Mobile Viruses
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Symbian Worm Yxes: Towards Mobile Botnets?
J Comput Virol (2012) 8:117–131 DOI 10.1007/s11416-012-0163-2 ORIGINAL PAPER Symbian worm Yxes: towards mobile botnets? Axelle Apvrille Received: 20 December 2010 / Accepted: 3 April 2012 / Published online: 1 May 2012 © Springer-Verlag France 2012 Abstract In 2009, a new Symbian malware named the costs and inconveniences caused by the famous Comm- SymbOS/Yxes was detected and quickly hit the headlines Warrior worm, with 115,000 infected phones [14] and over as one of the first malware for Symbian OS 9 and above 450,000 messages [16] sent prove the matter cannot be under- all as the foretaste of a mobile botnet. Yet, detailed analy- estimated. sis of the malware were still missing. This paper addresses At the beginning of 2009, a new Symbian malware was this issue and details how the malware silently connects to detected [13]. It installed on recent and widely-deployed the Internet, installs new malware or spreads to other victims. Symbian OS 9 phones. The malware looked perfectly legiti- Each of these points are illustrated with commented assembly mate and there was no hint it might be a malware apart from code taken from the malware or re-generated Symbian API the fact it created no application icon. As it was typically con- calls. Besides those implementation aspects, the paper also nected to the word “sexy” (sexy.sisx as package name, “Sexy provides a global overview of Yxes’s behaviour. It explains View”, “Sexy Girls”, “Sexy Space” as application name etc), how malicious remote servers participate in the configuration Fortinet christened it Yxes, i.e. -

Contemporary Report
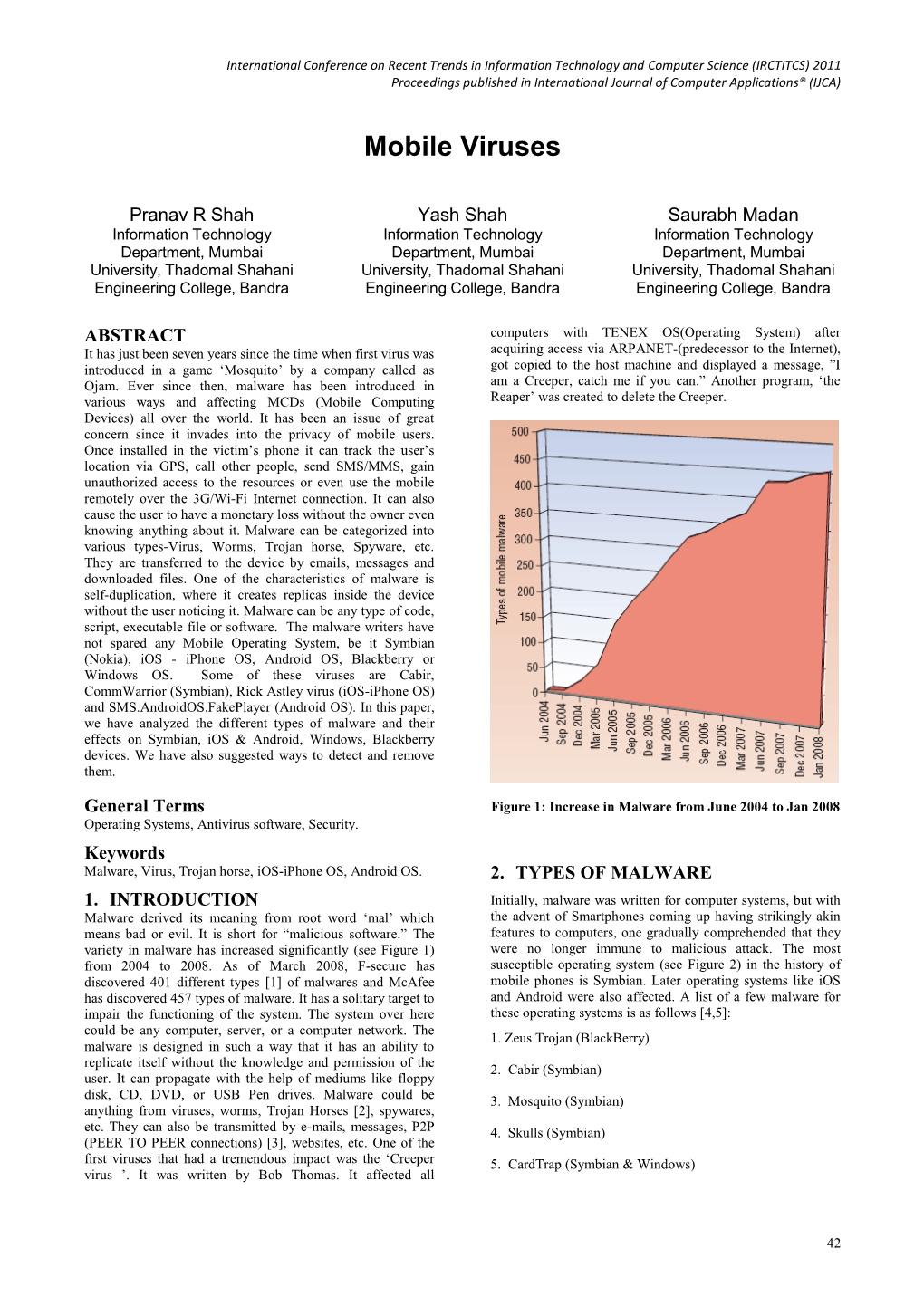
. .......... Mobile Phone and Infrastructure Vulnerabilities Summary and Analysis of Disclosed Issues 2005-2006 Prasanna Kannan Nesret Krasniqi The Thesis comprises 30 ECTS credits and is a compulsory part in the Master of Science with a Major in Master’s Programme in Electrical Engineering with specialisation in Communication and Signalprocessing, 120 ECTS credits Nr 9/2007 Mobile Phone and Infrastructure Vulnerabilities 2005 & 2006 Mobile Phone and Infrastructure Vulnerabilities – summary and analysis of disclosed issues 2005 - 2006 Prasanna Kannan Nesret Krasniqi Master thesis Series and Number Communication and Signal Processing 9/2007 University College of Borås School of Engineering SE-501 90 BORÅS Telephone +46 033 435 4640 Examiner: Jim Arlebrink Supervisor: Lennart Damm Client: OnePutt Solutions, Uppsala, Sweden. Date: 2007-11-08 Keywords: Mobile vulnerabilities , symbian viruses 1 Mobile Phone and Infrastructure Vulnerabilities 2005 & 2006 TABLE OF CONTENTS Abstract………………………………………………………………………………………………………………………10 Introduction……………………………………………………………………………………………………………..........11 About this report…………………………………………………………………………………………………………….12 What is a mobile phone virus and how does it spread? .............. ……………………………………………………………………114 List of vulnerabilities addressed…………………………………………………………………………………………….13 Statistics diagrams for 2005 and 2006………………………………………………………………………………………14 Overview of vulnerability families…………………………………………………………………………………………..16 Analysis………………………………………………………………………………………………………………………26 1. Skulls.D vulnerability -

