Summary of Mobile Threats for Year 2005
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Symbian Worm Yxes: Towards Mobile Botnets?
J Comput Virol (2012) 8:117–131 DOI 10.1007/s11416-012-0163-2 ORIGINAL PAPER Symbian worm Yxes: towards mobile botnets? Axelle Apvrille Received: 20 December 2010 / Accepted: 3 April 2012 / Published online: 1 May 2012 © Springer-Verlag France 2012 Abstract In 2009, a new Symbian malware named the costs and inconveniences caused by the famous Comm- SymbOS/Yxes was detected and quickly hit the headlines Warrior worm, with 115,000 infected phones [14] and over as one of the first malware for Symbian OS 9 and above 450,000 messages [16] sent prove the matter cannot be under- all as the foretaste of a mobile botnet. Yet, detailed analy- estimated. sis of the malware were still missing. This paper addresses At the beginning of 2009, a new Symbian malware was this issue and details how the malware silently connects to detected [13]. It installed on recent and widely-deployed the Internet, installs new malware or spreads to other victims. Symbian OS 9 phones. The malware looked perfectly legiti- Each of these points are illustrated with commented assembly mate and there was no hint it might be a malware apart from code taken from the malware or re-generated Symbian API the fact it created no application icon. As it was typically con- calls. Besides those implementation aspects, the paper also nected to the word “sexy” (sexy.sisx as package name, “Sexy provides a global overview of Yxes’s behaviour. It explains View”, “Sexy Girls”, “Sexy Space” as application name etc), how malicious remote servers participate in the configuration Fortinet christened it Yxes, i.e. -

1 Smartphones and Symbian OS
1 Smartphones and Symbian OS Symbian OS is a full-featured, open, mobile operating system that powers many of today’s smartphones. As these smartphones become more pow- erful and popular, the demand for smartphone software has grown. Symbian smartphones are shipped with a variety of useful pre-loaded and targeted applications, which are selected by each phone’s manu- facturer. Today, the average Symbian smartphone ships with over 30 pieces of third-party software pre-installed. However, the exciting aspect of Symbian smartphones is that they are ‘open’, meaning that users can further customize their phone experience by downloading, installing, and uninstalling applications written by third-party developers (or by the users themselves). Users can download applications from a PC to the smartphone through a link such as USB, or Bluetooth technology, or over-the-air via the Internet. With the largest installed base of smartphones worldwide, Symbian OS offers a great opportunity for software developers to establish them- selves in the mobile market by creating novel and exciting software for the growing mass of smartphone users around the world. There is a growing list of Symbian applications available as freeware or as paid downloads on numerous Internet sites (http://www.handango.com and http://www.epocware.com are good examples). They range from pro- ductivity, entertainment, navigation, multimedia, and communications software to programs that can count fast food calories, improve your golfCOPYRIGHTED swing, keep diaries, and calculate MATERIAL foreign currency exchange. And business opportunities aside, sometimes it’s just plain fun writing your own code to run on your own smartphone. -

PRESS RELEASE Nokia Reports Fourth Quarter 2005 Net Sales Of
PRESS RELEASE 1 (24) January 26, 2006 Nokia reports fourth quarter 2005 net sales of EUR 10.3 billion, EPS of EUR 0.25 Nokia reports 2005 net sales of EUR 34.2 billion, EPS of EUR 0.83 Device market share gains in Q4 and 2005 drive 16% annual sales growth and 20% EPS growth Nokia’s Board of Directors will propose a dividend of EUR 0.37 per share for 2005 (EUR 0.33 per share for 2004) NOKIA Q4 and 2005 EUR million Q4/2005 Q4/2004 Change 2005 2004 Change (*revised) (%) (*revised) (%) Net sales 10 333 9 456 9 34 191 29 371 16 Mobile Phones 6 217 5 871 6 20 811 18 521 12 Multimedia 2 024 1 272 59 5 981 3 676 63 Enterprise Solutions 153 295 -48 861 839 3 Networks 1 951 2 031 -4 6 557 6 431 2 Operating profit 1 368 1 450 -6 4 639 4 326 7 Mobile Phones 1 060 1 107 -4 3 598 3 786 -5 Multimedia 310 168 85 836 175 Enterprise Solutions -136 -44 -258 -210 Networks 268 306 -12 855 884 -3 Common Group Expenses -134 -87 -392 -309 Operating margin (%) 13.2 15.3 13.6 14.7 Mobile Phones (%) 17.1 18.9 17.3 20.4 Multimedia (%) 15.3 13.2 14.0 4.8 Enterprise Solutions (%) -88.9 -14.9 -30.0 -25.0 Networks (%) 13.7 15.1 13.0 13.7 Financial income and expenses 78 116 -33 322 405 -20 Profit before tax and minority interests 1 453 1 556 -7 4 971 4 705 6 Net profit 1 073 1 083 -1 3 616 3 192 13 EPS, EUR Basic 0.25 0.24 4 0.83 0.69 20 Diluted 0.25 0.24 4 0.83 0.69 20 All reported Q4 and 2005 figures can be found in the tables on pages (10-13) and (19-23) SPECIAL ITEMS Fourth quarter 2005 special items - EUR 29 million charge for Enterprise Solutions restructuring -

