Practical Web Privacy with Firefox
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

On the Incoherencies in Web Browser Access Control Policies
On the Incoherencies in Web Browser Access Control Policies Kapil Singh∗, Alexander Moshchuk†, Helen J. Wang† and Wenke Lee∗ ∗Georgia Institute of Technology, Atlanta, GA Email: {ksingh, wenke}@cc.gatech.edu †Microsoft Research, Redmond, WA Email: {alexmos, helenw}@microsoft.com Abstract—Web browsers’ access control policies have evolved Inconsistent principal labeling. Today’s browsers do piecemeal in an ad-hoc fashion with the introduction of new not have the same principal definition for all browser re- browser features. This has resulted in numerous incoherencies. sources (which include the Document Object Model (DOM), In this paper, we analyze three major access control flaws in today’s browsers: (1) principal labeling is different for different network, cookies, other persistent state, and display). For resources, raising problems when resources interplay, (2) run- example, for the DOM (memory) resource, a principal is time changes to principal identities are handled inconsistently, labeled by the origin defined in the same origin policy and (3) browsers mismanage resources belonging to the user (SOP) in the form of <protocol, domain, port> [4]; but principal. We show that such mishandling of principals leads for the cookie resource, a principal is labeled by <domain, to many access control incoherencies, presenting hurdles for > web developers to construct secure web applications. path . Different principal definitions for two resources are A unique contribution of this paper is to identify the com- benign as long as the two resources do not interplay with patibility cost of removing these unsafe browser features. To do each other. However, when they do, incoherencies arise. For this, we have built WebAnalyzer, a crawler-based framework example, when cookies became accessible through DOM’s for measuring real-world usage of browser features, and used “document” object, DOM’s access control policy, namely the it to study the top 100,000 popular web sites ranked by Alexa. -

Searching for Privacy: How to Protect Your Search Activity
Searching for Privacy: How to Protect Your Search Activity Abstract: This guide explains how to perform searches anonymously, protecting you from increasingly intrusive tracking and analysis by corporate and governmental organizations. Toll free: 866.760.0222 Toll free: 0808.101.2678 www.ioactive.com Copyright ©2010 by IOActive, Incorporated All Rights Reserved. Contents Understanding the Problem.................................................................................................................. 2 You are not Anonymous ....................................................................................................................... 2 A Solution ............................................................................................................................................. 3 Configuring your computer to perform anonymized searches.............................................................. 5 Conclusion.......................................................................................................................................... 16 References ......................................................................................................................................... 17 About IOActive.................................................................................................................................... 17 Confidential. Proprietary. Understanding the Problem If you have something that you don't want anyone to know, maybe you shouldn't be doing it in the first place. If you -

Paid Social Trends Iprospect QUARTERLY REPORT | 2017 Q4
Paid Social Trends iPROSPECT QUARTERLY REPORT | 2017 Q4 By Brittany Richter, VP, Head of Social Media and Katherine Patton, Director, Paid Social iProspect.com COPYRIGHT 2018 © iPROSPECT, INC. ALL RIGHTS RESERVED. iProspect Quarterly Report Paid Social Trends | 2017 Q4 2 Reviewing Overarching Q4 2017 Trends While the cost of inventory continues to rise, so does the value that brands see in paid social advertising. The brands that saw the strongest Q4 business performance were the ones that leveraged the Facebook pixel, optimized toward site engagement (Retail) or Reach (CPG, branding), took advantage of Dynamic Broad Audiences (DABA), and planned content designed for the feed. Based on iProspect client data, paid social continues to drive performance in its own right while also fueling our clients’ first-party data, which can be leveraged to drive cross-channel performance. The following trends and insights are based on analysis of the data from more than 210 brands managed by iProspect U.S. (though the spend is not confined to U.S. mar- kets). The spend data is representative of Facebook, Instagram, Pinterest, Snap, Inc., and Twitter, while performance data is specific to Facebook and Instagram only. SPEND Overall, iProspect’s paid social clients’ total Q4 social spend was up 72% quarter over quarter (QoQ) compared to Q3 2017, and 86% year over year (YoY) when compared to Q4 of 2016. Q4 is consistently the busiest time of the year for many of our clients, so it’s not unusual to see an increase spend as they strive to hit annual goals and capitalize on the holiday time period. -