Yet Another Symbian Vulnerability Update
Edith Cowan University Research Online Australian Information Security Management Conference Conferences, Symposia and Campus Events 11-30-2010 Yet Another Symbian Vulnerability Update Nizam Uddin Bhuiyan Edith Cowan University Follow this and additional works at: https://ro.ecu.edu.au/ism Part of the Information Security Commons DOI: 10.4225/75/57b523eccd8ae 8th Australian Information Security Mangement Conference, Edith Cowan University, Perth Western Australia, 30th November 2010 This Conference Proceeding is posted at Research Online. https://ro.ecu.edu.au/ism/101 Proceedings of the 8th Australian Information Security Management Conference Yet Another Symbian Vulnerability Update Nizam Uddin Bhuiyan School of Computer and Security Science Edith Cowan University Perth, Western Australia [email protected] Abstract The more the mobile devices are approaching to advance their security, the numbers of vulnerabilities are also becoming more astonishing. The number of mobile phones including smart phones is rising vertically, and so has the amount of malware activity. This report documents the latest threats in Symbian mobile industry and analyses the consequence. In addition, it will suggest the possible solution that may help individuals to protect their device & ultimately maintain the privacy. Keywords Symbian, Nokia vulnerability, Nokia threats, Mobile threat, Symbian malware, Symbian virus, Cell security, Consequences and counter measure for mobile threats. BACKGROUND The popularity of mobile has reached to sky high regardless whether you receive a blank SMS frequently or your mobile keeps sending a SMS to strangers persistently without your knowledge. According to Goode Intelligence 2009 Mobile Security Survey, “In the last couple of years, the percentage of mobile messaging traffic (SMS/MMS/e-mail) that is defined as spam or malware has risen from approximately 2% to between 20% and 30% of total traffic” (Francis, 2010). -