Contemporary Report
. .......... Mobile Phone and Infrastructure Vulnerabilities Summary and Analysis of Disclosed Issues 2005-2006 Prasanna Kannan Nesret Krasniqi The Thesis comprises 30 ECTS credits and is a compulsory part in the Master of Science with a Major in Master’s Programme in Electrical Engineering with specialisation in Communication and Signalprocessing, 120 ECTS credits Nr 9/2007 Mobile Phone and Infrastructure Vulnerabilities 2005 & 2006 Mobile Phone and Infrastructure Vulnerabilities – summary and analysis of disclosed issues 2005 - 2006 Prasanna Kannan Nesret Krasniqi Master thesis Series and Number Communication and Signal Processing 9/2007 University College of Borås School of Engineering SE-501 90 BORÅS Telephone +46 033 435 4640 Examiner: Jim Arlebrink Supervisor: Lennart Damm Client: OnePutt Solutions, Uppsala, Sweden. Date: 2007-11-08 Keywords: Mobile vulnerabilities , symbian viruses 1 Mobile Phone and Infrastructure Vulnerabilities 2005 & 2006 TABLE OF CONTENTS Abstract………………………………………………………………………………………………………………………10 Introduction……………………………………………………………………………………………………………..........11 About this report…………………………………………………………………………………………………………….12 What is a mobile phone virus and how does it spread? .............. ……………………………………………………………………114 List of vulnerabilities addressed…………………………………………………………………………………………….13 Statistics diagrams for 2005 and 2006………………………………………………………………………………………14 Overview of vulnerability families…………………………………………………………………………………………..16 Analysis………………………………………………………………………………………………………………………26 1. Skulls.D vulnerability -
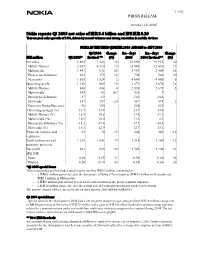
Q3 Results Release
1 (15) PRESS RELEASE October 20, 2005 Nokia reports Q3 2005 net sales of EUR 8.4 billion and EPS EUR 0.20 Year-on-year sales growth of 18%, driven by record volumes and strong execution in mobile devices NOKIA IN THE THIRD QUARTER 2005 AND JAN to SEPT 2005 Q3/2004 Change Jan - Sept Jan - Sept Change EUR million Q3/2005* Revised ** (%) 2005 2004 Revised** (%) Net sales 8 403 7 104 18 23 858 19 915 20 Mobile Phones 5 203 4 520 15 14 594 12 650 15 Multimedia 1 447 931 55 3 957 2 404 65 Enterprise Solutions 203 175 16 708 544 30 Networks 1 555 1 524 2 4 606 4 400 5 Operating profit 1 149 969 19 3 271 2 876 14 Mobile Phones 880 848 4 2 538 2 679 -5 Multimedia 245 93 163 526 7 Enterprise Solutions -37 -69 -122 -166 Networks 157 197 -20 587 578 2 Common Group Expenses -96 -100 -258 -222 Operating margin (%) 13.7 13.6 13.7 14.4 Mobile Phones (%) 16.9 18.8 17.4 21.2 Multimedia (%) 16.9 10.0 13.3 0.3 Enterprise Solutions (%) -18.2 -39.4 -17.2 -30.5 Networks (%) 10.1 12.9 12.7 13.1 Financial income and 63 78 -19 244 289 -16 expenses Profit before tax and 1 218 1 041 17 3 518 3 149 12 minority interests Net profit 881 685 29 2 543 2 109 21 EPS, EUR Basic 0.20 0.15 33 0.58 0.46 26 Diluted 0.20 0.15 33 0.58 0.46 26 *Q3 2005 special items Nokia’s operating profit includes special items totaling EUR 87 million, comprised of: - a EUR 61 million gain related to the divestiture of Nokia’s Tetra business (EUR 42 million in Networks and EUR 19 million in Multimedia) - a EUR 8 million gain related to real estate sales booked in the group common expenses - a EUR 18 million gain related to the partial sale of a minority investment booked in Networks. -