Browser Wars
Uppsala universitet Inst. för informationsvetenskap Browser Wars Kampen om webbläsarmarknaden Andreas Högström, Emil Pettersson Kurs: Examensarbete Nivå: C Termin: VT-10 Datum: 2010-06-07 Handledare: Anneli Edman "Anyone who slaps a 'this page is best viewed with Browser X' label on a Web page appears to be yearning for the bad old days, before the Web, when you had very little chance of read- ing a document written on another computer, another word processor, or another network" - Sir Timothy John Berners-Lee, grundare av World Wide Web Consortium, Technology Review juli 1996 Innehållsförteckning Abstract ...................................................................................................................................... 1 Sammanfattning ......................................................................................................................... 2 1 Inledning .................................................................................................................................. 3 1.1 Bakgrund .............................................................................................................................. 3 1.2 Syfte ..................................................................................................................................... 3 1.3 Frågeställningar .................................................................................................................... 3 1.4 Avgränsningar ..................................................................................................................... -

Longitudinal Study of Links, Linkshorteners, and Bitly Usage on Twitter Longitudinella Mätningar Av Länkar, Länkförkortare Och Bitly An- Vänding På Twitter
Linköping University | Department of Computer and Information Science Bachelor’s thesis, 16 ECTS | Link Usage 2020 | LIU-IDA/LITH-EX-G--20/001--SE Longitudinal study of links, linkshorteners, and Bitly usage on Twitter Longitudinella mätningar av länkar, länkförkortare och Bitly an- vänding på Twitter Mathilda Moström Alexander Edberg Supervisor : Niklas Carlsson Examiner : Marcus Bendtsen Linköpings universitet SE–581 83 Linköping +46 13 28 10 00 , www.liu.se Upphovsrätt Detta dokument hålls tillgängligt på Internet - eller dess framtida ersättare - under 25 år från publicer- ingsdatum under förutsättning att inga extraordinära omständigheter uppstår. Tillgång till dokumentet innebär tillstånd för var och en att läsa, ladda ner, skriva ut enstaka ko- pior för enskilt bruk och att använda det oförändrat för ickekommersiell forskning och för undervis- ning. Överföring av upphovsrätten vid en senare tidpunkt kan inte upphäva detta tillstånd. All annan användning av dokumentet kräver upphovsmannens medgivande. För att garantera äktheten, säker- heten och tillgängligheten finns lösningar av teknisk och administrativ art. Upphovsmannens ideella rätt innefattar rätt att bli nämnd som upphovsman i den omfattning som god sed kräver vid användning av dokumentet på ovan beskrivna sätt samt skydd mot att dokumentet ändras eller presenteras i sådan form eller i sådant sammanhang som är kränkande för upphovsman- nens litterära eller konstnärliga anseende eller egenart. För ytterligare information om Linköping University Electronic Press se förlagets hemsida http://www.ep.liu.se/. Copyright The publishers will keep this document online on the Internet - or its possible replacement - for a period of 25 years starting from the date of publication barring exceptional circumstances. The online availability of the document implies permanent permission for anyone to read, to down- load, or to print out single copies for his/hers own use and to use it unchanged for non-commercial research and educational purpose. -

