passed. This created a new Book of Common Prayer which was moderately worded I, a Protestant, and put Mary, Queen of Scots, her Roman Catholic cousin, on the English throne. but contained radical Protestant ideas. Catholic Mass was abandoned. The Bible and services were in English and the clergy were allowed to marry. Old catholic practices like pilgrimages and saints’ images February Mary, Queen of Scots, is executed at Fotheringhay Castle (increased already hostile tensions with Philip II of were banned. To please Catholics Priests were to wear traditional Catholic-style vestments and ornaments 1587 Spain). such as crosses and candles could be placed on the communion table (which replaced the altar). -

A Publication of the University of Dallas Drama Department
OnStage A Publication of the University of Dallas Drama Department 1 ONSTAGE Welcome to the first edition of OnStage, a Table of Contents new way for you, our audience, to engage more deeply with the productions of the drama department. OnStage will be published 3 The Life and Times of Mary once a semester and you can look forward to coverage which highlights our plays Stuart in performance with a focus on our major production each semester. My hope is 5 Tudor Timeline that OnStage will offer you a rich opportunity to enlarge and expand the ways in which we can interact with each other centered on the dynamic productions on 6 Coffee with the Queens our stages! 8 Cast and Characters 10 The Life of Friedrich Schiller Our first issue focuses on the fall 2015 mainstage, Mary Stuart, Schiller’s stunning 11 Modern Mary: Bringing the historical drama of political ambition, sexual jealousy and spiritual redemption. Queen of Scots to the 21st I am directing modern playwright Peter Oswald’s new version which features a muscular and direct english and uses both prose and poetry to dynamic effect. The Century historical Mary Stuart has always captured the imagination even while she was 12 Tackling Schiller: An Interview still alive. When Schiller began to work on his play, Mary was thought of in popular with Director Kyle Lemieux lore as a kind of second Helen. The Mary of our imagination is the Mary that exists 14 Behind the Scenes: An Interview in Schiller’s play, but no less so than Elizabeth, who by 1800 in Germany also had with the Designers mythic status as a ruler- “The Virgin Queen”. -

The Babington Plot Numerous Contacts Within the Catholic Community to Travel the Country Without Suspicion
Arnaud Moragues - Emilangues 2011 the Babington Plot numerous contacts within the Catholic community to travel the country without suspicion. Since she abdicated from the But Gifford was actually a double agent. Back in 1585, he had written to throne of Scotland in 1567 and fled Sir Francis Walsingham, Principal Secretary to Queen Elizabeth, to England, Mary, Queen of offering his services as a spy. Each time Gifford collected a message to Scots, the Roman Catholic or from Mary, he would first take it to Walsingham. claimant to the throne of England, came under the custody of the The vigilant spymaster would then break the seal on each letter, make a protestant Queen of England, copy, and then reseal the original letter with an identical stamp before Elizabeth I. Mary became the handing it back to Gifford. The apparently untouched letter could then focus of many plots and intrigues be delivered to Mary or her correspondents, who remained unaware to against the Queen and because of what was going on. this threat, she was imprisoned for eighteen years. Walsingham easily broke the cipher, and willing to know the names of all the conspirators, he encoded and sent back a forged message to Anthony Babington, a member Babington, impersonating Mary: of the Catholic gentry, led and organized the English Catholics Mary, Queen of Scotts, 1578 against Elizabeth. Understanding "I would be glad to know the names and qualities of the six gentlemen which are to accomplish the designment..." that he couldn't depose Queen Elisabeth without murdering her, he began to plot against her in 1586.