Symbian 'Vulnerability' and Mobile Threats
Symbian ‘vulnerability’ and Mobile Threats Wajeb Gharibi Head of Computer Engineering &Networks Department, Computer Science & Information Systems College, Jazan University, Jazan 82822-6694, Kingdom of Saudi Arabia [email protected] Abstract some possible protection techniques. Conclusions have been made in Section 5. Modern technologies are becoming ever more integrated with each other. Mobile phones are 2. Symbian Vulnerabilities becoming increasing intelligent, and handsets are The term 'vulnerability' is often mentioned in growing ever more like computers in functionality. connection with computer security, in many We are entering a new era - the age of smart different contexts. It is associated with some houses, global advanced networks which violation of a security policy. This may be due to encompass a wide range of devices, all of them weak security rules, or it may be that there is a exchanging data with each other. Such trends problem within the software itself. In theory, all clearly open new horizons to malicious users, and types of computer/mobile systems have the potential threats are self evident. vulnerabilities [1-5]. In this paper, we study and discuss one of the most Symbian OS was originally developed by Symbian famous mobile operating systems „Symbian‟; its Ltd.[4]. It designed for smartphones and currently vulnerabilities and recommended protection maintained by Nokia. The Symbian platform is the technologies. successor to Symbian OS and Nokia Series 60; Keywords: Information Security, Cyber Threats, unlike Symbian OS, which needed an Mobile Threats, Symbian Operating System. additional user interface system, Symbian includes a user interface component based on S60 5th 1. Introduction Edition. -

An Analysis of Mobile Malware Evolution
An Analysis of Mobile Malware Evolution Author: Tommy Tianyu Zhu [email protected] An Analysis of Mobile Malware Evolution Abstract People used to think of malicious software - or more commonly known as malware - as mainly a threat to desktop or laptop computers. As the use of smartphones becomes increasingly integrated into daily lives, the amount of mobile malware attacks is also growing rapidly. Smartphones have become a common device for storing personal information and sensitive data, which made them perfect targets for malware. Although the largest mobile companies like Apple and Google have taken tremendous measures to protect their users, malware keeps evolving and continue to find new ways onto smartphone systems. This paper will discuss the evolution of mobile malware in recent years. We will investigate the history of mobile malware, survey the emergence of new attack philosophies and way of distribution, evaluate the current situation, and discuss the future of mobile malware. Introduction Nowadays, most smartphone users store private information such as messages, photos, emails, and even banking information on their mobile devices. While more and more people consider a smartphone as an essential part of their daily lives, they are often not aware of or not concerned enough with the potential security vulnerabilities of their devices. Smartphones grow “smarter” each year into sophisticated pocket computers that not only store huge amount of personal data, but also contain sensors such as GPS, camera, and fingerprint, which has made smartphones the perfect targets of information and identity theft and a great platform for spyware. As a result, malware that specifically targets mobile phones began to appear. -

Mobile and Ubiquitous Malware
IST-AWSN 2009 Proceedings of MoMM2009 Mobile and Ubiquitous Malware Yean Li Ho Swee-Huay Heng Multimedia University Multimedia University Jalan Ayer Keroh Lama Jalan Ayer Keroh Lama 75450 Melaka, Malaysia 75450 Melaka, Malaysia [email protected] [email protected] ABSTRACT owner might even be sensitive or confidential to the owner like Mobile malware is an increasing threat to the world of handheld personal information, phone numbers, credit card information devices, which can prove to be costlier than PC viruses in the used in m-commerce, photos, classified documents, e-contact future. The current method used to combat mobile malware is cards, and etc. virus signature matching which is based on the slow process of reverse engineering. This paper studies the growth, spread and 1.2 Mobile Malware Research Due to the proprietary nature and recency of this research area, generic behaviors of mobile and ubiquitous malware in mobile available literature is limited. Most existing research in Mobile phones. We extend the works of Bose et al. and Schmidt et al. Smartphone Virology focus on detection and identification of with an additional feature to reduce the effectiveness of mobile smart phone viruses [12,13,16,3,1,11]. So far, not much research malware propagation. The objective of our work is to investigate has been done to address the issue of finding the solution to these the trends and generic behavioral patterns of mobile malware and mobile viruses and worms with the exception of [15] and [2]. Xie suggest a generic proof-of-concept model which combines the et al. -