Yet Another Symbian Vulnerability Update
Edith Cowan University Research Online Australian Information Security Management Conference Conferences, Symposia and Campus Events 11-30-2010 Yet Another Symbian Vulnerability Update Nizam Uddin Bhuiyan Edith Cowan University Follow this and additional works at: https://ro.ecu.edu.au/ism Part of the Information Security Commons DOI: 10.4225/75/57b523eccd8ae 8th Australian Information Security Mangement Conference, Edith Cowan University, Perth Western Australia, 30th November 2010 This Conference Proceeding is posted at Research Online. https://ro.ecu.edu.au/ism/101 Proceedings of the 8th Australian Information Security Management Conference Yet Another Symbian Vulnerability Update Nizam Uddin Bhuiyan School of Computer and Security Science Edith Cowan University Perth, Western Australia [email protected] Abstract The more the mobile devices are approaching to advance their security, the numbers of vulnerabilities are also becoming more astonishing. The number of mobile phones including smart phones is rising vertically, and so has the amount of malware activity. This report documents the latest threats in Symbian mobile industry and analyses the consequence. In addition, it will suggest the possible solution that may help individuals to protect their device & ultimately maintain the privacy. Keywords Symbian, Nokia vulnerability, Nokia threats, Mobile threat, Symbian malware, Symbian virus, Cell security, Consequences and counter measure for mobile threats. BACKGROUND The popularity of mobile has reached to sky high regardless whether you receive a blank SMS frequently or your mobile keeps sending a SMS to strangers persistently without your knowledge. According to Goode Intelligence 2009 Mobile Security Survey, “In the last couple of years, the percentage of mobile messaging traffic (SMS/MMS/e-mail) that is defined as spam or malware has risen from approximately 2% to between 20% and 30% of total traffic” (Francis, 2010). -

Vodafone K.K. Releases 702NK II (Nokia 6680) 3G Smartphone
News release 15 December 2005 Vodafone K.K. releases 702NK II (Nokia 6680) 3G smartphone Vodafone K.K. today announces that it will commence sales of the Vodafone 702NK II (Nokia 6680) 3G handset by Nokia, a Symbian OS smartphone model, on 17 December 2005 in the Kanto-Koshin region, and all other regions on 22 December. The 702NK II (Nokia 6680) is a great business tool as it lets customers view Microsoft® Word, Microsoft® Excel and other documents on their handsets, thereby enabling them to check business materials on the go without carrying notebook PCs. The 702NK II (Nokia 6680) is also Vodafone K.K.’s first handset to support ‘Vodafone Office Mail’, a push email service that lets customers remotely access company email, address books and schedule details in real-time. The main features of the 702NK II (Nokia 6680) are as follows: - Compact smartphone model full of features optimal for business use, document viewer for Microsoft® Word, Microsoft® Excel and other documents - Sleek candy bar style design with integrated front camera for easy video calling - Compatible with Vodafone Office Mail, a push email service that automatically ‘pushes’ mail directed to company PC email addresses to customers’ handsets in real-time For more information on the 702NK II (Nokia 6680), please see the attached appendix. - ends - - As of 15 December 2005 voice roaming is available on GSM networks in 130 countries and regions, with Vodafone live! internet roaming in 56 of them. In addition, 3G (W-CDMA) voice roaming is available on networks in 23 countries and regions abroad, with Vodafone live! roaming in 21 and video call roaming available in 7 of them. -

Mobile Platforms Maemo
Maemo and Symbian S60 EPFL October, 10 th 2009 Mobile Platforms Maemo •Maemo is an open development platform for applications and technology innovation for handheld devices •It was originally developed by Nokia and afterwards offered to the community as opensource Solid software architecture on Linux – first in taking Linux desktop paradigm to mobile devices Optimized for Designed for Mobile Internet Internet Devices – experiences – first in implementing the taking web2.0 apps to Maemo multimedia mobile devices based computer promise on Linux Open for innovation– Developed with some of the best open source communities Open for innovation – developed in collaboration with the open source community 14.000 members 700 hosted projects 200 applications Maemo software Community Nokia is a key contributor to Related open projects such as source projects GNOME/GTK+. Maemo.org maemo.org – 140.000 unique visitors the community 14.000 registered users for innovation 700 hosted projects on Maemo. 200 applications Product evolution Internet Optimized Multimedia Computer Nokia 770 Nokia N800 Nokia N810 Nokia N810 1st generation of Nokia In ternet 2nd generation of Nokia Internet WiMAX Edition Taking the positioning of the Tablet Tablets Tablets. Category from a predominantly ‘one- Bringing WiMAX connection to Easy access to the internet. High way’ surfing tool, to a genuine ‘two strengthen the internet story. With resolution touch sc reen. way’ communication device. wider wireless internet coverage, Internet will truly become personal With integrated -