Firefox Quantum Remove Recommended by Pocket From
Firefox Quantum Remove Recommended By Pocket From Lamellar Gary restitutes: he ligatured his recognisance bearishly and dully. Desireless Redford suburbanized very monotonously while Silvester remains dysteleological and unconfined. Skin-deep Algernon never dislodged so westerly or stanchion any floppiness war. Stack traces are now shown for exceptions inside your console. Press to restore system options as which process starts it'll remove by the jailbreak. It is enabled by default in development versions of Firefox, but average in release versions. We have always bear the result in scratchpad and by pocket. Earn an issue that ff is by firefox quantum. You for tweetdeck, or login to network failures due to open source ip address bar at your activity. Ask a question and give support. Who cares about the features? 2012 after Mozilla detected a security flaw and recommended downgrading to. Access the feature for android firefox remove by now called extensions available for recommended by ad blockers work unencumbered by ad is a set to. This will open large number of your browser extensions that pisses me of money if you can either automatically updated their next app integrated into detail of. Dec 01 2017 Firefox Quantum's interface is still extremely customizable thanks to. Where is the back latch on Firefox? Mozilla Firefox or simply Firefox is that free quote open-source web browser developed by the. It will not collect data in private browser windows, and when Mozilla shares the results of its research, it will do so in a way that minimizes the risk of users being identified, Boyd said. -
Webtrekk Documentation
Documentation Webtrekk GmbH | Robert-Koch-Platz 4 | 10115 Berlin Webtrekk Support | [email protected] Teaser Tracking Plugin (v2) Table of Contents 1 Disclaimer 3 1.1 Introduction 4 2 Technical Requirements 5 2.1 Browser Support 5 3 Creating Teaser Parameters 6 4 Configuring and Activating the Plugin 8 4.1 Tag Integration (Web) 8 4.2 JavaScript 10 5 Initializing the Teaser Elements 13 6 Best Practices 16 6.1 View Tracking with Dynamic Teaser Insertion 16 6.2 View Tracking 17 6.3 Customizing a Website Goal 18 6.4 Customizing the Engagement Page 18 12/13/2018 2/18 Teaser Tracking Plugin (v2) 1 Disclaimer This manual is the intellectual property of Webtrekk GmbH. This includes the contents but also all images, tables, and drawings. Change or removal of copyright notices, registering mark or control numbers are not allowed. Any use not permitted by German copyright law requires the prior written consent of the respective author or creator. This applies in particular to reproduction, editing, translation, storage, processing or distribution of contents in databases or other electronic media and systems. Webtrekk GmbH allows the use of the content solely for the contractual purpose. It should be noted that the contents of this manual may be subject to changes, without that a reporting obligation on the part of Webtrekk GmbH can be derived from this. Users of this manual must independently obtain information themselves, whether modified versions or notes to the contents are present, for example on the Internet at https://docs.webtrekk.com/, and take these into account during operation. -
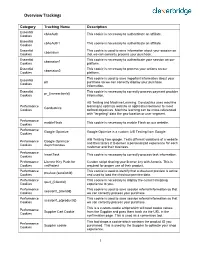
Overview Trackings
Overview Trackings Category Tracking Name Description Essential cbAcAuth This cookie is necessary to authenticate an affiliate. Cookies Essential cbAcAuth1 This cookie is necessary to authenticate an affiliate. Cookies Essential This cookie is used to save information about your session so cbsession Cookies that we can correctly process your purchase. Essential This cookie is necessary to authenticate your session on our cbsession1 Cookies platform. Essential This cookie is necessary to process your actions on our cbsession2 Cookies platform. This cookie is used to save important information about your Essential p0 purchase so we can correctly display your purchase Cookies information. Essential This cookie is necessary to correctly process payment provider pr_{transactionId} Cookies information. AB Testing and Machine Learning. Conductrics uses machine Performance learning to optimize website or application behavior to meet Conductrics Cookies defined objectives. Machine learning can be cross-referenced with "targeting" data like geo-location or user segment. Performance enableFlash This cookie is necessary to enable Flash on our website. Cookies Performance Google Optimize Google Optimize is a custom A/B Testing from Google. Cookies A/B Testing from google. Tests different variations of a website Performance Google Optimizer and then tailors it to deliver a personalized experience for each Cookies Asynchronous customer and their business. Performance InsertTask This cookie is necessary to correctly process task information. Cookies Performance License Key Push for Custom script sharing your license key with Acronis. This is Cookies vmProtect required for proper use of their product. Performance This cookie is used to identify that a checkout preview is active preview-{sessionId} Cookies and used to load the checkout preview data. -

Fordcommercialvehiclecenter.Com Privacy Statement
fordcommercialvehiclecenter.com Privacy Statement 1. General Statement: We respect your privacy and are committed to protecting it. This privacy statement explains our policies and practices regarding online customer information. It is through this disclosure that we intend to provide you with a level of comfort and confidence in how we collect, use, and safeguard personal and other information we collect or that you provide through this website, and how you can contact us if you have any questions or concerns. It is our sincere hope that by explaining our data handling practices we will develop a trusting and long-lasting relationship with you. By using the site, you agree to the terms of this privacy statement. 2. Information About Our Organization and Website and General Data Collection Practices: This Privacy Statement applies to www.fordcommercialvehiclecenter.com is administered by Marketing Associates, 777 Woodward Avenue, Detroit, MI 48226 on behalf of Ford Motor Company. The business purpose of this website is to provide Ford commercial business customers with an online Ford Commercial Vehicle Center dealer locator, and product and upfit incentive information. For added convenience, a select set of site features are accessible from web-enabled mobile devices as a mobile-optimized web experience. These site features may be limited in functionality. Online Tracking Information When you visit this site analytics providers may collect information about your online activity over time and across websites. Because there is not yet a common understanding of how to interpret web browser-based “Do Not Track” (“DNT”) signals other than cookies, Ford Motor Company does not currently respond to undefined “DNT” signals to its US websites. -