1. Introduction
Cell phone Virus And Security Seminar Report 2011 1. INTRODUCTION Phones are used in various ways. Majority of the people you see have a mobile phone. This comes as an advantage and a disadvantage. The advantage is the functionality and accessibility of the phone. Some are getting as powerful as laptops. With great power, however, comes great responsibility. The responsibility is the concern that a user should have of the security of their mobile phone. Numerous viruses are beginning to be made specifically to infect these phones. They are being targeted because of their vulnerability. Anything that is accessed via an open network is susceptible of being infected. Mobile phones are beginning to see that they are no different than their laptop counterpart. The variants that are being made can steal phonebooks or spread to other phones from the contacts that are stored in its host phone. The attacks are alarming and because of this many anti-virus companies are beginning tocome together and protect the phones from the malicious variants. One of the fastest growing technologies of our times is that of mobile phones. When one thinks of sources of communication, telephones would be one of the top sources. They have gone through many changes, going from the rotary phone, to the touch tone phone, to the cordless, and now to the mobile phone. With each advancement in technology comes more ways to exploit that technology. Since phones are the primary source of communication, an increase of exploitation of the advancement in technology has happened. When mobile phones were first used, because of the lack of technology, there susceptibility of being exploited was rare. -
Malicious Software in Mobile Devices
Chapter I Malicious Software in Mobile Devices Thomas M. Chen Southern Methodist University, USA Cyrus Peikari Airscanner Mobile Security Corporation, USA ABSTRACT This chapter examines the scope of malicious software (malware) threats to mobile devices. The stakes for the wireless industry are high. While malware is rampant among 1 billion PCs, approximately twice as many mobile users currently enjoy a malware-free experience. However, since the appearance of the Cabir worm in 2004, malware for mobile devices has evolved relatively quickly, targeted mostly at the popular Symbian smartphone platform. Significant highlights in malware evolution are pointed out that suggest that mobile devices are attracting more sophisticated malware attacks. Fortunately, a range of host-based and network-based defenses have been developed from decades of experience with PC malware. Activities are underway to improve protection of mobile devices before the malware problem becomes catastrophic, but developers are limited by the capabilities of handheld devices. INTRODUCTION found to be spreading “in the wild” (on real users’ PCs), but this list is known to comprise a small Most people are aware that malicious software subset of the total number of existing viruses. (malware) is an ongoing widespread problem The prevalence of malware was evident in a 2006 with Internet-connected PCs. Statistics about the CSI/FBI survey where 65% of the organizations prevalence of malware, as well as personal anec- reported being hit by malware, the single most dotes from affected PC users, are easy to find. PC common type of attack. malware can be traced back to at least the Brain A taxonomy to introduce definitions of malware virus in 1986 and the Robert Morris Jr. -
Mobile Malware Attacks: Review, Taxonomy & Future Directions
MOBILE MALWARE ATTACKS: REVIEW, TAXONOMY & FUTURE DIRECTIONS Attia Qamar1, Ahmad Karim2, Victor Chang3 1National College of Business Administration & Economics, Pakistan 2Department of Information Technology, Bahauddin Zakariya University, Pakistan 3International Business School Suzhou, Xi’an Jiaotong-Liverpool University, China Abstract A pervasive increase in the adoption rate of smartphones with Android OS is noted in recent years. Android's popular and attractive environment not only captured the attention of users but also increased security concerns. As a result, Android malware detection is one of the sizzling topics in the mobile security domain. This paper provides a comprehensive review of state-of-the-art mobile malware attacks, vulnerabilities, detection techniques and security solutions over the period of 2013-2019 that majorly targeted Android platform. We have presented various well-organized and in-depth taxonomies that uncover mobile malware detection approaches based on their analysis techniques, working platform, data acquisition, operational impact, obtained results and artificial intelligence component involved. Another taxonomy comprises of mobile malware attack vector is presented to look threat clusters and loopholes to locate their malicious widespread impact on communities. Furthermore, we have discussed and classified forensic analysis efforts in mobile malware detection perspective. From intruder point of view, we have compared various evasion techniques that are used prominently by the malware authors to hinder detection efforts. Finally, future work directions are presented as guidelines for academia and industry alike to help them reduce or even avoid the harmful impact of these annoying efforts. Keywords: Mobile Malware, Malware, Mobile malware detection, Android Malware, Machine Learning, Forensics 1. Introduction Smartphones are the recent advent of mobile platforms having diverse kind of operating systems in which android, iOS, Blackberry, Symbian and windows are included. -