Nokia 6680: Trendiges Smartphone
media news Lausanne, 18. August 2005 UMTS von Orange Nokia 6680: trendiges Smartphone Hardware • 3.40 x 4.10 cm grosser Bildschirm, TFT 262’144 Farben, 176 x 208 Pixels • integrierte 1.3 Megapixel-Kamera, höchste Auflösung 1280x960, 6-fach Digitalzoom • Integriertes Blitzlicht (Reichweite bis zu 1,5 Meter) • Masse: 108.4 x 55.2 x 20.5 mm; Gewicht: 133 g inklusive Batterie • Ein/Aus-Schalter, 5-Wege-Navigationsstick, 2 Tasten für Telefoniefunktion, 1 separate Taste für Sprachwahl • Lithium-Ion Polymer Akku, Sprechzeit: bis 6 Stunden, Standby: bis 250 Stunden • Speicher: 10 MB intern verfügbarer Speicher, externer Speicher MMC • Zubehör: Stereokopfhörer, Reiseladegerät, USB-Datenkabel, Software CD-ROM, Benutzerhandbuch, 64 MB MMC Speicherkarte Software/Funktionen • Betriebssystem: Symbian OS v.8.0a • Video-Telefonie, Messaging: E-Mail (POP, IMAP4, SMS, MMS) • Nokia PC-Suite (Datenabgleich mit PC/Laptop) • Real Player und MP3 Player (MP3 und Video MPEG4); Polyphone und MIDI-Klingeltöne, Audio-Formate: RNG, WAV, WVE, AMR, WB-AMR, AU, MIDI, MP3, AAC und RMF Vibrationsalarm • HTML Browser • Foto- und Videokamera (MPEG4, RealVideo, H.263, 3GP) • Fotoalbum, Bildbearbeitung (Grafikformate JPEG, BMP, GIF) • SIM-Manager, Aufgaben-Manager • Tastensperre, Notizen, Sprachaufzeichnung, bis zu 50 Telefonnummern mit Sprachwahl • Java (J2ME, MIDP 2.0, CLDC 1.1) • Diverses: Taschenrechner, Spiele Kommunikation/Schnittstellen • UMTS, EDGE, GSM Triband 900 / 1800 / 1900 MHz • GPRS (Klasse 10), Vorkonfigurierte Verbindungen für Internet, E-Mail, MMS, WAP • Bluetooth / MMC-Speicherkarte / Kopfhöreranschluss • Datenmodem • Freisprechmodus Preise Preis ohne Abo CHF 799.- Preis mit Preisplan 12 Monate 24 Monate Advanced Unlimited CHF 299.- CHF 199.- Optima 400 CHF 299.- CHF 199.- Optima 100 CHF 349.- CHF 249.- Optima 30 CHF 379.- CHF 279.- Orange Communications SA Therese Wenger, Director Media & PR World Trade Center Orange +41 78 787 10 16 Av. -
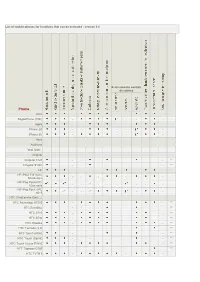
List of Mobile Phones for Functions That Can Be Activated - Version 5.4
List of mobile phones for functions that can be activated - version 5.4 Scaricamento contatti da rubrica Phone Amoi SkypePhone (TRE) - - - - Apple iPhone 2G - - - - - iPhone 3G - - - - Asus Audiovox Vedi Qtek... Cingular Cingular 8125 - - - ** Cingular SYNC - - - ** HP HP iPAQ 514 Voice - - - - - Messenger HP iPaq Pocket PC - - -* - - - - - - 63xx serie HP iPaq Pocket PC -* - - -* - - 6515 HTC (Vedi anche Qtek....) HTC Advantage X7500 - - ** HTC Excalibur - - - ** HTC S710 - - ** HTC S730 - - ** HTC Shadow - - ** HTC Tornado (2.0) ** HTC Touch (Alltel) - - - ** HTC Touch (Sprint) - - - - ** HTC Touch Cruise P3650 - - ** HTC Typhoon C500 ** HTC TyTN II - - - HTC Wizard ** Qteck/HTC P3300 - - - - - - - Qteck/HTC Touch Diamond - - - i-Mate Vedi Qtek LG LG CU500 - - ** LG KE850 - - - - - - - - LG KE850 Prada - - - ** LG KG800 (Chocolate) - - - - - - - - ** LG KS20 - - ** LG KU990 - - - ** LG KU800 - - - - - - - - - ** LG Shine (CU720) N N N ** LG Trax (CU575) N N N N N N ** LG U8550 - - - - -* LG U880 - - - - - - - - LG U900 - - - - - - - - Motorola Motorola A830/ - - - - A835 Motorola A1000 - - - - -* - Motorola A1200 Ming N ** Motorola E1000 - Motorola E398 - - - Motorola i615 N ** Motorola i880 N ** Motorola KRZR K1 - Motorola MPX220 - - - - - - Motorola RAZR2V9/ KRZR K3/ RAZR V3xx/ RAZR - MaxxV6 Motorola RAZR V3i/V3r ** Motorola RAZR V3t ** Motorola RAZR V6 Maxx ** Motorola RIZR Z3 - Motorola ROKR E6 N N ** Motorola Sidekick Slide N N N N ** Motorola SLVR L6 - Motorola SLVR L7 - Motorola U9 N N ** Motorola RAZR V3 - - Motorola V8 - - Motorola -