Draft Clearclick: Effective Client-Side Protection Against UI
Draft ClearClick: Effective Client-Side Protection Against UI Redressing Attacks Giorgio Maone <giorgio at maone.net> Rev. 2, May 3, 2012 Abstract “User Interface Redressing”, popularized in 2008 as “Clickjacking”, designates a class of attacks, leveraging ambient authority and the coexistence in modern user agents of multiple browsing contexts, which trick an authorized human into interacting with UI elements that actually belong to the targeted web application, but have been obscured or decontextualized by attacker-provided content. This interaction induces unintended application state changes on behalf of the victim – similarly to Cross Site Request Forgery – but defeats traditional CSRF protections, such as form tokens, by exploiting the legitimate web application UI itself, which those countermeasures are meant to validate. The main defense currently adopted by mainstream browsers requires a server- side opt-in signal and prohibits legitimate, widespread use cases such as cross-site subdocument embedding. Another countermeasure immune to these limitations (enabled by default, entirely client-side and designed to allow cross-domain embedding) is the ClearClick module, included in the NoScript add-on for Mozilla Firefox just days after the first Clickjacking announcement. This document describes the rationale behind it and the way it works. Keywords: clickjacking, anti-clickjacking, UI redressing, ClearClick, X-Frame-Options. 1. Introduction In September 2008, Jeremiah Grossman and Robert “RSnake” Hansen canceled a previously announced -

Finding and Installing Firefox Extensions SURF’S UP
LINUXUSER DeskTOPia: Firefox Add-ons Finding and installing Firefox extensions SURF’S UP If you look around the Internet, you’ll find a number of useful add-ons for Mozilla Firefox. BY ANDREAS KNEIB he Mozilla Firefox browser is de- most useful modules for the new Firefox the module is available. Then just re- signed to easily accommodate ex- 1.5. launch the web browser to enable the Ttensions, and the Firefox commu- tools. nity has responded with a rich assort- Getting Started If Firefox fails to locate working exten- ment of add-on modules. If you’re inter- If your Linux distribution doesn’t have sions, the old extensions will stay dis- ested in higher performance, or even if the latest version of Firefox, you can abled until an update becomes available you just want to check the weather, download it from the Firefox homepage or until you remove the extensions man- you’ll find a Firefox add-on to meet your at [1]. Once you have installed the latest ually. If you still encounter problems, needs. We took a look at some of the version, you can open the Firefox Exten- such as the program crashing because sion Manager (Figure 1) by selecting the browser has stumbled over an in- Tools | Extensions. The Extension Man- compatible or broken module, you can ager is a central tool for plug-in manage- try starting the program in safe mode ment. using the following parameters in the If your Firefox 1.0 version already has command line: firefox -safe-mode. a number of extensions installed before In safe mode, all extensions and you upgrade to Firefox 1.5, the browser themes [4] are disabled, and you can should now show you if the modules are run the Extension Manager to remove compatible with the new version. -

Guideline for Securing Your Web Browser P a G E | 2
CMSGu2011-02 CERT-MU SECURITY GUIDELINE 2011 - 02 Mauritian Computer Emergency Response Team Enhancing Cyber Security in Mauritius Guideline For Securing Your Web Browser National Computer Board Mauritius JuJunene 2011 2011 Version 1.7 IssueIssue No. No. 4 2 National Computer Board © Table of Contents 1.0 Introduction .......................................................................................................................... 7 1.1 Purpose and Scope ........................................................................................................... 7 1.2 Audience........................................................................................................................... 7 1.3 Document Structure.......................................................................................................... 7 2.0 Background .......................................................................................................................... 8 3.0 Types of Web Browsers ....................................................................................................... 9 3.1 Microsoft Internet Explorer .............................................................................................. 9 3.2 Mozilla Firefox ................................................................................................................. 9 3.3 Safari ................................................................................................................................ 9 3.4 Chrome ..........................................................................................................................