Malware Goes Mobile by Mikko Hypponen
MALWARE GOES MOBILE BY MIKKO HYPPONEN Computer viruses are now airborne, infecting mobile phones in every part of the globe. Security companies, cellular operators and phone makers are moving to quash these threats before they spiral out of control he day the computer security community had anticipated for years finally arrived in June 2004. I and other researchers who study malicious forms of software knew that it was only a matter of time until such T malware appeared on mobile phones as well. As cell phones have evolved into smartphones—able to download programs from the Internet and share software with one another through short-range Bluetooth connections, worldwide multimedia messaging service (MMS) communications and memory cards—the devices’ novel capabilities have created new vulnerabilities. Scoundrels were bound to find the weaknesses and exploit them for mis- chief or, worse, for criminal gain. Sure enough, three summers ago security ex- perts found the first rogue program written spe- cifically for smartphones. Dubbed Cabir, it was a classic proof-of-concept virus, clearly created to 70 SCIENTIFIC AMERICAN NOVEMBER 2006 COPYRIGHT 2006 SCIENTIFIC AMERICAN, INC. INFECTION of one smartphone by malicious software—malware— could bring down others in a domino effect. COPYRIGHT 2006 SCIENTIFIC AMERICAN, INC. SMARTPHONES ON THE RISE s) 15 on MORE PHONES, MORE TARGETS The number of smart mobile devices (milli in the world has expanded dramatically de 10 dwi in recent years, and so has the amount rl Wo of malware set loose to attack them. , That mix is a recipe for disaster: as the ld 5 size of a target audience increases, so, s So too, does the likelihood that miscreant it Un programmers will attack it. -

Analysis of a Smartphone Worm
Analysis of Smartphone Worms: A Smart worm for Smartphones Kayhan Ozturk Qaiser Munir Email: {kayoz945, qaimu880}@student.liu.se Supervisor: Anna Vapen, {[email protected]} Project Report for Information Security Course Linköpings universitet, Sweden Abstract • How to mitigate the threats of a Cabir attack? In this report, we discuss about mobile phone worms 1.2 Aim which are running on the Symbian operating system. We In our report, we focused on the Cabir worm which focused especially on the Cabir worm which is the first is the first identified worm is written for Symbian OS identified worm on mobile phones. We analyzed the based phones. We explain how the Cabir worm works; Cabir worm to identify the flaws it uses to exploit in try to find ways to mitigate its threats and explain which Symbian and how its spreading functionality works. We technology it uses to spread. Also we compare it with also compare Cabir with some other Smartphone other worms for the Symbian operating system. worms. 1.3 Expected Results 1. Introduction We expect to understand that how this worm Mobile communication was a dream in 1800s but it works and how it is harmful for Smartphones. We will became real in 1940s with cell based radio telephony show a flash animation to demonstrate how it spreads service. Since the invention of the mobile phone, it is from one phone to another. rapidly increasing in use of daily life. Its popularity came from the answering the need of daily life [1]. 1.4 Method of Work Nowadays, mobile phones are suited with advanced For understanding the structure of Symbian OS and operating systems such as the Symbian OS, Windows explaining how Cabir/Caribe worm works we need a Mobile, Palm OS and Apple OS X for Apple iPhone. -

Summary of Mobile Threats for Year 2005
Summary Of Mobile Threats For Year 2005 The first Mobile Threat that appeared in year 2004, that is Cabir.A has shown that mobile phone threat is a proof-of-concept application.. However, most Symbian malwares are still quite primitive and most of them are not in the form of executable code. It is able to replicates itself via bluetooth devices that supporting Symbian Series 60 user interface platform. To date, Cabir.A has been spreaded widely until affected many countries such as Malaysia, United States, United Kingdom, Italy, Russia, Indonesia, Japan, New Zealand, Australia, Singapore etc. Cell phone threat are currently targeting on Symbian Series 60 user interface platform only because its population has been increased. Year 2005 has been proved to us that more than 120 types of variants that exists worldwide today and virus creators has been use Cabir as a basis to create more damageable malware. The matter that worried by anti-virus firm is that virus creators release and release their source code. A very good example is, a Brazilian fella has spreaded the cabir source code since last year December and now causing more than 26 variants that detected as Cabir Variant! Understanding Basic Symbian File System . Symbian file system can be divided into four groups and their functions are summarize as shown below: Type of drive:- Functions:- C drive Act as a flash RAM and it contains user installed applications, user data such as phonebook data, multimedia files, messaging data etc. D drive Act as a temporary RAM that store temporary files for applications and also some data about WAP contents.