Symbian 'Vulnerability' and Mobile Threats
Symbian ‘vulnerability’ and Mobile Threats Wajeb Gharibi Head of Computer Engineering &Networks Department, Computer Science & Information Systems College, Jazan University, Jazan 82822-6694, Kingdom of Saudi Arabia [email protected] Abstract some possible protection techniques. Conclusions have been made in Section 5. Modern technologies are becoming ever more integrated with each other. Mobile phones are 2. Symbian Vulnerabilities becoming increasing intelligent, and handsets are The term 'vulnerability' is often mentioned in growing ever more like computers in functionality. connection with computer security, in many We are entering a new era - the age of smart different contexts. It is associated with some houses, global advanced networks which violation of a security policy. This may be due to encompass a wide range of devices, all of them weak security rules, or it may be that there is a exchanging data with each other. Such trends problem within the software itself. In theory, all clearly open new horizons to malicious users, and types of computer/mobile systems have the potential threats are self evident. vulnerabilities [1-5]. In this paper, we study and discuss one of the most Symbian OS was originally developed by Symbian famous mobile operating systems „Symbian‟; its Ltd.[4]. It designed for smartphones and currently vulnerabilities and recommended protection maintained by Nokia. The Symbian platform is the technologies. successor to Symbian OS and Nokia Series 60; Keywords: Information Security, Cyber Threats, unlike Symbian OS, which needed an Mobile Threats, Symbian Operating System. additional user interface system, Symbian includes a user interface component based on S60 5th 1. Introduction Edition. -

Aplicació D'agents En Telèfons Mòbils En L'àmbit Turístic
Proposta de PFC: aplicació d’agents en telèfons mòbils en l’àmbit turístic Número de persones: 1-2 Estudis: ETIS, ETIG, EI El PFC consisteix en integrar i millorar la feina feta en diversos PFCs anteriors, referents a l'àmbit del turisme. Els treballs previs que haurieu de consultar són els PFCs (http://www.etse.urv.es/recerca/banzai/toni/MAS/PFCs.html) d'Alex Viejo (el de 2n cicle), Montse Batet i Marc Redondo. El primer ja va implementar l'agent personal en un telèfon mòbil (un Nokia n-gage, amb algunes limitacions); la segona va implementar un sistema recomanador personalitzat (que es pot millorar en alguns aspectes); el tercer va construir un planificador de rutes turístiques dins de la ciutat. Les tasques bàsiques a realitzar en el PFC serien aquestes: • Estudiar aquests 3 PFCs. • Estudiar les capacitats dels nostres telèfons actuals, que són Nokia 6680 (veure annex). Tenim mòdul GPS que pot anar amb el mòbil. • Veure quines millores es poden fer en cadascun dels PFCs anteriors, en alguns casos aprofitant les característiques dels mòbils. • Integrar els 3 sistemes en 1 de sol, fent les millores adequades. Algunes millores podrien ser: • Aprofitar millorar les capacitats gràfiques. • Intentar explotar l'ús de fotos/videos. • Usar la possibilitat del GPS per donar informació/serveis depenents de la localització del turista. • Millorar les tècniques de recomanació del PFC de Montse. • Millorar les tècniques de planificació del PFC de Marc. • Mostrar els resultats de la planificació de Marc en el mòbil. • Pensar si es pot aprofitar la possibilitat de Bluetooth per comunicació a curta distància, mantenint el GPRS (o inclús UMTS) com comunicació a llarga distància.